- Skip to main content
- Skip to header right navigation
- Skip to site footer

RestorePrivacy
Resources to stay safe and secure online

How to Fix WebRTC Leaks (All Browsers)
When discussing online privacy and VPNs, the topic of WebRTC leaks and vulnerabilities frequently comes up.
While the WebRTC issue is often discussed with VPN services, this is, in fact, a vulnerability with web browsers . WebRTC leaks can affect these browsers: Chrome, Firefox, Safari, Opera, Brave, and Chromium-based browsers.
So what is WebRTC?
WebRTC stands for “Web Real-Time Communication”. This basically allows for voice, video chat, and P2P sharing within the browser (real-time communication) without adding extra browser extensions.
What is a WebRTC leak?
A WebRTC leak is when your external (public) IP address is exposed via your browser’s WebRTC functionality. This leak can de-anonymize you via WebRTC APIs, even if your VPN is working correctly.
If you have not protected yourself against WebRTC leaks in your browser, any website you visit could obtain your real (ISP-assigned) IP address through WebRTC STUN requests. This is a serious problem.
While the WebRTC feature may be useful for some users, it poses a threat to those using a VPN and seeking to maintain their online privacy without their IP address being exposed.
How to test for WebRTC leaks
Our guide on testing your VPN lists a few different WebRTC testing tools:
- ipleak.net – In addition to WebRTC leaks, this website also tests for IPv4, IPv6, and DNS leaks.
- BrowserLeaks WebRTC test
- Perfect Privacy WebRTC test
What does a WebRTC leak look like?
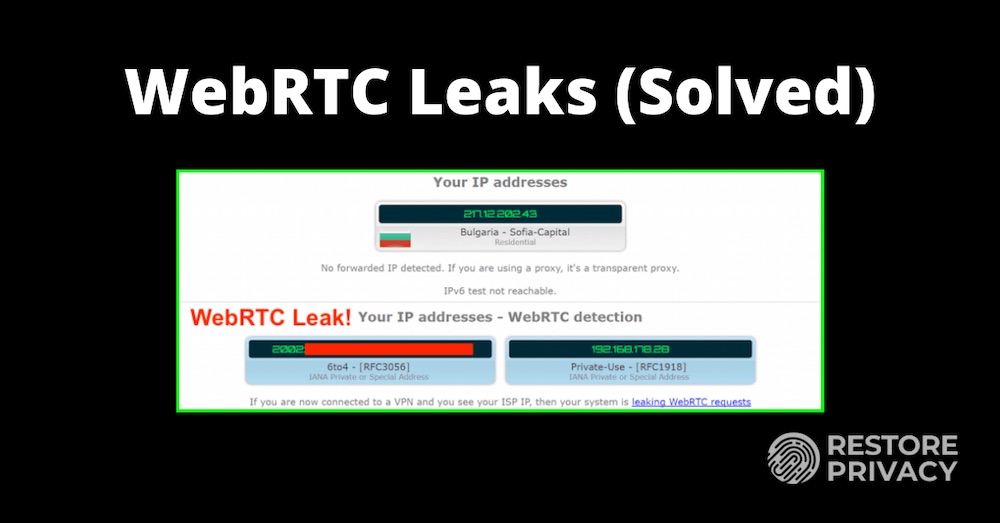
If you see your ISP-assigned (external) IP address, then this is a WebRTC leak. Below is an example of WebRTC leaks that I found when testing out a VPN service. You can see that my public IPv6 address (beginning with 2) is leaking in the WebRTC area, even while the VPN is connected and stable.
Note that a local IP address is blacked out on the left. These cannot be used to identify you. (An explanation of the difference between your local/internal IP and your public/external IP is here .)
The WebRTC Vulnerability
Anyone seeking to be anonymous online through privacy technology should take action against WebRTC leaks.
Daniel Roesler exposed this vulnerability in 2015 on his GitHub page , where he stated:
Firefox and Chrome have implemented WebRTC that allow requests to STUN servers be made that will return the local and public IP addresses for the user. These request results are available to javascript, so you can now obtain a users local and public IP addresses in javascript. Additionally, these STUN requests are made outside of the normal XMLHttpRequest procedure, so they are not visible in the developer console or able to be blocked by plugins such as AdBlockPlus or Ghostery. This makes these types of requests available for online tracking if an advertiser sets up a STUN server with a wildcard domain.
Essentially, this means that any site could simply execute a few Javascript commands to obtain your real IP address through your web browser.
WebRTC leak solutions
Here are two options for dealing with the WebRTC issue:
1. Disable WebRTC in the browser ( Firefox ) and only use browsers with disabled WebRTC capability. (Instructions are below.)
2. Use browser add-ons or extensions if disabling WebRTC is not possible. (Disabling WebRTC is not possible with Chrome and Chromium-based browsers, such as the Brave browser.)
Note : browser add-ons and extensions may not be 100% effective . Even with add-ons, the vulnerability still exists in the browser to reveal your true IP address with the right STUN code.
WebRTC fixes for different browsers
Below are different fixes for various browsers.
Firefox browsers
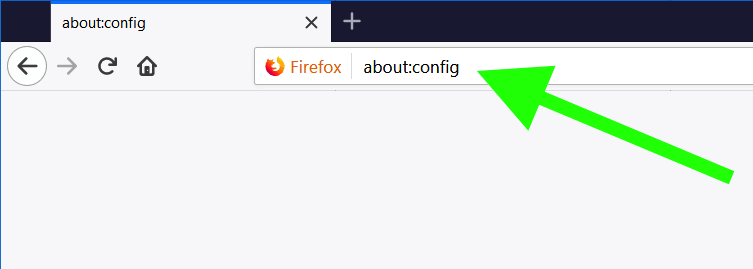
Disabling WebRTC is very simple in Firefox. First, type about:config into the URL bar and hit enter . Then, agree to the warning message and click the continue button.
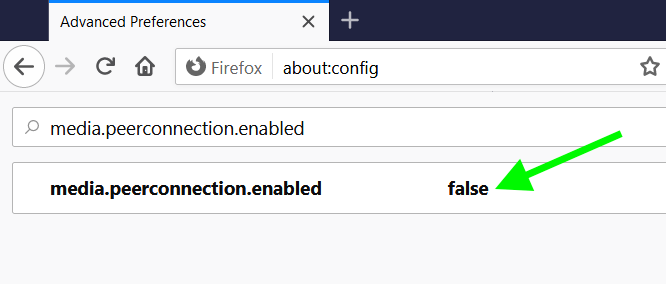
Then, in the search box type “ media.peerconnection.enabled “. Double click the preference name to change the value to “ false “.
That’s it.
WebRTC is now disabled in Firefox and you won’t have to worry about WebRTC leaks.
Chrome WebRTC (desktop)
Since WebRTC cannot be disabled in Chrome (desktop), add-ons are the only option (for those who do not want to just give up on using Chrome).
As pointed out above, it is important to remember that browser add-ons are may not be 100% effective . In other words, you may still be vulnerable to WebRTC IP address leaks under certain circumstances. Nonetheless, here are some add-ons that may be worth considering:
- WebRTC leak prevent
- uBlock Origin
Note : Unlike with Firefox, these extensions only change WebRTC’s security and privacy settings.
Recommended solution: stop using Chrome.
Disable Chrome WebRTC on Android
On your Android device, open the URL chrome://flags/#disable-webrtc in Chrome.
Scroll down and find “WebRTC STUN origin header” – then disable it. For safe measure, you can also disable the WebRTC Hardware Video Encoding/Decoding options, though it may not be necessary.
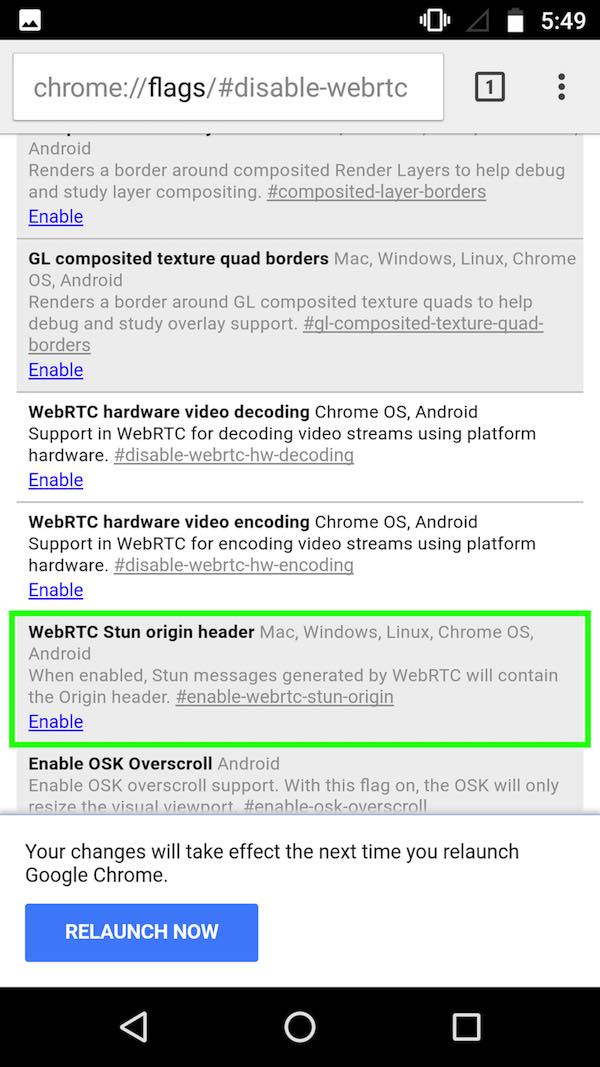
Note : Android users can also install Firefox, and disable WebRTC via the steps above.
Chrome iOS WebRTC
Chrome on iOS does not appear to implement the vulnerable parts of WebRTC that could expose local or external IP addresses (yet).
Brave WebRTC leaks
Because the Brave browser is based on Chromium , it is also vulnerable to WebRTC IP address leaks, even when you are using a VPN.
There are two ways to block WebRTC in the Brave browser:
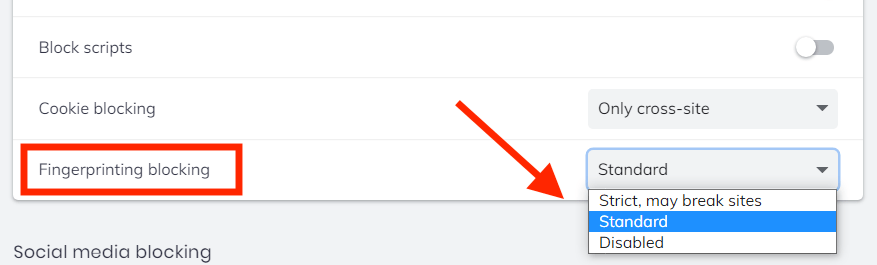
Method 1: Fingerprinting protection
Go to Settings > Shields > Fingerprinting blocking > and then select Standard or Strict . This should take care of all WebRTC issues – at least on desktop versions of Brave (Windows, Mac OS, and Linux).
Note on WebRTC handling policy
You can also adjust the WebRTC handling policy if you go to Settings , click on the search glass in the upper-right corner, and then enter WebRTC . Under the WebRTC IP Handling Policy click the drop down menu and you can see the options below.
Note : To understand the different options with WebRTC handling, Brave has an article on the topic here . Below are the different options:
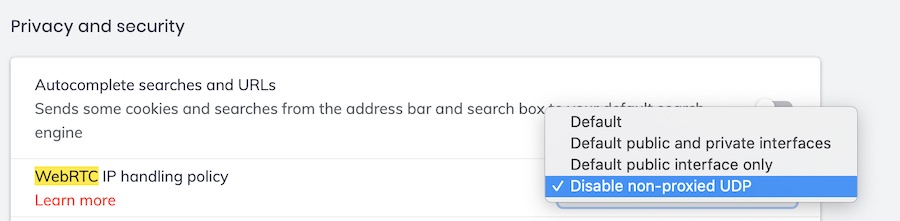
I have now tested this with the latest versions of Brave for Windows and Mac OS. Based on my tests, if you already have Fingerprinting blocking set to enabled , you should not experience any WebRTC leaks.
Note : I have seen some complaints from users who claim that WebRTC is not getting blocked on iOS, even after making the changes above. Brave developers appear to have confirmed this issue and are working on a fix.
Safari WebRTC
WebRTC leaks have traditionally not been an issue with Safari browsers (on Mac OS and iOS devices). However, Apple is now incorporating WebRTC into Safari, although it’s still technically an “ experimental ” feature. Nonetheless, it’d be wise to disable WebRTC in Safari for privacy reasons. Here’s how:
- Click “Safari” in the menu bar
- Then click Preferences
- Click on the “Advanced” tab, then at the bottom check the box for “Show Develop menu in menu bar”
- Now, click on “Develop” in the menu bar. Under the “WebRTC” option, if “Enable Legacy WebRTC API” is checked, click on it to disable this option (no check mark).
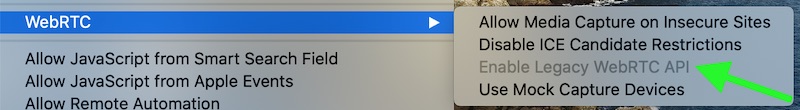
That should effectively disable WebRTC in Safari.
Opera and other Chromium browsers WebRTC
Just like with Chrome, the only way (as of now) to address the WebRTC vulnerability in Opera and other Chromium browsers is to use an extension.
First, download the extension “ WebRTC Leak Prevent ” to your Opera browser.
Then in the Advanced options for the WebRTC Leak Prevent extension, select “ Disable non-proxied UDP (force proxy) ” and then click Apply settings .
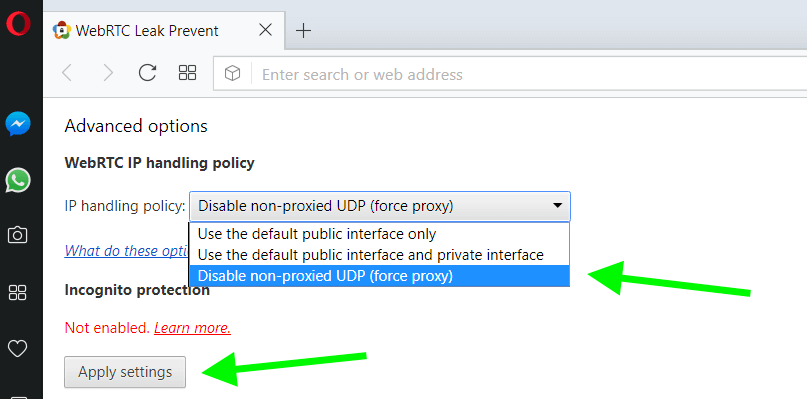
Again, because this is an extension solution, it may not be 100% effective.
Now verify you don’t have any WebRTC leaks
Now that you have disabled or blocked WebRTC in your browser, you should test to verify that it is working. Here are our favorite tools for identifying WebRTC leaks:
- Perfect Privacy WebRTC Test
- BrowserLeaks WebRTC Test
Note : If you are seeing a local IP address, this is not a leak. A WebRTC leak will only be with a public IP address.
Here I’m running a test in the Firefox browser while also connected to ExpressVPN :
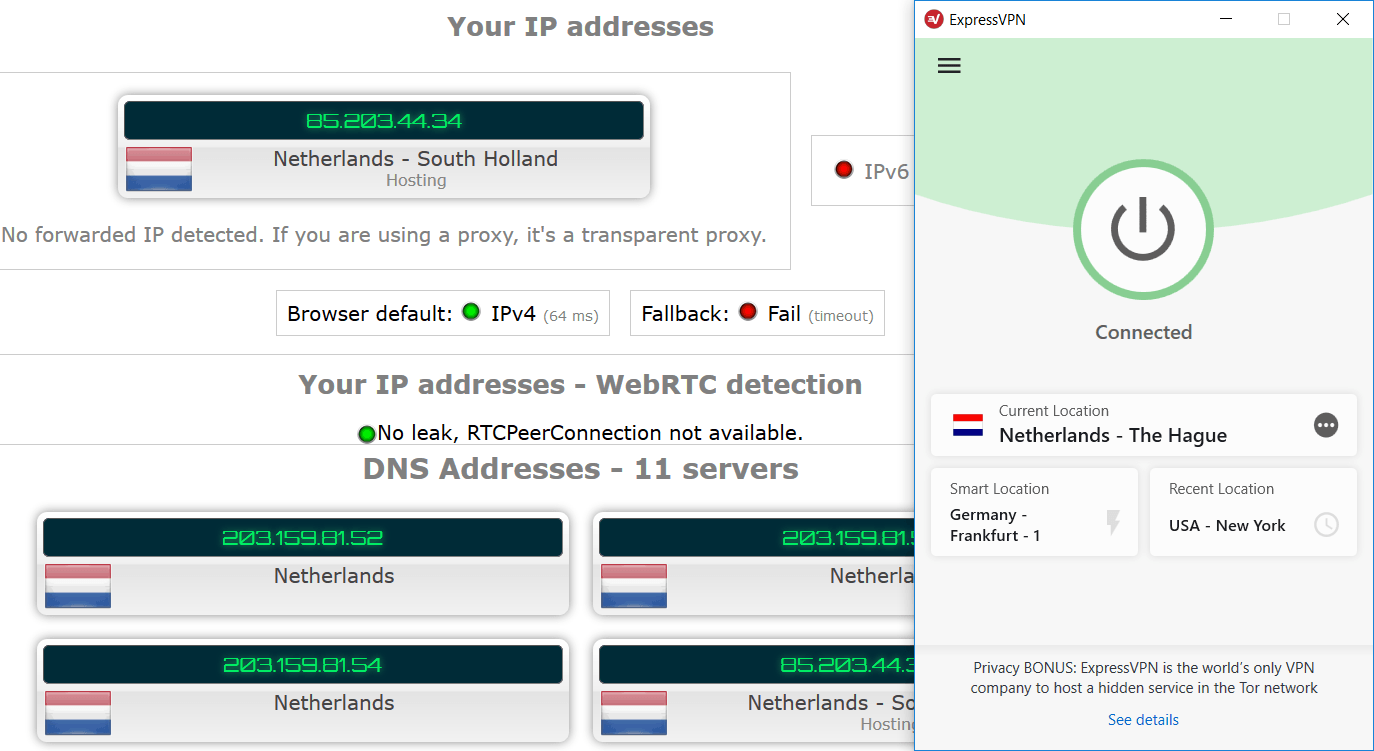
You can see the ExpressVPN client on the right, with the test results on the left. No leaks!
Note: ExpressVPN is currently our top VPN recommendation and they also have a discount for three months free, see our ExpressVPN coupon page for details.
Conclusion on WebRTC leaks and browser vulnerabilities
The WebRTC leak vulnerability highlights a very important concept for those seeking a higher level of online anonymity and security through various privacy tools .
The browser is usually the weak link in the chain.
The WebRTC issue also shows us that there may be other vulnerabilities that exist with your privacy setup, even if you are using a good VPN to hide your IP address and location. (The WebRTC issue was not publicly known until 2015.)
One other problem to be aware of is browser fingerprinting . This is when various settings and values within your browser and operating system can be used to create a unique fingerprint, and thereby track and identify users. Fortunately, there are effective solutions for this as well.
And lastly, there are many different secure and private browsers to consider, many of which can be customized for your own unique needs.

About Alex Lekander
Alex Lekander is the Editor-in-Chief and founder of RestorePrivacy. With a passion for digital privacy and accessible information, he created RestorePrivacy in 2017 to provide you with honest, useful, and up-to-date information about online privacy, security, and related topics. Follow him on Twitter
Reader Interactions
December 1, 2023
Some additional tools what I use for long time:
– https://dnscheck.tools/ – https://cmdns.dev.dns-oarc.net/ (more extended DNS test as above) – https://webbkoll.dataskydd.net/en – https://browserbench.org/Speedometer2.1/
January 19, 2024
I just installed brave on Fedora 35, and tested webRTC leaks on mullvad.net. I had to disable non-proxied UDP as well as having fingerprinting disabled-strict.
November 16, 2022
Hi Sven Taylor! Every time I open up Ebay page on Firefox, Google pop up a window ask me to sign in to Google Account! Can you show us how to get rid of this annoying thing? I did turn the WebRTC to False. Thanks, CT
August 25, 2022
Hi Sven, iOS has changed greatly since your guide. Instead of the one Safari toggle you mention there are now many experimental WebKit toggles, including 20+ that look to relate to canvas. A new guide on what to do with them sure would help! Is this already available somewhere?
August 26, 2022
Hi Milton, we’ll get this out but we need an updated iOS device to verify settings first.
March 11, 2023
iOS app’s & browsers leak like sieves. VPNs mostly leak & do not work anymore Nordvpn leaks true location: 2 examples paramount plus, & Firefox tying to use bbciplayer FYI 3-11-23 everything is most recent updated versions
July 14, 2022
I’m trying to disable WebRTC in Amazon Silk browser (based on Chrome) on the newer Echo Show devices. The Chrome web store extensions are unavailable to this browser and side-loading on the Echo Show seems difficult at best. I also wish I could install the NordVPN extension for Silk, but it’s only available for Edge and Chrome, and maybe Firefox. Surely there must be a way to get into the Developer settings on Silk. Is there any hope? I these days of hackers and snooping, I don’t see any reason why Amazon needs total control over knowing my actual IP address.
April 19, 2022
Firefox for Android does not allow you to disable WebRTC. This is due to the fact that as of April 2021, Androids have been denied access to about:config in Firefox stable and beta channels. Install Firefox Nightly.
October 16, 2022
Really? So does that mean that when I put about:config in the iceraven for Android browser I use and the full developer page pops up and I then find the section to disable WebRTC and able to toggle to Disable along with a couple more WebRTC related setting also. That this is not actually disabled?? Actually you CAN Disable WebRTC for Android thru Iceraven, Nightly, Firefox, and Icecat (unfortunately abandoned).
WebRTC disabled in browser. Microsoft softwares and Android apps WebRTC is leaking?
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
- VPN & Privacy
How to stop WebRTC leaks on Chrome, Firefox, Safari, and Edge [SOLVED]

WebRTC is used by web browsers for voice and video chat applications like Skype for Web, Discord, and Google Hangouts. The free and open-source project lets apps set up peer-to-peer connections without the need for any extra plugins or applications, allowing for efficient real-time communication (the ‘RTC’ in WebRTC). Most modern web browsers now support and enable WebRTC by default, including desktop browsers like Chrome, Firefox, Safari, and Edge, as well as mobile browsers on Android and iOS.
The problem is that WebRTC compromises the security provided by VPNs, or virtual private networks. When a user connects to a VPN server, all of the internet traffic from their device should go through an encrypted tunnel to the VPN server. Among other benefits, this prevents websites and apps from determining the user’s real IP address, which is masked by that of the VPN server. An IP address is a string of numbers and decimals unique to every internet-connected device that can be used to determine location.
Whenever a VPN user visits a site that has WebRTC enabled, WebRTC can transmit data outside the encrypted tunnel. This exposes the user’s real IP address and location to the website, which means the user can be tracked by advertisers and other third parties.
In this article, we’ll explain how to prevent WebRTC leaks when using a VPN on all major browsers.
Preferred solution: Use a better VPN
Not all VPNs suffer from WebRTC leaks. Some have added security features to their apps that prevent WebRTC traffic from traveling outside the encrypted VPN tunnel. Of the many VPNs we’ve tested, two stand out:
While many VPNs claim to prevent IP leaks, many fail to live up to their promises. We’ve put these two VPNs through rigorous leak tests to ensure they never allow WebRTC leaks to occur under any circumstances. Both NordVPN and ExpressVPN prevent WebRTC leaks on any web browser or app.
By signing up for and installing either of these VPNs, you don’t need to worry about WebRTC leaks. No further tweaks are required.
How do I know if WebRTC is leaking?
When you connect to a VPN, your WebRTC IP address should either change to that of the VPN or be disabled entirely.
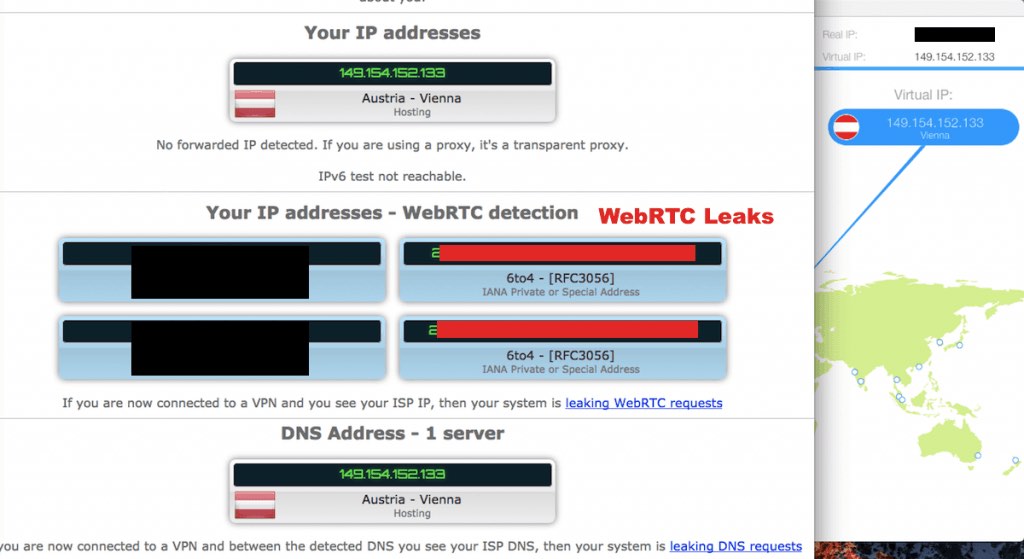
As an example, here’s my connection info while connected to a VPN that suffers from WebRTC leaks :
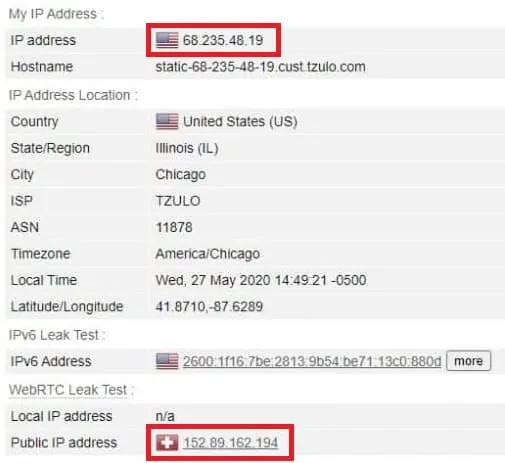
Notice that my standard IP address and WebRTC address are different. That’s because my real IP address is being leaked through WebRTC, and WebRTC traffic is not going through the VPN. While connected to the VPN, both addresses should both be identical.
You can run this test on your own using our VPN leak tester .
WebRTC leak severity depends on permissions granted
Before we get into other ways to prevent WebRTC leaks, we want to clarify that not all leaks are equal. When it comes to WebRTC leaks, we categorize them into two levels of severity:
- Leaks when permissions granted – less severe
- Leaks when permissions not granted – more severe
When you visit a website that uses WebRTC, your browser will usually ask your permission before allowing a website access to your camera or microphone.
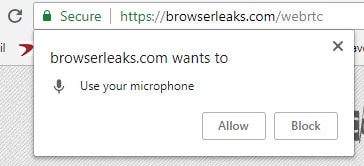
If a VPN leaks your IP address before you’ve even granted that website permission to use your camera or microphone, that’s a big red flag. That means any website could use some simple javascript to monitor your IP address and expose your real location. We label this a “persistent vanilla leak,” which is the most severe type. Most VPNs that claim to prevent WebRTC leaks can at least stop this from happening.
Except for the two mentioned above, almost all VPNs suffer from the less severe version of WebRTC leaks, in which your IP address is exposed to the website only after you grant it permission to use your microphone or camera. Even though this leak is less severe, it’s still cause for concern. A VPN user should be able to safely visit WebRTC-enabled sites without exposing their IP address.
How to stop WebRTC leaks in Chrome
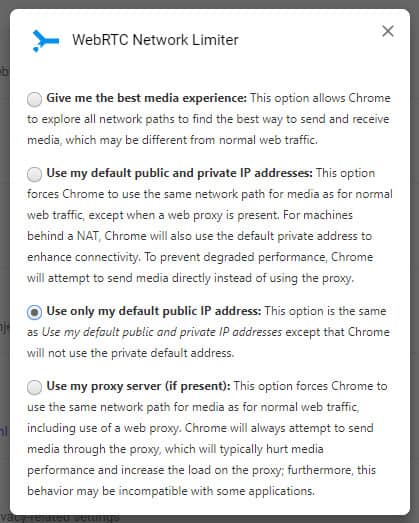
Google Chrome requires a simple browser extension to disable WebRTC. WebRTC Network Limiter lets you choose how WebRTC network traffic is routed. You can easily configure it to use only your VPN’s public IP address.
Alternatively, you can use the WebRTC Control browser extension to enable or disable WebRTC via a simple toggle switch.
See also: Best VPNs for Chrome
How to stop WebRTC leaks in Firefox
In Firefox, you can disable WebRTC in the browser settings:
- In the URL bar, enter: about:config
- Run a search for: media.peerconnection.enabled
- Double-click the entry to change it to False
Note that changes you make to the settings may not carry across updates, so you might need to re-adjust this setting again if your browser updates.
How to stop WebRTC leaks in Microsoft Edge
Microsoft Edge now supports both WebRTC plus its own proprietary version, dubbed ORTC. Unfortunately, Edge does not allow you to disable either. You merely get the option to hide your local IP address over WebRTC connections, but not your public IP address.
To conceal local IP addresses with mDNS hostnames, do the following
- Types “about:flags” in the browser’s address bar and hit “Enter”
- Scroll down until you see “Anonymize local IPs exposed by WebRTC” or enter it in the search field
- Choose “Enabled” from the drop-down menu
A “WebRTC Leak Shield” extension is available on the Microsoft app store , but given it has no user feedback at time of writing and sparse details about the developers, we would avoid it for now.
If you’re an Edge user and you want to prevent WebRTC leaks, ExpressVPN and NordVPN will both get the job done. Websites will only see your VPN server’s public IP address and not your own when connected through either of their respective apps.
See also: Best VPNs for Microsoft Edge
How to stop WebRTC leaks in Safari
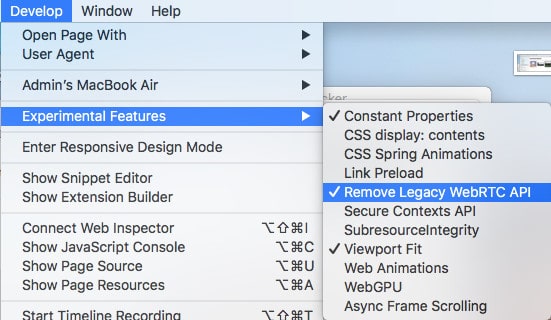
Safari blocks sites from accessing your camera and microphone by default, so we’re really only concerned about the less severe type of WebRTC leak here. You can turn WebRTC off in the developer settings:
- Open Safari and go to Safari > Preferences…
- Go to the Advanced tab and check the box at the bottom that says Show Develop menu in menu bar
- Close the preferences menu and go to Develop > Experimental Features
- Check the option for Remove Legacy WebRTC API
See also: Best VPNs for Safari
How to stop WebRTC leaks on Android
Those with old versions of Android — such as 8.1.0 Oreo — are often advised to disable WebRTC Stun origin header in the flags menu. However, in our experience this does not work. Even if we disable every WebRTC-related setting, our real IP address leaks. In any event, this will be irrelevant to those using recent versions of Android — such as Android 13 — where the “WebRTC Stun origin header” feature is not available. You can check availability on your own device as follows:
- Open Chrome
- Type “chrome://flags” in the address bar
- Search for “WebRTC” in the “Search flags” field
Notably, ExpressVPN and NordVPN do prevent this leak when we connect through their Android apps. Websites can still see an IP address, but it’s the VPN server’s IP address and not our real IP address.
See also: Best VPNs for Android
How to stop WebRTC leaks on iOS
You can only disable WebRTC in mobile Safari on iOS 11 or earlier. The setting to disable it was removed in iOS 12. For later versions of iOS (12+), you can use ExpressVPN’s or NordVPN’s iOS app to mask your real IP address and prevent WebRTC leaks.
Disabling WebRTC on the Safari browser in iOS 11 or earlier is fairly similar to the desktop version:
- Open the Settings app on your iPhone or iPad
- Scroll down and tap on Safari > Advanced > Experimental Features
- Tap the switch next to Remove Legacy WebRTC API so it turns green
We will update this article if we come across a way to plug WebRTC leaks in iOS 12 and later.
See also: Best VPNs for iPhone
How to stop WebRTC leaks with uBlock Origin
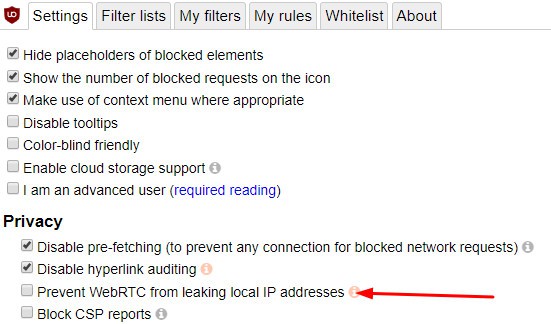
uBlock Origin is a popular browser add-on/extension for Firefox and Chrome. It can prevent your browser from leaking your device’s local IP address, but not your public IP address . For this reason, we recommend uBlock Origin more as a supplement to the other solutions in this list, and not a standalone solution.
After installing it, just go into the Settings and check the box that says, Prevent WebRTC from leaking local IP address.
What about VPN browser extensions?
There’s no shortage of browser plug-ins that claim to work like VPNs by redirecting internet traffic through a secure proxy. The vast majority of VPN browser extensions won’t protect you from WebRTC leaks. The only standalone VPN add-on we know of that does stop WebRTC leaks is NordVPN. In addition to its native desktop and mobile apps, its browser extension for Chrome and Firefox protects against WebRTC leaks.
The ExpressVPN browser extension stops WebRTC leaks, but isn’t a standalone product. Instead, users must already have installed the native VPN app. The browser extension is a way to conveniently control the app, and allows users to change the WebRTC network path so that it passes through an ExpressVPN server.
Disabling WebRTC won’t break VoIP apps
If you want to stop WebRTC leaks but like to use voice and video chat apps like Google Hangouts, Discord, and Skype, worry not. Disabling WebRTC doesn’t usually break those apps; they just have to fall back on a different method of communicating. While the call quality might suffer a bit, you can still use voice and video chat normally with WebRTC disabled.
Test for WebRTC leaks
Once you’ve applied a fix, you can check to make sure it’s working using Comparitech’s DNS leak test . This page runs a test in two parts: with the VPN connected and with the VPN disconnected. The results will show you in plain terms whether your VPN is leaking DNS, IPv6, or WebRTC traffic. You can even choose whether to allow or disallow microphone and camera permissions to determine leak severity.
Leave a Reply Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Roundup - best VPNs for
Privacy alert: websites you visit can find out who you are.
The following information is available to any site you visit:
Your IP Address:
Your Location:
Your Internet Provider:
This information can be used to target ads and monitor your internet usage.
Using a VPN will hide these details and protect your privacy.
We recommend using NordVPN - #1 of 72 VPNs in our tests. It offers outstanding privacy features and is currently available at a discounted rate.
WebRTC Leaks and Your Privacy (+ how to fix them)
This post was originally published on 31 JAN 2021 ; it has since been updated and revised.
WebRTC can prove useful when users need to use it, which is most commonly during peer-to-peer (P2P) calling in the browser.
However, a critical flaw yet to be directly and adequately addressed across all browsers exists in WebRTC that leaks users' internal IP addresses? Even if using a trusted and leak-resistant VPN service, the IP address can leak through this flaw.
This phenomenon is known as a WebRTC leak and it can have an impact on privacy while remaining "invisible" to the user.
What is WebRTC?
WebRTC = Web R eal T ime C ommunication
WebRTC allows users to communicate by voice, video chat, and other forms of P2P sharing from directly inside the browser - without downloading any additional extensions or add-ons. WebRTC was released officially in 2011. However, only in recent years has it become more popular.
WebRTC is an open-source project, but it is created, backed, and heavily endorsed by Google.
WebRTC leaks and privacy
WebRTC leaks a user's internal IP address and can leak the external IP address as well. This leak can occur from even behind a well implemented and trusted VPN provider. WebRTC leaks are not the same as DNS leaks or IPv6 leaks which are almost entirely a problem with VPN configuration settings.
Your internal IP address is not the same as your external IP address. Your external IP address is assigned by your Internet Service Provider (ISP) and is "meant" to be shared with the internet. However, users who wish to hide their IP address via a VPN are compromised via these leaks.
The internal IP address is meant to only be shared with other devices connected to your local network, such as a user's home Wi-Fi. If leaked to the outside world, it can serve as an even more unique identifier than the external IP address meant to be shared with other machines on the internet.
Naturally, this poses a problem in protecting and maintaining online privacy.
While IP addresses exposed on the internet aren't necessarily a large concern of itself, the collection of IP address data alongside other tracking methods and fingerprinting methods pose a serious hurdle for users seeking improved online privacy. This is especially true if a user is accidentally and silently leaking their IP address even while taking privacy and cybersecurity enhancing measures.
IP addresses can be used to collect or infer with reasonable accuracy information such as:
- Your precise geo-location (frequently within 1-2 miles accuracy)
- Excessive details about the device you're using (make, operating system, software version{s}, exact model, etc.)
- Information about other devices on your network
- ISP information
Perhaps the worse thing about WebRTC leaks is that most methods websites use to pull an IP address via WebRTC are silent. In fact, just a few lines of JavaScript executing silently can use a WebRTC leak to pull an IP address even from behind a VPN as WebRTC traffic doesn't always route through the VPN.
Most times, the end-user would be totally unaware of this happening.
Is your browser leaking your IP address?
Tools are available to evaluate whether the browser is leaking information via WebRTC:
- BrowserLeaks
These tools emulate the common techniques websites use to pull from this information from the browser. Again, as noted earlier, most of these techniques happen silently and without the expressed knowledge of the user. Denying cookies does nothing to alleviate this.
Fixing browser WebRTC leaks
Two main ways to fix WebRTC leaks include:
- Disabling the WebRTC function in a chosen web browser, if possible .
- Installing an extension that fixes or helps curve WebRTC components from leaking the internal IP address.
Users should be aware the extension method _isn't_ always 100% effective.
WebRTC can be completely disabled in Mozilla Firefox:
- Open Mozilla Firefox
- Type about:config into the address bar
- If you've never been the advanced settings, you'll see an alert. Click the equivalent of "I accept."
- You should be looking at a mostly blank page with a search bar the top. In the search bar on the page, type media.peerconnection.enabled
- Double click on media.peerconnection.enabled . It should now say " false ."
- Restart the browser and retest for leaks
This browser isn't recommended for users seeking privacy.
On the desktop version of Chrome, WebRTC cannot be disabled from within the browser settings .
The only option to disable WebRTC in Google Chrome is via installing an extension that mitigates WebRTC leaks.
WebRTC extension recommendations:
- uBlock Origin
It's important to understand that these extensions will not disable WebRTC, but rather tweak settings to help prevent leaks from occurring.
And again, even with the tweaking done by these extensions, this is not foolproof . Under specific circumstances, IP address information can still be revealed via WebRTC leakage.
With Chrome on Android, WebRTC can be disabled:
- Open Chrome on your Android device
- In the address bar, type chrome://flags/#disable-webrtc
- Find the setting Disable WebRTC
- Click " Enable "
- Restart the browser and test for leaks
Like Google Chrome, WebRTC cannot be disabled within Edge. Starting in 2020, the new version of Microsoft Edge uses Chromium like Google Chrome and the Brave Browser.
However, Edge does have a setting to disable sharing the internal IP address over WebRTC connections:
- Open Microsoft Edge
- Type about:flags into the address bar.
- There's a whole bunch of settings here. Look for Anonymize local IPs exposed by WebRTC ( hint : use CTRL+F to the search the page for "hide")
- For Anonymize local IPs exposed by WebRTC , select " Enable ."
Brave is based on the Chromium engine. Therefore WebRTC cannot be disabled from within the browser.
However, WebRTC leaks can be mitigated from within the Brave Browser's settings:
- Open the Brave browser
- Find and click " Settings "
- Click on the search icon, located in the upper right of the screen (or press CTRL+F)
- In the search bar, type webrtc
- Under WebRTC IP Handling Policy, click the drop-down
- Select "Default public interface only" from the drop-down
- Restart browser and test for leaks
- Look for the " Shields " section within the " Settings " page
- Click on the drop down for " Fingerprinting blocking "
- Select " Strict, may break sites " from the drop-down
Alternatively, since most extensions that work on Chrome also work on Brave, it's possible to install an extension to mitigate potential WebRTC traffic leaks.
Users may find the settings within Brave to be more reliable for mitigating WebRTC leaks as opposed to using extensions.
Supposedly , Safari doesn't leak IP address information via WebRTC, but many users have experienced otherwise since WebRTC was first introduced into Safari.
Allegedly, WebRTC leaks allegedly only affect browsers on Windows platforms and potentially on Linux systems, depending on the distro. This claim is yet to be proven and should be taken with a grain of salt.
Apple was relatively "late" in implementing WebRTC in Safari on both its macOS and iOS platforms. Specifically, WebRTC was officially introduced with the release of Safari 11 on both desktop and mobile platforms, circa 2017 . At this point in time, many web browsers had long adapted and incorporated WebRTC into their source code.
Disabling WebRTC in Safari:
WebRTC reportedly doesn't leak your internal IP address on iOS. Source
You can still disable WebRTC related features by using the advanced settings for Safari:
- Open the Settings app on your iDevice
- Tap " Safari "
- Scroll all the way down and tap " Advanced "
- Tap " Experimental Features "
- Disable anything with WebRTC in the name
- Open Safari and test for leaks
NOTE: There does not appear to be a way to disable WebRTC outright in iOS. Supposedly this has been the case since the release of iOS 12.
- Open Safari and navigate to Preferences
- Click on the Advanced tab and then check Show Develop menu
- Outside the preferences menu, navigate to Develop > Experimental Features
- Check Remove Legacy WebRTC API
- Close Safari. Open and then test for leaks
Re-testing for IP leaks
After adjusting settings accordingly, users will want to retest the browser for any leaks:
- Ensure the correct settings are enabled (or extensions are installed and active).
- Restart the browser
- Re-test for leaks
Again, these are solid web tools for testing for WebRTC leaks:
Keep in mind that seeing the external (or public) IP address is fine in most cases if not behind a VPN.
Final thoughts
WebRTC leaks are silent and websites engaging in tracking and fingerprinting can just as silently pull information leaked via WebRTC traffic.
Even if using a VPN, users should take steps to address potential WebRTC from inside their chosen browsers. All browsers are subject to WebRTC leaks.
Preventing WebRTC leaks is a relatively painless way to improve any given user's online privacy.
Stay safe out there!
Next Post Previous Post
WebRTC leaks: what they are and how to prevent them
Even with a VPN, your privacy can still be exposed to dangers

Even the best VPN services cannot prevent your privacy from being exposed at times. This is something that can occur from a leak on your browser, for example.
First discovered in 2015, WebRTC leaks are a serious vulnerability with web browsers that anyone concerned about their online anonymity should be aware of.
Chrome, Firefox, Safari , Opera, Brave, Chromium-based browsers: all these can be affected.
But what even is WebRTC? Here we assess the risks of it leaking as well as the best practices to help prevent it - even if you're somebody who already uses a VPN to try and stay anonymous online.
What is WebRTC?
Short for Web Real-Time Communication, WebRTC it is an open source tool first introduced in 2011 that allows web browsers to manage real-time peer-to-peer connections with the websites they visit.
WebRTC basically enables voices and video communication to work inside web pages, without the need to add any extensions to your browser.
As the Covid-19 pandemic made working from home and other remote communications a necessity, there's been a huge surge in its use. Today, WebRTC is widely popular for video calling and data transferring applications.
Although users can find WebRTC technology really useful, its intrinsic vulnerabilities pose a threat to those concerned of their privacy - whether or not they are using a VPN.
When does a WebRTC leak occur?
It's worth noting from the outset that for WebRTC to work, it must expose your IP address in order to establish its connections. A leak then accordingly occurs when you are trying to establish communications with someone through a browser that uses WebRTC technology. So if you're somebody who is privacy conscious or doesn't like the idea of being tracked as you navigate the internet, this is likely to be of alarm.
And even if you're a conscientious web user who takes care to cover their tracks by using a VPN, WebRTC leaks can still bypass the encrypted tunnel through which your VPN is supposed to protect your privacy. If a leak occurs, your real IP will be then revealed.

How to prevent WebRTC leaks
Thankfully, there are a few tips and tools that can help you prevent these leaks.
The first step for people already using a VPN is is to see whether your real IP address is actually leaking . Carrying out a test is one of the best ways to prevent WebRTC leaks from endangering your privacy, and it's really simple:
- If you have one, disconnect your device from the VPN service
- Note down your IP address - you can simply find it out by searching 'What’s my IP' on the internet
- Exit the browser
- Re-connect to your VPN
- Refresh the page and look for your IP again on a WebRTC leaks online checker . Among those, there are ipleak.net – which also tests for IPv4, IPv6, and DNS leaks - BrowserLeaks WebRTC test and Perfect Privacy WebRTC test . Plus, Some VPN providers like ExpressVPN offer their own WebRTC Leak Test to make monitoring breaches even easier.
If your IP is not being revealed, it should come out a completely different address each time. But if the the series of numbers is the same, a WebRTC leak is likely exposing your IP address.
It is worth mentioning that WebRTC leaks can vary per browser. So if you use Chrome and Firefox for instance, you should test both. You may also want to verify your results by checking your IP address on different platforms.
Once you are sure that there is a WebRTC leak affecting your browser, you have some options to secure your online privacy:
1. Disable WebRTC on your browser
Depending on which search engine software you're using, the process to follow will be different.
Disabling WebRTC technology on Microsoft Edge couldn't be any easier. Simply type into the address bar about:flags to enter the settings. Scroll down and enable the option Hide my local IP address over WebRTC connections before restarting the browser.
Also doing so on Opera is quite intuitive. Open the settings on the left window and tap on Privacy & security . Head down to the section WebRTC and enable the option Disable non-proxied UDP . Restart then the search engine.
With Safari, go to Preferences and click on the Advanced tab. Here, check the box saying Show Develop menu in menu bar . Click on Develop in the menu bar and head on Experimental Features tab you can find in the drop-down menu. Scroll down to disable the WebRTC mDNS ICE candidates option.
If you are using Firefox, write on the search bar about:config . A warranty warning will appear, click on Accept the risk for carry on. At this point tap on Show all . You will see a long list of settings - be careful not to mess them up. To make it easier, search for media.peerconnection.enabled in the top bar. Press the Toggle button on the right so that the value in the middle will be identified as False .
If WebRTC tech can be disabled in Google Chrome for Android via the URL chrome://flags/#disable-webrtc , it cannot be switched off for the desktop version. That's where you must add a dedicated browser extension.
It is worth nothing that Chrome on iOS does not seem to apply the vulnerable parts of WebRTC technology responsible to expose local or external IP addresses - for now, at least.
2. Use a browser extension
Adding a browser extension to your search engine software can be an effective way to prevent WebRTC leaks from happening. As we mentioned before, it may be the only way if your browser doesn't permit switching it off.
Compatible with Chrome and Chromium browsers, WebRTC Leak Prevent prevents WebRTC leaks by controlling hidden WebRTC privacy settings.
While WebRTC Leak Shield protects you from this security threat by disabling the WebRTC technologies and prevent IP leaks.

3. Choose a better VPN service
While many providers claim to prevent WebRTC leaks, many fail to do so. But the good news is that the best VPNs work hard to protect users from WebRTC leaks in their apps.
The ExpressVPN browser extension - currently available from Chrome, Firefox and Edge - is meant for protecting your privacy by preventing websites from discovering your true IP address and location. Among the providers offering a similar feature there also are NordVPN , Surfshark and Avast SecureLine VPN .
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!

Chiara is a multimedia journalist committed to covering stories to help promote the rights and denounce the abuses of the digital side of life—wherever cybersecurity, markets and politics tangle up. She mainly writes news, interviews and analysis on data privacy, online censorship, digital rights, cybercrime, and security software, with a special focus on VPNs, for TechRadar Pro, TechRadar and Tom’s Guide. Got a story, tip-off or something tech-interesting to say? Reach out to [email protected]
Surfshark drops new Apple TV VPN app
The best travel VPN in 2024
Quordle today – hints and answers for Sunday, April 21 (game #818)
Most Popular
- 2 I’ve seen Sony’s impressive new mini-LED TV backlight tech in action, and OLED TVs should be worried
- 3 Scientists at KAIST have come up with an ultra-low-power phase change memory device that could replace NAND and DRAM
- 4 Billions of Discord chats have been harvested, set to be sold online
- 5 I listened to Sony’s new Bravia Theater Quad system, and it's full-fat Dolby Atmos without wires
- 2 The latest macOS Ventura update has left owners of old Macs stranded in a sea of problems, raising a chorus of complaints
- 3 Disney Plus' possible cable-style Star Wars channel plan proves we're never getting rid of cable
- 4 Bosses are becoming increasingly scared of AI because it might actually adversely affect their jobs too
- 5 Apple's M4 plans could make the latest MacBooks outdated already

How to Stop a WebRTC Leak on Your Favorite Browser
DataProt is supported by its audience. When you buy through links on our site, we may earn a commission. This, however, does not influence the evaluations in our reviews. Learn More .
Affiliate Disclosure
DataProt is an independent review site dedicated to providing accurate information about various cybersecurity products.
DataProt remains financially sustainable by participating in a series of affiliate partnerships - it is visitors’ clicks on links that cover the expenses of running this site. Our website also includes reviews of products or services for which we do not receive monetary compensation.
DataProt's in-house writing team writes all the site’s content after in-depth research, and advertisers have no control over the personal opinions expressed by team members, whose job is to stay faithful to the truth and remain objective.
Some pages may include user-generated content in the comment section. The opinions expressed in the comment section do not reflect those of DataProt.
As we have moved so much of our lives online, privacy has become a priority. For that particular reason, we at DataProt advise using one of the recommended VPN services to protect your information and privacy. However, not everything can be solved with a gadget-like extension or app. It’s important to familiarize yourself with potential breaches and vulnerabilities some VPNs have; a WebRTC leak is one of the most common ones.
WebRTC: What Is It and Why It’s Useful
WebRTC (Web Real-Time Communication) is open-source software that’s free to use and add through JavaScript APIs (Application Programming Interface) to allow for video and audio communication through P2P (peer-to-peer) protocols.
The technology reduces video and audio lagging, even for large files. WebRTC is an excellent choice for software enabling group calls and webinars with improved sound quality. Now that we have answered: “What is WebRTC?” we’ll move on to analyzing why it represents a potential privacy issue.
WebRTC and IP Address Leaks
WebRTC is supported by modern browsers like Chrome, Firefox, Safari, Opera, Brave, Edge, etc. Because of browser vulnerabilities, leaving your public IP address unprotected may cost you your anonymity through a WebRTC STUN (Session Traversal Utilities for NAT) server request, even though your VPN is properly functioning.
Windows makes it possible to send data over routes that weren’t set up as the default ones, and a STUN server sends requests to any interface it can reach from the user’s side. A UDP packet can sometimes include your actual IP address, and a WebRTC IP leak is the result of that.
Testing for Leaks
Thankfully, plenty of services online test for potential leaks so you can diagnose your VPN. According to our tests, ExpressVPN prevents IP leaks and has an online service for checking if WebRTC is enabled and if the IP address is encrypted and tunneled through VPN. Websites like BrowserLeaks test WebRTC as well, and you can get an in-depth report.
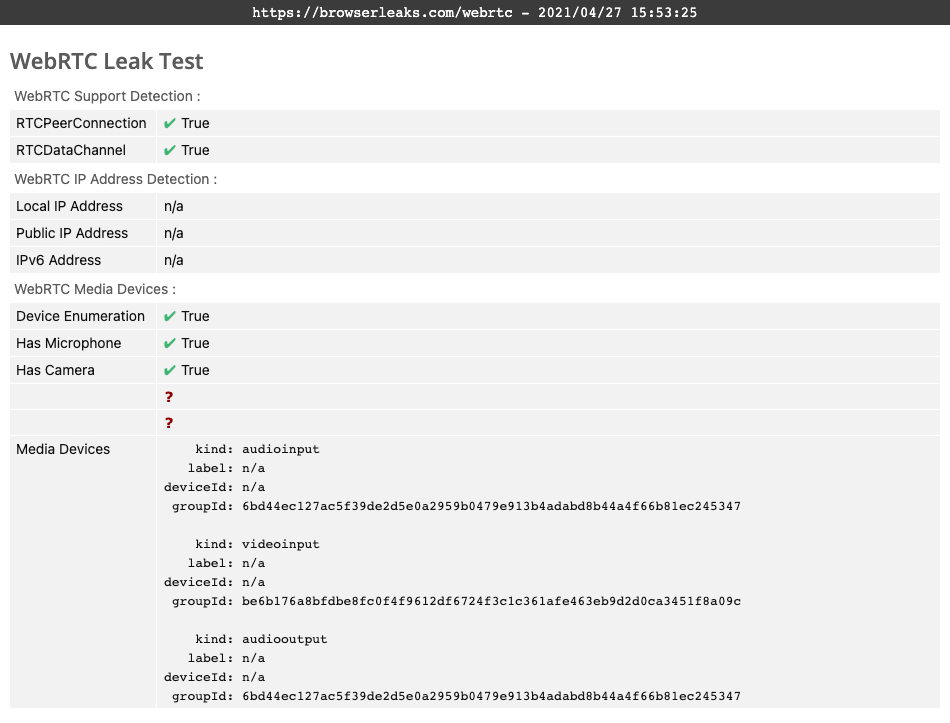
If your VPN service is working correctly, your report should show something similar to the one displayed here.
How to Prevent a WebRTC Leak in Chrome
The most straightforward way of preventing WebRTC from leaking your IP address is to use a VPN with a Chrome extension. However, if you are not looking to solve the leak issue with a VPN service, you need to know that you can’t disable it manually. Instead, you will have to use an external solution. While VPN extensions are more reliable, there are few free non-VPN options available. Also, keep in mind that, besides dealing with WebRTC, these extensions don’t protect your privacy further.
WebRTC Leak Shield
This is a Chrome browser extension with a simple interface, as you can see from the screenshot.
The only options available are to turn the shield on or off and run the extension’s leak test. After conducting a few tests of our own, we found that the extension reliably shielded us from public IP address leaks through WebRTC services. However, unlike a VPN, the extension doesn’t encrypt your connection, nor does it hide your IP address during your online browsing experience. This is something you need a virtual private network for.
The extension is also available for Microsoft Edge users and can be found on the Microsoft Edge Add-ons page.
WebRTC Leak Prevent
This is another go-to solution a large number of Chrome users prefer. When you add the extension to Chrome, it will present you with a few options.
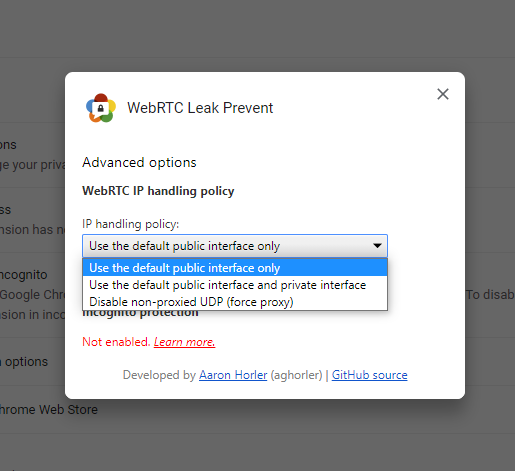
The first option that uses the default public interface will route WebRTC traffic directly through the VPN adapter. The second option will also use the default network adapter for your local network. The third option forces the use of a proxy and only allows for WebRTC traffic over UDP proxies. It can also affect your WebRTC communication and can end up disabling it altogether for some users.
Stopping a WebRTC Leak in Firefox
Unlike Chrome, Firefox does allow for these WebRTC related settings to be changed within the browser. It just takes three simple steps:
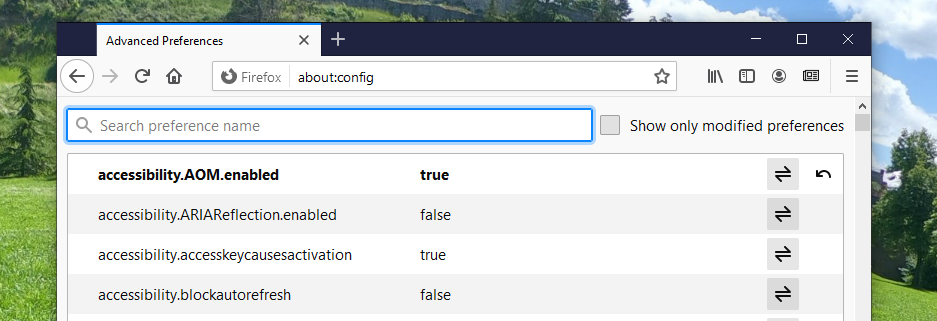
Remember to check these settings regularly after updating Firefox, since updates can sometimes revert it to default, i.e., turn it back on.
How to Disable WebRTC in Safari
Safari takes a more cautious approach than Chrome and Firefox by blocking camera and microphone access by default. Therefore, the only potential leak you need to worry about with this Apple product is not that severe. To turn off WebRTC, you will need to do the following:
- Open Safari;
- Open Preferences and find the Advanced tab;
- Check the option that says “Show Develop menu in menu bar.”
- From the Develop drop-down menu, go to WebRTC;
- Mark the option called “Disable Legacy WebRTC API.”
How to Disable WebRTC on Android and iOS
The option for disabling WebRTC directly through the Android version of Chrome isn’t currently available. We have tested solutions that have worked for previous versions of the browser, but with our test phone running on Android 11 and Chrome version 90.00.4430.82, it wasn’t possible.
At DataProt, for that particular reason, we recommend using a dedicated Android VPN. Users with a tendency of connecting to public Wi-Fi need to think about their security and privacy even more.
Unfortunately, the situation with iOS is similar to Android. To prevent a WebRTC Leak, you will have to see what VPN for iOS is the best fit for your needs.
Further reading

How to Use ProtonVPN: A Step-by-Step Guide

Does NordVPN Work with Netflix in 2024? YES! It Does
Leave a comment.
You must be logged in to post a comment.
What Are WebRTC Leaks and How Can You Prevent Them?
Your real IP address could leak thanks to WebRTC. Here's why that's bad for your privacy and what you can do about it.
WebRTC (Web Real-Time Communication) is an open-source technology that enables peer-to-peer communication in web browsers and similar applications.
Initially released in 2011, WebRTC eliminates the need for browser plugins and third-party software. If you've ever used Discord or Google Hangouts, for example, you've used a WebRTC-powered service.
But there's one problem with WebRTC: the possibility of IP address leaks.
What's a WebRTC leak?
Tech giants such as Google, Microsoft, and Apple use WebRTC. Most browsers nowadays use this technology as well, which means there's always a chance your IP address (a string of characters unique to your computer or network) leaks without you knowing. But what are WebRTC leaks exactly, and how would one take place?
Let's say you're using a VPN to browse the internet, whether to protect your privacy or just because you need to bypass geographical restrictions. A good VPN uses strong encryption, obscures your real IP address , and spoofs your location, making it seem like you're based in a different country and thus protecting your privacy.
But even with a VPN turned on, a browser using WebRTC technology may be leaking your real IP address. So if you're trying to video chat with somebody through your browser, or talk through Google Hangouts, WebRTC might be bypassing the protections you've put up and leaking your real IP address.
WebRTC leaks don't just defeat the purpose of using a VPN, but also represent a major security vulnerability that a competent threat actor could exploit, were they to intercept your communications in some way. For example, they might launch an IP spoofing attack and deploy malware to your computer.
How to Check If WebRTC Is Leaking Your Real IP Address
If you don't have VPN software installed, your real IP address is visible regardless of which browser or device you're using. But, as explained above, even if your VPN is on, your IP address might be visible due to a WebRTC leak.
Here's how to check if your IP is leaking.
The first thing you need to do is disconnect your VPN, and then head over to a site like WhatIsMyIP —here, you can easily check what you real IP address is.
After you do that, turn on your VPN and go to BrowserLeaks . This is a free online tool anyone can use to test their browser for different types of security and privacy issues. Once on the BrowserLeaks website, navigate to WebRTC Leak Test . Click the hyperlink, and let the page load. Your real IP address will be displayed here.
What you need to do next is repeat the process with your VPN turned on. So, turn on your VPN, go to BrowserLeaks, and launch the WebRTC Leak Test once again. If your VPN is doing its job properly, your real IP address will not be visible.
This test was conducted on ProtonVPN, which—as you can see below—does not seem vulnerable to WebRTC leaks. Instead of showing our real IP address, it's showing the IP address of a random server it connected to in the Netherlands.
Evidently, using a safe and reliable VPN is a good way to prevent WebRTC leaks, but to ensure maximum protection you should disable WebRTC in your browser.
How to Disable WebRTC In Your Browser
The good news is, it's possible to disable WebRTC in many popular browsers, and so prevent leaks. Here's how to disable WebRTC in Chrome, Firefox, and Safari.
How to Disable WebRTC In Chrome
It is not possible to manually disable WebRTC in the Chrome browser. However, there are several free extensions that can do just that. WebRTC Leak Prevent is one of them. It's available on the Chrome Web Store , and should work in most Chromium-based browsers, including Brave. All you need to do is install the extension and turn it on.
How to Disable WebRTC In Firefox
If you're using Firefox, launch the browser and type "about:config" in the address bar and hit Enter . If you see a warning page, click the Accept the Risk and Continue button. Next, type "media.peerconnection.enabled" in the search box. Change the value from true to false by pressing the toggle button.
How to Disable WebRTC In Safari
If you're using Safari, you can disable WebRTC in the Preferences menu. Once you enter it, navigate to the Advanced tab at the bottom, and check the Show Develop menu in menu bar box. After that, click Develop and select Experimental Features . Find WebRTC mDNS ICE candidates , and click on it to disable WebRTC.
Disabling WebRTC: What to Keep In Mind
After you disable WebRTC in your browser, head over to BrowserLeaks once again to check if your IP address is leaking. Conduct the test with and without your VPN turned on. If you followed the steps outlined above, your real IP address should not be visible in BrowserLeaks' WebRTC Leak Test.
However, keep in mind that disabling WebRTC in your browser does not come without its downsides. Doing so may cause websites and services that use WebRTC technology to malfunction, or not work at all. In any case, you can refer back to this guide, and enable or disable WebRTC however you deem fit.
Using a good VPN and disabling WebRTC are certainly steps in the right direction if you want to boost your security and privacy. But there are other things you can do to protect yourself online; switch from Chrome or Microsoft Edge to a more secure browser , start using encrypted email services and chat apps, and familiarize yourself with Tor.
Prevent WebRTC Leaks to Stay Safe
WebRTC is an ambitious project that will likely stick around for years to come. As useful and convenient as it is, it does have some security issues that need to be addressed. If you want to protect your online privacy, you should probably consider disabling WebRTC in your browser.
And if you're using a VPN, make sure it does a good job protecting you from different types of leaks. However, leak protection is not the only feature you should look for when choosing a VPN provider, so do your research accordingly before making any major decisions.
VPNoverview.com Privacy Anonymous Browsing WebRTC and WebGL Leaks: How to Fix and Prevent Them
WebRTC and WebGL Leaks: How to Fix and Prevent Them
Countless users will tell you they downloaded a Virtual Private Network (VPN) so they can be more anonymous online . Whether it’s bypassing oppressive government censorship or dodging unwanted online trackers, protecting one’s identity has become paramount in today’s online world.
But two persistent and sneaky vulnerabilities remain — WebRTC (Real-Time Communication) and WebGL (Graphics Library) leaks. WebRTC can give away your true location through your IP address, while WebGL can leak information about your device. If you use a weak VPN service and standard settings on popular browsers (like Chrome) these leaks can still happen today. They can also put your privacy at risk through browser fingerprinting .
Our tests found that Surfshark and NordVPN consistently block WebRTC leaks.
If you’re looking to seal WebGL leaks, you’ll need to get a good private browser or adjust the settings on your current one. Whichever route you’d like to take, we’ve got you covered in our full guide below on WebRTC and WebGL leaks and how to fix and prevent them.
A Virtual Private Network (VPN) protects your data from hackers, advertisers, and other unwanted online trackers while keeping your privacy intact. VPNs do this by encrypting your internet traffic and assigning you an anonymous IP address . Unfortunately, online surveillance techniques are constantly evolving and becoming more sophisticated.
Not all VPNs are created equal, either. With a subpar service, parts of your identity could still be traced using browser fingerprinting , which makes use of WebRTC and WebGL leaks .
In this article, we’ll explain exactly what WebRTC and WebGL leaks are and why you need to be wary of them if you want to be completely anonymous online.
Browser Fingerprinting and WebRTC and WebGL Leaks
In order to protect your online privacy, you’ll have to stop this form of tracking. Browser fingerprinting attempts to assign a unique profile, or “fingerprint,” to your device based on your browser and settings.
Once you’ve been “fingerprinted,” online trackers can collect your internet patterns , behaviors , and interests — a serious privacy invasion that could be used for advertising or other purposes. WebRTC and WebGL form a crucial part of this fingerprint.
What are WebRTC and WebGL?
These plug-ins were introduced to enhance your overall browsing experience and provide compatibility with other programs. Unfortunately, they also decrease your online anonymity . While WebGL is generally a strong indicator of your browser’s capabilities and other hardware information, WebRTC will sometimes accidentally leak your real IP address — revealing your true location.
WebRTC (Web Real-Time Communication)
WebRTC is a critical software specification for incorporating real-time streaming elements between browsers and devices via the HTML5 standard. Essentially, it is needed for audio and video (peer-to-peer) communications on the web.
Thanks to modern APIs (bundled software functions) WebRTC enables you to video chat directly from your browser , so you don’t have to install video conferencing software, like Skype or Zoom.
WebGL (Web Graphics Library)
WebGL, on the other hand, enables hardware rendering of 3D graphics within your browser , if your computer is capable. While WebRTC leaks your public IP address, WebGL can leak information about your device’s hardware — like your device’s operating system (OS) and browser.
Websites use all of this information to construct the unique “fingerprint” used to identify you.
How Does WebRTC Leak My Real IP Address?
One of the main reasons people use a VPN is to hide their real IP address . This helps them remain anonymous and secure. But WebRTC has access to your real IP address . Once your browser asks for permission to connect to your camera or microphone, your public IP address has to be transmitted in order to establish the connection. This direct connection allows you to easily video chat within the browser, but it also betrays your real location.
Sometimes, the peer-to-peer functionality of WebRTC has to send out your real IP address in order to work in what is known as WebRTC peering. Some VPNs will hide a computer’s public IP address from WebRTC , but not all manage to do so.
Which VPNs Protect You Against WebRTC Leaks?
Other VPN providers are capable of neutralizing WebRTC leaks but aren’t consistent enough to stop them entirely . Most budget or free VPN providers don’t even try to stop WebRTC leaks. If you’re looking for top-tier security and anonymity, this problem emphasizes the importance of choosing a reliable and established VPN , rather than just searching out a freebie.
Surfshark: Protection against WebRTC leaks, top speeds, best price

Surfshark is one of the best VPN providers at the moment. It is also, interestingly enough, one of the cheapest. Throughout our tests (we’ll show you how to do those yourself later), it repeatedly kept us safe from WebRTC leaks . Surfshark also has over 3,200 servers in 65 countries around the world, all offering top speeds and secure connections.
It works with some of the strongest encryption protocols available and allows you to simultaneously connect with as many devices as you’d like. Surfshark is a great VPN for WebRTC leak protection , has top-of-the-line security features, great speeds, and an unbeatable price. You can try it out for 30 days by taking advantage of Surfshark’s free money-back guarantee .

Save 84% and pay only $ 2.49 a month!
- Very user-friendly and works with Netflix and torrents
- 30-day money-back guarantee. No questions asked!
- Cheap with many extra options
NordVPN: Seals WebRTC leaks, top security protocols at lightning-fast speeds

NordVPN is another of our favorite, security-geared VPN services. It is affordable, offers over 5,400 servers in 50 countries all across the globe, and works on nearly all operating systems. They have a strict no-logging policy , and also prevent WebRTC leaks consistently and reliably , so you can be sure your data is safe and remains anonymous .
Besides that, NordVPN is easy to install and has a clear, user-friendly interface, making it pleasant software to use on a daily basis. You can try NordVPN out free for 30 days to see if you’d prefer its WebRTC protection over Surfshark’s.

Save big with up to 58% off a two-year subscription!
- Fast and large worldwide network of VPN servers
- Perfect for privacy and streaming
- Trusted by many, with over 14 million users
How Do I Check Whether My Browser is Leaking Private Information?
Check WebRTC leaks
If you’re checking for WebRTC leaks, it’s especially important to check if your real public IP address is exposed. When we used NordVPN and Surfshark on these sites, our WebRTC IP address showed up as the VPN’s anonymous IP, and not our true IP — which is exactly the outcome you want.
Your public IP address is the address you send out to any other online entities, such as websites, cookies, trackers, etc. Some of the best testing sites are:
- Browserleaks (offers tests for WebRTC and WebGL leaks)
Check WebGL leaks
VPNs can protect your true location and identity, but unfortunately, WebGL can still give away some information on your hardware, like your browser and operating system. You can check exactly which information you’re leaking with Browserleaks . While WebGL doesn’t give away your IP address like WebRTC has a tendency to do, it does contribute to creating a unique browser fingerprint.
In the table below, you can see a number of WebGL functions taken from the Microsoft Edge browser as well as Firefox. Take notice that as Firefox is a more privacy-oriented browser, there are fewer functions than Edge.
How Do I Prevent WebRTC and WebGL Leaks?
Using a top-tier VPN service like Surfshark or NordVPN is the starting point for preventing WebRTC and WebGL leaks. These VPN providers have built-in protection against such leaks — especially WebRTC. However, VPNs cannot make up for all information points being leaked. This has to be manually adjusted by the user for each browser, to whatever extent is possible.
Of course, if you choose to use a subpar VPN, or no VPN at all, it’s necessary to download and install a special extension, like uBlock Origin.
uBlock Origin

To prevent potential WebRTC leaks, you can use uBlock Origin. This is a reliable and trusted adblocker that is often regarded as one of the best free adblockers on the market . It’s completely free to use and works on Safari, Opera, Edge, Chrome, Firefox, Brave, and Epic Privacy Browser .
Simply download the extension to your browser, and you’re ready to go. You’ll be protected against most forms of online tracking and won’t have to see as many annoying ads as usual. uBlock Origin also easily disables the WebRTC functionality. All you have to do to make sure you’re protected is change a setting. Here’s how you do that:
- Click on the extension in the top-right corner of your browser.
- Click on the Settings icon on the far right, just below the big on/off switch.
- Check the box “ Prevent WebRTC from leaking local IP address ,” which is the third item under the “ Privacy ” tab.
Once you’ve done this, you can rest assured your browser leak your local IP address by means of WebRTC. You can now re-check if you are leaking with one of the checkers linked above.
WebRTC and WebGL Protection By Browser
Your browser can make a real difference when it comes to the amount of WebGL information that is being sent out . Because of that, the steps you have to take to protect your online traffic from WebRTC and WebGL leaks differ depending on which browser you have.
Below, we’ll show you how to improve your privacy on the most popular browsers out there today.

We’re leading with Firefox because it’s the most easy-to-use, privacy-oriented browser we’ve come across. You can customize this browser as much as you’d like , and we’ve even compiled a complete guide on how to set up Firefox as an anonymous browser . Once you’ve changed those settings, only the Tor browser will offer more anonymity.
To withstand WebRTC and WebGL leaks and browser fingerprinting specifically, there are four important settings to tweak:
Setting 1: Block content and trackers
This setting will help you stop trackers and cookies from following you across the web. Click on the information symbol (the circle with the “i” in the middle) on the left side of the address bar. You’ll be shown this menu:

Click on the wheel on the right side of “ Content Blocking ,” right next to “ Custom .” Select the option “ Custom ” and check the boxes before “ Trackers ,” “ Cryptominers ,” and “ Fingerprinters ” as shown in the image below.

You could also check the box in front of “ Cookies ” and choose “ Cookies from unvisited websites ” from the dropdown menu. This stops cookies from websites you haven’t visited from tracking you across the web. It’s even possible to block all cookies from third-party trackers, but this will seriously limit the browser’s ability to load a large number of websites.
Setting 2: Turn off WebRTC functionality
To prevent WebRTC leaks, type in “ about:config ” in the browser’s address bar and press Enter . You’ll be shown a warning, stating that changes you make might derail the browser. As long as you follow the steps lined out here and don’t change any additional settings, you won’t have to worry.
Click past the warning and type “ media.peerconnection.enabled ” in the search bar, as shown in the picture below. This setting is by default set to “ True .” Right-click this setting and click “ Toggle ” to switch the value to “ False .”

Setting 3: Turn off WebGL
Similarly to turning off WebRTC, you can disable WebGL by typing in “ about:config ” in the address bar and searching for “ webgl.disabled .” Toggle this setting to “ True ” by right-clicking on the toggle button to the right. Restart Firefox and you should’ve turned off WebGL.
Setting 4: Use the Trace extension
Trace is a browser extension that allows you to spoof different settings that make up your browser fingerprint . Although adding an extension to your browser goes a bit beyond changing basic settings, it can be very useful and we would heavily recommend it if you worry about browser fingerprinting.
The Trace extension gives you many different options to adjust your fingerprint. You can adjust your “Canvas,” “Audio,” “Screen Resolution,” “Hardware,” and many other functions. The picture below gives an idea of what this extension looks like.

Once you’ve added Trace to your browser, you can find the settings by clicking the extension in the top right corner. This will open a new tab, where you’ll have to click on Settings again.
Next, you can turn on “ Trace Features ,” “ WebRTC Protection ,” and “ WebGL Fingerprinting Protection .” Your browser fingerprint will now no longer be as unique as before, which increases your online privacy.

However, there are many options to improve Chrome’s security . The easiest way is to add a number of extensions that allow you to spoof your WebRTC and WebGL settings.
There are multiple options available for WebRTC spoofing. Simply pick one of the extensions listed below and add them to your browser.
- WebRTC Protect
- WebRTC Network Limiter
- WebRTC Control
- WebRTC Leak Prevent
At the time of writing, there is only one extension that effectively helps you tackle the WebGL problem, and that’s WebGL Fingerprint defender .

The Brave browser runs on Chromium, an open-source project by Google. This means that all Google Chrome extensions also work for Brave . If you want to make this browser safer by adding extensions, you can use all of the programs mentioned above.
Additionally, you can play around with the settings in Brave to better protect yourself against cookies, trackers, and WebRTC leaks . Here are a few ways in which you can do that:
- Use an anonymous search engine such as DuckDuckGo , Qwant, and Startpage. Make sure to set it as your default search engine . Don’t use Google, as Google is one of the biggest data harvesters in the world.
- Go to “ Settings ” by clicking on the three stripes in the top-right corner of your browser. Scroll down to the section “ Shields ” and enable “ Upgrade connections to HTTPS .” An HTTPS connection is safer than HTTP, so this option will help you protect your online privacy while browsing.
- You could also check to see if you can “force” secure HTTPS connections under Privacy and Security if it is listed.
- At the “ Cookies ” section of your settings, select “ Only block cross-site cookies .” This will keep websites from following you across different parts of the internet.
- Scroll down and go to “ Additional Settings .” Check the option “ Safe Browsing ” if it is listed.
- Minimize the chance of WebRTC leaks by selecting “ Disable non-proxied UDP ” underneath “ WebRTC IP Handling Policy .” You could also choose to select one of the less safe options, such as “ Default public interface only ” or “ Default public and private interfaces .” These options allow the browser to load certain WebRTC functions if a website requests it. However, they will also increase the risk of leaking private information. That’s why we recommend going for the safest option and disabling the function altogether.
- Under the “ Shields ” tab you will find a “ Block fingerprinting ” option. Set that to “ Strict .”
- In that same area, set “ Trackers & ads blocking ” to “ Aggressive .”
- In the “ Privacy and security ” tab, untick any analytics, diagnostics and usage options .

The standard settings of Safari are set to block website requests that seek access to your camera or microphone. Default settings also hide your IP address. Because of that, you won’t have to worry too much about WebRTC leaking your real IP address .
Even so, you can completely disable WebRTC functionality in the settings, if you want to make sure your information stays safe. First, go to the Safari main menu. Under the “ Develop ” tab, go to the “ WebRTC ” tab and make sure “ Legacy API ” is disabled.
Secondly, in the settings, you can visit the “ Experimental Features ” section under the “ Develop ” tab. Here you can disable all features relating to WebRTC and WebGL except the “ profile 2 codec .” You can also disable the “ VP9 codec .” If for any reason you experience an issue with your browsing, write down what you’ve disabled so that you can turn it back on.
It’s also possible to install uBlock Origin. If you’re specifically looking for protection against potential WebGL fingerprinting, however, you’d be better off using a different browser.

Apart from adding uBlock Origin to your Opera browser, it’s also possible to alter the settings to increase your online safety.
To do so, type “ WebRTC ” into the search bar in the Settings menu. You will be shown four options, which correspond with four different levels of safety against WebRTC leaks. Set the WebRTC function to “ Turn off proxied UDB .” Just as is the case with the Brave browser, you could also pick one of the other three options. However, this does mean that your browsing experience will be slightly less safe.

This browser also allows you to visit the dark web , although that can be very dangerous without taking the right safety measures .
Thankfully, the Tor browser is not susceptible to most WebRTC and WebGL leaks . The basic settings of Tor are so strict that the average user won’t need to install any extra extensions. Once you’ve turned off JavaScript in the “Safest” mode, you will be safe from most forms of online tracking.
However, the “Safer” mode will be more than enough for most. This doesn’t mean Tor is invulnerable to leaks or other vulnerabilities. If you want to learn more about these vulnerabilities, you can read our article on the safety of the Tor browser .

Microsoft Edge is undoubtedly the best and safest browser Microsoft has released so far. Unfortunately, Edge is less resistant to potential WebRTC and WebGL leaks than some other browsers. Edge uses these protocols by default and doesn’t allow you to disable them.
Should you want to continue using Edge, it’s best to protect yourself with other extensions such as uBlock Origin or the NordVPN browser extension.
Wrapping Up: Test Your Anonymity
The internet allows for a tremendous amount of information about its users to be stored and collected. This is done through website trackers, cookies, fingerprinting, and more. As a frequent internet user, it’s good to be aware of the different types of online identification that exist and the options available to protect yourself.
Each browser and VPN has its own strengths and weaknesses. We recommend checking out our list of the best internet browsers for your privacy , and couple that with either Surfshark or NordVPN , and you’ll be well-protected against WebRTC and WebGL leaks.
After you’ve made these tweaks, you can revisit one of the anonymity checking sites via the links above and see if your WebRTC leak is sealed, and your anonymity score has improved. Need one more tip for the road? Most browsers will even perform better when these adjustments are coupled with the “ Incognito ” or “Private” browsing modes.
Got a question about WebRTC or WebGL leaks? We may have answered it already below.
WebRTC (Real-Time Communication) is a plug-in to makes it possible to stream peer-to-peer audio and video directly through your browser, rather than a video calling app. While WebRTC makes video calls more convenient, it has been known to accidentally leak true IP addresses. If you need a VPN with full WebRTC protection, make sure to read our full guide on WebRTC and WebGL .
To disable WebRTC, you’ll need to adjust your browser settings. We’ve compiled step-by-step guides on how to tweak settings on popular browsers like Firefox, Chrome and Brave, among others, in our full guide on WebRTC and WebGL leaks . If you’re concerned about WebRTC leaks, there are only a select few VPNs that we’ve found consistently provide protection.
WebGL (Graphics Library) is a plug-in that enables hardware rendering of 3D graphics in your browser. Though this extension improves your browsing experience, WebGL can leak hardware information about your devices — such as its operating system and browser. Check our full guide on WebRTC and WebGL leaks for more information and fixes.
VPNs with weak security measures will not stop WebRTC leaks. You’ll need a premium service with high-level security protocols. We’ve found that NordVPN and Surfshark both offer consistent protection against WebRTC leaks, keeping your true IP address from being discovered by online trackers.

David Janssen Author
Cybersecurity analyst.
David is a cybersecurity analyst and one of the founders of VPNOverview. Since 2014 he has been gaining international experience working with governments, NGOs, and the private sector as a cybersecurity and VPN expert and advisor.
Share this article
More articles from the anonymous browsing section.

Kanary Review (2024): A Cheap and Secure Data Removal Service

OneRep Review (2024): Can OneRep Protect Your Private Data?

The Best Data Removal Services (Personal Information Removal Made Easy)
Explain what the acronyms mean up front, at the top, otherwise we are left dangling, so to speak, without the key thing you are painstakingly explaining. Otherwise, thanks. Good stuff. Sad I have to lie and make up name and email. The whole point of visiting you is to maintain best practices before doing other things. Surrendering info unnecessarily results in the opposite. I do not like to lie at all. Roger?
Thank you for your feedback! The reason we ask you to leave a name and email is so we and other readers are more easily able to navigate the comments and make sense of conversations. Your email won't be shared with anyone - it's just to notify you when someone replies to your comment. We understand that many of our users will not use their real names and emails, and we even encourage this: privacy is one of our main concerns, after all. You're always welcome to use a private and anonymous email, such as ProtonMail , as well.
Looking for a VPN?
Take a look at our overview of the most trustworthy, fast, and safe VPN services. Extensively tested by our experts.

What Is WebRTC And How To Disable It From Your Browsers
All information on this site is harmless and purely for educational purposes, which is why we post only authentic, unbiased information! The affiliate links are really there for discounts for our readers and for us to earn small commissions that help us stay afloat! Thanks! read more …
Webrtc Leak Became A Huge Disaster, Especially When You Were Behind The VPN Firewall. But There Is A Way To Disable It.
Your online experience greatly relies on WebRTC as it allows you to establish real-time communication (that’s where it gets its name from) and transmits information between websites and browsers. There are a variety of applications that utilize WebRTC technology. For instance, while using Google Meet to conduct a virtual meeting, you are using WebRTC. Similarly, you are also accessing it for video calls made via Facebook Messenger. Using Discord also requires access to WebRTC.
When most of your online activities are linked with WebRTC, it becomes challenging to acknowledge its drawbacks and security concerns. Instead, you focus more on its advantages and the ways you can utilize it, no matter its consequences. However, we are here to warn you against precisely that, as the negative impact of WebRTC isn’t minor enough to be ignored. Instead, it has the potential to compromise your privacy and leak your private data.
It makes no difference which web browser you employ for internet access since WebRTC operates on every single one of them. However, you can successfully disable WebRTC from your browser with the proper guidance, and we’re here to help you fulfill precisely this purpose.
Tip! Use VPN That Prevent WebRTC
It is terrifying to think of a channel bypassing the encrypted tunnel you have built for your security. It is, therefore, best to use a secure VPN that prevents WebRTC leaks such as :
- CyberGhost : allrounder VPN (cheap in price)
- NordVPN : Best For Netflix & Torrrenting
- ExpressVPN : Great speedy servers & security
- Surfshark : smart choice
By using VPN that comes with a built-in feature to prevent WebRTC would not require any other settings mentioned below.
What is WebRTC?
WebRTC is a user-oriented technology that does not require to be run using third-party applications or by additional plug-ins. Instead, it utilizes JavaScript to make it easier to use since it operates directly in the browser and enables video conferences without installing an application. This ability to establish direct links is one of the most prominent reasons WebRTC has established itself as the primary rival to the widely used video-calling applications on the internet, such as Skype or FaceTime.
WebRTC possesses an open-source code, and many major browsers, including Google Chrome, Mozilla Firefox, Microsoft Edge, Apple Safari, and Opera, are actively promoting it as it can be easily upgraded. It lets you share real-time audio, video, and stream data without needing a server that stores and processes data; instead, it links directly amongst client desktops.
One of the most significant features of WebRTC is the decrease in lag for video chat, voice chat, live streaming, and file-sharing in peer-to-peer communication. It also provides superior sound quality than Adobe Flash due to its ability to modify the microphone’s settings.
WebRTC has the potential to be quite helpful for web developers as well as end-users. While we tend to conceive of it as a mere audio and video communication source, its capabilities extend well beyond those of multimodal connectivity. Because of its enhanced adaptability, app developers may include it in non-browser apps as well. However, because of the security issues surrounding its application by several browsers, it is recommended that you leave it disabled unless you are visiting a trustworthy website.

When It Becomes a Problem?
WebRTC indeed enables a flow of data between peers, which is more rapid and has less latency since there is no intermediary to manage the communication between the clients. Even though WebRTC serves as a beneficial tool that enhances your online experience. Nevertheless, due to its peer-to-peer mode of communication, it can also be used for illegal purposes by several websites so that they can establish a direct link between their server and your browser, making your online presence vulnerable.
Browsers need to share both external as well as local IP addresses to establish audio and video connections. This is why enabling WebRTC in specific browsers poses several security issues as it is prone to leaking your IP address. Once someone gains access to your IP address, they can also detect your personal information, location, and even the device you are currently using, putting your privacy at risk.
Consider the following scenario: You are connected to what you think is a ‘secure’ VPN, and so you would like to make a video/audio call to someone; therefore, you will need to utilize WebRTC to do so. This communication is beneficial for you; however, it comes with a high cost. In exchange, WebRTC leaks some of your private information, and your actual IP address starts showing on the website. This violation of privacy defeats the whole point of having a VPN installed in the first place.
Further security breaches carried out by WebRTC:
You thought this was it? Unfortunately, we haven’t even started mentioning the worst-case scenarios implemented by WebRTC yet.
Have you ever accessed a webpage and granted permission to that webpage to use your microphone or camera? You thought you were the one benefitting from the features, didn’t you? Well, in granting access, you may have unknowingly revealed your identity to that website without even realizing it.
WebRTC makes it simpler for third parties to identify your browser, enabling them to monitor your online activity more quickly. It happens because, in addition to your IP address, WebRTC also exposes additional data like your device specifications including things like:
- the browser you are using
- screen resolution of your device
- your device’s operating system.
It enables hackers, advertising companies, or others to imprint you by combining all of your information. We urge you not to dismiss this as a joke or take your privacy lightly. You can mitigate all of these security hazards by simply disabling WebRTC from your browser.
How Can WebRTC Leak IP Address with VPN?
Back in 2015, one of the most severe issues regarding the application of WebRTC in browsers was brought to the forefront by TorrentFreak . They revealed that a significant bug was harming browsers that supported the WebRTC protocol at the time. According to their findings, a security vulnerability was identified in WebRTC that may jeopardize VPNs’ security and reveal users’ public IP addresses to others. The vulnerability, known as a WebRTC Leak, is said to impact nearly all major browsers.
WebRTC can establish a link between a website’s server and your browser regardless of your network or VPN settings. It is a technology that utilizes sophisticated methods to circumvent firewalls and gather information to create peer-to-peer communications; hence, in most cases, VPNs are also not effective enough to prevent leaks. WebRTC leaks arise due to flaws in the technology that enable hackers to execute JavaScript instructions and acquire information about their peers.
There are great chances that WebRTC may leak your IP address even though you haven’t utilized the technology yet. The longer it remains completely active in your browser, the more your system remains vulnerable.
You may believe that WebRTC leaks occur due to the usage of a VPN plug-in in your web browser. However, this is not the case. Even if you utilize a VPN on your router, it won’t make any difference in resolving the leak concern. The only way you can stop WebRTC leaks is by following the procedures outlined below.
How To Disable WebRTC On Chrome?
Chrome does not offer a built-in mechanism for disabling WebRTC on the desktop. Instead, disabling WebRTC on Chrome would require the installation of a third-party browser extension.
- To commence, you need to open the chrome web store.
- You can either access the extension link directly by clicking here . You can also copy the following URL into your address bar https://chrome.google.com/webstore/
- Once the webpage is launched, search for “WebRTC Control” in the search box.
- The required browser extension should come up as the first result in the search.
- To grant access, you just need to click on “Add to Chrome,” which opens a dialogue box for confirmation.
- There, you need to click on “Add extension.”
- The installation of WebRTC Control will take place immediately. With that Chrome will launch a new tab with some more details regarding the browser extension.
You can learn more about the extension by reading up on its information on the web. Apart from that, you can modify its settings by right-clicking on the extension icon that appears on the upper-right side of the browser. All you have to do is make sure that the extension icon has a blue circle around it to complete the process. The blue circle indicates that WebRTC Control is activated and is performing its functions effectively.
As an alternative, you can also install extensions such as “WebRTC Network Limiter , ” “WebRTC Leak Prevent , ” or a script-blocker like ScriptSafe .
How To Disable WebRTC On Firefox?
Just like Chrome, Firefox also offers several extensions that you can use to disable WebRTC. However, there is a far more efficient technique that takes less time and energy. Here’s how you can disable WebRTC on Firefox:
- Enter “about:config” into your browser’s address bar.
- Then, click the “I accept the risk!” option that appears as a warning on the screen.
- This might seem unsafe to you, but we assure you that you will not notice any difference in the performance of your browser as this does not have any negative impact.
- In the search box of the spreadsheet-style screen that appears, enter “media.peerconnection.enabled.”
- That phrase should be the only item that displays on the website right now.
- If WebRTC is enabled, the term “true” will appear on the right-hand side of the row, underneath the heading “Value.”
- You are need to double-click anywhere around the entire row, which will change the value to “false” and ultimately disable WebRTC from Firefox.
Firefox is the only browser that does not necessitate the installation of any extra plug-ins; instead, it offers a quick manual setup without much hassle. This method is also very convenient as you can follow the same procedure to enable WebRTC when required.
Even though this is a much easier method, most users consistently require turning WebRTC on and off depending on their usage, which is why it is much convenient to install an extension called WebRTC Control and simply turn it on or off through the upper corner of your browser by just one click.
How To Disable WebRTC On Safari?
Apple has recently been integrating WebRTC into Safari; however, it is still considered a trial function. Safari is the only browser, along with Internet Explorer, that does not have WebRTC enabled by default; hence, you do not need to disable it unless you have enabled it yourself. Whereas most of the other browsers have WebRTC enabled by default, and regardless of whether you have enabled it or not, you need to disable it urgently.
Even though WebRTC leaks are generally not a part of Safari, disabling WebRTC on Safari is a sensible approach for user privacy. Here’s how you can disable WebRTC on Safari:
- Launch Safari on your device and select “Safari” in the menu.
- Then choose “Preferences” from the drop-down menu.
- After clicking on the “Advanced” tab, scroll down to the bottom of the page and tick the option labeled “Show Develop menu in menu bar . “
- Now, in the menu bar, choose the option “Develop . “
- Then search for the “WebRTC” option, and disable the checkbox for “Enable Legacy WebRTC API” by clicking it.
Alternatively, most devices display a list of options once you click Develop . In this case, click on Experimental Features and select Remove Legacy WebRTC API from the drop-down menu to disable WebRTC on Safari.
How To Disable WebRTC On Edge?
WebRTC and ORTC (Microsoft’s very own version of WebRTC) are both supported by Microsoft Edge. While it is not possible to altogether disable WebRTC on Edge, instead, you can easily conceal your actual IP address.
Disabling WebRTC is much more convenient in Microsoft Edge than it is in other browsers. More precisely, Edge allows you to disable a portion of the WebRTC technology in order to get rid of the particular security risk that emerges as a result of the technology and simultaneously utilize its several other beneficial features. Here’s how you can go about doing that:
- Launch Microsoft Edge on your browser.
- Enter “about:flags” in the address bar, which will open a list of advanced developer settings.
- Scroll down towards the bottom of the page, and you will find an option to “Hide my local IP address over WebRTC connections.”
- That option had been left blank by default. To activate the feature, you need to click the checkbox.
Although you will not be able to disable WebRTC connections fully, you will be able to improve the security. You will be prompted to relaunch Firefox after enabling this feature. The change will not be effective until you do so.
The benefit of this function in Microsoft Edge is that it enables you to utilize WebRTC more efficiently and in a secure manner, without having to turn it on and off for video chat and normal surfing, as you would otherwise have to do.
How To Disable WebRTC On Android?
GOOGLE CHROME: Chrome is widely used by Android users, and hence, your phone is also susceptible to WebRTC leaks. However, androids possess the ability to disable WebRTC manually. You can simply disable WebRTC in Android by the following method:
- Enter the following URL into a Chrome tab: “chrome:/flags/#disable-webrtc”
- Once the site has launched, scroll down to the bottom and search for “WebRTC STUN origin header , “ and then disable it.
- You may also deactivate the WebRTC Hardware Video Encoding/Decoding option as a precautionary measure, but this may not be required in all cases.
MOZILLA FIREFOX: Firefox for Android does not allow you to disable WebRTC. This is due to the fact that as of April 2021, Androids have been denied access to about:config in Firefox stable and beta channels. Though you are able to gain access to about:config in Android if you install Firefox Nightly from the Play Store for free and utilize it in the manner described below:
- Launch Firefox Nightly on your Android smartphone
- Enter about:config in the address bar and press Enter .
- Then scroll down and look for the option media.peerconnection.enabled .
- You must double-tap on this setting to shift it from its default value of ‘True’ and change it to ‘False . ‘
After you make this change to your Firefox Nightly settings on your Android smartphone, all of the peer-to-peer links, such as WebRTC, will be disabled on your device henceforth.
How To Disable WebRTC On iPhone?
You can only disable WebRTC on your iPhone if you have iOS 11 or earlier versions. The option to disable WebRTC in Settings has been eliminated from iOS 12 and later versions of the iPhone.
SAFARI: To disable WebRTC in iOS 11 or earlier versions, follow this process:
- Go to Settings, scroll down towards the bottom of the page and click on Safari .
- Select Advanced from the drop-down menu.
- Choose Experimental Features .
- Now, search for the option to Remove Legacy WebRTC API and tap it so that it turns green, which indicates that the disabling process has been completed in your iPhone.
For Firefox and Chrome in iPhone, you can follow the same methods as listed in the Android section.
Testing WebRTC Leaks
You will want to perform a vulnerability check on your device with a VPN connection as well as without a VPN connection in order to examine the extent of WebRTC leaks thoroughly. This test will assist you in determining whether you and your private data are safe online, allowing you to take necessary measures in order to keep your data protected.
Without VPN Connection:
Once you have disabled WebRTC from your browser, you can head on to examine whether it actually hides your IP address or not. You wouldn’t need a VPN connection for this test. Here’s how you can conduct this test:
- Open your preferred web browser and visit ipleak.net .
- As soon as you launch the website, it will start examining your browser automatically, which might take a minute or so.
- Check the subsection titled Your IP addresses– WebRTC detection .
- If the area displays an IP address, this indicates that the vulnerability is impacting your web browser.
Suppose the subsection indicates “No leak” with or without the VPN connection. In that case, it means your online activity and identity are protected, and WebRTC leaks are not compromising your information.
With VPN Connection:
You might even check whether it is necessary for you to disable WebRTC from your browser when you have activated your VPN connection. This test will also prove whether your VPN connection is secure enough or not. Here’s how you can check for WebRTC leaks with a VPN connection:
- Activate your VPN and establish a secure connection with a server.
- Open your browser again and rerun the WebRTC leak test to see if anything has changed.
- Repeat the same process as above, and if a public IP address still appears, that indicates that you are facing a violation of privacy.
To make it clear, if you are conducting other tests to see your IP address, you need to know that if a local IP address appears after the test, it does not mean that it is a leak. Instead, a WebRTC leak occurs only if your public IP address is displayed.
Final Words
Staying safe and ensuring anonymity on the internet has been an issue under research for quite a while. Even though complete anonymity has not been achieved in most cases, ensuring that you take total preventive measures is essential, and enabling you to do so is our responsibility.
As WebRTC possesses the ability to bypass all the encrypted channels that you have established for your privacy, it is necessary for you to disable it from your browser, despite its many advantages.
Many users, particularly those who are worried about their online privacy, are concerned about WebRTC leaks, which is understandable. However, after following the mentioned steps to disable WebRTC from your browser and establishing a connection with a secure VPN, you will be able to browse and stream the web without any concerns and enhance your online experience even further.
How To Hide Browsing History From ISP, Employer Or Wi-Fi Router (7 Tips)
March 2, 2023
How Secure Is The Avast SafeZone Browser? Let’s Review In 2023
January 1, 2023
How To Encrypt Internet Traffic Or Connection Completly In 2023
July 14, 2022
How to Hide Browser Fingerprinting? Cover Your Tracks
Protect your children’s – internet safety guide for parents, 8 best private browsers to use without being tracked.
July 13, 2022
Kenneth G Aranda
Leave a Comment Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Privacy Tools
VPN Encryption Guide
VPN Reviews
Top Ranked VPNs
Affiliates Disclosure
Editorial Team
© VPNInsights.com 2023
Privacy Policy | Terms Of Service
ExpressVPN security tools
- IP Address Checker
- DNS Leak Test
WebRTC Leak Test
- Password Generator
ExpressVPN not connected Connected Connected
You’re connected to:
UK - London
You may be leaking private information, even if you’re connected to a VPN.
Verify you’re safe using the instructions below .
Try opening this page in a new tab . If you still see a leak, your app may be out of date.
Please refresh the page to try again.
Your browser is not leaking your IP address to the websites you visit.
Prevent WebRTC leaks:
Update your app:
Need help? Contact Support .
WebRTC exposed IP addresses
Your browser is exposing these IPs to websites you visit:
No WebRTC leak detected
ExpressVPN is protecting you from WebRTC leaks.
WebRTC not available
Your browser doesn't support WebRTC or WebRTC has been disabled.
WebRTC Leak Test incomplete
Learn how to disable WebRTC:
How to use the WebRTC leak checker
What’s the difference between public and local ip addresses.
When you use the leak checker you’ll see two classes of IP addresses displayed: public and local .
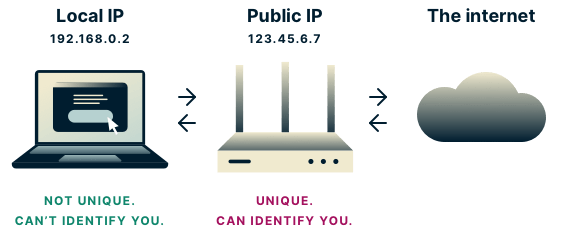
Public IPs are highly specific to you. They form part of your identity on the internet. When you use a VPN, sites see the VPN server’s public IP address instead of yours, and your identity is protected.
However, if WebRTC detects your real public IP address when you’re connected to a VPN, as opposed to the VPN server’s, then third parties can still use it to identify you. If you see a public IP in the test results, then you may have a privacy leak.
Local IPs are not specific to you. These IPs are assigned to you by your router and are reused millions of times by routers all over the world. So if a third party knows your local IP address, it has no way of linking it directly to you. If you see a local IP in the test results, it is not a threat to your privacy.
5 steps to test for a WebRTC leak (with and without VPN)
If you’re not using a VPN you will undoubtedly be exposing some private information to third parties. (Want to learn more? See how a VPN hides your IP address to keep your information private .)
If you are using a VPN and the leak tool indicates there may be a leak, then you can perform the following leak test to be sure:
Disconnect from your VPN and open this page in a new tab or window
Make a note of any public IP addresses you see
Close the page
Connect to your VPN and reopen the page
If you still see any of the public IP addresses from Step 2, then you have a privacy leak
If you’re using a VPN and the tool specifically tells you there is no leak, you’re safe!
Want to check for other privacy leaks? Try these tools:
What is WebRTC?
Web Real-Time Communication (WebRTC) is a collection of standardized technologies that allows web browsers to communicate with each other directly without the need for an intermediate server. Benefits of WebRTC include: faster speeds and less lag for web apps like video chat, file transfer, and live streaming.
Any two devices talking to each other directly via WebRTC, however, need to know each other’s real IP addresses. In theory this could allow a third-party website to exploit the WebRTC in your browser to detect your real IP address and use it to identify you. This is what we call a WebRTC leak.
Any leak of your public IP address is a threat to your privacy , but WebRTC leaks are lesser-known and easily overlooked, and not all VPN providers protect you from them!
How does a WebRTC leak put my privacy at risk?
The problem with WebRTC is that it uses techniques to discover your IP addresses that are more advanced than those used in “standard” IP detection.
How does WebRTC detect my IPs?
WebRTC discovers IPs via the Interactive Connectivity Establishment (ICE) protocol. This protocol specifies several techniques for discovering IPs, two of which are covered below.
STUN/TURN servers
STUN/TURN servers play two key roles in WebRTC: They allow web browsers to ask the question “What are my public IPs?” and they also facilitate two devices talking to each other even if they are behind NAT firewalls. The former is the one that can affect your privacy. STUN/TURN servers discover your IPs much as a website sees your IPs when you visit it.
Host candidate discovery
Most devices have multiple IP addresses associated with their hardware. Usually these are hidden from websites and STUN/TURN servers via firewalls. However, the ICE protocol specifies that browsers can gather these IPs simply by reading them off your device.
The IPs most commonly associated with your device are local IPv4 addresses, and discovery of them won’t affect your privacy. If you have IPv6 addresses, however, then your privacy could be at risk.
IPv6 addresses don’t work quite the same as IPv4 addresses. Generally, an IPv6 address is a public one (which means it is unique to you). If you have an IPv6 address associated with your device, and it is discovered via ICE, then your privacy could be exposed.
A malicious website could use STUN/TURN servers or host candidate discovery to trick your browser into revealing an IP address that could identify you, all without your knowledge.
WebRTC leaks: Which browsers are most vulnerable?
As of this writing, users of Firefox, Chrome, Opera, and Microsoft Edge are most vulnerable to WebRTC leaks because these browsers have WebRTC enabled by default.
Microsoft Edge
Mozilla firefox, google chrome.
Browsers that are most vulnerable to WebRTC leaks
Note that you may be safe from WebRTC leaks in one browser and not in another. If you regularly use multiple browsers, then you should consider using the ExpressVPN WebRTC Leak Test on each of them.
What does ExpressVPN do to protect me from WebRTC leaks?
ExpressVPN works hard to ensure its apps protect you from WebRTC leaks. When you open new web pages while connected to ExpressVPN, your public IP addresses won’t leak.
Some browsers, however, can be aggressive when it comes to holding onto data from old tabs. If you have a tab open from before you connected to the VPN, your real IP address may be cached in memory by the browser. These IPs can persist even if you refresh the tab, which puts your privacy at risk.
The ExpressVPN browser extension (currently available for Chrome , Firefox , and Edge ) solves this problem by letting you completely disable WebRTC from the settings menu, which will ensure that you’re not vulnerable to any caching issues.
How ExpressVPN’s dedicated leak-proofing engineers keep you safe
ExpressVPN protects you from a wide spectrum of WebRTC leaks across different browsers and platforms. Because WebRTC is still a relatively new technology, it’s important to continually test different scenarios for WebRTC leaks across different platforms and browsers. ExpressVPN leads the industry with a team of dedicated engineers who constantly investigate new leak vectors and rapidly develop any necessary fixes.
Learn more about ExpressVPN’s latest leak-proofing developments.
How else can I prevent WebRTC leaks?
In addition to using ExpressVPN, you may be able to guard against leaks by manually disabling WebRTC in your browser.*
How to disable WebRTC in Firefox on desktop
- Type about:config into the address bar
- Click the “I accept the risk!” button that appears
- Type media.peerconnection.enabled in the search bar
- Double-click to change the Value to “false”
This should work on both mobile and desktop versions of Firefox.
How to disable WebRTC in Chrome on desktop
There are two Chrome extensions known to successfully block WebRTC leaks:
- uBlock Origin
- WebRTC Network Limiter
uBlock Origin is a general all-purpose blocker that blocks ads, trackers, malware, and has an option to block WebRTC. WebRTC Network Limiter is an official Google add-on that specifically stops IP leaks without totally blocking WebRTC.
How to disable WebRTC in Safari on desktop
There’s no need to disable WebRTC in Safari. Safari’s permissions model is stricter than those of most browsers. By default, no IP addresses are made available to websites except the one you use to access the site. Therefore you shouldn’t need to take any additional action to prevent WebRTC leaks in Safari. Note, however, that if you grant any particular site permission to use audio or video capture, you might expose your IPs.
How to disable WebRTC in Opera on desktop
- Open Settings in Opera. To do this:
- On Windows or Linux, click the Opera logo at the top-left corner of the browser window
- On Mac, click Opera in the toolbar and locate settings under Preferences
- Expand the Advanced section on the left-hand side and click Privacy & security
- Scroll down to WebRTC and select the Disable non-proxied UDP radio button
- Close the tab and the settings should automatically save
How to disable WebRTC in Microsoft Edge
Unfortunately, there’s currently no way to completely disable WebRTC in Microsoft Edge. However, you can set your browser to hide your local IP address if you:
- Type about:flags into the address bar
- Check the option marked Hide my local IP address over WebRTC connections
As mentioned above, revealing your local IP address is not a threat to your privacy, so the steps above offer little benefit. Therefore the best way to stop WebRTC leaks while using Microsoft Edge is by using the ExpressVPN app for Windows .
*Disabling WebRTC probably won’t affect normal web browsing. Most websites don’t depend on it… yet. But as WebRTC becomes more popular, the functionality of certain sites may decline if you disable it completely.
What if I’m connected to ExpressVPN, and I still see a WebRTC leak on this page?
Contact ExpressVPN Support , and we’ll get that sorted out promptly.
Refer a friend and you both get 30 days free!
Give your friends the gift of internet freedom. With every successful referral, you BOTH get 30 days free.

Choose language
Techvanila is supported by its audience. When you purchase through links on our site, we may earn an affiliate commission. Learn more .
WebRTC Leaks: Everything You Need to Know
WebRTC is a technology that allows web browsers and mobile applications to communicate with each other in real-time. While it’s a useful tool for video conferencing and other collaborative applications, it can also pose a security risk. WebRTC leaks occur when a user’s real IP address is exposed, potentially allowing others to track their online activities.
In this complete guide to WebRTC leaks, readers will learn everything there is to know about this vulnerability. The guide will cover what WebRTC is, why leaks happen, and how they can be prevented. It will also provide step-by-step instructions for performing a WebRTC leak test and disabling WebRTC in popular web browsers. With this information, readers can take steps to protect their online privacy and security.
Understanding WebRTC
WebRTC stands for Web Real-Time Communications. It is a collection of technologies and protocols that allow real-time communication between web browsers without the need for any additional software or plugins. WebRTC is supported by all major web browsers, including Google Chrome, Mozilla Firefox, Microsoft Edge, and Apple Safari.
WebRTC is commonly used for video and audio communication, such as video conferencing, voice calling, and live streaming. It uses peer-to-peer communication, which means that data is transmitted directly between the browsers without passing through a central server. This makes WebRTC faster and more efficient than traditional communication methods.
However, WebRTC can also pose a security risk. Since WebRTC uses peer-to-peer communication, it can reveal the IP address of the user to the other party. This is known as a WebRTC leak, and it can compromise the user’s privacy and anonymity.
To prevent WebRTC leaks, it is recommended to use a VPN (Virtual Private Network) service. A VPN encrypts the user’s internet traffic and hides their IP address, preventing WebRTC leaks and other forms of online tracking. It is also recommended to disable WebRTC in the web browser settings to ensure maximum privacy and security.
WebRTC (Web Real-Time Communication) is a technology that enables web browsers to communicate directly with each other, without the need for a central server. This technology is used for video conferencing, file sharing, and other real-time communication applications.
However, WebRTC can also be used to leak your real IP address, even if you are using a VPN or a proxy server. This is called a WebRTC leak.
A WebRTC leak occurs when your browser leaks your real IP address through WebRTC APIs. This can happen even if you are using a VPN or a proxy server, because WebRTC bypasses these technologies and communicates directly with the other browser.
WebRTC leaks are a serious privacy issue, because they can reveal your real location and identity to websites and other online services. This can be used to track your online activities, target you with ads, or even steal your personal information.
To prevent WebRTC leaks, you can disable WebRTC in your browser, use a browser extension that blocks WebRTC, or use a VPN that has built-in protection against WebRTC leaks.
Read More: Best VPNs for 2023
How WebRTC Leaks Occur
WebRTC leaks happen when a user’s IP address is revealed despite using a VPN. This vulnerability is caused by WebRTC, a technology that enables real-time communication between browsers without the need for plugins or additional software.
Browser Vulnerabilities
WebRTC leaks can occur due to vulnerabilities in the user’s browser. Some browsers may automatically enable WebRTC, allowing websites to access a user’s IP address without their knowledge. This can happen even if the user is using a VPN.
Network Security Flaws
WebRTC leaks can also occur due to network security flaws. This can happen when a user connects to a public Wi-Fi network, which can be easily accessed by hackers. In some cases, hackers can use a technique called “man-in-the-middle” to intercept and read a user’s traffic, including their IP address.
To prevent WebRTC leaks, users can disable WebRTC in their browser settings or use a VPN that has built-in protection against WebRTC leaks. It is also important to use a secure network when accessing the internet, especially when using public Wi-Fi.
Impact of WebRTC Leaks
WebRTC leaks can have serious consequences for internet users. When a WebRTC leak occurs, it can reveal the user’s real IP address, even when they are using a VPN or proxy server. This can allow third parties, such as advertisers or hackers, to track the user’s online activity and potentially compromise their privacy and security.
One of the most significant impacts of WebRTC leaks is on users who rely on VPNs to protect their online privacy. VPNs are supposed to hide the user’s IP address and encrypt their internet traffic, but if a WebRTC leak occurs, the user’s real IP address is exposed, and their online activity can be tracked and monitored.
WebRTC leaks can also impact users who are behind a NAT (Network Address Translation) firewall. NAT is commonly used by home and office networks to allow multiple devices to share a single public IP address. However, if a WebRTC leak occurs, it can reveal the user’s real local IP address, which can be used to identify the specific device on the network.
In addition to privacy concerns, WebRTC leaks can also pose security risks. If a hacker is able to obtain a user’s real IP address, they can potentially launch a targeted attack against the user’s device or network. WebRTC leaks can also be used to bypass security measures such as firewalls or content filters.
Overall, WebRTC leaks can have significant impacts on users’ privacy and security. It is important for internet users to be aware of the risks of WebRTC leaks and take steps to protect themselves, such as using a WebRTC leak test tool to check for vulnerabilities and ensuring that their VPN or proxy server is configured correctly to prevent leaks.
WebRTC leaks are a potential threat to online privacy. Fortunately, there are ways to prevent them. This section will cover two primary methods to prevent WebRTC leaks: the use of VPNs and browser configurations.
Use of VPNs
One of the most effective ways to prevent WebRTC leaks is to use a VPN. A VPN encrypts your internet connection and masks your IP address, making it difficult for websites to track your online activity. When choosing a VPN, it is important to select a provider that has a no-logging policy and is committed to protecting your privacy.
To test for WebRTC leaks, you can use online tools such as Kaspersky WebRTC Leak Test. If you detect a leak, you can try changing your VPN provider or configuring your browser settings.
Browser Configurations
Another way to prevent WebRTC leaks is to configure your browser settings. This can be done by disabling WebRTC or using a browser extension that blocks WebRTC requests. However, disabling WebRTC can also affect the performance of some websites and applications that rely on it.
To disable WebRTC in Google Chrome, you can go to the Settings menu, click Advanced, and then click Privacy and Security. From there, you can toggle off the option for “Use a web service to help resolve navigation errors” and “Use a prediction service to load pages more quickly.” In Mozilla Firefox, you can type “about” in the address bar, search for “media.peerconnection.enabled,” and set it to “false.”
Online Testing Tools
There are several online testing tools available to detect WebRTC leaks. These tools are easy to use and require no technical knowledge. Users can simply visit the website and run the test to see if there are any WebRTC leaks.
One of the most popular online testing tools is the Kaspersky WebRTC Leak Test. This tool is designed to check if your browser is leaking your real IP address through WebRTC. It works by sending a request to a STUN server, which returns the IP address of the user. If the IP address returned by the server is not the same as the user’s real IP address, then there is no leak.
Another great online testing tool is the BrowserLeaks WebRTC Leak Test. This tool also checks for WebRTC leaks by communicating with a STUN server. It can detect leaks even if the user is behind a NAT or using a VPN or proxy server.
Manual Detection Methods
In addition to online testing tools, there are also manual methods to detect WebRTC leaks. These methods require some technical knowledge and may not be suitable for all users.
One manual method is to use the browser’s developer tools to inspect the WebRTC connections. Users can open the developer tools and navigate to the Network tab to see the WebRTC connections. If there are any connections that reveal the user’s real IP address, then there is a leak.
Another manual method is to use a packet sniffer to capture the network traffic. Users can capture the traffic and analyze it to see if there are any WebRTC packets that reveal the user’s real IP address. This method requires more technical knowledge and may not be suitable for all users.
Overall, using online testing tools or manual detection methods can help users detect WebRTC leaks and protect their privacy online.
Case Studies of WebRTC Leaks
WebRTC leaks are a serious threat to online privacy. They can reveal your real IP address and location to websites and other online entities. In this section, we will look at a few case studies of WebRTC leaks and how they can be prevented.
Case Study 1: ExpressVPN Leak Testing Tools
ExpressVPN has developed a set of leak testing tools that can help users detect WebRTC leaks. These tools are easy to use and can quickly identify any vulnerabilities in your browser or VPN connection.
Case Study 2: Kaspersky WebRTC Leak Test on Windows
Kaspersky has also developed a WebRTC leak test that can be used on Windows devices. This test is designed to check for any leaks in your browser or VPN connection and can help you identify and fix any vulnerabilities.
Case Study 3: VPN Protection from WebRTC Vulnerabilities
While some VPNs offer protection from WebRTC vulnerabilities, it is important to note that not all VPNs are created equal. Some VPNs may not offer adequate protection or may even be vulnerable to WebRTC leaks themselves.
In conclusion, WebRTC leaks are a serious threat to online privacy and can reveal your real IP address and location to websites and other online entities. It is important to take steps to protect yourself from these vulnerabilities, such as using leak testing tools and choosing a VPN that offers adequate protection.
WebRTC leaks can pose a serious threat to online privacy, even when using a VPN. It is important to understand what WebRTC is and how it can potentially leak sensitive information.
There are a variety of ways to prevent WebRTC leaks, including disabling WebRTC in your browser settings, using a browser extension or add-on to block WebRTC, or using a VPN with built-in WebRTC leak protection.
It is also important to regularly test for WebRTC leaks to ensure that your online activity is not being exposed. There are a number of free online tools available for testing WebRTC leaks.
Overall, staying informed and taking proactive measures to protect against WebRTC leaks can greatly enhance online privacy and security.
Frequently Asked Questions
How do i check for webrtc leaks.
To check for WebRTC leaks, there are several online tools available. One of the most commonly used tools is the Kaspersky WebRTC Leak Test. It is a simple tool that can be used to test if your browser is leaking your IP address. Other tools include the ExpressVPN WebRTC Leak Test and the BrowserLeaks WebRTC Test.
Can WebRTC bypass VPN?
No, WebRTC cannot bypass VPN. However, WebRTC can leak your real IP address even if you are using a VPN. This is because WebRTC is a browser-based technology that can reveal your real IP address to websites even if you are connected to a VPN.
Does WebRTC still leak IP?
Yes, WebRTC can still leak your IP address. Although many browsers have implemented measures to prevent WebRTC leaks, some browsers may still be vulnerable to WebRTC leaks. It is important to regularly test for WebRTC leaks to ensure that your IP address is not being revealed.
How do I stop my WebRTC from leaking?
To stop your WebRTC from leaking, you can disable WebRTC in your browser or use a browser extension that blocks WebRTC. Another option is to use a VPN that has built-in protection against WebRTC leaks. It is important to note that disabling WebRTC may affect the functionality of some web applications that rely on WebRTC.
What is WebRTC IP handling?
WebRTC IP handling refers to the way that WebRTC handles IP addresses. When WebRTC is enabled, it can reveal your real IP address to websites even if you are using a VPN. This is because WebRTC uses STUN (Session Traversal Utilities for NAT) servers to obtain your IP address.
What is a DNS leak test?
A DNS leak test is a test that checks if your DNS requests are being leaked. DNS leaks can occur when your DNS requests are sent outside of the encrypted VPN tunnel, which can reveal your browsing activity to your ISP or other third parties. DNS leak tests can be performed using online tools such as DNS Leak Test and IPLeak.net.
Muhammad Yasir is a tech enthusiast with a knack for exploring how technology influences modern relationships. They have written extensively on the topic, offering unique insights into the intersection of love and technology.
Privacy Policy
Terms & Conditions
How to Disable WebRTC in Chrome, Firefox, Safari, and Others
This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page. However, it has a sneak peek, easy guide steps, and/or a quick list providing quick in-page navigations and easily-found answers if desired.
This article provides steps on how to disable WebRTC from your browser. Learn all about this feature and why you may want to turn it off.
WebRTC constitutes a critical communication component for most web browsers, empowering users with audio/video communication functionalities. However, despite all its usefulness, it can threaten your online privacy by leaking your IP address, which can be big trouble for VPN users. Therefore, you should know how to disable WebRTC whenever you wish to go anonymous online. This guide elaborates on how to disable WebRTC on Firefox , Chrome , Safari , and other popular browsers.
Websites can take advantage of WebRTC technology to make a direct connection between your browser and its servers. These connections can potentially leak your IP address , thus rendering your VPN useless. Consequently, third parties such as hackers and advertisers can access your location, ISP, and device if they get your IP address.
WebRTC is intended to work on all browsers, so it doesn’t matter what you use. Fortunately, it is effortless to disable it.
Wondering how to do that? Don’t worry. This article explains the different ways to deactivate WebRTC to stay private online. You’ll also discover how a trustworthy VPN such as NordVPN will keep you safe.
Quick guide on how to disable WebRTC on popular browsers
- Open the Chrome Web Store.
- Search for ‘ WebRTC Control .’
- Click ‘ Add to Chrome ’ and then ‘ Add Extension ’ to install the add-on.
- Right-click on the add-on icon to change its options.
- 6,100+ VPN servers in more than 60 countries
- Fastest among the VPNs we tested
- Unblocks virtually all the streaming platforms
- Unlimited bandwidth and torrent downloads

WebRTC Leak Test
How to disable webrtc, webrtc in firefox.
To disable WebRTC in Firefox:
- Type about:config in the address bar and press Enter.
- In the search bar, type media.peerconnection.enabled and double-click the preference to set its value to false .
WebRTC in Chrome
The recommended solution to limit the risk of IP leakage via WebRTC is to use the official Google extension called WebRTC Network Limiter , which provides a range of options with varying levels of protection.
Further Reading
- RTC Peer Connection – MDN
- Media Devices API – MDN
- Media Stream Track API – MDN
- An Intro to WebRTC's NAT/Firewall Problem – webrtcHacks
- Anatomy of a WebRTC SDP – webrtcHacks
Leave a Comment (178)
- Skip to primary navigation
- Skip to main content
- Skip to primary sidebar
- Skip to footer
webrtcHacks
[10 years of] guides and information for WebRTC developers
Guide apple , code , getUserMedia , ios , Safari Chad Phillips · September 7, 2018
Guide to WebRTC with Safari in the Wild (Chad Phillips)
It has been more than a year since Apple first added WebRTC support to Safari. My original post reviewing the implementation continues to be popular here, but it does not reflect some of the updates since the first limited release. More importantly, given its differences and limitations, many questions still remained on how to best develop WebRTC applications for Safari.
I ran into Chad Phillips at Cluecon (again) this year and we ended up talking about his arduous experience making WebRTC work on Safari. He had a great, recent list of tips and tricks so I asked him to share it here.
Chad is a long-time open source guy and contributor to the FreeSWITCH product. He has been involved with WebRTC development since 2015. He recently launched MoxieMeet , a videoconferencing platform for online experiential events, where he is CTO and developed a lot of the insights for this post.
{“editor”, “ chad hart “}

In June of 2017, Apple became the last major vendor to release support for WebRTC, paving the (still bumpy) road for platform interoperability.
And yet, more than a year later, I continue to be surprised by the lack of guidance available for developers to integrate their WebRTC apps with Safari/iOS. Outside of a couple posts by the Webkit team, some scattered StackOverflow questions, the knowledge to be gleaned from scouring the Webkit bug reports for WebRTC, and a few posts on this very website , I really haven’t seen much support available. This post is an attempt to begin rectifying the gap.
I have spent many months of hard work integrating WebRTC in Safari for a very complex videoconferencing application. Most of my time was spent getting iOS working, although some of the below pointers also apply to Safari on MacOS.
This post assumes you have some level of experience with implementing WebRTC — it’s not meant to be a beginner’s how to, but a guide for experienced developers to smooth the process of integrating their apps with Safari/iOS. Where appropriate I’ll point to related issues filed in the Webkit bug tracker so that you may add your voice to those discussions, as well as some other informative posts.
I did an awful lot of bushwacking in order to claim iOS support in my app, hopefully the knowledge below will make a smoother journey for you!
Some good news first
First, the good news:
- Apple’s current implementation is fairly solid
- For something simple like a 1-1 audio/video call, the integration is quite easy
Let’s have a look at some requirements and trouble areas.
General Guidelines and Annoyances
Use the current webrtc spec.
If you’re building your application from scratch, I recommend using the current WebRTC API spec (it’s undergone several iterations). The following resources are great in this regard:
- https://developer.mozilla.org/en-US/docs/Web/API/WebRTC_API
- https://github.com/webrtc/samples
For those of you running apps with older WebRTC implementations, I’d recommend you upgrade to the latest spec if you can, as the next release of iOS disables the legacy APIs by default. In particular, it’s best to avoid the legacy addStream APIs, which make it more difficult to manipulate tracks in a stream.
More background on this here: https://blog.mozilla.org/webrtc/the-evolution-of-webrtc/
iPhone and iPad have unique rules – test both
Since the iPhone and iPad have different rules and limitations, particularly around video, I’d strongly recommend that you test your app on both devices. It’s probably smarter to start by getting it working fully on the iPhone, which seems to have more limitations than the iPad.
More background on this here: https://webkit.org/blog/6784/new-video-policies-for-ios
Let the iOS madness begin
It’s possible that may be all you need to get your app working on iOS. If not, now comes the bad news: the iOS implementation has some rather maddening bugs/restrictions, especially in more complex scenarios like multiparty conference calls.
Other browsers on iOS missing WebRTC integration
The WebRTC APIs have not yet been exposed to iOS browsers using WKWebView . In practice, this means that your web-based WebRTC application will only work in Safari on iOS, and not in any other browser the user may have installed (Chrome, for example), nor in an ‘in-app’ version of Safari.
To avoid user confusion, you’ll probably want to include some helpful user error message if they try to open your app in another browser/environment besides Safari proper.
Related issues:
- https://bugs.webkit.org/show_bug.cgi?id=183201
- https://bugs.chromium.org/p/chromium/issues/detail?id=752458
No beforeunload event, use pagehide
According to this Safari event documentation , the unload event has been deprecated, and the beforeunload event has been completely removed in Safari. So if you’re using these events, for example, to handle call cleanup, you’ll want to refactor your code to use the pagehide event on Safari instead.
source: https://gist.github.com/thehunmonkgroup/6bee8941a49b86be31a787fe8f4b8cfe
Getting & playing media, playsinline attribute.
Step one is to add the required playsinline attribute to your video tags, which allows the video to start playing on iOS. So this:
Becomes this:
playsinline was originally only a requirement for Safari on iOS, but now you might need to use it in some cases in Chrome too – see Dag-Inge’s post for more on that..
See the thread here for details on this issue requirement: https://github.com/webrtc/samples/issues/929
Autoplay rules
Next you’ll need to be aware of the Webkit WebRTC rules on autoplaying audio/video. The main rules are:
- MediaStream-backed media will autoplay if the web page is already capturing.
- MediaStream-backed media will autoplay if the web page is already playing audio
- A user gesture is required to initiate any audio playback – WebRTC or otherwise.
This is good news for the common use case of a video call, since you’ve most likely already gotten permission from the user to use their microphone/camera, which satisfies the first rule. Note that these rules work alongside the base autoplay rules for MacOS and iOS, so it’s good to be aware of them as well.
Related webkit posts:
- https://webkit.org/blog/7763/a-closer-look-into-webrtc
- https://webkit.org/blog/7734/auto-play-policy-changes-for-macos
- https://webkit.org/blog/6784/new-video-policies-for-ios
No low/limited video resolutions
UPDATE 2019-08-18:
Unfortunately this bug has only gotten worse in iOS 12, as their attempt to fix it broke the sending of video to peer connections for non-standard resolutions. On the positive side the issue does seem to be fully fixed in the latest iOS 13 Beta: https://bugs.webkit.org/show_bug.cgi?id=195868
Visiting https://jsfiddle.net/thehunmonkgroup/kmgebrfz/15/ (or the webrtcHack’s WebRTC-Camera-Resolution project) in a WebRTC-compatible browser will give you a quick analysis of common resolutions that are supported by the tested device/browser combination. You’ll notice that in Safari on both MacOS and iOS, there aren’t any available low video resolutions such as the industry standard QQVGA, or 160×120 pixels. These small resolutions are pretty useful for serving thumbnail-sized videos — think of the filmstrip of users in a Google Hangouts call, for example.
Now you could just send whatever the lowest available native resolution is along the peer connection and let the receiver’s browser downscale the video, but you’ll run the risk of saturating the download bandwidth for users that have less speedy internet in mesh/SFU scenarios.
I’ve worked around this issue by restricting the bitrate of the sent video, which is a fairly quick and dirty compromise. Another solution that would take a bit more work is to handle downscaling the video stream in your app before passing it to the peer connection, although that will result in the client’s device spending some CPU cycles.
Example code:
- https://webrtc.github.io/samples/src/content/peerconnection/bandwidth/
New getUserMedia() request kills existing stream track

If your application grabs media streams from multiple getUserMedia ( ) requests, you are likely in for problems with iOS. From my testing, the issue can be summarized as follows: if getUserMedia ( ) requests a media type requested in a previous getUserMedia ( ) , the previously requested media track’s muted property is set to true, and there is no way to programmatically unmute it. Data will still be sent along a peer connection, but it’s not of much use to the other party with the track muted! This limitation is currently expected behavior on iOS.
I was able to successfully work around it by:
- Grabbing a global audio/video stream early on in my application’s lifecycle
- Using MediaStream . clone ( ) , MediaStream . addTrack ( ) , MediaStream . removeTrack ( ) to create/manipulate additional streams from the global stream without calling getUserMedia ( ) again.
source: https://gist.github.com/thehunmonkgroup/2c3be48a751f6b306f473d14eaa796a0
See this post for more: https://developer.mozilla.org/en-US/docs/Web/API/MediaStream and
this related issue: https://bugs.webkit.org/show_bug.cgi?id=179363
Managing Media Devices
Media device ids change on page reload.
This has been improved as of iOS 12.2, where device IDs are now stable across browsing sessions after getUserMedia ( ) has been called once. However, device IDs are still not preserved across browser sessions, so this improvement isn’t really helpful for storing a user’s device preferences longer term. For more info, see https://webkit.org/blog/8672/on-the-road-to-webrtc-1-0-including-vp8/
Many applications include support for user selection of audio/video devices. This eventually boils down to passing the deviceId to getUserMedia ( ) as a constraint.
Unfortunately for you as a developer, as part of Webkit’s security protocols, random deviceId ’s are generated for all devices on each new page load. This means, unlike every other platform, you can’t simply stuff the user’s selected deviceId into persistent storage for future reuse.
The cleanest workaround I’ve found for this issue is:
- Store both device . deviceId and device . label for the device the user selects
- Try using the saved deviceId
- If that fails, enumerate the devices again, and try looking up the deviceId from the saved device label.
On a related note: Webkit further prevents fingerprinting by only exposing a user’s actual available devices after the user has granted device access. In practice, this means you need to make a getUserMedia ( ) call before you call enumerateDevices ( ) .
source: https://gist.github.com/thehunmonkgroup/197983bc111677c496bbcc502daeec56
Related issue: https://bugs.webkit.org/show_bug.cgi?id=179220
Related post: https://webkit.org/blog/7763/a-closer-look-into-webrtc
Speaker selection not supported
Webkit does not yet support HTMLMediaElement . setSinkId ( ) , which is the API method used for assigning audio output to a specific device. If your application includes support for this, you’ll need to make sure it can handle cases where the underlying API support is missing.
source: https://gist.github.com/thehunmonkgroup/1e687259167e3a48a55cd0f3260deb70
Related issue: https://bugs.webkit.org/show_bug.cgi?id=179415
PeerConnections & Calling
Beware, no vp8 support.
Support for VP8 has now been added as of iOS 12.2. See https://webkit.org/blog/8672/on-the-road-to-webrtc-1-0-including-vp8/
While the W3C spec clearly states that support for the VP8 video codec (along with the H.264 codec) is to be implemented, Apple has thus far chosen to not support it. Sadly, this is anything but a technical issue, as libwebrtc includes VP8 support, and Webkit actively disables it.
So at this time, my advice to achieve the best interoperability in various scenarios is:
- Multiparty MCU – make sure that H.264 is a supported codec
- Multiparty SFU – use H.264
- Multiparty Mesh and peer to peer – pray everyone can negotiate a common codec
I say best interop because while this gets you a long way, it won’t be all the way. For example, Chrome for Android does not support software H.264 encoding yet. In my testing, many (but not all) Android phones have hardware H.264 encoding, but those that are missing hardware encoding will not work in Chrome for Android.
Associated bug reports:
- https://bugs.webkit.org/show_bug.cgi?id=167257
- https://bugs.webkit.org/show_bug.cgi?id=173141
- https://bugs.chromium.org/p/chromium/issues/detail?id=719023
Send/receive only streams
As previously mentioned, iOS doesn’t support the legacy WebRTC APIs. However, not all browser implementations fully support the current specification either.
As of this writing, a good example is creating a send only audio/video peer connection. iOS doesn’t support the legacy RTCPeerConnection . createOffer ( ) options of offerToReceiveAudio / offerToReceiveVideo , and the current stable Chrome doesn’t support the RTCRtpTransceiver spec by default.
Other more esoteric bugs and limitations
There are certainly other corner cases you can hit that seem a bit out of scope for this post. However, an excellent resource should you run aground is the Webkit issue queue, which you can filter just for WebRTC-related issues: https://bugs.webkit.org/buglist.cgi?component=WebRTC&list_id=4034671&product=WebKit&resolution=—
Remember, Webkit/Apple’s implementation is young
It’s still missing some features (like the speaker selection mentioned above), and in my testing isn’t as stable as the more mature implementation in Google Chrome.
There have also been some major bugs — capturing audio was completely broken for the majority of the iOS 12 Beta release cycle (thankfully they finally fixed that in Beta 8).
Apple’s long-term commitment to WebRTC as a platform isn’t clear, particularly because they haven’t released much information about it beyond basic support. As an example, the previously mentioned lack of VP8 support is troubling with respect to their intention to honor the agreed upon W3C specifications.
These are things worth thinking about when considering a browser-native implementation versus a native app. For now, I’m cautiously optimistic, and hopeful that their support of WebRTC will continue, and extend into other non-Safari browsers on iOS.
{“author”: “ Chad Phillips “}
Related Posts

Reader Interactions
September 7, 2018 at 9:42 am
One of the most detailed posts I’ve seen on the subject; thank you Chad, for sharing.
September 11, 2018 at 7:04 am
Please also note that Safari does not support data channels.
September 11, 2018 at 12:40 pm
@JSmitty, all of the ‘RTCDataChannel’ examples at https://webrtc.github.io/samples/ do work in Safari on MacOS, but do not currently work in Safari on iOS 11/12. I’ve filed https://bugs.webkit.org/show_bug.cgi?id=189503 and https://github.com/webrtc/samples/issues/1123 — would like to get some feedback on those before I incorporate this info into the post. Thanks for the heads up!
September 26, 2018 at 2:44 pm
OK, so I’ve confirmed data channels DO work in Safari on iOS, but there’s a caveat: iOS does not include local ICE candidates by default, and many of the data channel examples I’ve seen depend on that, as they’re merely sending data between two peer connections on the same device.
See https://bugs.webkit.org/show_bug.cgi?id=189503#c2 for how to temporarily enable local ICE on iOS.
January 22, 2020 at 4:21 pm
Great article. Thanks Chad & Chad for sharing your expertise.
As to DataChannel support. Looks like Safari officially still doesn’t support it according to the support matrix. https://developer.mozilla.org/en-US/docs/Web/API/RTCDataChannel
My own testing shows that DataChannel works between two Safari browser windows. However at this time (Jan 2020) it does not work between Chrome and Safari windows. Also fails between Safari and aiortc (Python WebRTC provider). DataChannel works fine between Chrome and aiortc.
A quick way to test this problem is via sharedrop.io Transferring files works fine between same brand browser windows, but not across brands.
Hope Apple is working on the compatibility issues with Chrome.
September 13, 2018 at 2:37 pm
Nice summary Chad. Thanks for this! –
September 18, 2018 at 4:29 pm
Very good post, Chad. Just what I was looking for. Thanks for sharing this knowledge. 🙂
October 4, 2018 at 10:11 am
Thanks for this Chad, currently struggling with this myself, where a portable ‘web’ app is being written.. I’m hopeful it will creep into wkwebview soon!
October 5, 2018 at 2:43 am
Thanks for detailing the issues.
One suggestion for any future article would be including the iOS Safari limitation on simultaneous playing of multiple elements with audio present.
This means refactoring so that multiple (remote) audio sources are rendered by a single element.
October 5, 2018 at 9:46 am
There’s a good bit of detail/discussion about this limitation here: https://bugs.webkit.org/show_bug.cgi?id=176282
Media servers that mix the audio are a good solution.
December 18, 2018 at 1:10 pm
The same issue I’m facing New getUserMedia() request kills existing stream track. Let’s see whether it helps me or not.
December 19, 2018 at 6:23 am
iOS calling getUserMedia() again kills video display of first getUserMedia(). This is the issue I’m facing but I want to pass the stream from one peer to another peer.
April 26, 2019 at 12:07 am
Thank you Chad for sharing this, I was struggling with the resolution issue on iOS and I was not sure why I was not getting the full hd streaming. Hope this will get supported soon.
May 21, 2019 at 12:54 am
VP8 is a nightmare. I work on a platform where we publish user-generated content, including video, and the lack of support for VP8 forces us to do expensive transcoding on these videos. I wonder why won’t vendors just settle on a universal codec for mobile video.
August 18, 2019 at 2:17 pm
VP8 is supported as of iOS 12.2: https://webkit.org/blog/8672/on-the-road-to-webrtc-1-0-including-vp8/
July 3, 2019 at 3:38 am
Great Post! Chad I am facing an issue with iOS Safari, The issue is listed below. I am using KMS lib for room server handling and calling, There wasn’t any support for Safari / iOS safari in it, I added adapter.js (shim) to make my application run on Safari and iOS (Safari). After adding it worked perfectly on Safari and iOS, but when more than 2 persons join the call, The last added remote stream works fine but the existing remote stream(s) get struck/disconnected which means only peer to peer call works fine but not multiple remote streams. Can you please guide how to handle multiple remote streams in iOS (Safari). Thanks
July 3, 2019 at 1:45 pm
Your best bet is probably to search the webkit bugtracker, and/or post a bug there.
August 7, 2019 at 6:40 pm
No low/limited video resolutions: 1920×1080 not supported -> are you talking about IOS12 ? Because I’m doing 4K on IOS 12.3.1 with janus echo test with iphone XS Max (only one with 4K front cam) Of course if I run your script on my MBP it will say fullHD not supported -> because the cam is only 720p.
August 18, 2019 at 2:20 pm
That may be a standard camera resolution on that particular iPhone. The larger issue has been that only resolutions natively supported by the camera have been available, leading to difficultly in reliably selecting resolutions in apps, especially lower resolutions like those used in thumbnails.
Thankfully, this appears to be fully addressed in the latest beta of iOS 13.
April 18, 2020 at 7:01 am
How many days of work I lost before find this article. It’s amazing and explain a lot the reasons of all the strange bugs in iOS. Thank you so much.
September 21, 2020 at 11:38 am
Hi, i’m having issues with Safari on iOS. In the video tag, adding autoplay and playsinline doesn’t work on our Webrtc implementation. Obviously it works fine in any browser on any other platform.
I need to add the controls tag, then manually go to full screen and press play.
Is there a way to play the video inside the web page ?
December 9, 2020 at 2:35 am
First of all, thanks for detailing the issues.
This article is unique to provide many insides for WebRTC/Safari related issues. I learned a lot and applied some the techniques in our production application.
But I had very unique case which I am struggling with right now, as you might guess with Safari. I would be very grateful if you can help me or at least to guide to the right direction.
We have webrtc-based one-2-one video chat, one side always mobile app (host) who is the initiator and the other side is always browser both desktop and mobile. Making the app working across different networks was pain in the neck up to recently, but managed to fix this by changing some configurations. So the issue was in different networks WebRTC was not generating relay and most of the time server reflexive candidates, as you know without at least stun provided candidates parties cannot establish any connection. Solution was simple as though it look a lot of search on google, ( https://github.com/pion/webrtc/issues/810 ), we found out that mobile data providers mostly assigning IPv6 to mobile users. And when they used mobile data plan instead of local wifi, they could not connect to each other. By the way, we are using cloud provider for STUN/TURN servers (Xirsys). And when we asked their technical support team they said their servers should handle IPv6 based requests, but in practice it did not work. So we updated RTCPeerConnection configurations, namely, added optional constraints (and this optional constraints are also not provided officially, found them from other non official sources), the change was just disabling IPv6 on both mobile app (iOS and Android) and browser. After this change, it just worked perfectly until we found out Safari was not working at all. So we reverted back for Safari and disabled IPv6 for other cases (chrome, firefox, Android browsers)
const iceServers = [ { urls: “stun:” }, { urls: [“turn:”,”turn:”,… ], credential: “secret”, username: “secret” } ];
let RTCConfig; // just dirty browser detection const ua = navigator.userAgent.toLocaleLowerCase(); const isSafari = ua.includes(“safari”) && !ua.includes(“chrome”);
if (isSafari) { RTCConfig = iceServers; } else { RTCConfig = { iceServers, constraints: { optional: [{ googIPv6: false }] } }; }
if I wrap iceServers array inside envelop object and optional constraints and use it in new RTCPeerConnection(RTCConfig); is is throwing error saying: Attempted to assign readonly property pointing into => safari_shim.js : 255
Can you please help with this issue, our main customers use iPhone, so making our app work in Safari across different networks are very critical to our business. If you provide some kind of paid consultation, it is also ok for us
Looking forward to hearing from you
July 13, 2022 at 2:42 pm
Thanks for the great summary regarding Safari/IOS. The work-around for low-bandwidth issue is very interesting. I played with the sample. It worked as expected. It’s played on the same device, isn’t it? When I tried to add a similar “a=AS:500\r\n” to the sdp and tested it on different devices – one being windows laptop with browser: Chrome, , another an ipad with browser: Safari – it seemed not working. The symptom was: the stream was not received or sent. In a word, the connections for media communications was not there. I checked the sdp, it’s like,
sdp”: { “type”: “offer”, “sdp”: ” v=0\r\n o=- 3369656808988177967 2 IN IP4 127.0.0.1\r\n s=-\r\n t=0 0\r\n a=group:BUNDLE 0 1 2\r\n a=extmap-allow-mixed\r\n a=msid-semantic: WMS 7BLOSVujr811EZHSiFZI2t8yMML8LpOgo0in\r\n m=audio 9 UDP/TLS/RTP/SAVPF 111 63 103 104 9 0 8 106 105 13 110 112 113 126\r\n c=IN IP4 0.0.0.0\r\n b=AS:500\r\n … }
Also I didn’t quite understand the statement in the article. “I’ve worked around this issue by restricting the bitrate of the sent video, which is a fairly quick and dirty compromise. Another solution that would take a bit more work is to handle downscaling the video stream in your app before passing it to the peer connection” – don’t the both scenarios work on the sent side?
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
This site uses Akismet to reduce spam. Learn how your comment data is processed .

How to Disable WebRTC in Safari for iPhone
Are you looking for a way to disable WebRTC in Safari on your iPhone? WebRTC (Web Real-Time Communication) is a free, open-source project that enables real-time communication between web browsers and devices. Unfortunately, it can also leak your IP address and other sensitive information if not properly configured. In this blog post we’ll show you how to disable WebRTC in Safari on your iPhone.
The first step is to make sure your device is running the latest version of iOS. Then open the «Settings» app and tap «Safari». Tap «Advanced» and enable the «Show Develop menu in menu bar» option. Now you’ll see a new menu item called «Develop» in the menu bar at the top of the screen.
Next, tap «Develop» and select «Experimental Features». Scroll down until you find the WebRTC section and toggle off all options related to WebRTC such as ICE Candidate Filtering and Media Source Extensions (MSE). This will effectively disable all WebRTC features in Safari on your iPhone.
That’s it! You have now successfully disabled WebRTC in Safari on your iPhone. Keep in mind that this is an experimental feature so it may not work with all websites or services, but it should be enough to protect most of your online activity from leaking sensitive information such as your IP address or other identifying information.
We hope this blog post has been helpful for disabling WebRTC in Safari on your iPhone. If you have any questions or concerns abot this feature, feel free to leave us a comment below!
Enabling WebRTC in Safari
To enable WebRTC in Safari, firt open the Preferences menu by clicking Safari in the top left corner and selecting Preferences from the dropdown menu. Then go to Advanced and enable the option Show Develop menu in the menu bar.
Next, open the Develop menu and select Experimental Features. In there, search for WebRTC and check the box next to it to turn it on. Once you have done that, WebRTC will be enabled in Safari.
Stopping WebRTC
To stop WebRTC, you can use the Avast SecureLine VPN browser extension. This free browser extension is availble for Google Chrome and Mozilla Firefox, and it blocks WebRTC. To install it, open the Avast SecureLine VPN app on your device, then select the “SecureLine Browser Extension” option from the main menu. Follow the prompts to install the extension in your preferred browser. Finally, enable the WebRTC Blocker feature within the extension settings to effectively stop WebRTC.
Does iOS Safari Support WebRTC?
No, iOS Safari does not currently support WebRTC. WebRTC is a web technology that allows for real-time communication between two devices in the form of peer-to-peer connections. The Safari 10 browser does not have native support for this technology, altough it can be enabled through third-party plugins and extensions. As of now, the only way to enable WebRTC on iOS Safari is through these third-party plugins. It is important to note that due to the lack of native support, users may experience certain limitations when using these plugins.
Understanding WebRTC on iPhone
WebRTC is a streaming protocol that enables real-time communication between mobile applications and web browsers, including those on iPhones. It was first released in 2011 and is now supported by all major modern browsers, including Safari on iPhones. WebRTC provides a variety of functionalities, such as voice calling, video conferencing, file sharing, text messaging, and more. With WebRTC, developers can create apps that run smoothly across different platforms and devices without having to rewrite code for each platform. Additionally, WebRTC is an open-source technology that encourages collaboration between developers and offers them access to the latest advancements in real-time communication.
Disabling WebRTC in Safari
In order to disable WebRTC in Safari, you will need to open the Settings application on your iOS device. Once you are in the Settings app, find and tap the Safari option. After that, tap on the Advanced option followed by Experimental Features. This will bring up a switch that you can use to turn off Legacy WebRTC API. After this is done, the switch will turn green to indicate that WebRTC has been successfully disabled for the current session.
Does iOS 13 Support WebRTC?
Yes, iOS 13 does support WebRTC. WebRTC (Web Real-Time Communication) is an open source framework for enabling web browsers and mobile applications to communicate using real-time data streaming. This allows for audio and video calls, as well as data sharing within a browser. The support for WebRTC in iOS 13 is limited to Safari; othr browsers do not yet have support for WebRTC on iOS devices.
Blocking WebRTC on an iPhone
If you’re using iOS 13 or below, you can block WebRTC on your iPhone by going to the Settings app, tapping on Safari, scrolling all the way down, and then tapping on Advanced. Under Experimental features, toggle off the switch for WebRTC mDNS ICE candidates. This will prevent websites from accessing your device’s local IP address and location information. However, if you’re using an updated version of iOS (iOS 14 or later), thee is no option to disable WebRTC directly on your device. Instead, you’ll need to use a third-party browser such as Firefox that offers an option to block WebRTC requests in its settings menu.
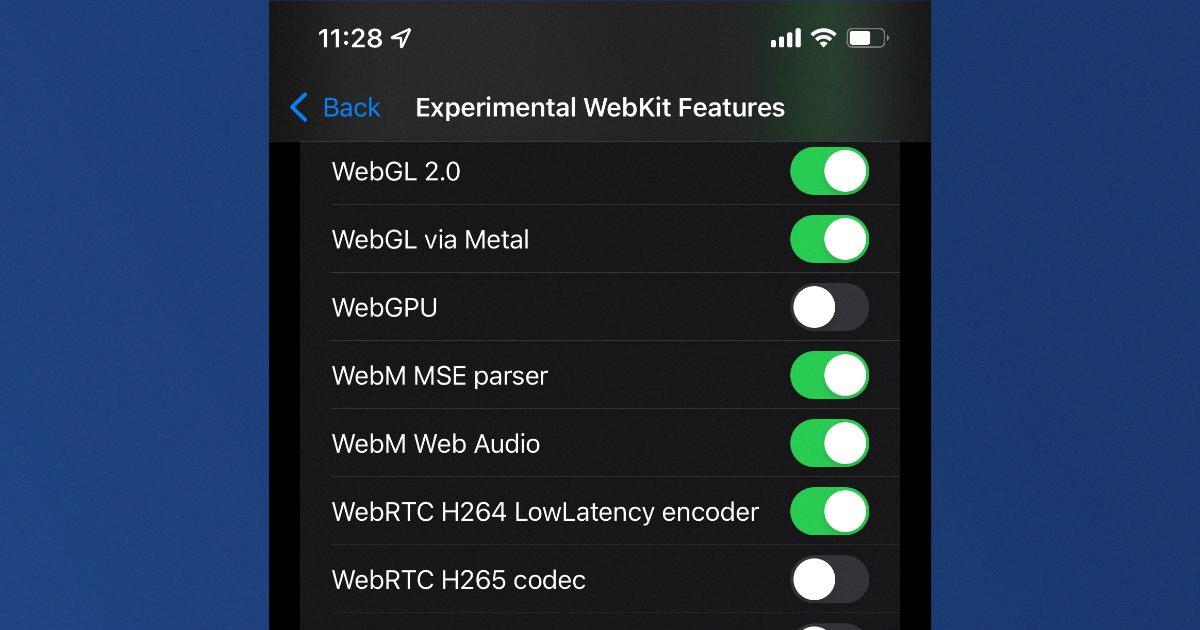
Should I Disable WebRTC?
It is a good idea to turn off WebRTC if you are concerned about protecting your privacy and security. WebRTC is a technology that allows websites and applications to access certain information about your network, such as your IP address, even if you are usng a VPN or proxy. This could potentially lead to sensitive information being exposed, and also give malicious actors a way to track you online. Disabling WebRTC can help protect your privacy by blocking websites from accessing information about your network. It can also help improve the performance of some applications, as not having to deal with the extra data exchanged through the WebRTC protocols can make them run smoother.
In conclusion, WebRTC is not supported on iOS devices. To disable WebRTC on Safari for iPhone, you will need to install the Avast SecureLine VPN browser extension and enable the WebRTC Blocker feature. This will prevent potential data leaks, keeping your data and browsing sessions secure while using Safari on your iPhone.
Related posts:
Sanjeev Singh

IMAGES
VIDEO
COMMENTS
Here's how: Click "Safari" in the menu bar. Then click Preferences. Click on the "Advanced" tab, then at the bottom check the box for "Show Develop menu in menu bar". Now, click on "Develop" in the menu bar. Under the "WebRTC" option, if "Enable Legacy WebRTC API" is checked, click on it to disable this option (no ...
You can turn WebRTC off in the developer settings: Open Safari and go to Safari > Preferences…. Go to the Advanced tab and check the box at the bottom that says Show Develop menu in menu bar. Close the preferences menu and go to Develop > Experimental Features. Check the option for Remove Legacy WebRTC API.
The problem lies in a browser more so than a VPN - as you'll learn later, Safari is quite safe when it comes to WebRTC leaks. 6 steps to confirm a WebRTC leak (with a VPN on and off) To test whether your browser is leaking your IP address, use any online WebRTC leak checker (there is also one at the top of this page).
Disabling WebRTC on Safari is possible, but the option is a bit harder to find than on Firefox. That's because WebRTC was only recently implemented, and is still considered an experimental feature that only developers would want to fiddle with. ... Your Safari is now free of WebRTC leaks. However, this may also prevent WebRTC-based services ...
Open the Brave browser. Find and click " Settings ". Click on the search icon, located in the upper right of the screen (or press CTRL+F) In the search bar, type webrtc. Under WebRTC IP Handling Policy, click the drop-down. Select "Default public interface only" from the drop-down. Restart browser and test for leaks.
Refresh the page and look for your IP again on a WebRTC leaks online checker. Among those, there are ipleak.net - which also tests for IPv4, IPv6, and DNS leaks ... With Safari, go to ...
Stopping a WebRTC Leak in Firefox. Unlike Chrome, Firefox does allow for these WebRTC related settings to be changed within the browser. It just takes three simple steps: After opening Firefox, enter "about:config" in the URL bar. The setting you need to search for is "media.peerconnection.enabled". Now double-click the entry, or single ...
Brave is a Chromium browser, but it's very privacy-focused and you can disable WebRTC using one of two methods explained below. Method 1. Click on the menu button in the top right corner and open the settings menu. Select Shields on the left-hand menu and find Fingerprinting blocking at the bottom of the list.
The good news is, it's possible to disable WebRTC in many popular browsers, and so prevent leaks. Here's how to disable WebRTC in Chrome, Firefox, and Safari. How to Disable WebRTC In Chrome It is not possible to manually disable WebRTC in the Chrome browser. However, there are several free extensions that can do just that.
Which browsers are affected by WebRTC leaks? Unfortunately, nearly all the best-known web browsers are susceptible to WebRTC leaks - and this is because WebRTC is usually enabled by default. If you're using Chrome, Firefox, Brave, Safari, or Edge, it's a good idea to perform a quick WebRTC leak to ensure you're not leaking your IP address!
Setting 3: Turn off WebGL. Similarly to turning off WebRTC, you can disable WebGL by typing in " about:config " in the address bar and searching for " webgl.disabled .". Toggle this setting to " True " by right-clicking on the toggle button to the right. Restart Firefox and you should've turned off WebGL.
WebRTC leak is more frequent where people depend on unreliable VPN services that can't protect users from such attacks. WebRTC channels, in some cases, bypass a VPN's encrypted tunnel through which your traffic flows. ... You've disabled WebRTC from Safari. 4. Microsoft Edge. If you're using Microsoft Edge, you should know that the ...
WebRTC leak has nothing to do with Safari. However, due to the recent integration of WebRTC with it, we should disable the WebRTC API for our privacy and security. Follow the steps to disable it.
The simplest solution to the problem is to just disable WebRTC. In Firefox can be easily done manually in the advanced settings: a) Type ' about:config' into the URL bar (and click through 'I'll be careful I promise!') b) Search for ' media.peerconnection.enabled '. c) Double-click on the entry to change the Value to ' false'.
Here's how you can disable WebRTC on Safari: Launch Safari on your device and select "Safari" in the menu. Then choose "Preferences" from the drop-down menu. After clicking on the "Advanced" tab, scroll down to the bottom of the page and tick the option labeled "Show Develop menu in menu bar.
How to disable WebRTC in Firefox on desktop. Type about:config into the address bar. Click the "I accept the risk!" button that appears. Type media.peerconnection.enabled in the search bar. Double-click to change the Value to "false". This should work on both mobile and desktop versions of Firefox.
Safari: By default, Safari adopts a stricter permissions model, significantly reducing the risk of WebRTC leaks. Opera and Microsoft Edge : These browsers offer settings to manage WebRTC traffic, though effectiveness may vary.
WebRTC leaks occur when a user's real IP address is exposed, potentially allowing others to track their online activities. ... Microsoft Edge, and Apple Safari. WebRTC is commonly used for video and audio communication, such as video conferencing, voice calling, and live streaming. It uses peer-to-peer communication, which means that data is ...
Open the Chrome Web Store. Search for 'WebRTC Control.'. Click 'Add to Chrome' and then 'Add Extension' to install the add-on. Right-click on the add-on icon to change its options. This article provides steps on how to disable WebRTC from your browser. Learn all about this feature and why you may want to turn it off.
The WebRTC Leak Test is a critical tool for anyone using a VPN, as it leverages the WebRTC API to communicate with a STUN server and potentially reveal the user's real local and public IP addresses, even when using a VPN, proxy server, or behind a NAT. This tool can help verify whether a real public IP is being leaked.
Safari and WebRTC in the wild. Logos added to Mountain Lion attacking deer-taxidermy photo by Flickr user Curious Expeditions (CC BY-NC-SA 2.0) In June of 2017, Apple became the last major vendor to release support for WebRTC, paving the (still bumpy) road for platform interoperability.
In order to disable WebRTC in Safari, you will need to open the Settings application on your iOS device. Once you are in the Settings app, find and tap the Safari option. After that, tap on the ...