Apple Platform Security
- Intro to Apple platform security
- Hardware security overview
- Apple SoC security
- Secure Enclave
- Face ID and Touch ID security
- Magic Keyboard with Touch ID
- Face ID, Touch ID, passcodes, and passwords
- Facial matching security
- Uses for Face ID and Touch ID
- Secure intent and connections to the Secure Enclave
- Hardware microphone disconnect
- Express Cards with power reserve
- System security overview
- Boot process for iOS and iPadOS devices
- Memory safe iBoot implementation
- Boot process
- Paired recoveryOS restrictions
- Startup Disk security policy control
- LocalPolicy signing-key creation and management
- Contents of a LocalPolicy file for a Mac with Apple silicon
- Startup Security Utility
- Firmware password protection
- recoveryOS and diagnostics environments
- Signed system volume security
- Secure software updates
- Operating system integrity
- Additional macOS system security capabilities
- System Integrity Protection
- Trust caches
- Peripheral processor security
- Rosetta 2 on a Mac with Apple silicon
- Direct memory access protections
- Kernel extensions
- Option ROM security
- UEFI firmware security in an Intel-based Mac
- System security for watchOS
- Random number generation
- Apple Security Research Device
- Encryption and Data Protection overview
- Passcodes and passwords
- Data Protection overview
- Data Protection
- Data Protection classes
- Keybags for Data Protection
- Protecting keys in alternate boot modes
- Protecting user data in the face of attack
- Sealed Key Protection (SKP)
- Activating data connections securely in iOS and iPadOS
- Role of Apple File System
- Keychain data protection
- Volume encryption with FileVault
- Managing FileVault
- Protecting app access to user data
- Protecting access to user’s health data
- Digital signing and encryption
- App security overview
- Intro to app security for iOS and iPadOS
- App code signing process
- Security of runtime process
- Supporting extensions
- App protection and app groups
- Verifying accessories
- Intro to app security for macOS
- Gatekeeper and runtime protection
- Protecting against malware
- Controlling app access to files
- Secure features in the Notes app
- Secure features in the Shortcuts app
- Services security overview
- Apple ID security
- Managed Apple ID security
- iCloud security overview
- iCloud encryption
- Advanced Data Protection for iCloud
- Security of iCloud Backup
- Account recovery contact security
- Legacy Contact security
- iCloud Private Relay security
- Passcode security overview
- Sign in with Apple security
- Automatic strong passwords
- Password AutoFill security
- App access to saved passwords
- Password security recommendations
- Password Monitoring
- Sending passwords
- Credential provider extensions
- iCloud Keychain security overview
- Secure keychain syncing
- Secure iCloud Keychain recovery
- Escrow security for iCloud Keychain
- Apple Pay security overview
- Apple Pay component security
- How Apple Pay keeps users’ purchases protected
- Card provisioning security overview
- Adding credit or debit cards to Apple Pay
- Payment authorization with Apple Pay
- Paying with cards using Apple Pay
- Contactless passes in Apple Pay
- Rendering cards unusable with Apple Pay
- Apple Card security
- Apple Cash security
- Tap to Pay on iPhone
- Access using Apple Wallet
- Access credential types
- Car key security
- Adding transit and eMoney cards to Apple Wallet
- IDs in Apple Wallet
- iMessage security overview
- How iMessage sends and receives messages
- Secure iMessage name and photo sharing
- Secure Apple Messages for Business
- FaceTime security
- Find My security
- Locating missing devices
- Continuity security overview
- Handoff security
- iPhone cellular call relay security
- iPhone Text Message Forwarding security
- Instant Hotspot security
- Network security overview

TLS security
- IPv6 security
- VPN security
- Secure access to wireless networks
- Wi-Fi privacy
- Bluetooth security
- Ultra Wideband security
- Single sign-on security
- AirDrop security
- Wi-Fi password sharing security
- Firewall security
- Developer kit security overview
- Communication security
- Data security
- Securing routers with HomeKit
- Camera security
- Security with Apple TV
- SiriKit security
- DriverKit security
- ReplayKit security
- ARKit security
- Secure device management overview
- Pairing model security
- MDM security overview
- Configuration profile enforcement
- Automated Device Enrollment
- Activation Lock security
- Managed Lost Mode and remote wipe
- Shared iPad security
- Apple Configurator security
- Screen Time security
- Document revision history
iOS, iPadOS, and macOS support Transport Layer Security (TLS 1.0, TLS 1.1, TLS 1.2, TLS 1.3) and Datagram Transport Layer Security (DTLS). The TLS protocol supports both AES128 and AES256, and prefers cipher suites with forward secrecy. Internet apps such as Safari, Calendar, and Mail automatically use this protocol to enable an encrypted communication channel between the device and network services. High-level APIs (such as CFNetwork) make it easy for developers to adopt TLS in their apps, while low-level APIs (such as Network.framework) provide fine-grained control. CFNetwork disallows SSL 3, and apps that use WebKit (such as Safari) are prohibited from making an SSL 3 connection.
In iOS 11 or later and macOS 10.13 or later, SHA-1 certificates are no longer allowed for TLS connections unless trusted by the user. Certificates with RSA keys shorter than 2048 bits are also disallowed. The RC4 symmetric cipher suite is deprecated in iOS 10 and macOS 10.12 . By default, TLS clients or servers implemented with SecureTransport APIs don’t have RC4 cipher suites enabled and are unable to connect when RC4 is the only cipher suite available. To be more secure, services or apps that require RC4 should be upgraded to use secure cipher suites. In iOS 12.1 , certificates issued after October 15, 2018, from a system-trusted root certificate must be logged in a trusted Certificate Transparency log to be allowed for TLS connections. In iOS 12.2 , TLS 1.3 is enabled by default for Network.framework and NSURLSession APIs. TLS clients using the SecureTransport APIs can’t use TLS 1.3.
App Transport Security
App Transport Security provides default connection requirements so that apps adhere to best practices for secure connections when using NSURLConnection, CFURL, or NSURLSession APIs. By default, App Transport Security limits cipher selection to include only suites that provide forward secrecy, specifically:
ECDHE_ECDSA_AES and ECDHE_RSA_AES in Galois/Counter Mode (GCM)
Cipher Block Chaining (CBC) mode
Apps are able to disable the forward secrecy requirement per domain, in which case RSA_AES is added to the set of available ciphers.
Servers must support TLS 1.2 and forward secrecy, and certificates must be valid and signed using SHA256 or stronger with a minimum 2048-bit RSA key or 256-bit elliptic curve key.
Network connections that don’t meet these requirements will fail unless the app overrides App Transport Security. Invalid certificates always result in a hard failure and no connection. App Transport Security is automatically applied to apps that are compiled for iOS 9 or later and macOS 10.11 or later.
Certificate validity checking
Evaluating the trusted status of a TLS certificate is performed in accordance with established industry standards, as set out in RFC 5280 , and incorporates emerging standards such as RFC 6962 (Certificate Transparency). In iOS 11 or later and macOS 10.13 or later, Apple devices are periodically updated with a current list of revoked and constrained certificates. The list is aggregated from certificate revocation lists (CRLs), which are published by each of the built-in root certificate authorities trusted by Apple, as well as by their subordinate CA issuers. The list may also include other constraints at Apple’s discretion. This information is consulted whenever a network API function is used to make a secure connection. If there are too many revoked certificates from a CA to list individually, a trust evaluation may instead require that an online certificate status response (OCSP) is needed, and if the response isn’t available, the trust evaluation will fail.
Download this guide as a PDF
Information Technology
Search form.
- Technology Help Desk
- How-To Articles
- IT Services Portal
- Ticket Status
- Feature Articles
- Alerts & Announcements
- Customer Success Stories
- In the News
- IT Events Calendar
- Report a Security Concern
- Accounts & Access
- Data Classification & Compliance
- Security Awareness Training
- Vendor Risk Assessment
- Services by Category
- Software for Faculty
- Software for Staff
- Software for Students
- Software for Research
- IT Training & Development
- On-Demand Learning
- Instructor-Led Training
- Training Content Development
- Tech Ambassadors
- About Pitt IT
- Office of the CIO
- Leadership Team
- IT Vision and Strategy
- Community Engagement
- IT 10-Year Horizon
You are here
Enable support for tls 1.2 or 1.3 on web browsers.
In keeping with security best practices, the University is requiring the use of current web browsers to ensure continued access to University web services—including Pitt Passport .
Older web browsers use out-of-date protocols that do not support modern encryption and contain security vulnerabilities that can be exploited by attackers. Effective July 1, 2021, only web browsers that support versions 1.2 or 1.3 of the Transport Layer Security (TLS) protocol will be permitted to access University web services. Browsers that use TLS version 1.0 or 1.1 will not be supported.
To ensure your web browser supports TLS 1.2 or 1.3, complete the steps below.
Microsoft Edge
TLS 1.2 is automatically enabled in all versions of Microsoft Edge.
Google Chrome
TLS 1.2 is automatically enabled in Google Chrome version 29 or greater.
- Ensure you are using the most recent version of Chrome ...
Apple Safari
TLS 1.2 is automatically enabled in Safari version 7 or greater.
- Ensure you are using the most recent version of Safari ...
Mozilla Firefox
TLS 1.2 is automatically enabled in Firefox version 27 or greater.
- Ensure you are using the most recent version of Firefox ...
To enforce TLS version 1.3 in Firefox, complete the steps below.
1. Open Firefox.
2. In the address bar, type about:config and press Enter .
3. In the Search field, enter tls . Find and double click the entry for security.tls.version.max .
4. Set the integer value to 4 to force a maximum protocol of TLS 1.3.

5. Click OK .
6. Close your browser and restart Mozilla Firefox.
Microsoft Internet Explorer
1. Open Internet Explorer.
2. From the menu bar, click Tools , then Internet Options , then click the Advanced tab.
3. Scroll down to the Security category and manually check the box next to Use TLS 1.2 .

4. Click OK .
5. Close your browser and restart Internet Explorer.
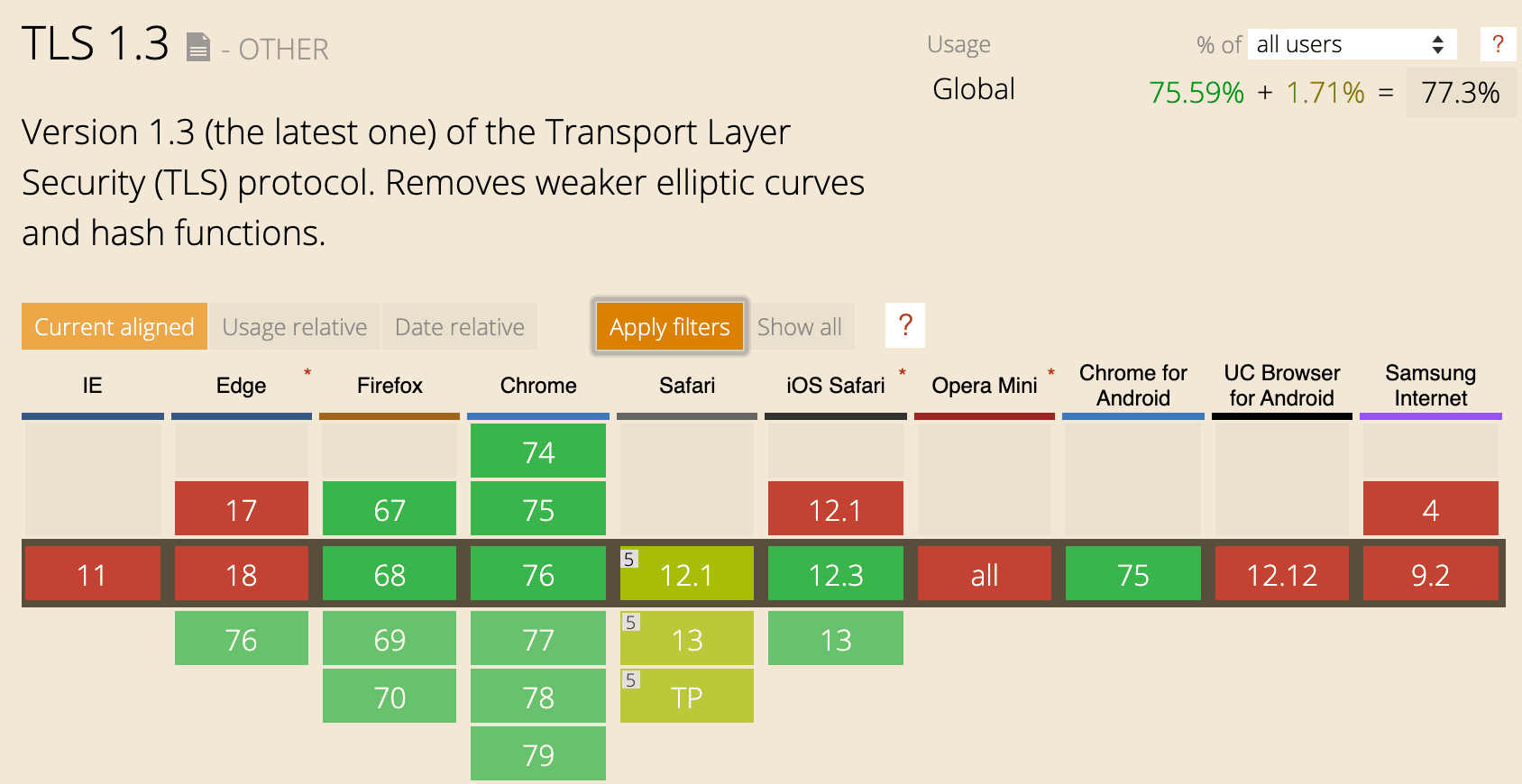
Version 1.3 (the latest one) of the Transport Layer Security (TLS) protocol. Removes weaker elliptic curves and hash functions.
Supports a draft of the TLS 1.3 specification, not the final version.
Can be enabled in Firefox by setting the security.tls.version.max pref to "4" in about:config .
Can be enabled in Chrome and Opera via the #tls13-variant flag in chrome://flags or opera://flags .
Partial support in Safari refers to being limited to macOS 10.14 Mojave and later.
- Wikipedia article about TLS 1.3
- Chrome support bug
Data by caniuse.com Licensed under the Creative Commons Attribution License v4.0. https://caniuse.com/tls1-3
Home » TLS 1.3: Everything you Need to Know
TLS 1.3: Everything you Need to Know

The ability to provide secure data transfers and convey information over the internet without having it interfered with, altered, used illegally, or read by anyone other than the intended users has become a significant concern for many electronic commerce and online organizations in today’s digital era. These worries have made it necessary to upgrade a variety of internet security mechanisms.
The TLS 1.3 update, which represents a significant step from the transport layer security protocol (TLS) and secure sockets layer (SSL) encryption protocols, is an essential advancement over the current security standard.
The upgraded version was created to avoid exposing the flaws and vulnerabilities present in other previous versions of encryption, and it was approved by the Internet Engineering Task Force (IETF). Numerous advantages of TLS 1.3 include a clear protocol flow, better cryptographic primitives, and increased speed and performance.
TLS 1.3 and its advantages will be thoroughly explained in this article. Let’s first discuss the Transport Layer Security Protocol (TLS) before moving on.
What Is Transport Layer Security Protocol (TLS)?
The term “TLS,” or transport security protocol, refers to the cryptographic protocols that enable secure internet connections. TLS makes data security and privacy for conversations across a computer network easier.
TLS was created from SSL and is frequently used in place of TLS. Every website and certain online services use HTTPS, an application of TLS encryption built on top of the HTTP protocol. Web applications are protected from hazards like DDoS attacks and data breaches with the help of the transport layer security encryption protocol.
The goal is to stop an intermediary from accessing the current packets and obtaining sensitive information (such as usernames, passwords, financial information, personal material, etc.) since cryptographic encryption ensures all data is unreadable to outsiders.
What is TLS 1.3 Encryption?
TLS 1.3 is the internet’s most widely used security protocol, which encrypts data to create a secure mode of communication between two endpoints. TLS 1.3 strives to encrypt as much of the handshake as feasible, replaces outdated cryptographic techniques, and improves security over earlier versions.
TLS 1.2 vs TLS 1.3: What are the Main Differences?
The Internet Engineering Task Force (IETF) defined the TLS protocol, which has undergone several versions. Most web browsers have used the TLS 1.2 protocol, the most recent version of TLS, for the past eight years.
TLS 1.2 was described in RFC 5246. The TLS 1.3 specification had 28 drafts before being finalized on March 21st, 2018. The final iteration of TLS 1.3 has since been published (RFC 8446) as of August 2018
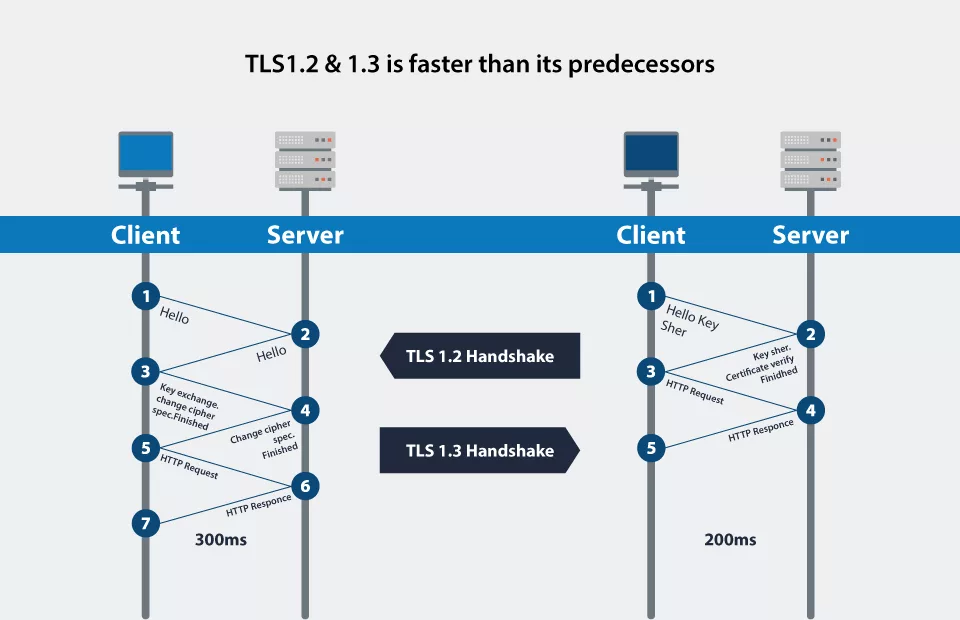
TLS 1.3 delivers many improvements over earlier versions, with the fastest TLS handshake and the most simple, secure cipher suites. TLS handshake efficiency is increased via zero-round-trip-time (0-RTT) key transfers. These modifications strengthen security and improve performance when taken together.
Browsers and operating systems are responsible for adding support for new versions of protocols when they are released. Therefore, they are incentivized to do so; operating systems and browsers should all strive for increased performance and security.
However, it may take time until new protocols are widely supported, mainly as private companies and customers might be cautious about utilizing the most recent browsers, apps, and operating systems.
What Benefits Come with Utilizing the Most Recent TLS Version?
Choose TLS 1.3 if you’re creating an application and need help deciding which TLS version you should use. Significant advancements in the most recent TLS version include:
Zero Round-Trip Time (0-RTT)
Client application data, also known as 0-RTT data, can be sent to the Server after the ClientHello message and has zero round-trip time by the TLS 1.3 protocol.
The time to the first byte on a TLS connection can be lowered using TLS 0-RTT, commonly called “ TLS early data ” In contrast to TLS 1.2 and earlier versions, TLS 1.3 only needs one RTT (single round trip) of the protocol.
A Quicker TLS Handshake
TLS encryption and SSL decryption slow down network connections by adding latency and requiring CPU resources. The initial handshake required encryption and decryption under TLS 1.2 since it was conducted in plain text.
Recommended: SSL/TLS Handshake: A Crucial Step Towards Secure Connections
Given that a handshake typically included 5–7 packets being transmitted between the client and server, this significantly increased connection overhead. With the introduction of server certificate encryption in version 1.3, a TLS handshake may be finished in 0–3 packets, decreasing or eliminating this overhead and enabling more rapid and more responsive connections.
Robust and Better Cipher Suites
Version 1.3 has reduced the size of the encryption cipher suites and lowered the number of packets that must be sent during the TLS handshake.
Using ciphers with cryptographic weaknesses presented possible security issues in TLS 1.2 and older versions. Only algorithms that do not enable Perfect Forward Secrecy (PFS) that are known to be secure are supported by TLS 1.3.
The update also removed the “ renegotiation ” mechanism, which allows a client and Server with a TLS connection to negotiate new parameters and create new keys. Renegotiation could increase risk.
TLS 1.3’s Enhanced Security
TLS 1.2 has a significant weakness: it is frequently not configured correctly, leaving websites open to attackers.
From TLS 1.2, the following features have been removed by TLS 1.3 because they are no longer necessary or secure: AES-CBC, MD5, SHA-1, RC4, DES, and 3DES, Arbitrary Diffie-Hellman groups — CVE-2016-0701. It is less probable for administrators and developers to misconfigure the protocol because it has been considerably simplified.
Google has begun informing consumers in the search console that they are switching to TLS version 1.2 since TLS version 1 is no longer considered secure. This scenario is another example of Google raising the bar. March 2018 has been set as the ultimate deadline.
Ultimate Advance Secrecy
Perfect forward secrecy is a characteristic of SSL/TLS that prohibits an attacker from being able to decode the data from previous or future sessions if they are successful in stealing the private keys used in a specific session.
Forward secrecy is likely to protect against cybercriminals who put in a lot of effort to see or steal data that has already been sent between a client and Server using a compromised private key. Unique session keys are used for forward secrecy and are regularly and automatically produced. Encrypting the data received during the handshake and decrypting it prevents an attacker from getting the session key.
TLS 1.3’s Browser Support
Since Chrome 65, a draft of TLS 1.3 has been delivered by Chrome. TLS 1.3 final was made available for outbound connections in Chrome 70, which was made public in October 2018.
In Firefox 52 and later (including Quantum), a draft version of TLS 1.3 was made available. Before learning more about server tolerance and the 1.3 handshake, they were still using a risky fallback to TLS 1.2. The most recent TLS 1.3 version was preloaded in Firefox 63, released in October 2018.
TLS 1.3 is enabled by default in Safari 12.1 on macOS 10.14.4, and Microsoft Edge began supporting it with version 76.
Difference Between TLS 1.2 and TLS 1.3:
Due to numerous benefits of the TLS 1.2 protocol, such as enhanced performance, security, and zero round trip time, the TLS 1.3 protocol is more likely to be utilized in today’s world.
Although TLS version 1.2 is still in use, there is a growing trend towards TLS version 1.3 because of the version’s ease of use, enhanced performance, data privacy, and security. TLS 1.3 offers a quicker connection, lowering latency when adequately implemented. The speed and user experience of websites are enhanced by reduced latency.
Client-server communications can be made considerably secure by eliminating vulnerable components, simplifying cipher suites, and other weaknesses in security. Organizations should consider maintaining both versions for secure data transfers with legacy systems and apps for a while because TLS 1.3 is not backward compatible with TLS 1.2.
The upgrade from TLS 1.2 to TLS 1.3 is a significant leap. However, choosing to update is simple if your organization wants to increase client confidence while enhancing website performance and security.
FAQ’s
How is tls 1.3 work.
Each session in TLS 1.3 begins with a brief key exchange. There will be no impact on earlier sessions if a server is hacked. After exchanging ephemeral public keys, key exchange is completed, and new keys can be generated.
Does TLS 1.3 Encrypt the Certificate?
When server certificate encryption became the default in version 1.3, a TLS handshake could be completed in as few as three packets, lowering or eliminating this cost and enabling quicker, more responsive connections.
Why is TLS 1.3 More Rapid?
On the other hand, the TLS 1.3 handshake only needs one round trip from both sides. As a result, HTTPS connections are quicker and more responsive, and the whole setup time has been reduced in half. In addition to improving website speed, faster connections significantly improve user experience.
Does TLS 1.3 use AES?
Every TLS 1.3 implementation must use AES-128-GCM-SHA256. However, AES-256-GCM-SHA384 and CHACHA20-Poly1305-SHA256 are also recommended.
Why doesn’t TLS 1.3 use RSA?
All static (non-PFS) key exchanges and RSA have been removed in TLS 1.3, however ephemeral Diffie-Hellman keys are still used.

Janki Mehta
Janki Mehta is a passionate Cyber-Security Enthusiast who keenly monitors the latest developments in the Web/Cyber Security industry. She puts her knowledge into practice and helps web users by arming them with the necessary security measures to stay safe in the digital world.
EncryptedFence Blog
Subscribe to our newsletter.
Never miss any Update on Cyber Security
We respect your privacy and we will not use your email for spam!
Enjoy 2 months of free hosting with an annual WordPress plan. 30-day money-back guarantee.
An Overview of TLS 1.3 – Faster and More Secure

It has been over eight years since the last encryption protocol update, but the final version of TLS 1.3 has now been published as of August 2018 . 👏 The exciting part for the WordPress community and customers here at Kinsta is that TLS 1.3 includes a lot of security and performance improvements. With the HTTP/2 protocol update in late 2015, and now TLS 1.3 in 2018, encrypted connections are now more secure and faster than ever. Read more below about the changes with TLS 1.3 and how it can benefit you as a WordPress site owner.
What is TLS?
TLS stands for Transport Layer Security and is the successor to SSL (Secure Sockets Layer). TLS provides secure communication between web browsers and servers. The connection itself is secure because symmetric cryptography is used to encrypt the data transmitted. The keys are uniquely generated for each connection and are based on a shared secret negotiated at the beginning of the session, also known as a TLS handshake.
Many IP-based protocols, such as HTTPS, SMTP , POP3, FTP support TLS to encrypt data.
Web browsers utilize an SSL certificate which allows them to recognize that it belongs to a digitally signed certificate authority. Technically these are also known as TLS certificates, but most SSL providers stick with the term “SSL certificates” as this is generally more well known.
SSL/TLS certificates provide the magic behind what many people simply know as the HTTPS that they see in their browser’s address bar.
TLS 1.3 vs TLS 1.2
Speed benefits of tls 1.3, improved security with tls 1.3, tls 1.3 browser support, tls 1.3 server support, kinsta tls 1.3 support.
The Internet Engineering Task Force (IETF) is the group that has been in charge of defining the TLS protocol, which has gone through many various iterations. The previous version of TLS, TLS 1.2, was defined in RFC 5246 and has been in use for the past eight years by the majority of all web browsers . On March 21st, 2018, TLS 1.3 has was finalized , after going through 28 drafts. And as of August 2018, the final version of TLS 1.3 is now published ( RFC 8446 ).
Companies such as Cloudflare are already making TLS 1.3 available to their customers. Filippo Valsorda had a great talk (see presentation below) on the differences between TLS 1.2 and TLS 1.3. In short, the major benefits of TLS 1.3 vs that of TLS 1.2 is faster speeds and improved security .
TLS and encrypted connections have always added a slight overhead when it comes to web performance. HTTP/2 definitely helped with this problem, but TLS 1.3 helps speed up encrypted connections even more with features such as TLS false start and Zero Round Trip Time (0-RTT).
To put it simply, with TLS 1.2, two round-trips have been needed to complete the TLS handshake . With 1.3, it requires only one round-trip , which in turn cuts the encryption latency in half. This helps those encrypted connections feel just a little bit snappier than before.
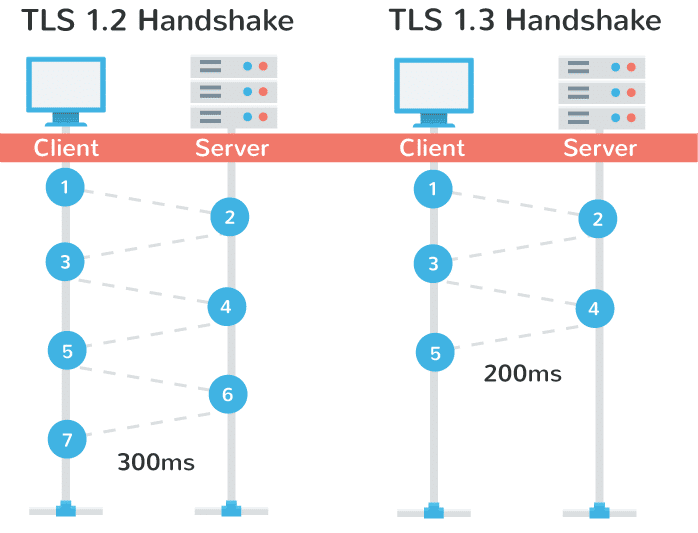
Another advantage of is that in a sense, it remembers ! On sites you have previously visited, you can now send data on the first message to the server. This is called a “zero round trip.” (0-RTT). And yes, this also results in improved load time times.
TLS 1.3 is much faster than 1.2…. RUM data (30days) showing median TLS handshake times #webperf #isTLSFastYet pic.twitter.com/Mc4RHwg8Vt — Tim Vereecke (@TimVereecke) May 16, 2019
A big problem with TLS 1.2 is that it’s often not configured properly it leaves websites vulnerable to attacks. TLS 1.3 now removes obsolete and insecure features from TLS 1.2, including the following:
- Arbitrary Diffie-Hellman groups — CVE-2016-0701
- EXPORT-strength ciphers – Responsible for FREAK and LogJam
Because the protocol is in a sense more simplified, this makes it less likely for administrators and developers to misconfigure the protocol. Jessie Victors, a security consultant, specializing in privacy-enhancing systems and applied cryptography stated :
I am excited for the upcoming standard. I think we will see far fewer vulnerabilities and we will be able to trust TLS far more than we have in the past.
Google is also raising the bar, as they have started warning users in search console that they are moving to TLS version 1.2, as TLS 1 is no longer that safe. They are giving a final deadline of March 2018.
Chrome has been shipping a draft version of TLS 1.3 since Chrome 65. In Chrome 70 (released in October 2018), the final version of TLS 1.3 was enabled for outgoing connections.
A draft version of TLS 1.3 was enabled in Firefox 52 and above (including Quantum). They have been retaining an insecure fallback to TLS 1.2 until they knew more about server tolerance and the 1.3 handshake. Firefox 63 (released in October 2018) shipped with the final version fo TLS 1.3.
Microsoft Edge started supporting TLS 1.3 with version 76, and it’s enabled by default in Safari 12.1 on macOS 10.14.4.
With that being said some SSL test services on the Internet don’t support TLS 1.3 yet and neither do other browsers such as IE or Opera mobile.
It might be a while for the rest of the browsers to catch up. Most of the remaining ones are in development at the moment. Cloudflare has an excellent article on why TLS 1.3 isn’t in browsers yet .
However, as of September 11, 2018, TLS 1.3 surpassed TLS 1.0 as the second most used version at Cloudflare.
Guess what happened today? TLS 1.3 surpassed TLS 1.0 as the second-most common version of TLS seen by Cloudflare. #tls13 pic.twitter.com/ASzgNaUIy0 — Nick Sullivan (@grittygrease) September 11, 2018
If you’re curious whether or not your server or host supports TLS 1.3 yet you can use the SSL Server Test tool. Simply scan your domain and scroll down to the “Protocol Features” section. It will say either yes or no.
In August 2019, we added TLS 1.3 support to all of our servers. 🔒 You can now take full advantage of the web performance and security benefits of TLS 1.3 .
Just like with HTTP/2, TLS 1.3 is another exciting protocol update that we can expect to benefit from for years to come. Not only will encrypted (HTTPS) connections become faster, but they will also be more secure. Here’s to moving the web forward! If you’re using legacy TLS versions, you might want to fix ERR_SSL_OBSOLETE_VERSION notifications in Chrome.
Brian has a huge passion for WordPress, has been using it for over a decade, and even develops a couple of premium plugins. Brian enjoys blogging, movies, and hiking. Connect with Brian on Twitter .
Related Articles and Topics

Free SSL Certificates and Hosting From Kinsta

In-Depth HTTP to HTTPS Migration Guide for WordPress
- Application Development
- Content Management Systems
Safari supports it in version 11.1 on macOS High Sierra, but TLS 1.3 is disabled by default. It can be enabled by running the following Terminal command: sudo defaults write /Library/Preferences/com.apple.networkd tcp_connect_enable_tls13 1
Thanks Jon! I’ve updated the post above with a note about being able to enable TLS 1.3 on macOS.
My computer marks error when oppening some websites, like mail ans stuff, saying its because of TSL 1.3. Why is this happening? It was safe minutes ago
Kaspersky would not allow me to access my Gmail account on Browsers with TLS 1.3 on my desktop with Windows 10. The errors that I was getting on Firefox and Chrome said that Gmail was not a secure connection. It had to be downgraded to TLS 1.2.
UPDATE: Safari supports it on macOS 10.14.4 and newer, as well as iOS 12.2 and newer.
Thanks Jon! We’ve updated the post above with information regarding TLS 1.3 and Safari support.
Can you send me the components and operating principle of TLS 1.3? I want to take a closer look at this version.
Performance of TLS 1.3 is clearly explained about taking away one round trip in the initial handshake and also zero round trip for returning clients. That’s all between the server and the client. The client can be Cloudflare or another CDN like Sucuri or at Kinsta KeyCDN or a direct web connection.
Cloudflare implemented free TLS origin CA certificates to enhance performance & security even more between the server and Cloudflare. Also at entreprise levels $200 or more accounts a trusted CA certificate can be entered to put the SSL/TLS encryption mode on Full (strict). According to Cloudflare and their white paper it’s even more secure and performing.
One side of the TLS/SSL handshake that has a major impact on the performance of TLS/SSL and that’s not discussed or considered anywhere in this document is the verification or validation of certificate made by the browser or establishment of trust. The keychain. If browser doesn’t have the Certificate Authority in it’s database it verifies by going up the keychain it can go up the keychain to establish trust on the certificate. With all the free certificates available now a hacker can have a website up and running with TLS/SSL.
Being that performance is somewhat of an obsession for me and it seem’s Kinsta also. To my understanding so far purchasing a high trust or short keychain certificate will reduce browser delays in verification of certificate trust. That’s why Symantec sells basic certificates for crazy high prices. Organisation validation certificates imply high trust for the browser and higher certificates.
We’ve all seen variations in time to first byte connection and SSL that are perplexing in waterfall charts. It’s simply to my understanding browser validation or establishment of trust of the supplied certificate and the additional lookups or crawling up the keychain that the browser does prior to establishing the TLS/SSL connection.
It brings the question of how much difference in performance or reduction of connection times that short keychain or high trust Certificate Authority purchased TLS certificates give?
Leave a Reply Cancel reply
By submitting this form: You agree to the processing of the submitted personal data in accordance with Kinsta's Privacy Policy , including the transfer of data to the United States.
You also agree to receive information from Kinsta related to our services, events, and promotions. You may unsubscribe at any time by following the instructions in the communications received.
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
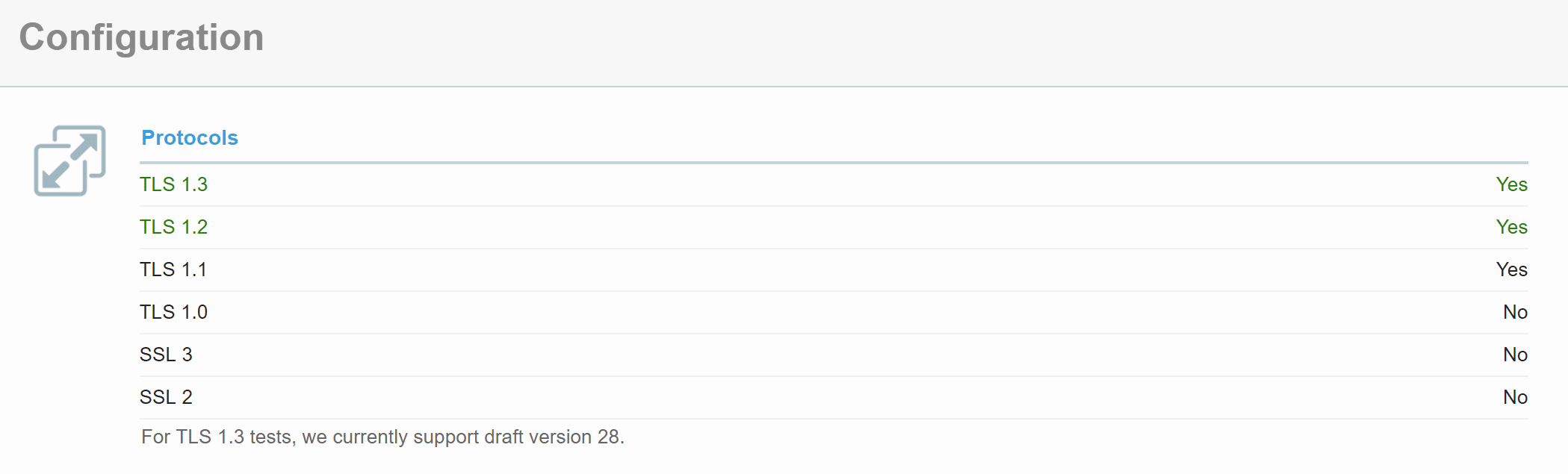
How do I enable TLS 1.3 in iOS and MacOS?
It's reported that TLS 1.3 (currently in draft status) can reduce connection setup delays by 30% or approximately 30ms.
How can I configure this on MacOS or iOS?
According to WWDC2017:
TLS 1.3 is not enabled by default
You can enable this on iOS with this provisioning profile
You can enable this on MacOS with this command in Terminal
sudo defaults write /Library/Preferences/com.apple.networkd tcp_connect_enable_tls13 1
- can you please share the wwdc link for this? – Ankit Kumar Gupta Aug 6, 2018 at 4:41
- It's in session 709 (Advances in Networking, Part 2) around minute 37:29 in the session: developer.apple.com/videos/play/wwdc2017/701/?time=2249 – mat Oct 24, 2018 at 12:46
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged macos iphone tls ..
- The Overflow Blog
- Is GenAI the next dot-com bubble?
- What language should beginning programmers choose?
- Featured on Meta
- New Focus Styles & Updated Styling for Button Groups
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network
- Google Cloud will be Sponsoring Super User SE
Hot Network Questions
- How to plan a trail route?
- Rock as a heat sink
- Do parabolic inductions share a composition factor if and only if the inducing data are associate?
- How do I programmatically check if a Flatpak package is installed in a shell script?
- How much latency is acceptable in an amplification system for singing?
- Is Batman's utility belt ever missing something he needs?
- How to answer pre screening question "do you have a car" if I currently don't but could get one?
- What would be the grounds for the US Chamber of Commerce to sue the FTC over its new rule concerning noncompetes?
- Could anyone translate these characters for me on what I think is a Ming Taoist figure
- Jawohl answer when someone knocks at the door
- めったに without a negative?
- 4,4,2,6,2,10,4,_ sequence from 4th grade packet
- How can a senior finance building a home with no current credit score but good equity in current home?
- Windows Batch Script: how to recursively go through all files except certain file types and folders?
- Order of an RC circuit and independent initial conditions
- Is Quantum Gravity research implying that gravity is actually a force and not spacetime curvature according to GR?
- Why is a post-measurement state a valid quantum state?
- A genius Margonon!
- Is this job a scam or legit?
- Latin minimal pairs, distinguished only by the length of the vowel in an unstressed non-last syllable
- Need help with a timeline using Tikz
- Are there any philosophies related to different structures of organization of information?
- Unable to Understand How Current Divides in Parallel Circuits
- Is my simpler proof correct?

- Guides and Tutorials
- Setup and How-to Guides
- TLS 1.3 Guide
The Complete and Easy Guide to TLS1.3
Transport Layer Security (TLS) provides the foundation for encryption in-flight. The first version of TLS, 1.0, replaced Secure Sockets Layer (SSL) in 1999. The latest version, 1.3, was finalized as a proposed standard in RFC 8446 in December of 2018. With it, comes enhancements in both speed and security.
One of the biggest differences between TLS 1.2 and TLS 1.3 is that perfect forward secrecy (PFS) is no longer a decision made at the cipher level. TLS 1.3 by definition implements PFS. PFS uses a constantly rotating key so that even in the event of a private key compromise, communication cannot be decrypted by a third party. To do this, TLS 1.3 drops support for an unprecedented number of legacy ciphers and encryption options including RC4 ciphers, SHA1, and MD5. It also completely drops support for TLS renegotiation (which defines what happens when the client or server try to send data after the other side thinks the session is expired). This secondary negotiation mechanism was frequently abused over the years. TLS 1.3 does this by removing the need for renegotiation entirely by removing an entire round trip from the initial negotiation.
TLS 1.3 is a huge step forward. Very reasonably, you might be asking how to take advantage of this bleeding edge technology.
TLS 1.3 in NGINX
NGINX has had support for TLS 1.3 since version 1.14.0. NGINX relies on OpenSSL for certain cryptographic functions, and will have to have been built against OpenSSL 1.1.1 or later in order to take advantage of TLS 1.3. In a text editor, simply open your nginx.conf file (usually located at /etc/nginx.conf or /etc/nginx/nginx.conf ) and add TLSv1.3 to the ssl_protocols directive .
For example:
TLS 1.3 in Apache on RPM based Linux Distributions
In Red Hat/ CentOS 7 and above, the httpd package 2.4.38 and above support TLS 1.3. It is compiled against OpenSSL 1.1.1a by default. In your httpd.conf file , simply add SSLProtocol TLSv1.3 to the SSLProtocol directive.
TLS 1.3 in Apache on Debian Based Linux Distributions
Debian 10 (Codename Buster) will be released with TLS 1.3 support out of the box for Apache Webserver. Ubuntu 19.04 comes with a version of Apache in its repositories that supports TLS 1.3 out of the box. The configuration directive is the same as above.
TLS 1.3 in IIS on Windows Server
Even on Server 2019, IIS does not support TLS 1.3 at this time. Microsoft is often slow to support proposed standards of the IETF, even though current IETF guidance considers a proposed standard as a stable protocol. Consider using a reverse proxy to take advantage of the benefits TLS 1.3 provides.
TLS 1.3 Client-Side Support
TLS must be supported by both the client and the server for it to be used. Chrome has supported TLS 1.3 since version 63, and Firefox since 61. Internet Explorer does not support TLS 1.3, and has been referred to as a “compatibility solution” by Microsoft. Edge, Microsoft’s latest offering, also does not currently support TLS 1.3, but plans to in a future release.
How to check if you’re successfully using TLS 1.3
To verify your site supports TLS 1.3 after the configuration changes above, you can use the SSL Test by Qualys to scan your server at www.ssllabs.com/ssltest . The results for an optimally configured server look like the figure below.

What about Proxies?
When TLS 1.3 was released, many Administrators were concerned that TLS 1.3 would break the ability to proxy connections for compliance related reasons. It turns out that many vendor’s implementations were written to support TLS 1.2 (and will need to be rewritten to support TLS 1.3), but there is nothing inherent about TLS 1.3 that prevents vendors from doing so.
And Packet Captures?
Many times, Administrators need to take a packet capture in order to figure out why something on their network isn’t behaving in a way they might expect. The introduction of PFS across the board poses an interesting problem. When using PFS, an algorithm called Diffie-Helman is used to constantly rotate the symmetric key each side agrees to use for communication after the initial handshake. (Without PFS this key remains static, and Wireshark uses the server’s private key onto to decrypt the first part of the communication in order to derive the symmetric key). With PFS enabled, Wireshark would need access to something called the “master key” which is only stored in memory (never written to disk) on the server. Barring extracting this key from RAM and providing it to a program like Wireshark, another option is to fall back to TLS 1.2 only when taking a packet capture. This can be done by simply disabling TLS 1.3 in your client application (such as a web browser). Even though this is inconvenient, it means that PFS is doing its job!
Author: Jeremy Schatten Published: 23-05-2019
Next Guide...
Setup haproxy 2 with keepalived and layer 7 retries.
HAProxy is an extremely powerful free and open-source load balancing solution. With it, you can insure high availability within your datacenter. Highly available systems are better for business continuity and better for security, as they can be patched with updates without taking the service down.…
- Forgot Password?
- Shared Web Hosting
- Clustered HA Cloud Server
- Dedicated Server
- Register a New Domain
- Transfer Domains to Us
- Domain Pricing
- Website & Security
- SSL Certificates
- Website Security
- Website Builder
- Knowledgebase

- How to enable TLS 1.3 in Mac Safari
- Client Area
- Technical and scripting information
Support
1- Open the Mac Terminal accessing to the Spotlight icon.
2- Start typing terminal in the search box.
3- Once it find the app, double click in the Terminal icon to open the terminal window.
4- Type sudo su - root to become a root user.
5- Type defaults write /Library/Preferences/com.apple.networkd tcp_connect_enable_tls13 1 command and press Enter .
6- Restart Safari.
Note : If you are using Safari version 7 or greater, TLS 1.1 and TLS 1.2 are automatically enabled.
Most Popular Articles
By default the encoding is latin1 but you could try to workaround your code. To change the...
If you made no changes in your account or oscommerce script and this happened suddenly then there...
This option is available in all our shared cPanel hosting accounts but may be unavailable...
You could try changing it sending the headers in your php code, i.e.: header('Vary:...
You can add the following line in your .htaccess file: AddHandler server-parsed .html or if you...
- English English Español No Records Found
Generate Password
iAchieved.it

TLS 1.3 Support Coming with Safari 12.1

With the landing of macOS 10.14.4 Beta (18E194d), Safari has versioned up from 12.0.3 to 12.1, and includes with it support for TLS 1.3 !

Pointing Safari 12.1 at tls13.iachieved.it (which only runs TLS 1.3) returns
Your User Agent is: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_4) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.1 Safari/605.1.15 with TLS_AES_256_GCM_SHA384 selected as the cipher. Note: If your current browser doesn’t support TLS 1.3 it will not be able to connect with tls13.iachieved.it .
Interesting in standing up your own TLS 1.3 webserver or see what browsers and clients support TLS 1.3? Come check out our instructions on configuring NGINX to do just that.
safari tls 1.3
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Related Posts
Service-agnostic mobile analytics.
Mobile application analytics is the capture and analysis of what users are doing with your mobile app. Of course, it ...
Multiple Build Schemes with Apple Watch
I frequently use Xcode schemes and configurations to manage building iPhone applications for specific environments. For example, let’s say you’re ...
Swift on Linux In 2021
It has been nearly 6 years since Apple first open sourced the Swift language and brought it to Linux. In ...

- What Is Transport Layer Security? A Breakdown of the Secure TLS Encryption Protocol

- How to Set Up SSH Without a Password in Linux

- How to Digitally Sign an Email Using Outlook

- What Is an Outlook Digital Signature (Digital ID)? A 90-Second Overview

- Mitigating Session Data Exposure: Perfect Forward Secrecy Explained

11 WordPress Security Best Practices & Tips to Do on Your Lunch Break

PKI 101: All the PKI Basics You Need to Know in 180 Seconds
![does safari support tls 1.3 The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-150x150.jpg)
The TLS Handshake Explained [A Layman’s Guide]

How to Tell If You’re Using a Secure Connection in Chrome

TLS Handshake Failed? Here’s How to Eliminate This Error in Firefox

2018 Top 100 Ecommerce Retailers Benchmark Study

5 Ridiculous (But Real) Reasons IoT Security is Critical

Comodo CA is now Sectigo: FAQs

8 Crucial Tips To Secure Your WordPress Website

What is Always on SSL (AOSSL) and Why Do All Websites Need It?

How to Install SSL Certificates on WordPress: The Ultimate Migration Guide

The 7 Biggest Data Breaches of All Time

Hashing vs Encryption — The Big Players of the Cyber Security World

How to Tell If a Website is Legit in 10 Easy Steps

What Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
- Most commented

- Cyber Security
- Web Security
- WordPress Security
- SSL Certificates
- Code Signing
- Email Certificates
- PCI Compliance
- CodeGuard Backup

TLS Version 1.3: What to Know About the Latest TLS Version
Tls 1.3 is used by 30% of connections on chrome and 27% on firefox, according to the ietf . here’s what to know about tls 1.3 and what this latest tls version of website security means for your business.
One of the things that I love most about the SSL industry is that it’s always changing. There’s always something new to talk about, discuss, debate, and learn about. Today, we’re going to talk about something that’s relatively new in the SSL world. We’re going to get under the hood of TLS 1.3, the latest TLS version of the cryptographic protocol that’s supposed to take SSL security and performance to new heights.
Before I get to TLS 1.3, I’ve got a question for you. Can you shift your car directly in fifth gear? Well, no, you can’t, right? In the same way, it’s essential to learn what TLS means before we get to TLS 1.3. So, let’s get started!
What Is TLS (Transport Layer Security)?
As the cliché goes, necessity is the mother of invention. The necessity of the TLS protocol was created in the early 1990s when more and more people started using the internet and there was suddenly a need to protect users’ privacy. To address this concern, SSL (secure socket layer), the first internet security protocol, was invented. So, what’s the difference between SSL and TLS ?
SSL, first developed by Netscape, was released in 1995 as SSL 2.0. SSL 1.0 was never released. Subsequently, TLS became the successor of SSL. So far, three versions of TLS have been released, and TLS 1.3 is the latest one.
TLS provides a secure connection between a client (typically, an end user’s web browser) and a web server. This secure connection is established by encrypting the data-in-transit. TLS data encryption is supported by many IP-based internet protocols, including HTTPS, POP3, SMTP, and FTP.
In everyday use, TLS is employed through what’s known as an “ SSL certificate .” These digital certificates are also known as “TLS certificates,” but most people use the legacy term “SSL certificate” because it’s more common. These certificates are the reason why your critical information doesn’t get leaked on the internet whenever you submit information to a website.
How TLS 1.3 Came Into Existence
As time has passed, the tech industry has made significant strides as far as computing power is concerned. Today’s technology has enabled us to use devices and share data at an unprecedented speed. However, with increasing performance prowess and data sharing, there comes a concern in the form of security. The more the computing power, the more vulnerable old security mechanisms, and that’s what happened with TLS 1.0 and TLS 1.1. Both these protocols were secure enough for a period but have since proven that they couldn’t stand the test of time when security vulnerabilities were discovered in them.
That’s why TLS 1.2, the most widely used TLS protocol, came into existence in 2008. It’s been the longest-serving TLS protocol — but, as it goes with all security technologies, it, too, has vulnerabilities. However, the majority of the weaknesses of TLS 1.2 are theoretical in nature, and that’s why it’s still a secure protocol to use. The potential flaws in TLS 1.2 underscored the need for a more secure successor of TLS 1.2, and that’s where the quest to develop TLS 1.3 began.
The road to the release of TLS 1.3 hasn’t been an easy one by any means — it took 28 drafts for Internet Engineering Task Force (IETF) to define it. There were many roadblocks, such as middleboxes and undermining attempts by commercial elements. But finally, after a decade of efforts, TLS 1.3 was released in 2018.
How TLS Version 1.3 Is a Significant Upgrade Over TLS 1.2
First, let us state it once again that there’s no need to panic as TLS 1.2 is still a safe protocol to use. In fact, as of May 2020, more than 67% of the websites surveyed by SSL Labs support TLS 1.2, whereas only 29.7% of sites support TLS 1.3. Having said that, TLS 1.2 was released in 2008, and that’s why it has some concerns that need to be addressed, keeping the future in mind.
Amongst many technical differences, TLS 1.3 version offers three upgrades that are quite critical to an ordinary user. These advantages are:
- Increased Speed
- Better Security
- Simplified Cipher Suites
Let’s learn about each of these benefits in a bit more detail.
TLS 1.3: The Performance Benefit of a Shortened Handshake Process
At the heart of all SSL/TLS protocols, there’s a process known as the “handshake process.” This handshake process occurs when the client and the server connect to transfer the data securely by the processes of authentication and encryption. It’s a series of back and forth communications between both parties.
As far as the TLS 1.2 handshake is concerned, it involves two round trips of communication between the client and the server. Therefore, the number of negotiations required becomes four. While this isn’t a big idea when you have just a few users on your website, it hurts the network performance when you’re doing it at scale.
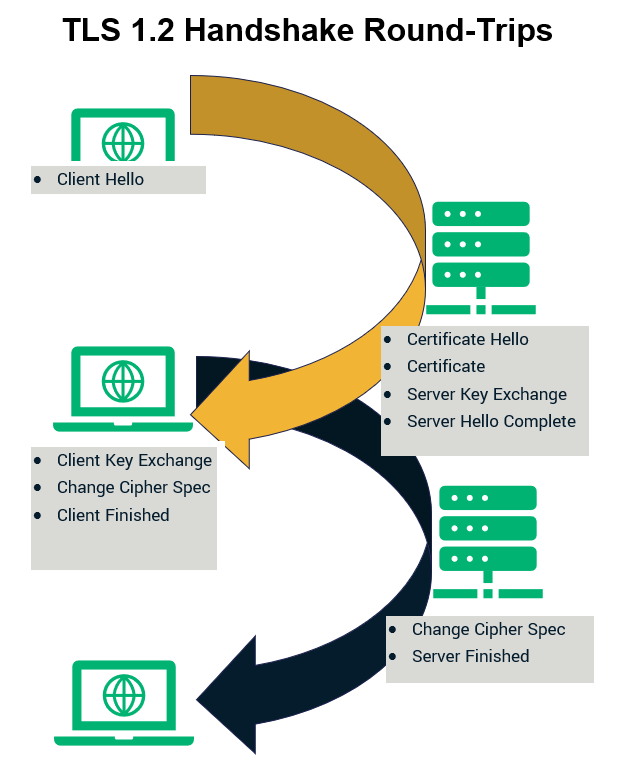
TLS 1.3 addresses this concern by reducing the handshake to a single round trip. That’s because the negotiations take place between the client and the server only twice. This results in increased network speed. The difference might be in milliseconds, but in domains where even a microsecond can make a world of difference, this is undoubtedly a significant advantage.
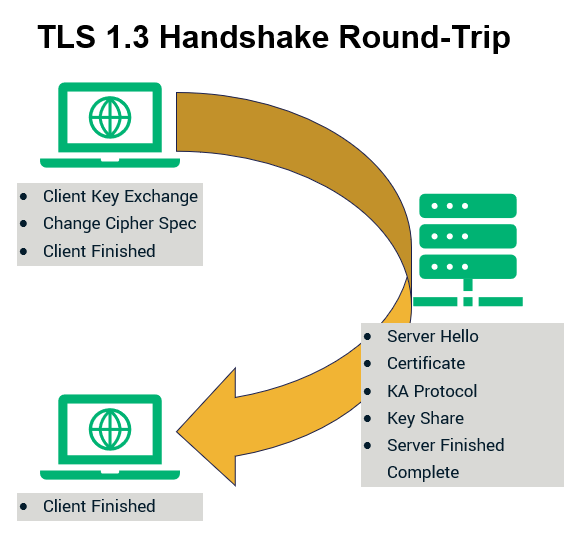
Not only that, but TLS 1.3 also introduces another feature that will have a considerable impact on the performance. This feature is known as “Zero Round Trip Time Resumption” (0-RTT). Much like its name implies, the 0-RTT feature paves the way for SSL/TLS handshakes that have zero roundtrips.
The 0-RTT feature comes into play when a server and client are resuming a connection. Therefore, on websites that you’ve visited in the past, no back and forth communication happens, and data encryption occurs with the first message you send to the server. This is done by resumption master key. 0-RTT decreases the load time significantly.
TLS 1.3: The Security Advantage
The most obvious but also the most essential benefit of TLS 1.3 comes in the form of security. TLS 1.3 has discontinued support for some of the older, potentially insecure ciphers and algorithms that were supported in TLS 1.2. These deprecated items include:
- RSA Key Transport
- Various Diffie-Hellman groups
- CBC Mode Ciphers
- RC4 Steam Cipher
- MD5 Algorithm
- EXPORT-Strength Ciphers
TLS 1.3: Simplified Cipher Suites
As we saw previously, the number of negotiations between the client and the server have been cut in half. This reduction results in a decreased cipher size. TLS 1.2 and its previous TLS versions used cipher suites that had four ciphers in them. Therefore, it made dozens of cipher combinations possible and didn’t have any clear guidance in choosing the right cipher combination for better security.
TLS 1.3, however, simplifies this process of selecting the right cipher combination as it has only five ciphers to choose from. These cipher suites are as below:
- TLS_AES_256_GCM_SHA384
- TLS_CHACHA20_POLY1305_SHA256
- TLS_AES_128_GCM_SHA256
- TLS_AES_128_CCM_8_SHA256
- TLS_AES_128_CCM_SHA256
Do Browsers Support TLS 1.3?
Initially, when the TLS 1.3 version was released, there were some concerns, and the browsers took a bit of time to adopt it. However, today, all major browsers have enabled support for TLS 1.3. However, as a site user, you must make sure that you’re using an updated version of your browser to take advantage of it as older versions may not be compatible with TLS 1.3
Final Word: Start Using TLS 1.3
Had it been up to security enthusiasts like me, we’d make it mandatory for all sites to use TLS 1.3. Fortunately — or unfortunately, depending on how you look at it — that’s not the case. Although it’s undoubtedly a saddening thing seeing only a fraction of websites supporting TLS 1.3 considering all of the benefits it offers. However, there’s a silver lining since that number is increasing day by day.
If you have a website, then you must make sure that you’ve enabled support for TLS 1.3. If you’re not sure about it, you can go to the SSL Labs website to check the TLS protocols your server supports. If your site is still supporting TLS versions preceding TLS 1.2, then you should disable their support ASAP as it could put your website at substantial risk. And if you find your web server not compatible with TLS 1.3, you know what to do . Right?
About the author
Jay Thakkar
Jay is a cybersecurity writer with an engineering background. A regular contributor on InfoSec Insights and Hashed Out, Jay covers encryption, privacy, cybersecurity best practices, and related topics in a way that an average internet user can easily relate.
You might also like

Years’ Old Unpatched Python Vulnerability Leaves Global Supply Chains at Risk
No comments, leave a reply cancel reply.
Your email address will not be published. Required fields are marked *
Search InfoSec Insights
Latest articles, recommended posts.
- DevSecOps: A Definition, Explanation & Exploration of DevOps Security
Version 1.3 (the latest one) of the Transport Layer Security (TLS) protocol. Removes weaker elliptic curves and hash functions.
- 4 - 53 : Not supported
- 54 - 69 : Disabled by default
- 70 - 123 : Supported
- 124 : Supported
- 125 - 127 : Supported
- 12 - 18 : Not supported
- 79 - 123 : Supported
- 3.1 - 12 : Not supported
- 12.1 - 13.1 : Partial support
- 14 - 17.3 : Supported
- 17.4 : Supported
- 17.5 - TP : Supported
- 2 - 50 : Not supported
- 51 - 59 : Disabled by default
- 60 - 62 : Partial support
- 63 - 124 : Supported
- 125 : Supported
- 126 - 128 : Supported
- 9 - 53 : Not supported
- 54 - 56 : Disabled by default
- 57 - 108 : Supported
- 109 : Supported
- 5.5 - 10 : Not supported
- 11 : Not supported
Chrome for Android
Safari on ios.
- 3.2 - 12.1 : Not supported
- 12.2 - 17.3 : Supported
- 17.5 : Supported
Samsung Internet
- 4 - 9.2 : Not supported
- 10.1 - 23 : Supported
- 24 : Supported
- all : Not supported
Opera Mobile
- 10 - 12.1 : Not supported
- 80 : Supported
UC Browser for Android
- 15.5 : Supported
Android Browser
- 2.1 - 4.4.4 : Not supported
Firefox for Android
- 14.9 : Supported
Baidu Browser
- 13.52 : Supported
KaiOS Browser
- 2.5 : Not supported
- 3 : Supported
Bringing Modern Transport Security to Google Cloud with TLS 1.3
Matt silverlock.
Product Manager, CDN
Gabriel Redner
Software Engineer, Cloud LB
We spend a lot of time thinking about how to improve internet protocols at Google—both for our Google Cloud customers and for our own properties. From our work developing SPDY into HTTP/2 and QUIC into HTTP/3, we know that improving the protocols we use across the Internet is critical to improving user experience.
Transport Layer Security, or TLS, is a family of internet protocols that Google has played an important role in developing. Formerly known as SSL, TLS is the main method of securing internet connections between servers and their clients. We first enabled TLS 1.3 in Chrome in October 2018 , at the same time as Mozilla brought it to Firefox. Today, the majority of modern clients support TLS 1.3, including recent versions of Android, Apple’s iOS and Microsoft’s Edge browser, as well as BoringSSL, OpenSSL and libcurl. Support for TLS 1.3 is wide-ranging, and brings performance and security benefits to a large part of the Internet.
Given this, we recently rolled out TLS 1.3 as the default for all new and existing Cloud CDN and Global Load Balancing customers. TLS 1.3 is already used in more than half of TLS connections across Google Cloud, nearly on-par with Google at large.
To gain confidence that we could do this safely and without negatively impacting end users, we previously enabled TLS 1.3 across Search, Gmail, YouTube and numerous other Google services. We also monitored the feedback we received when we rolled out TLS 1.3 in Chrome. This prior experience showed that we could safely enable TLS 1.3 in Google Cloud by default, without requiring customers to update their configurations manually.
What is TLS 1.3, and what does it bring?
TLS 1.3 is the latest version of the TLS protocol and brings notable security improvements to you and your users, aligned with our goal of securing the Internet.
Specifically, TLS 1.3 provides:
Modern ciphers and key-exchange algorithms, with forward secrecy as a baseline.
Removal of older, less-secure ciphers and key exchange methods, as well as an overall reduction in the complexity of the protocol.
Low handshake latency (one round-trip between client and server) for full handshakes, which directly contributes to a good end-user experience.
This combination of performance and security benefits is particularly notable: the perception is often that one must trade off one for the other, but modern designs can improve both. Notably, TLS 1.3 can have outsized benefits for users on:
Congested networks, which is particularly relevant during times of increased internet usage.
Higher-latency connections—especially cellular (mobile) devices—where the reduction in handshake round-trips is particularly meaningful.
Low-powered devices, thanks to the curated list of ciphers.
For example, Netflix also recently adopted TLS 1.3, and observed improvements in user experience around playback delay (network related) and rebuffers (often CPU related).
As an added benefit, customers who have to meet NIST requirements, including many U.S. government agencies and their contractors, can begin to address the requirement to support TLS 1.3 ahead of NIST’s Jan 1, 2024 deadline.
What’s next?
TLS 1.3 has quickly taken responsibility for securing large swaths of Google Cloud customers’ internet traffic, and we expect that proportion to grow as more clients gain support for it. We’re (already!) working on the next set of modern protocols to bring to our Google Cloud customers—including TCP BBRv2 , as well as IETF QUIC and HTTP/3 , which are close to being finalized. We’re also planning to support TLS 1.3 0-RTT (though customers will need to update their applications to benefit from it ) and certificate compression .
Click here to learn more about how Google Cloud secures customer traffic using TLS across our edge network, and how to secure your global load balancer using SSL policies .
- Google Cloud
Related articles

Introducing the Verified Peering Provider program, a simple alternative to Direct Peering
By Dave Schwartz • 7-minute read

Direct VPC egress on Cloud Run is now generally available
By Wietse Venema • 2-minute read

Upgrading Immersive Stream for XR to Unreal Engine 5.3
By Aria Shahingohar • 2-minute read

Announcing the general availability of Next Gen Firewall Enterprise
By Muninder Sambi • 4-minute read

z/TPF - Group home
Transport layer security (tls) 1.3 support for z/tpf.
Transport Layer Security (TLS) 1.3 is the latest iteration of the TLS protocol.
- Streamlined session startup
- Enforcement of perfect forward secrecy ciphers, such as ECDHE
- Removed unsafe ciphers and unsafe message digests
- TLS_AES_128_GCM_SHA256
- TLS_AES_256_GCM_SHA384
You can use SSL APIs to specify TLS 1.3 and TLS 1.3 cipher suites for applications that use TLS. z/TPF middleware packages also support the TLS 1.3 specification and the supported cipher suites in their respective TLS configuration files.
For more information about APAR PJ47183 , see the APEDIT.

IMAGES
VIDEO
COMMENTS
TLS security. iOS, iPadOS, and macOS support Transport Layer Security (TLS 1.0, TLS 1.1, TLS 1.2, TLS 1.3) and Datagram Transport Layer Security (DTLS). The TLS protocol supports both AES128 and AES256, and prefers cipher suites with forward secrecy. Internet apps such as Safari, Calendar, and Mail automatically use this protocol to enable an ...
Enabling TLS 1.3 in Firefox. Launch Firefox. Type about:config in the address bar and hit Enter. Start typing tls.version in a search, and you should see the following. Ensure security.tls.version.max value is 4. If not, double-click on it to modify to 4.
TLS 1.3 is Fully Supported on Safari. If you use TLS 1.3 on your website or web app, ... Support on previous Safari versions. Here's the support for TLS 1.3 across all versions of Safari: Safari versions: 16.4-14.1. Fully Supported. Safari versions: 13-12.1. Partially supported.
Version history for TLS/SSL support in web browsers tracks the implementation of Transport Layer Security protocol versions in major web browsers . ^ Note actual security depends on other factors such as negotiated cipher, encryption strength, etc. (see § Cipher table). ^ Whether a user or administrator can choose the protocols to be used or not.
Effective July 1, 2021, only web browsers that support versions 1.2 or 1.3 of the Transport Layer Security (TLS) protocol will be permitted to access University web services. Browsers that use TLS version 1.0 or 1.1 will not be supported. To ensure your web browser supports TLS 1.2 or 1.3, complete the steps below. Microsoft Edge
Notes. Supports a draft of the TLS 1.3 specification, not the final version. Can be enabled in Firefox by setting the security.tls.version.max pref to "4" in about:config.. Can be enabled in Chrome and Opera via the #tls13-variant flag in chrome://flags or opera://flags.. Partial support in Safari refers to being limited to macOS 10.14 Mojave and later.
1. There are several in-and-out messages between the client and server in TLS version 1.2. While TLS version 1.3 tries to shorten the handshake procedure' duration by minimizing the number of messages sent to and from between the Client and the Server. 2. The Cipher suites in TLS version 1.2 are less secure.
Enabling TLS 1.3 in Edge. Launch the Edge browser. Type "chrome://flags /" in the address bar. Type " TLS " in the search box. Set TLS to Default or Enabled. Restart the browser. 'Edge ...
Microsoft Edge started supporting TLS 1.3 with version 76, and it's enabled by default in Safari 12.1 on macOS 10.14.4. TLS 1.3 browser support. With that being said some SSL test services on the Internet don't support TLS 1.3 yet and neither do other browsers such as IE or Opera mobile. It might be a while for the rest of the browsers to ...
SSL/TLS is the protocol that encrypts communication between users and your website. When web traffic is encrypted with TLS, users will see the green padlock in their browser window. By turning on the TLS 1.3 feature, traffic to and from your website will be served over the TLS 1.3 protocol when supported by clients.
Tour Start here for a quick overview of the site Help Center Detailed answers to any questions you might have Meta Discuss the workings and policies of this site
TLS 1.3 Client-Side Support. TLS must be supported by both the client and the server for it to be used. Chrome has supported TLS 1.3 since version 63, and Firefox since 61. Internet Explorer does not support TLS 1.3, and has been referred to as a "compatibility solution" by Microsoft.
Enter TLS 1.3. While TLS 1.0, 1.1 and 1.2 are not that different, 1.3 is a big jump. Most importantly, establishing a TLS 1.3 connection takes one less round-trip. In TLS 1.3 a client starts by sending not only the ClientHello and the list of supported ciphers, but it also makes a guess as to which key agreement algorithm the server will choose ...
TLS 1.3 is the latest version of the TLS protocol. TLS, which is used by HTTPS and other network protocols for encryption, is the modern version of SSL. TLS 1.3 dropped support for older, less secure cryptographic features, and it sped up TLS handshakes, among other improvements.
Last year, Cloudflare was the first major provider to support TLS 1.3 by default on the server side. We expected the client side would follow suit and be enabled in all major browsers soon thereafter. It has been over a year since Cloudflare's TLS 1.3 launch and still, none of the major browsers have enabled TLS 1.3 by default.
TLS 1.2 is highly configurable, and vulnerable sites simply failed to disable the older features in hopes of being compatible with old browsers. TLS 1.3 embraces the "less is more" philosophy, removing support for older broken forms of cryptography. That means you can't turn on the potentially vulnerable stuff, even if you try.
Knowledgebase. Technical and scripting information. How to enable TLS 1.3 in Mac Safari. 1- Open the Mac Terminal accessing to the Spotlight icon. 2- Start typing terminal in the search box. 3- Once it find the app, double click in the Terminal icon to open the terminal window. 4- Type sudo su - root to become a root user.
With the landing of macOS 10.14.4 Beta (18E194d), Safari has versioned up from 12.0.3 to 12.1, and includes with it support for TLS 1.3! Pointing Safari 12.1 at tls13.iachieved.it (which only runs TLS 1.3) returns
SSL 1.0 was never released. Subsequently, TLS became the successor of SSL. So far, three versions of TLS have been released, and TLS 1.3 is the latest one. TLS provides a secure connection between a client (typically, an end user's web browser) and a web server. This secure connection is established by encrypting the data-in-transit.
Version 1.3 (the latest one) of the Transport Layer Security (TLS) protocol. Removes weaker elliptic curves and hash functions. 1 Supports a draft of the TLS 1.3 specification, not the final version. 2 Can be enabled in Firefox by setting the security.tls.version.max pref to "4" in about:config. 3 Can be enabled in Chrome and Opera via the # ...
Microsoft and Apple plan to support TLS 1.3 in future versions of Edge and Safari, respectively. TLS 1.0 will turn 20 years old on January 19, 2019. Here is what each browser maker has promised:
TLS 1.3, the latest and unsurprisingly the most advanced cryptographic protocol till date, has finally been approved by the IETF (Internet Engineering Task Force). Soon, TLS 1.3 will be adopted by all leading browsers and will soon become a reality from the theoretical concept it is. Needless to say, TLS 1.3 brings a host of improvements over ...
TLS 1.3 is the latest version of the TLS protocol and brings notable security improvements to you and your users, aligned with our goal of securing the Internet. Specifically, TLS 1.3 provides: Modern ciphers and key-exchange algorithms, with forward secrecy as a baseline. Removal of older, less-secure ciphers and key exchange methods, as well ...
You can use SSL APIs to specify TLS 1.3 and TLS 1.3 cipher suites for applications that use TLS. z/TPF middleware packages also support the TLS 1.3 specification and the supported cipher suites in their respective TLS configuration files. For more information about APAR PJ47183, see the APEDIT.