Why WebCrypto Encryption Matters: Apple’s Argument for Ditching Older Methods
In a recent WebKit blog post, Apple made a compelling argument for adopting some new coding standards for encryption. The technology behind those web pages we love to use is ever-evolving, but sometimes the trick is convincing developers to learn new ways of doing things. Let’s look at the argument Apple makes for adopting WebCrypto encryption, in easier-to-understand language.

What Is WebKit and WebCrypto Encryption?
WebKit, in short, is a mechanism for showing you those web pages you love in your browser. It powers Apple’s Safari web browser as well as Chromium-based browsers like Google Chrome and Opera.
Apple created the WebCrypto API to bring cryptography, the cornerstone of information security, native to the web browser. Cryptography is what’s behind those secure websites you visit, like the checkouts for shopping sites and your bank’s website. Previously, developers have used several very successful JavaScript cryptography libraries to allow cryptography on the web.
Why Should We Change If the JavaScript Libraries Are so Successful?
The post dives into quite a bit of highly technical programming mumbo-jumbo, but the gist of it is this: WebCrypto encryption and the new SubtleCrypto method are more secure and operate faster than competing third-party JavaScript libraries.
Performance Increases Using WebCrypto
See the table below, demonstrating WebCrypto’s performance in AES-GCM encryption and decryption. The table also showcases how quickly SHA–2 can determine a file’s overall integrity the file is encrypted or decrypted.
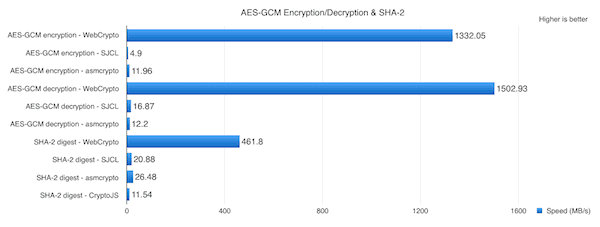
You can see that the table says higher numbers are better. Let me elaborate. WebCrypto encryption is able to encrypt a file at a speed of 1.33GB per second. By way of comparison, the fastest JavaScript library can only do so at around 12MB per second. That’s a huge performance increase, and the results are similar for both decryption and the SHA–2 digest integrity check.
The Problem With JavaScript’s Security
In addition, the post points out that WebCrypto encryption is functionally more secure. In non-native JavaScript libraries, secret or private keys have to be stored within the “execution context” of JavaScript. This means JavaScript stores them in the executable or resource scripts or files used by the library.
This lends itself to an extreme vulnerability, because those JavaScript resources are exposed at runtime and could be attacked – the keys can be stolen by skillful hackers. We call this an XSS, or cross-site scripting attack. Such an attack happens when hackers inject malicious scripts into web sites we trust, usually through our computers.
This typically happens because a Trojan or other malware on the user’s computer injects the malicious code. I believe we may have seen examples of this with LastPass and LinkedIn, although those sites haven’t disclosed precisely how they were breached.
WebCrypto API: A More Secure Model
WebCrypto stores the keys outside of the JavaScript “execution context.” This limits the chance of a malicious person stealing the private key through an XSS attack. In other words, a hacker can’t execute malicious JavaScript in your browser to steal a secure web site’s private keys.
The fact that security and performance are better across the board with WebCrypto API should be enough to encourage developers to migrate their secure web apps. So, why haven’t more secure websites implemented the WebCrypto API?
These Things Take Time
Developing a secure interface for a transport medium (like the web) that is so inherently insecure takes loads of time and resources. Once they’ve completed the job, companies are reluctant to devote the time, energy, and money to do it over again.
Apple’s latest argument, in the form of the blog post we’ve been discussing, should help speed things up. It explains in readily understandable language (if you’re a developer) why the WebCrypto API is superior to non-native JavaScript libraries. I fully believe some companies are already in the lengthy process of adopting these changes, and others are sure to follow suit after Apple’s compelling argument.
3 thoughts on “ Why WebCrypto Encryption Matters: Apple’s Argument for Ditching Older Methods ”
@dizzy1618 Actually, not at all inaccurate, despite what you may have read on Wikipedia. Apple owns all rights to WebKit at this point and is behind much of its active development. Look at WebKit.org , the official web page for the project. At the bottom, you’ll see:
WebKit and the WebKit logo are trademarks of Apple Inc.
My opening paragraph doesn’t say that Apple invented WebKit, just that Apple is behind it now and is making a compelling argument for adopting the WebCrypto encryption.
Google forked Webkit into Blink a few years ago, so your opening paragraph there is slightly inaccurate 🙂
We call this an XSS, or cross-site scripting attack. Such an attack happens when hackers inject malicious scripts into web sites we trust, usually through our computers.
Glad you mentioned this. Just a week or so ago we were having a discussion of the need for a good Anti-malware on the Mac. Someone said it wasn’t necessary as long as you didn’t download software outside of the MacAppStore and “Avoid sketchy sites”. Well, you can get hit from any site, and this is how. About once every couple of months I get a warning, either from Safari or Avast about a page on GoComics. Never the same one. It never is there the next day, Just occasionally the page I hit every day is a carrier.
Leave a Reply Cancel reply
You must be logged in to post a comment.
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Web Cryptography
JavaScript API for performing basic cryptographic operations in web applications
- 4 - 36 : Not supported (but has polyfill available)
- 37 - 124 : Supported
- 125 : Supported
- 126 - 128 : Supported
- 12 - 18 : Supported
- 79 - 123 : Supported
- 124 : Supported
- 3.1 - 7 : Not supported (but has polyfill available)
- 7.1 - 10.1 : Supported
- 11 - 17.4 : Supported
- 17.5 : Supported
- 17.6 - TP : Supported
- 2 - 31 : Not supported (but has polyfill available)
- 32 - 33 : Disabled by default
- 34 - 125 : Supported
- 126 : Supported
- 127 - 129 : Supported
- 9 - 23 : Not supported (but has polyfill available)
- 24 - 108 : Supported
- 109 : Supported
- 5.5 : Not supported
- 6 - 10 : Not supported (but has polyfill available)
- 11 : Partial support
Chrome for Android
Safari on ios.
- 3.2 - 7.1 : Not supported (but has polyfill available)
- 8 - 10.3 : Supported
- 17.6 : Supported
Samsung Internet
- 4 - 23 : Supported
- 24 : Supported
- all : Not supported
Opera Mobile
- 10 - 12.1 : Not supported (but has polyfill available)
- 80 : Supported
UC Browser for Android
- 15.5 : Supported
Android Browser
- 2.1 - 4.4.4 : Not supported (but has polyfill available)
Firefox for Android
- 14.9 : Supported
Baidu Browser
- 13.52 : Supported
KaiOS Browser
- 2.5 : Supported
- 3 : Supported
Many browsers support the [crypto.getRandomValues()](#feat=getrandomvalues) method, but not actual cryptography functionality under crypto.subtle .
WebCrypto Master Key
The app Friendly Streaming is asking me to share with that app my WebCrypto Master Key. I have no idea what that is. Where can I find the Master Key if it exists, and if it doesn't exist, how do I set it up? Is it safe to share with an app? Meanwhile, I cannot use the app on my Mac. Any help would be greatly appreciated.
MacBook Air (M1, 2020)
Posted on Apr 24, 2023 3:23 PM
Posted on Apr 24, 2023 4:45 PM
I have it too. I've used Friendly Streaming for 2 year or more and have never had any problems. Now I'm spooked and would like to know what this is all about. I have Apple TV on my iMac but it does't connect to Prime or Netflix like I can on the TV screen.
Similar questions
- Chrome Keychain Access Extension I want to access the Macbook keychain password for the Google Chrome & if there any possible way to use keychain access just like it is used in safari at just one single click to access various accounts.Hence Saving time to regain access to account easily. 2078 4
- Keychain What is BeaconStore App in Keychain? What is it for? How did it get there? Is it safe to delete? 957 1
- how to install keychain in Edge or Edge extension I need to install keychain in a Windows PC; also want it to work in iPhone and iPad Geeksavy 237 1
Loading page content
Page content loaded
Apr 24, 2023 4:45 PM in response to lridolfi
Apr 25, 2023 12:08 PM in response to lridolfi
I'm one of developers of Friendly Streaming.
The webcrypto key is automatically created by Apple's Webkit framework (supporting safari as well as Friendly Streaming).
An update is on its way that fix this issue (submitted today to the AppStore Review team).
In the meantime the best and most secure solution is to:
1- quit friendly
2- open the "Keychain access" app (in applications/Utilities) or look for "keychain access" in spotlight.
3- in Keychain Access, look for this key (enter "Friendly Streaming" in the search box)
4- delete the key,
5- Launch friendly streaming again. When navigating to any website that uses webcrypto, a new "friendly streaming webcrypto master key" will be created.
I'm attaching screenshots:
Hope this helps,
Don't hesitate to contact us via our support email if you need more information.
Apr 25, 2023 6:43 PM in response to joi-joikeith
- Make sure the Friendly Streaming app is closed.
- Open your Applications folder. Inside it, find the folder Utilities and in it, find the app Keychain Access .
- On the left sidebar of Keychain Access , find System Roots . Click on it.
- At the top of the window, use the search box to search for Friendly Streaming.
- This should bring you to the key for Friendly Streaming.
- Press the Control key and click on Friendly Streaming Web Crypto Master Key.
Then you should be able to select Delete.
This is my best shot at describing how to delete the Crypto Master Key.
Apr 25, 2023 12:46 PM in response to sphilipakis
Thank you for your response. I have tried to delete the Master Key and am unable to do so. I had also created another master key yesterday in my attempts to fix the problem myself. This may have exacerbated the problem. I am unable to delete either key. I may have to call Apple to figure out how to delete them.
Apr 25, 2023 1:02 PM in response to lridolfi
What Sphilipakis suggested work for me. If you are unable to delete the “friendly streaming” from keychain access go to “system root” then search friendly streaming and delete it from there. Look at Sphilipakis’s screenshot. On the left hand go on “system root” then do the search and you will be able to delete it.
Apr 25, 2023 1:49 PM in response to del_monte
In the Keychain Access app, look for System Roots on the left sidebar. Click on it and then search for Simple Streaming. You should see the master keychain. Right-click the master keychain and delete it. This worked for me.
Apr 25, 2023 10:49 PM in response to lridolfi
I couldn't delete either and ended up going down a very long Terminal rabbit hole. In my case, I discovered that the delete was not in the System Roots folder but was in the Default Keychains/login folder. I searched for "WebCrypto", found the Friendly Streaming one and deleted. It doesn't really matter which option you click, though, I'm pretty sure search will search for all of the keychains no matter where they ar.
I ran this command in a terminal window prior to it working:
sudo security delete-certificate -c "Friendly Streaming WebCrypto Master Key" login.keychain-db
To be fair, this might be the wrong command. Anyway, I messed around with it for awhile running searches using security, tried that command, went back into the GUI and was able to delete and relaunch it again. May be a coincidence but it could be worth trying.
Apr 26, 2023 5:15 AM in response to rhiannasilel
I was having the same issue (couldn't delete it either) but this method worked. I ran your suggested command in the terminal and initially it returned unable to delete, but when I went back to the keychains login folder and tried again it finally worked. I was able to relaunch without issue after that, hopefully it stays that way!
Apr 26, 2023 10:58 AM in response to del_monte
Apr 25, 2023 12:59 PM in response to lridolfi
Can you right-click and select the 'delete Friendly Streaming WebCrypto Master Key' menu entry ?
Apr 25, 2023 7:42 PM in response to sphilipakis
This is so messed up I can’t do anything. It will not delete. Yes I tried the system root. Now I have this
Apr 24, 2023 4:09 PM in response to lridolfi
You should probably delete that app.
Apr 24, 2023 6:12 PM in response to iDiane13
I've decided to delete the app.
Apr 25, 2023 12:20 PM in response to sphilipakis
I can't delete the key.
Apr 25, 2023 1:18 PM in response to parinaz18
Thank you, parinaz18. I was able to delete the key from "system root." All is well now!
- Skip to main content
- Skip to search
- Skip to select language
- Sign up for free
SubtleCrypto: digest() method
Secure context: This feature is available only in secure contexts (HTTPS), in some or all supporting browsers .
The digest() method of the SubtleCrypto interface generates a digest of the given data. A digest is a short fixed-length value derived from some variable-length input. Cryptographic digests should exhibit collision-resistance, meaning that it's hard to come up with two different inputs that have the same digest value.
It takes as its arguments an identifier for the digest algorithm to use and the data to digest. It returns a Promise which will be fulfilled with the digest.
Note that this API does not support streaming input: you must read the entire input into memory before passing it into the digest function.
This may be a string or an object with a single property name that is a string. The string names the hash function to use. Supported values are:
- "SHA-1" (but don't use this in cryptographic applications)
- "SHA-512" .
An ArrayBuffer , a TypedArray or a DataView object containing the data to be digested.
Return value
A Promise that fulfills with an ArrayBuffer containing the digest.
Supported algorithms
Digest algorithms, also known as cryptographic hash functions , transform an arbitrarily large block of data into a fixed-size output, usually much shorter than the input. They have a variety of applications in cryptography.
Warning: SHA-1 is now considered vulnerable and should not be used for cryptographic applications.
Note: If you are looking here for how to create a keyed-hash message authentication code ( HMAC ), you need to use the SubtleCrypto.sign() instead.
For more examples of using the digest() API, see Non-cryptographic uses of SubtleCrypto .

Basic example
This example encodes a message, then calculates its SHA-256 digest and logs the digest length:
Converting a digest to a hex string
The digest is returned as an ArrayBuffer , but for comparison and display digests are often represented as hex strings. This example calculates a digest, then converts the ArrayBuffer to a hex string:
Specifications
Browser compatibility.
BCD tables only load in the browser with JavaScript enabled. Enable JavaScript to view data.
- Non-cryptographic uses of SubtleCrypto
- Chromium secure origins specification
- FIPS 180-4 specifies the SHA family of digest algorithms.
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
Web Cryptography API Examples Demo: https://diafygi.github.io/webcrypto-examples/
diafygi/webcrypto-examples
Folders and files, repository files navigation, web cryptography api examples.
Live Table: https://diafygi.github.io/webcrypto-examples/
I couldn't find anywhere that had clear examples of WebCryptoAPI, so I wrote examples and made a live table with them. Pull requests welcome!
RSASSA-PKCS1-v1_5
- generateKey | importKey | exportKey | sign | verify
- generateKey | importKey | exportKey | encrypt | decrypt | wrapKey | unwrapKey
- generateKey | importKey | exportKey | deriveKey | deriveBits
- generateKey | importKey | exportKey | wrapKey | unwrapKey
- SHA-1 digest | SHA-256 digest | SHA-384 digest | SHA-512 digest
- importKey | deriveKey | deriveBits
- generateKey | importKey | deriveKey | deriveBits
RSASSA-PKCS1-v1_5 - generateKey
Rsassa-pkcs1-v1_5 - importkey, rsassa-pkcs1-v1_5 - exportkey, rsassa-pkcs1-v1_5 - sign, rsassa-pkcs1-v1_5 - verify, rsa-pss - generatekey, rsa-pss - importkey, rsa-pss - exportkey, rsa-pss - sign, rsa-pss - verify, rsa-oaep - generatekey, rsa-oaep - importkey, rsa-oaep - exportkey, rsa-oaep - encrypt, rsa-oaep - decrypt, rsa-oaep - wrapkey, rsa-oaep - unwrapkey, ecdsa - generatekey, ecdsa - importkey, ecdsa - exportkey, ecdsa - sign, ecdsa - verify, ecdh - generatekey, ecdh - importkey, ecdh - exportkey, ecdh - derivekey, ecdh - derivebits, aes-ctr - generatekey, aes-ctr - importkey, aes-ctr - exportkey, aes-ctr - encrypt, aes-ctr - decrypt, aes-ctr - wrapkey, aes-ctr - unwrapkey, aes-cbc - generatekey, aes-cbc - importkey, aes-cbc - exportkey, aes-cbc - encrypt, aes-cbc - decrypt, aes-cbc - wrapkey, aes-cbc - unwrapkey, aes-cmac - generatekey, aes-cmac - importkey, aes-cmac - exportkey, aes-cmac - sign, aes-cmac - verify, aes-gcm - generatekey, aes-gcm - importkey, aes-gcm - exportkey, aes-gcm - encrypt, aes-gcm - decrypt, aes-gcm - wrapkey, aes-gcm - unwrapkey, aes-cfb - generatekey, aes-cfb - importkey, aes-cfb - exportkey, aes-cfb - encrypt, aes-cfb - decrypt, aes-cfb - wrapkey, aes-cfb - unwrapkey, aes-kw - generatekey, aes-kw - importkey, aes-kw - exportkey, aes-kw - wrapkey, aes-kw - unwrapkey, hmac - generatekey, hmac - importkey, hmac - exportkey, hmac - sign, hmac - verify, dh - generatekey, dh - importkey, dh - exportkey, dh - derivekey, dh - derivebits, sha-1 - digest, sha-256 - digest, sha-384 - digest, sha-512 - digest, concat - importkey, concat - derivekey, concat - derivebits, hkdf-ctr - importkey, hkdf-ctr - derivekey, hkdf-ctr - derivebits, pbkdf2 - generatekey, pbkdf2 - importkey, pbkdf2 - derivekey, pbkdf2 - derivebits, contributors 7.
- HTML 100.0%
webcrypto 0.5.6 webcrypto: ^0.5.6 copied to clipboard
Cross-platform implementation of Web Cryptography APIs for Flutter.
Cross-Platform Web Cryptography Implemenation #
This package provides a cross-platform implementation of the Web Cryptograph API .
Disclaimer: This is not an officially supported Google product.
This packages provides an implementation of the Web Cryptograph API across multiple platforms. Outside the browser, this package features a native implementation embedding BoringSSL using dart:ffi . When used inside a web browser this package wraps the window.crypto APIs and providing the same Dart API as the native implementation.
This way, package:webcrypto provides the same crypto API on Android , iOS , Web , Windows , Linux and Mac .
- Get random bytes
- Digest (sha-1/sha-256/sha-384/sha-512)
- HMAC (sign/verify)
- RSASSA-PKCS1-v1_5 (sign/verify)
- RSA-PSS (sign/verify)
- ECDSA (sign/verify)
- RSA-OAEP (encrypt/decrypt)
- AES-CTR, AES-CBC, AES-GCM (encrypt/decrypt)
- ECDH (deriveBits)
- HKDF (deriveBits)
- PBKDF2 (deriveBits)
- BoringSSL, Chrome and Firefox implementations pass the same test cases.
- Exceptions and errors thrown for invalid input is not tested yet.
- The native implementation executes on the main-thread, however, all expensive APIs are asynchronous, so they can be offloaded in the future.
For a discussion of the API design of this package, see doc/design-rationale-md .
Use with flutter test #
Unlike most plugins it is possible to run code that uses package:webcrypto with flutter test . For this to work the native library must be built in the application folder where flutter test is called. This can be done with:
This requires:
- a C compiler (like gcc or clang )
- Linux or Mac.
The native library will be stored in .dart_tool/webcrypto/ which should not be under source control.
It is also possible to run tests with Flutter Web using flutter test -p chrome , this does not require any additional setup steps.
Limitations #
This package has a few limitations compared to the Web Cryptograph API . For a discussion of parity with Web Cryptography APIs see doc/webcrypto-parity.md .
- deriveKey is not supported, however, keys can always be created from derivedBits which is supported.
- wrapKey is not supported, however, keys can be exported an encrypted.
- unwrapKey is not supported, however, keys can be decrypted and imported.
- AES-KW is not supported because it does not support encrypt / decrypt .
Compatibility notes #
This package has many tests cases to asses compatibility across the native implementation using BoringSSL and various browser implementations of the Web Cryptography APIs.
At the moment compatibility testing is limited to native implementation, Chrome, Firefox and Safari.
Known Issues:
- Chrome and BoringSSL does not support valid ECDH spki-formatted keys exported by Firefox prior to version 72.
- Firefox does not support PKCS8 import/export for ECDSA and ECDH keys.
- Firefox does not handle counter wrap around for AES-CTR .
- Safari does not support P-521 for ECDSA and ECDH.
- The browser implementation of streaming methods for encryption , decryption , signing and verification buffers the entire input, because window.crypto does not expose a streaming API. However, the native implementation using BoringSSL does support streaming.
References #
- Web Cryptograpy Specification .
- MDN Web Crypto API .
- Chromium Web Crypto Source .
- BoringSSL Source .
- BoringSSL Documentation .
Repository (GitHub) View/report issues Contributing
Documentation
API reference
Dependencies
ffi , flutter , flutter_web_plugins , meta
Packages that depend on webcrypto
- Home New Posts Forum List Trending New Threads New Media Spy
- WikiPost Latest summaries Watched WikiPosts
- Support FAQ and Rules Contact Us
Webcrypto Master Key
- Thread starter StarShot
- Start date Apr 24, 2023
- Sort by reaction score
- macOS Ventura (13)
macrumors 65816
- Apr 24, 2023
Somehow I go webcrypto master key running in my brand new Macbook Pro 16. Last night I watch a couple of NetFlix video with no problem. Today I booted up Netflix and got the following message, "Friendly steaming wants to access key "Friendly Streaming Webcrypto Master Key" in your keychain". To allow this, enter the "login" keychain password. Allows allow, Deny, or Allow. None of these options work for me and I haven't any idea as to what the password is. I've only be using this new laptop for a couple of weeks and am in the process of setting it up. Do you think if I uninstall "Friendly streaming" and then reinstalled it, the problem would go away? Any help would be appreciated greatly!
macrumors 6502a
This dialog is asking you for YOUR login password for the account, not for the webcrypto master key itself. Your login password is used to unlock the keychain and give access to the key stored there to this application. Considering the name of this key and my complete lack of understanding what "Friendly steaming" and this key are for, I would be bit worried to suggest you give this access. I am bit suspicious about this whole thing. Calling anything "webcrypto" seems poor choice or words. Do you know that this is safe?
Honza1 said: This dialog is asking you for YOUR login password for the account, not for the webcrypto master key itself. Your login password is used to unlock the keychain and give access to the key stored there to this application. Considering the name of this key and my complete lack of understanding what "Friendly steaming" and this key are for, I would be bit worried to suggest you give this access. I am bit suspicious about this whole thing. Calling anything "webcrypto" seems poor choice or words. Do you know that this is safe? Click to expand...
macrumors 68030
Honza1 said: Calling anything "webcrypto" seems poor choice or words. Do you know that this is safe? Click to expand...
StarShot said: I think I'm going to bite the bullet and do a clean install on my new MBP 16" M1 and TOTALLY staying away from webcrypto Click to expand...
macrumors newbie
- Apr 25, 2023
StarShot said: Somehow I go webcrypto master key running in my brand new Macbook Pro 16. Last night I watch a couple of NetFlix video with no problem. Today I booted up Netflix and got the following message, "Friendly steaming wants to access key "Friendly Streaming Webcrypto Master Key" in your keychain". To allow this, enter the "login" keychain password. Allows allow, Deny, or Allow. None of these options work for me and I haven't any idea as to what the password is. I've only be using this new laptop for a couple of weeks and am in the process of setting it up. Do you think if I uninstall "Friendly streaming" and then reinstalled it, the problem would go away? Any help would be appreciated greatly! Click to expand...
- Apr 26, 2023
thank you, I'll give it a try...
StarShot said: thank you, I'll give it a try... Click to expand...
Greyfriars Hall

The idea of formal seminary education dies hard. We have trained so many generations of ministers in this fashion that we can scarcely credit any other way of doing it
The idea of formal seminary education dies hard. We’ve trained so many generations of ministers in this fashion that we can scarcely credit any other way of doing it. Click here to learn more about our vision for pastoral training.

Greyfriars Hall is a ministerial training program which aims to prepare men for serving the Church. As such, the courses necessarily revolve around three main themes: Purity of Life, Boldness in Preaching, & Truth as Foundation.

Our faculty is comprised of men who have a wealth of pastoral experience, insight and wisdom. Class sizes are small so students can glean from our Faculty’s years of knowledge. Their pastoral wisdom is a rich augment to the training process.

For those men who are interested in beginning the process of pursuing pastoral ministry training through Greyfriars Hall: APPLY HERE.

GREYFRIARS HALL Pastoral Ministry Training
Under the oversight of Christ Church’s board of elders, Greyfriars Hall is approximately three years of rigorous study, ministry training, and biblical mentoring for men called to pastoral ministry. Though it is not a degree program, a letter from Greyfriars Hall commending them to the work of Christian ministry will be given upon successful completion.

Safari Pearl is your source on the Palouse for comics, games, costumes, and theatrical make-up. Our selection of comics and graphic novels offer captivating stories for every taste, age, and reading level. We also have a great selection of board games, card games, role-playing games, 40K, and Age of Sigmar. Games are a great entertainment value, they bring people together, and they build brain power. Feel free to try a game or join an event in our store game room. Safari Pearl is also your local, year-round source for costumes, cosplay, and stage make-up. We can supply everything you need for your theatrical production, we'll happily help you plan a theme party, and we love Halloween...
Shop Our Web Store - Browse Our Pokemon And Magic Singles
Calendar Of Events - Safari Pearl Customer Wish List
Send An eGift Card - Check Your Gift Card Balance
Safari Pearl 660 W Pullman Rd Moscow, ID 83843 Monday - Saturday 11:00 am - 7:00 pm Sunday Noon - 5:00 pm 208-882-9499 - [email protected] Map it!

IMAGES
VIDEO
COMMENTS
The concrete numbers for all selected parties are: 999 for prefixed WebKit, 46653 for Safari 11, 45709 for Chrome 59, and 18636 for FireFox 54. 2. DER encoding support for importing and exporting asymmetric keys. The WebCrypto API specification supports DER encoding of public keys as SPKI, and of private key as PKCS8.
mulberry58 Author. Level 6. 10,157 points. Jan 19, 2020 1:19 PM in response to jeremy_v. Thanks! I was wondering how it came in my keychain. If I double click on it, it gives as account : com.apple.WebKit.WebCrypto.master+com.apple.Safari. Under 'remarks' it says: They are used for coding WebCrypto-keys in persistent storage, such as IndexedDB.
The Web Crypto API is an interface allowing a script to use cryptographic primitives in order to build systems using cryptography. Warning: The Web Crypto API provides a number of low-level cryptographic primitives. It's very easy to misuse them, and the pitfalls involved can be very subtle. Even assuming you use the basic cryptographic ...
It powers Apple's Safari web browser as well as Chromium-based browsers like Google Chrome and Opera. ... WebCrypto encryption is able to encrypt a file at a speed of 1.33GB per second. By way ...
Preview the latest Safari and web technology updates including: Auto-Play improvements, WebAssembly, WebRTC, and Media Capture. Safari Technology Preview 31 Release Notes Preview the latest web technology updates including: Web API, JavaScript, Layout & Rendering, CSS Grid, Font Variations, Web Inspector, Media, Web Driver, WebCrypto, and Security.
I have the following code to test WebCrypto API. It works in Firefox and Chrome and I am trying to make it work in Safari. function ab2str(buf) { return String.fromCharCode.apply(null, new
WebCrypto. Added support for AES-CTR . Security. Changed private browsing sessions to not look in keychain for client certificates . AppleScript. Fixed an issue where Safari would throw an exception when evaluating JavaScript ending with an implied return value, where the final statement doesn't include the return keyword
Safari Technology Preview Release 42 is now available for download for macOS Sierra and macOS High Sierra. If you already have Safari Technology Preview installed, you can update from the Mac App Store's Updates tab. ... WebCrypto, Web API, Web Inspector, CSS, Rendering, Media, and bug fixes. Safari Technology Preview 24 Release Notes.
1 Support in IE11 is based on an older version of the specification. 2 Support in Safari before version 11 was using the crypto.webkitSubtle prefix. 3 In Edge 12-18, Web Crypto was not supported in Web Workers and Service Workers. "Can I use" provides up-to-date browser support tables for support of front-end web technologies on desktop and ...
The webcrypto key is automatically created by Apple's Webkit framework (supporting safari as well as Friendly Streaming). An update is on its way that fix this issue (submitted today to the AppStore Review team). In the meantime the best and most secure solution is to: 1- quit friendly
The digest () method of the SubtleCrypto interface generates a digest of the given data. A digest is a short fixed-length value derived from some variable-length input. Cryptographic digests should exhibit collision-resistance, meaning that it's hard to come up with two different inputs that have the same digest value.
Supported browsers. The library is targeted to fix these browsers having prefixed and buggy webcrypto api implementations: Internet Explorer 11, Mobile Internet Explorer 11, Safari 8 - 10, iOS Safari 8 - 10. These browsers have unprefixed and conforming webcrypto api implementations, so no need in shim: Chrome 43+, Chrome for Android 44+,
Saved searches Use saved searches to filter your results more quickly
This way, package:webcrypto provides the same crypto API on Android, iOS, Web, Windows, Linux and Mac. ... Safari does not support P-521 for ECDSA and ECDH. The browser implementation of streaming methods for encryption, decryption, signing and verification buffers the entire input, ...
Adding an AirPlay button to your Safari media controls. To navigate the symbols, press Up Arrow, Down Arrow, Left Arrow or Right Arrow . 3 of 591 symbols inside <root> Adding Picture in Picture to your Safari media controls.
Does webcrypto allow me to change passwords (in my case a 4 digit number). G. gilby101 macrumors 68030. Mar 17, 2010 2,526 1,362 Tasmania. Apr 24, 2023 #4 ... you won't get away from WebCrypto which is used by Safari (and other browsers) without you knowing it! I suggest to contact the developers of Friendly Streaming Browser https://friendly ...
Pastoral Ministry Training. Under the oversight of Christ Church's board of elders, Greyfriars Hall is approximately three years of rigorous study, ministry training, and biblical mentoring for men called to pastoral ministry. Though it is not a degree program, a letter from Greyfriars Hall commending them to the work of Christian ministry ...
Russia, like many other countries, struggles with the problem of homelessness.Estimates of Russia's homeless population range from the thousands to millions....
Safari Pearl is your source on the Palouse for comics, games, costumes, and theatrical make-up. Our selection of comics and graphic novels offer captivating stories for every taste, age, and reading level. We also have a great selection of board games, card games, role-playing games, 40K, and Age of Sigmar.
Safari Pearl, Moscow, ID. 2,536 likes · 39 talking about this. Safari Pearl has everything you need to bring out the super-hero, pirate, or monster inside you!