Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.

How do I make Safari automatically use a particular client certificate for an entire site?
Using client certificates with Safari present a number of problems:
- Safari asks to select a client certificate on each page of the site (annoying)
- Safari might even re-ask you to choose a certificate on a page you've already visited, particularly if you have to update your client certificate
How can I fix these issues?
- ssl-certificate
3 Answers 3
Safari's client certificates and related preferences are stored in Keychain Manager with a kind of certificate .
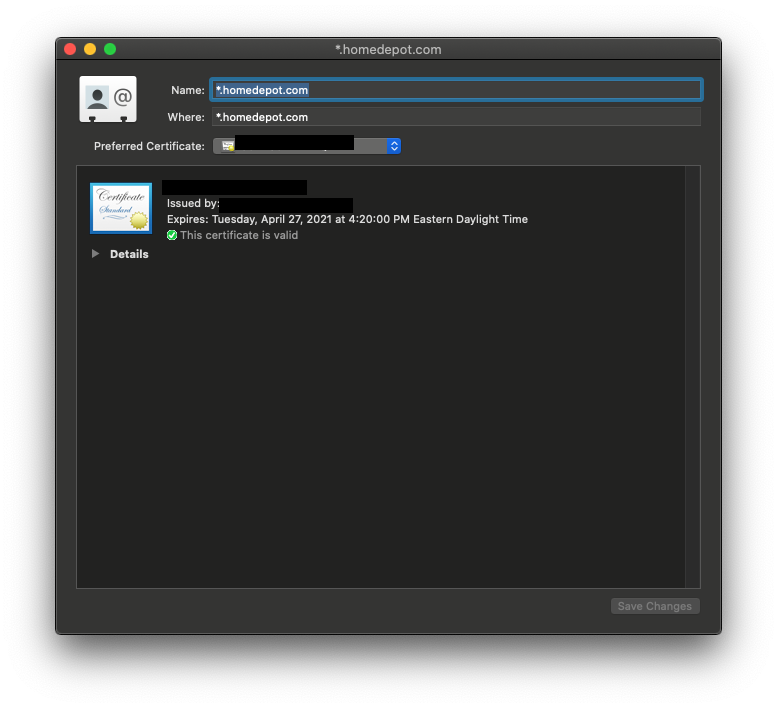
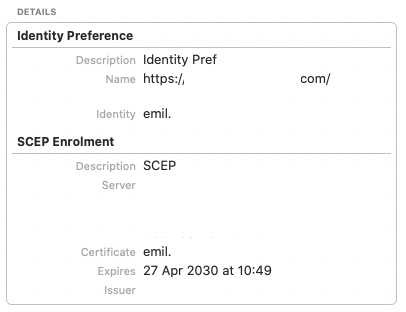
When you select a certificate to use with a web site, it stores another entry in the Keychain Manager with a kind of identity preference . Unfortunately, by default it stores it only for the exact page you were on. Both the name and location are set to the URL of the page.
To fix this, you can just edit one of the identity preference entries and change the where section to the base URL, like https://somesslsite.com/ (the trailing slash is important!). I also update the name to the same thing to prevent confusion. You can then delete all of the other identity preference entries for that site.
If you have a certificate that expired and you've had to add a new one, I would recommend that you delete the old certificate entries and all of the related identity preference entries.
To find certificate and identity preference entries, open Keychain Manager, make sure All Items is selected, and search for the partial URL and/or certificate name as appropriate. You probably don't have many, so if that doesn't work just sort the list by kind and you should be able to find them easily.
NOTE: I'm answer this myself since I figured it out but wanted to persist the knowledge for myself and others.
- 2 Unfortunately, Safari keeps asking for each sub URL... :-/ – Tafkadasoh Sep 16, 2014 at 9:27
- removed comment. DanJs answer already explains that. – Calon Sep 14, 2015 at 13:05
- 1 Not that you have to update the location property. Name is not sufficient. – andy Oct 1, 2018 at 15:16
Partial paths and wildcards are now supported in more recent versions of OS X. So you can use the Keychain Manager to create an identity preference for an entire web site and/or domain.
Partial path example (note that the trailing slash is required!):
Wildcard example:
Full details here (from 'man security' page):
Prior to 10.5.4, identity preferences for SSL/TLS client authentication could only be set on a per-URL basis. The URL being visited had to match the service name exactly for the preference to be in effect. In 10.5.4, it became possible to specify identity preferences on a per-server basis, by using a service name with a partial path URL to match more specific paths on the same server. For example, if an identity preference for " https://www.apache-ssl.org/ " exists, it will be in effect for " https://www.apache-ssl.org/cgi/cert-export ", and so on. Note that partial path URLs must end with a trailing slash character. Starting with 10.6, it is possible to specify identity preferences on a per-domain basis, by using the wildcard character * as the leftmost component of the service name. Unlike SSL wildcards, an identity preference wildcard can match more than one subdomain. For example, an identity preference for the name *.army.mil will match server1.subdomain1.army.mil or server2.subdomain2.army.mil . Likewise, a preference for *.mil will match both server.army.mil and server.navy.mil .
- Worked for me (running Safari 7.0.1 on Mac OS X 10.9.1) – Tafkadasoh Dec 19, 2013 at 11:07
- The "File->New Identity Preference" menu item seems to have disappeared (as of Keychain Access 10.5). Now I can only find it in a contextual menu if I control-click on a certificate. – jhfrontz Jan 29, 2020 at 15:01
- Strange @jhfrontz... I am also running 10.5 and I still see the "File->New Identity Preference...". 4th item down under "New Keychain...". Are you sure you have a certificate selected? – DanJ Jan 30, 2020 at 16:33
- @DanJ aha, thanks. I was expecting it to be a generally available menu item. – jhfrontz Jun 23, 2020 at 14:07
I've been struggling with this myself and the above answer made me realize what was going on.
If you had a certificate for a website and it expired, what you should do is remove the old certificate. Then also remove the identity preference type items for that website. These old items are just as much expired as the certificate is. After you remove them, any new identity preference will be stored and used correctly.
- Remove old certificate
- Remove old certificate's identity preference items
- Add new certificate
Then you can browse to the website, select the new certificate from the list, this will be remembered for that specific web address. Currently we are at Safari 5.1.3 and this version will not use any wildcards for preferences, you will have to add the preference for each change in web address... Hope this helps someone, just putting it out there because I didn't find any complete answer.
- please refer to @apinstein answer for the correct way to do it – dwery Oct 10, 2013 at 12:50
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged safari ssl-certificate ..
- The Overflow Blog
- Climbing the GenAI decision tree sponsored post
- Diverting more backdoor disasters
- Featured on Meta
- New Focus Styles & Updated Styling for Button Groups
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network
- Google Cloud will be Sponsoring Super User SE
Hot Network Questions
- Where's the `info` command in recent macOS versions?
- Red Dwarf: Episode in which Holly Offers to Make a Woman?
- What's to stop domain registrars from price gouging renewals?
- Is this super soldier viable and grounded?
- Professor Rackbrane: Count the triangles
- How to simulate low-rank hamiltonian?
- What is a safe way to transport an e-bike battery on planes?
- How would the existence of sapient "Pet Rocks" affect the economy of a medieval kingdom?
- "Pure Imaginary" or "Purely Imaginary"?
- How to execute a command on all files whose names match a pattern and whose contents match a pattern?
- Insurance for expeditions
- Differences Between `/dev/null` and Devices Under `null_blk` Driver
- Does there exist a triangle with heights 2, 4, and 5?
- Is there an overarching purpose for philosophy?
- Fixed Repeating Output
- How do I snap an object permanently to another object in animation?
- What's the most common word in Latin?
- Is an LED driver IC just a boost conv with voltage across Rsense fed into FB?
- Why does a goddess put a low limit on the number of priests?
- Is there something between Debug and Release build?
- Planet is settled by people who want to recreate their ancestors' African society. A very intelligent girl is not allowed to learn to read and write
- Why are the solar prominences visible during a total solar eclipse - orange? Is the sun orange?
- Why is remote desktop very slow when host monitor is off unless HDMI cable is used?
- Novella about man reminiscing about his girlfriend/wife while standing by her dead body
How to get client certificate from application
I've installed a certificate into my iOS device by downloading it using Safari. But when I run my app and query site needs client certificate, it will show message "No required SSL certificate was sent". How can I find client certificate and send it to server?
iOS apps do not have access to credentials stored in the Apple ‘slice’ of the keychain. QA1745 Making Certificates and Keys Available To Your App explains this in more depth.
As to what you can do about this, that depends on your specific requirements. First up, are you working in a managed environment?
Share and Enjoy — Quinn “The Eskimo!” Apple Developer Relations, Developer Technical Support, Core OS/Hardware
The most important scenario is to fix enertprise user's requirement. They are managed accounts.
QA1745 Making Certificates and Keys Available To Your App explains to use digital identities in our apps, we need to write code to import them. Is there a detail guideline about how to import them to non-apple-provided apps and support client certificate based authentication in our app? How to automatically know which certificate should be used for target site?
You can import a digital identity using
Ideally, there would be a way for admins to push a digital identity to a specific keychain access group via a configuration profile. This is a commonly-requested feature but, alas, there’s no sign of it being implemented. If you feel like adding your voice to the choir, please file an enhancement request describing your requirements.
In the absence of such a feature, you need to come up with a different way to get your PKCS#12 data. There’s a bunch of ways you can do this but in managed environments the best option IMO is to use Kerberos SSO. You have two ways to approach that:
You can configure your origin server to support Kerberos SSO and then you’re done.
If that’s not feasible — for example, because your origin server software doesn’t support Kerberos SSO — you can configure a second server that supports Kerberos SSO and, once authenticated, hands out the digital identity required to access the origin server. Your app can then first talk to that server to get the digital identity, and then use that to talk to the origin server.
Beyond that, there’s a bunch of less-than-ideal approaches. For example, many folks use managed app configuration for this [1], despite the fact that, when we introduced that feature, we specifically warned folks not to use it for credentials.
[1] See WWDC 2013 Session 301 Extending Your Apps for Enterprise and Education Use .
With regards your other questions:
Is there a detail guideline about how to … support client certificate based authentication in our app?
How you do that depends on the networking API you’re using. If you’re using
How to automatically know which certificate should be used for target site?
The only automatic way of doing that is to rely on an obscure feature of the authentication challenge, namely the
Doing that is quite tricky, and thus very few apps implement it. The alternative is to implement some less automatic mechanism:
You can ask the user, à la Safari.
You can document a managed app configuration preference that lets admins configure this.
I'm currently facing a similar situation.
We're using WKWebView . In its delegate method didReceiveAuthenticationChallenge , I managed to access distinguishedNames .
The problem is, I don't know how to get credential from certificate that is installed by MDM.
Apparently our website managed to work when accessing with
>The only automatic way of doing that is to rely on an obscure feature of the authentication challenge, namely the
I appreciate so much if you could show my how to let this done.
Apparently our website managed to work when accessing with SFSafariViewController .
Right, because
Thank you for detailed information.
We made some modification on server side respondings, and decided to use SFAuthenticationSession instead of WKWebView .
Search code, repositories, users, issues, pull requests...
Provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
iOS application to demonstrate the use of a client certificate for authentication
MarcoEidinger/ClientCertificateSwiftDemo
Folders and files, repository files navigation, client certificate handling on ios demo.
Explanation and Demonstration of Client Certificate Authentication on iOS.
Complete YouTube video: https://youtu.be/qSzk-gMsFZ4
What is it?
Client Certificate Authentication is a mutual certificate-based authentication, where the client provides its Client Certificate to the server to prove its identity. This happens as a part of the SSL Handshake ( optional ).
How it works with ... ?
URLSessionDelegate is required which implements URLSession:didReceiveChallenge:completionHandler: and returns URLCredential instance to resolve a client certificate authentication challenge.
WKNavigationDelegate is required which implements webView(_:didReceive:completionHandler:) and returns URLCredential instance to resolve a client certificate authentication challenge.
SafariViewController
Works when certificate was installed on the device in the Apple keychain access group.
- Open link in Safari
Why apps cannot rely on installed certificates through Safari, Email or MDM ?
Users can install digital identities (certificates plus their associated private keys) onto their iOS devices by downloading them from within Safari, by opening them as email attachments, and by installing them with configuration profiles. Or, identities can be pushed from a Mobile Device Management (MDM) server. However, identities installed in any of these ways are added to the Apple keychain access group.
Apps can only access keychain items in their own keychain access groups. This means that items in the Apple access group are only available to Apple-provided apps such as Safari or Mail.
To use digital identities in your own apps, you will need to write code to import them. This typically means reading in a PKCS#12-formatted blob and then importing the contents of the blob into the app's keychain using the function SecPKCS12Import documented in Certificate, Key, and Trust Services Reference .
This way, your new keychain items are created with your app's keychain access group.
Source: Technical Q&A QA1745 - Making Certificates and Keys Available To Your App
iOS application to demonstrate the use of a client certificate for authentication.
Use this app to access https://client.badssl.com/ in various ways
- URLSession.dataTask
- SFSafariViewController
Website https://client.badssl.com/ requires a valid user certificate. Otherwise server returns HTTP 400.
For convenience, I added badssl.com-client.p12 (downloaded from https://badssl.com/download/ ) as a bundle resource. This allows you to test the successful authentication with a user certificate using URLSession and WKWebView .
Note: in case the certificate does no longer work (expires Nv 28, 2025) then try to download the latest version from https://badssl.com/download/ .

Acknowledgments
https://badssl.com/ (open-source: https://github.com/chromium/badssl.com )
Client certificate with URLSession in Swift
WKWebView with client certificate
WKWebView in SwiftUI
More Details about Client Certificate
A Client Certificate is a digital certificate which confirms to the X.509 system. A certificate contains an identity (a hostname, or an organization, or an individual) and a public key (RSA, DSA, ECDSA, ed25519, etc.), and is either signed by a certificate authority or is self-signed. It is used by client systems to prove their identity to the remote server.
The certificate public key as well as the correspinding private keya is stored in a .p12 files. The container format is password protected and therefore fully encrypted (unlike .pem files).
This is a password-protected container format that contains both public and private certificate pairs. Unlike .pem files, this container is fully encrypted.
You can use the openssl library to decrypt the p12 file, access the certificate or private key information and transform them. For example, to decode the certificate information stored in the encrypted file.
- Swift 100.0%
Trust manually installed certificate profiles in iOS and iPadOS
If you manually install a profile that contains a certificate payload in iOS and iPadOS, that certificate isn't automatically trusted for SSL. Learn how to manually trust an installed certificate profile.
This article is intended for system administrators for a school, business, or other organization.
You must manually turn on trust for SSL/TLS when you install a profile that is sent to you via email or downloaded from a website.
If you want to turn on SSL/TLS trust for that certificate, go to Settings > General > About > Certificate Trust Settings. Under "Enable full trust for root certificates," turn on trust for the certificate.
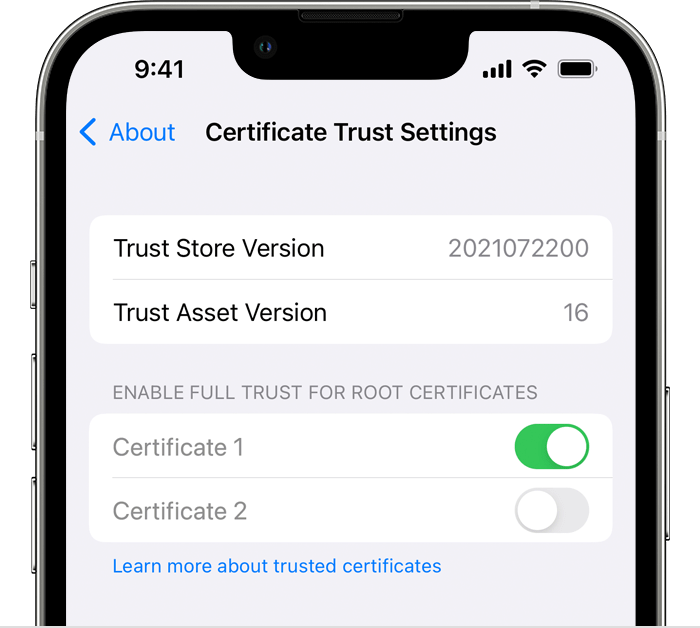
Apple recommends deploying certificates via Apple Configurator or Mobile Device Management (MDM). Certificate payloads are automatically trusted for SSL when installed with Configurator, MDM, or as part of an MDM enrollment profile.
Explore Apple Support Community
Find what’s been asked and answered by Apple customers.
Contact Apple Support
Need more help? Save time by starting your support request online and we'll connect you to an expert.
Looks like no one’s replied in a while. To start the conversation again, simply ask a new question.
Make Safari accept an untrusted certificate
I'm using Safari 10.0.1 on macOS Sierra 10.12.1
I'm trying to view use Safari to view a web server I use for staging content. Since it's only a staging server, I have a certificate with an untrusted root (it's from the letsencrypt staging environment). It used to be that when I tried to load a site like this from Safari, it would alert me, but I could still accept the insecure certificate and continue on to the site.
Lately, I just get an error that "Safari can't establish a secure connection to the server," and that's it. There's no option to load it anyway. There's no lock icon in the URL bar to look at the certificate. I've been using Chrome to load this site because it has the behavior I used to see in Safari. Is there any way to get the old behavior back?
MacBook Pro with Retina display, macOS Sierra (10.12.1)
Posted on Nov 18, 2016 4:03 PM
Posted on Nov 19, 2016 7:16 AM
From Safari Help
Change the trust settings of a certificate
You can view or change a certificate’s trust policies in Keychain Access.
Open Keychain Access for me
In the Category list, select a category.
Select a certificate, then choose File > Get Info.
Click the Trust disclosure triangle to display the trust policies for the certificate.
To override the trust policies, choose new trust settings from the pop-up menus.
Safari Certificate not recognized
Certificate isn’t being accepted
Loading page content
Page content loaded
Nov 19, 2016 7:16 AM in response to feck
Nov 20, 2016 11:42 AM in response to Eric Root
Thanks for the reply. Now I realize that the title of the post is inaccurate. I don't want Safari to accept the certificate. I want it to prompt me whether or not it should load a site with an untrusted certificate.
The certificate is not in the keychain. I suppose a workaround would be to add it to the keychain and then set it to always trust. I would rather have the old behavior back, where I get a warning with the option to continue or cancel loading the page.
I get the behavior I want on other staging sites. I'm thinking I might regenerate my certificate for the problematic site and see if that fixes it.
Jun 12, 2017 7:36 AM in response to feck
Found the answer in this thread .
Safari -> Preferences -> Privacy -> Manage Website Data…-> Remove All
- Jamf Nation Community
- Auto-selecting client certificates for website in ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Auto-selecting client certificates for website in Safari
- Mark as New
- Report Inappropriate Content
Posted on 04-28-2020 03:41 AM
- All forum topics
- Previous Topic
Posted on 04-28-2020 08:28 AM
Posted on 04-29-2020 01:51 AM
Posted on 04-29-2020 09:55 AM
Posted on 09-29-2022 08:19 PM
Posted on 03-01-2024 09:02 AM
never-displayed
Client certificate authentication
Would it be possible to add TLS client certificate authentication to the iOS app? I think android app already allows it.
My HA is behind a reverse proxy configured to require client certificate authentication, improving it’s security a lot.
I installed the certificate profile on my iPhone and can access HA with Safari, but iOS companion complains with “Client Certificate Authentication is not supported”.
I’m not an expert on iOS programming, but I think there are two ways of supporting it:
1- Using SFSafariViewController (not WKWebView) to login on HA (it can use the certificate profile installed on iPhone, just like Safari)
2- Asking for a certificate file to be installed inside Companion app and manage the authentication there.
The login window supporting it does little for the rest of the app also supporting it, and it’s not as simple as installing the certificate somewhere and the app uses it. You can see the current ‘status’ in the following draft (as in, not going to be merged soon) pull request: Allow supplying client certificates by zacwest · Pull Request #2144 · home-assistant/iOS · GitHub
The biggest issue here is that it will basically preclude using the Apple Watch complications and certain (future) types of widgets. Apple’s networking system simply doesn’t support client certificates for background networking operations, which these effectively require. I’m a bit reluctant to introduce a feature with such restrictions, but it may be okay if it’s super clear that it’s happening.
I’m hung up on this as well. Where I have landed, is two different access methods from the phone. The Companion app has a specific URL that allows Pre-Determined web hook ID’s through. This allows for the app to push updates into HA. But I can’t view any of the HA information when external.
Then I have another “External HA” access icon, this loads Safari and connects back home on a different port that requires Client Certificates. It allows un-restricted access to the HA server. It’s not elegant, but it works for the time being.
Support client SSL certificates in iOS app
It looks like Brave on iOS does not support authentication through client SSL certificates like it does in the desktop app.
This is supported in Safari on iOS through configuration profiles: I can install a .p12 client certificate on my phone, and this will automatically be used on websites that have SSL client verification enabled.
After some searching I found that Apple does not expose these configuration profiles to other apps, but it should be possible to import client certificates into the Brave app keystore: https://developer.apple.com/library/archive/qa/qa1745/_index.html
It seems like you’ve identified that Brave on iOS currently lacks support for client SSL certificates, unlike its desktop counterpart. While Safari on iOS does support client SSL certificates through configuration profiles, the same functionality is not exposed to other apps, including Brave.
However, you’ve come across a potential workaround—importing client certificates into the Brave app keystore. According to Apple’s documentation ( https://developer.apple.com/library/archive/qa/qa1745/_index.html ), this should be feasible.
For a more detailed and accurate solution, you may want to discuss this with the Brave community or development team. They might provide insights on any ongoing developments, workarounds, or plans to support client SSL certificates in future iOS app updates. Your findings and input could be valuable for others facing similar challenges.
Related Topics
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Certificate-based authentication for iOS fails to prompt for user certificates
- 4 contributors
- Applies to: Microsoft Entra ID, Microsoft 365
Federated users on Apple iOS devices that have valid user certificates discover that they can't perform Certificate-Based Authentication (CBA) against Microsoft Entra ID. However, federated users on Android and Windows devices can successfully authenticate by using CBA. The same iOS users encounter no issues when they authenticate by using their username and password.
Here's the typical experience for iOS users who can't authenticate when they sign in to ADAL-enabled Office applications on iOS:
- The user walks through the Office app setup experience. At the "Office365" sign-in page, the user clicks Sign-in.
- The ADAL Sign-in page appears, on which the user enters their federated email address and then clicks Next.
- The ADAL Sign-in process hangs at a blank page until it times out and returns a "There is a problem with your account. Try again later" error. This page includes the option to tap OK.
- If the user taps OK, they sit at the same blank Sign-in page with the option at the top to tap Back.
- Tapping Back returns the user to the ADAL Sign-in page, where the process starts all over: the user is prompted to enter their federated email address and then click Next.
- Tapping OK returns to a blank Sign-in screen, where the user can enter their UserPrincipalName and repeat the process.
To eliminate Office applications as a factor, we recommend that federated users in an iOS environment test certificate-based authentication in the Safari browser by following the steps in the "More Information" section. The typical experience for iOS users who can't authenticate against https://portal.office.com from a Safari browser goes as follows:
The user isn't prompted as expected to approve the use of their user certificate after they click the Sign-in using an X.509 certificate link.
The federated user either sits at an unresponsive STS sign-in page or advances to the default STS sign-in page, where they're prompted as follows:
Select a certificate that you want to use for authentication. If you cancel the operation, please close your browser and try again.
Note If other authentication methods are enabled in AD FS, the users also see a link stating "Sign-in with other options." If they click this link, they return to the STS sign-in page.
Both experiences fail with the following error:
Safari could not open the page because the server stopped responding.
The certificate chain is incomplete because the issuing subordinate CA certificate isn't retrieved by the device as expected when the MDM policy pushes just the Root certificate to the Apple device along with the SCEP profile.
The iOS device doesn't correctly acquire the Issuing CA's *.crt file, even though the AIA path on the user certificate has a valid URL that points to the Issuing subordinate CA's *.crt file.
If the customer is using Intune to manage the device, advise them to create a new configuration policy for an iOS Trusted Root Certificate that points to the Intermediate Certificate Authorities' *.CER file. Then, advise them to open the company portal on the device and refresh the policy. The connection should now succeed.
More Information
If you take an "Apple Configurator 2" trace from an OS X client that's connected to the iPad by using the lightning cable, the trace log resembles the following example:
Was this page helpful?
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources

IMAGES
VIDEO
COMMENTS
Safari's client certificates and related preferences are stored in Keychain Manager with a kind of certificate. When you select a certificate to use with a web site, it stores another entry in the Keychain Manager with a kind of identity preference. Unfortunately, by default it stores it only for the exact page you were on.
You can ask the user, à la Safari. You can document a managed app configuration preference that lets admins configure this. Share and Enjoy. —. Quinn "The Eskimo!". Apple Developer Relations, Developer Technical Support, Core OS/Hardware. let myEmail = "eskimo" + "1" + "@apple.com". Posted 4 years ago by.
Root certificates installed manually on an unsupervised iPhone and iPad through a profile display the following warning, "Installing the certificate "name of certificate" adds it to the list of trusted certificates on your iPhone or iPad. This certificate won't be trusted for websites until you enable it in Certificate Trust Settings.".
Safari (or any other web client) doesn't present its client certificate unless requested by the website. So your client certificate is safe. The server is always the one asking for the certificate, sending along its own certificate. Therefore, your browser will see that the certificate do not match the one you have and will result in failure ...
1. There is another freeware Inspect - View TLS certificate. - Franklin Yu. Nov 7, 2021 at 4:07. 1. TLS Inspector also adds a convenient feature to view the certificate straight from Safari: tap the Share button and scroll down to the Show Certificate option. - dregad.
With Safari on iOS, I can browse to my main page using the Stack Exchange Network Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
3. Before using client certificates in your app (as already answered by Jake) you have to implement import of certificate within your app to your app keychain. (note you need to use PKCS#12 certificate format, but you need to register it in your app (search for exported UTIs and Document types) with different extension, other than ".p12", which ...
A Client Certificate is a digital certificate which confirms to the X.509 system. A certificate contains an identity (a hostname, or an organization, or an individual) and a public key (RSA, DSA, ECDSA, ed25519, etc.), and is either signed by a certificate authority or is self-signed. It is used by client systems to prove their identity to the remote server.
To use client certificates in your app you have to implement import of certificate within your app to your app keychain. (note you need to use PKCS#12 certificate format, but you need to register it in your app (search for exported UTIs and Document types) with different extension, other than ".p12", which is already registered by the iOS.
If you want to turn on SSL/TLS trust for that certificate, go to Settings > General > About > Certificate Trust Settings. Under "Enable full trust for root certificates," turn on trust for the certificate. Apple recommends deploying certificates via Apple Configurator or Mobile Device Management (MDM).
To introduce redundancy into your pinning configuration, you can associate multiple public keys with a domain name. For example, to pin multiple public keys for the example.net server certificate, you would add individual entries as items in an array to the Info.plist file of your app. To satisfy the pinning requirement for a connection to ...
From Safari Help. Change the trust settings of a certificate. You can view or change a certificate's trust policies in Keychain Access. Open Keychain Access for me. In the Category list, select a category. Select a certificate, then choose File > Get Info. Click the Trust disclosure triangle to display the trust policies for the certificate.
3. I use a free app for this: TLS Inspector. It lets you view details about a domain's certificate and other security-related information. It also adds a convenient feature to view the certificate straight from Safari: tap the Share button. scroll down to the Show Certificate option. Share.
Hey guys. I have a website we use that asks for a client certificate from the users. I'd like to auto-accept it in Safari and are pushing these custom settings with the SCEP certificate, but it wont work in Safari. We are using this documentation and it works for the TENANT.vmwareidentity.eu. I can get Google Chrome to auto-select the certificate.
1- Using SFSafariViewController (not WKWebView) to login on HA (it can use the certificate profile installed on iPhone, just like Safari) or. 2- Asking for a certificate file to be installed inside Companion app and manage the authentication there. Regards. The login window supporting it does little for the rest of the app also supporting it ...
It looks like Brave on iOS does not support authentication through client SSL certificates like it does in the desktop app. This is supported in Safari on iOS through configuration profiles: I can install a .p12 client certificate on my phone, and this will automatically be used on websites that have SSL client verification enabled. After some searching I found that Apple does not expose these ...
Safari could not open the page because the server stopped responding. ... advise them to create a new configuration policy for an iOS Trusted Root Certificate that points to the Intermediate Certificate Authorities' *.CER file. ... If you take an "Apple Configurator 2" trace from an OS X client that's connected to the iPad by using the ...
This opened Safari, the user can select their certificate and the web server authenticates. I got a successful callback URL on the iOS app and the Safari view gets dismissed automatically. After the session has been started, I used the following to open a URL: UIApplication.shared.open(url, options: [:], completionHandler: nil) It opens the ...
2. I've got an ASP.NET MVC application deployed on Azure, and users login using a client certificate. All the process works fine on desktop browser (Chrome, Opera, Firefox, IE) and Android, but on iOS Safari asks to the user to select the proper client certificate at every link tapped if there're more than one certificate available installed.