- More from M-W
- To save this word, you'll need to log in. Log In

Definition of trip wire
Examples of trip wire in a sentence.
These examples are programmatically compiled from various online sources to illustrate current usage of the word 'trip wire.' Any opinions expressed in the examples do not represent those of Merriam-Webster or its editors. Send us feedback about these examples.
Word History
1915, in the meaning defined at sense 1
Dictionary Entries Near trip wire
Cite this entry.
“Trip wire.” Merriam-Webster.com Dictionary , Merriam-Webster, https://www.merriam-webster.com/dictionary/trip%20wire. Accessed 24 Apr. 2024.
More from Merriam-Webster on trip wire
Thesaurus: All synonyms and antonyms for trip wire
Subscribe to America's largest dictionary and get thousands more definitions and advanced search—ad free!

Can you solve 4 words at once?
Word of the day.
See Definitions and Examples »
Get Word of the Day daily email!
Popular in Grammar & Usage
More commonly misspelled words, commonly misspelled words, how to use em dashes (—), en dashes (–) , and hyphens (-), absent letters that are heard anyway, how to use accents and diacritical marks, popular in wordplay, the words of the week - apr. 19, 10 words from taylor swift songs (merriam's version), 9 superb owl words, 10 words for lesser-known games and sports, your favorite band is in the dictionary, games & quizzes.


- Your Cart is Empty
- What is a Trip Wire and How Do You Use It?
February 03, 2021
Recent Articles
- What the COVID-19 Pandemic Teaches Us About Being Prepared
- What are my rights during a state of emergency?
- Why did a pandemic result in almost 2 million gun sales?
- Is your internet connection secure? Why you need a VPN
What is a trip wire?
As its name suggests, a trip wire is a thin line of wire (or other material) that is intended to cause an intruder to trip over it, thus triggering a mechanism elsewhere that will activate an alarm. The wire is stretched tight and low to the ground between two fixed points, where it will be unseen. When an unwanted visitor trips over the wire, it activates an alarm system, which can be as crude or as elegant as you have the time and materials to construct. Trip wires have been used for hundreds of years by military, police, and civilians alike.
Trip wire comes in a variety of materials. Wire is often preferred due to its rigidity, but multifilament silicon coated Kevlar is also an excellent and more flexible option. In a pinch you could even use fishing line or string.
How do you use a trip wire?
A basic trip alarm system is essentially a simple booby trap. The alarm signaling device will be tethered to a length of trip wire. When the wire is pulled hard enough (presumably by someone tripping over it), it activates the device which alerts you to the presence of an intruder. It couldn’t be simpler!
Trip wire can also be used independently of a signaling device as an all-purpose wire for whatever purposes you need.
When might you need a trip wire?
Trip wires are often used, with or without a signaling device, for applications such as:
- Perimeter alarms
- Boundary setting
- DIY animal trapping
- Securing gear
Where can I get a trip wire?
Although just about any kind of string or wire can work in a pinch, the Kevlar Trip Line included in our Tripwire Alarm Kit makes excellent trip line (it’s not actually wire) due to its flexibility and ease of deployment. Get yours here: https://tihk.co/collections/urban-survival-gear/products/tripwire-alarm-kit
Instagram Feed
Facebook feed.
- Affiliate Program
- Press & Media
Copyright © 2024 TIHK. U.S. Patents Pending.
DISCLAIMER: Our products may contains certain features that may be regulated in your state. You are solely responsible for complying with local, state and federal laws. Your use of the product is at your risk and discretion. Don't be stupid. We are not responsible for your use of the product in any way including complying with any application laws or regulations in your state.

TERMS OF SERVICE
Last Updated: October 10, 2017
Welcome to http://tihk.co/, owned and operated by Quampton LLC (“TIHK”, “we”, “us” or “our”). We are makers of urban survival products, designed and manufactured in the USA. Please read these Terms of Service (“Terms”) carefully because they govern your use of the website http://tihk.co/ (the “Site”), and the content, services, and products available at or through the Site and associated social media profiles. If you have any questions, please contact us . To make these Terms easier to read, the Site, and our products and services and are collectively called the “Services.”
Agreement to Terms
By accessing, or using our Services, you agree to be bound by these Terms. If you do not agree to these Terms, simply stop using the Services.
Changes to Terms or Services
We may modify these Terms and our Services at any time, in our sole discretion. If we do so, we’ll make it known on the Site. It’s important that you review the Terms whenever we modify them because continuing to use the Services after we have posted modified Terms on the Site indicates to Us that you agree to be bound by the modified Terms. If you don’t agree to be bound by the modified Terms, please discontinue use of the Services immediately. Because our Services are evolving over time we may change or discontinue all or any part of the Services, at any time and without notice to you, at our sole discretion.
Privacy policy
Your privacy is important to us. Please review our Privacy Policy for information about the data we may collect and use. Our Privacy Policy is incorporated in these Terms, and is available at http://tihk.co/pages/privacy-policy .
We welcome feedback, comments and suggestions for improvements to the Services. You can submit feedback by emailing us at [email protected]. You grant to us a non-exclusive, worldwide, perpetual, irrevocable, fully-paid, royalty-free, sublicensable and transferable license under any and all intellectual property rights that you own or control to use, copy, modify, create derivative works based upon and otherwise exploit the feedback for any purpose
TIHK Content
Subject to your compliance with these Terms, TIHK grants you a limited, non-exclusive, non-transferable, non-sublicenseable license to access and view the content we create, post, upload, or otherwise make available to you (“TIHK Content”) solely in connection with your permitted use of the Services and solely for your personal and non-commercial purposes. You may not: (i) copy, modify or distribute TIHK Content for any purpose; (ii) transfer, sublicense, lease, lend, rent or otherwise distribute TIHK Content to any third party; (iii) decompile, reverse-engineer, disassemble, or create derivative works of TIHK Content or the Services; or (iv) use the Services in any unlawful manner, for any unlawful purpose, or in any manner inconsistent with these Terms. You acknowledge sole responsibility for and assume all risk arising from your use or reliance of any TIHK Content.
Application of Products
Application.
Certain of our products may feature sharp objects, or objects with an inherently elevated risk of physical injury. None of TIHK’s products are designed with testing and components for a level of reliability suitable for use in or in connection with surgical implants or as critical components in any life support systems. None of TIHK’s products are intended as a medical or life saving device.
In any application, including the above, where a product use would create a risk of harm to property or person (including the risk of bodily injury and death) it is the sole responsibility of the persons contemplating such use to comply with all applicable laws, regulations, codes and standards. To avoid damage, injury, or death, the user must take reasonably prudent steps to protect against failures. The user is ultimately responsible for verifying and validating the suitability of TIHK products whenever you intend to use any such product.
Compliance with Local, State & Federal Regulations
Certain of our products may contain features that may be regulated in your state. You are solely responsible for complying with local, state and federal laws. Your use of the product is at your risk and discretion. We are not responsible for your use of the product in any way including complying with any application laws or regulations in your state.
Payment & Delivery
Price & payment terms.
TIHK products are intended for your own personal use and not for resale, unless authorized in writing by TIHK. In order to make a purchase (or two, or three...!), you will need a valid credit card. You agree to provide only information that is accurate and current, and that you have authorization to provide. You may choose to save the information you enter for the next time you visit the Site or make a purchase. You may be charged additional fees, taxes or other costs, in addition to the retail price of our products. For more information about how we handle credit card and other personally identifying and sensitive personal information you may provide us, please read our Privacy Policy at http://tihk.co/pages/privacy-policy . Please note that you are subject to the terms and privacy policies of, and proceed to use at your own risk, any payment processors we may offer for your use, such as Stripe and PayPal. All transactions are secure and encrypted, and we never store your credit card information.
TIHK offers you the several shipping options to ensure delivery of your purchased items. TIHK does not and cannot control the delivery carrier’s estimated or actual time of delivery of the items, and TIHK does not and cannot take the responsibility of ensuring that you have received your items. Please enter an accurate and accessible shipping address to ensure prompt delivery.
Back Ordered Items
Orders that contain a combination of in-stock and back ordered items will ship once all products are in stock.
Returns, Exchanges & Refunds
If you are unsatisfied with your items for any reason, you may return it within thirty (30) days from delivery. Items must be unused and in original packaging. Please contact us with your order number to initiate a return. Any custom/built-to-order items are not returnable. To return your product, you should mail your product to:
1941 1st Ave S #3E
Seattle , WA 98134
You are responsible for your own shipping costs for returning your item(s). Shipping costs are non-refundable. If you receive a refund, the cost of return shipping will be deducted from your refund. If you are shipping an item over $75, you should consider using a trackable shipping service or purchasing shipping insurance. We do not guarantee that we will receive your returned item.
TIHK warrants its products from defects in materials and workmanship for a period of thirty (30) days from delivery. This limited warranty shall not apply to damages due to: a) abuse, misuse, or neglect of the purchased item(s); b) modifications or repairs made to purchased item(s), other than those made by TIHK; c) improper use; or d) excessive mechanical, physical, electrical stress, or environmental stress on the purchased item(s).
Once your return is received and inspected, we will send you an email to notify you that we have received your returned item. We will also notify you of the approval or rejection of your refund. If you are approved for a refund, it will be processed, and a credited to your original method of payment automatically. If you have requested an exchange, we will notify you of shipment of the items upon shipment.
Links and Advertisements of Third Party Websites
The Services may contain links to or advertisements of third-party websites or resources. We are not responsible for the content, products or services on or available from those advertisements, websites, resources or links displayed on such sites. You acknowledge sole responsibility for and assume all risk arising from, your use of any third-party websites or resources.
Termination
Upon any termination, discontinuation or cancellation of Services to you, all provisions of these Terms which by their nature should survive will survive, including, without limitation indemnification, warranty disclaimers, limitations of liability, and dispute resolution provisions.
You agree to defend, indemnify and hold harmless TIHK, or its officers, directors, employees agents, suppliers and partners, from and against any and all claims, damages, obligations, losses, liabilities, costs, debts, or expenses (including but not limited to attorneys’ fees), to the extent allowed by applicable law, that arise from or are caused by: a) your use of and access to the Services; b) your violation of these Terms; or c) your violation of any third party right, including without limitation any copyright, property, moral or privacy right. This section shall survive these Terms and your use and termination of the Services.
Representations and Warranties; Disclaimers
THE SERVICES AND ALL CONTENT ARE PROVIDED “AS IS,” WITHOUT WARRANTY OF ANY KIND. WITHOUT LIMITING THE FOREGOING, WE EXPLICITLY DISCLAIM ANY WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, QUIET ENJOYMENT OR NON-INFRINGEMENT, AND ANY WARRANTIES ARISING OUT OF COURSE OF DEALING OR USAGE OF TRADE. WE MAKE NO WARRANTY THAT THE SERVICES WILL MEET YOUR REQUIREMENTS OR BE AVAILABLE ON AN UNINTERRUPTED, SECURE, OR ERROR-FREE BASIS. WE MAKE NO WARRANTY REGARDING THE QUALITY, ACCURACY, TIMELINESS, TRUTHFULNESS, COMPLETENESS OR RELIABILITY OF ANY CONTENT.
Limitation of Liability
NEITHER TIHK NOR ANY OTHER PARTY INVOLVED IN CREATING, PRODUCING, OR DELIVERING THE SERVICES, PRODUCTS OR TIHK CONTENT WILL BE LIABLE FOR ANY INCIDENTAL, SPECIAL, EXEMPLARY OR CONSEQUENTIAL DAMAGES, INCLUDING LOST PROFITS, LOSS OF DATA OR GOODWILL, SERVICE INTERRUPTION, MOBILE DAMAGE OR SYSTEM FAILURE OR THE COST OF SUBSTITUTE SERVICES ARISING OUT OF OR IN CONNECTION WITH THESE TERMS OR FROM THE USE OF OR INABILITY TO USE THE SERVICES OR CONTENT, WHETHER BASED ON WARRANTY, CONTRACT, TORT (INCLUDING NEGLIGENCE), PRODUCT LIABILITY OR ANY OTHER LEGAL THEORY, AND WHETHER OR NOT CLASSPOP HAS BEEN INFORMED OF THE POSSIBILITY OF SUCH DAMAGE, EVEN IF A LIMITED REMEDY SET FORTH HEREIN IS FOUND TO HAVE FAILED OF ITS ESSENTIAL PURPOSE. IN NO EVENT WILL TIHK’S TOTAL LIABILITY ARISING OUT OF OR IN CONNECTION WITH THESE TERMS OR FROM THE USE OF OR INABILITY TO USE THE SERVICES OR CONTENT EXCEED THE LESSER OF THE AMOUNTS YOU HAVE PAID TO TIHK FOR USE OF THE SERVICES OR TIHK CONTENT OR FIFTY DOLLARS ($50), IF YOU HAVE NOT HAD ANY PAYMENT OBLIGATIONS TO TIHK, AS APPLICABLE.
Waiver of Liability
TIHK is in no way responsible or to be held liable for any claims, including for physical, bodily or financial injury, arising out of your use of TIHK product(s) on the whole, and your use of TIHK product(s) in your state, and you are subject to the additional terms and policies of each applicable private venue, local, state and federal laws as applicable.
Dispute Resolution
We prefer to resolve things amiably when possible therefore, you agree to the following dispute resolution policy in connection with any potential claims or disputes arising from your use of the Application. Start by notifying us of your dispute by sending a notice via our contact form .
- Informal Negotiations : Parties to a dispute concerning the Terms, the Privacy Policy, or the use of the Services will attempt to informally negotiate a potential settlement or resolution to the dispute;
- Arbitration : In the event that informal negotiations are unsuccessful, the parties agree to follow the arbitration procedures set forth by the American Arbitration Association (AAA) to resolve the dispute.
- Binding Arbitration : If for any reason arbitration is unsuccessful or unavailable to the parties, parties agree to submit to binding arbitration in the State of Washington. Each of us is responsible for paying our own filing, administrative and arbitrator fees. Judgment on the arbitration award may be entered in any court having jurisdiction thereof.
Entire Agreement
These Terms, and any future updates we make, constitute the entire and exclusive understanding and agreement between you and TIHK. If for any reason a court of competent jurisdiction finds any provision of these Terms invalid or unenforceable, that provision will be enforced to the maximum extent permissible and the other provisions of these Terms will remain in full force and effect. You may not assign or transfer these Terms, by operation of law or otherwise, without our prior written consent. Any attempt by you to assign or transfer these Terms, without such consent, will be null and of no effect. If we provide certain notices or other communications to you, we will place the information on the Site.
TIHK’s failure to enforce any right or provision of these Terms will not be considered a waiver of those rights. The waiver of any such right or provision will be effective only if in writing and signed by a duly authorized representative TIHK. Except as expressly set forth in these Terms, the exercise by either party of any of its remedies under these Terms will be without prejudice to its other remedies under these Terms or otherwise.
Questions & contact information
If you have any questions regarding these Terms, please contact us.
- Post a Job Post a Job
- Find Talent Find Talent
- Log in Log in
Tripwire explained
Tripwire: Enhancing Cybersecurity with File Integrity Monitoring
Table of contents
Introduction, what is tripwire, how tripwire is used, background and history of tripwire, examples and use cases, career aspects, relevance and best practices.
In the world of cybersecurity, organizations face a constant battle to protect their digital assets from unauthorized access, data breaches, and other security incidents. One crucial aspect of maintaining a secure environment is ensuring the integrity of critical files and system configurations. This is where Tripwire, a leading file integrity Monitoring (FIM) solution, comes into play. In this article, we will explore Tripwire in detail, covering its definition, usage, background, examples, use cases, career aspects, relevance in the industry, and best practices.
Tripwire is a comprehensive security solution that provides file integrity monitoring, vulnerability management, and configuration assessment capabilities. Its primary objective is to detect and alert on unauthorized changes made to files, directories, and system configurations. By continuously monitoring and analyzing these changes, Tripwire helps organizations identify potential security breaches, Compliance violations, and system misconfigurations.
Tripwire operates by comparing the current state of files and configurations against a known baseline or set of predefined policies. It accomplishes this through the following key components:
Baseline Creation : Initially, Tripwire creates a baseline by scanning and cataloging the current state of files, directories, and system configurations. This baseline acts as a reference point against which subsequent changes will be compared.
Monitoring : Once the baseline is established, Tripwire continually monitors the integrity of files and configurations for any modifications. It uses cryptographic hashes, such as MD5 or SHA-256, to verify the integrity of files and detect any alterations.
Change Detection : Any changes made to files or configurations are detected by comparing the current state with the baseline. Tripwire generates alerts and notifications whenever unauthorized or unexpected modifications are identified.
Alerting and Reporting : Tripwire provides real-time alerts and detailed reports to security teams, enabling them to investigate and respond to potential security incidents promptly. These alerts can be integrated with security information and event management ( SIEM ) systems for centralized monitoring and correlation.
Remediation : To ensure the integrity of the system, Tripwire helps organizations restore the affected files or configurations to their trusted state. It also assists in identifying the root cause of the changes and implementing preventive measures to minimize future incidents.
Tripwire was initially developed in 1992 by Gene Kim, Dr. Gene Spafford, and Dr. Ron Ritchey as an open-source Intrusion detection system for Unix-based systems. It gained popularity due to its effectiveness in detecting unauthorized changes to critical files and directories. In 1997, Tripwire, Inc. was founded to commercialize the solution and provide enterprise-grade support and additional features.
Over the years, Tripwire evolved into a comprehensive security suite, offering a range of capabilities beyond file integrity monitoring. Tripwire, Inc. has expanded its product portfolio to include vulnerability management, configuration assessment, and Threat intelligence solutions. Today, Tripwire is widely recognized as a leading provider of security and compliance solutions for organizations across various industries.
Tripwire finds application in a wide range of industries and use cases. Here are a few examples:
Financial Institutions : Banks and financial organizations rely on Tripwire to ensure the integrity of critical financial data, transaction records, and regulatory Compliance . It helps detect unauthorized changes that could lead to fraud or compromise the integrity of financial systems.
Healthcare Providers : Healthcare organizations use Tripwire to protect patient data, comply with industry regulations like the Health Insurance Portability and Accountability Act ( HIPAA ), and safeguard medical devices from unauthorized modifications.
Government Agencies : Government agencies leverage Tripwire to secure sensitive information, critical infrastructure, and ensure compliance with security standards such as the Federal Information Security Management Act ( FISMA ).
Cloud Environments : Tripwire plays a vital role in securing cloud-based infrastructure and virtualized environments. It helps organizations monitor and control changes to virtual machines, containers, and cloud configurations.
As the demand for robust cybersecurity solutions continues to grow, professionals with expertise in Tripwire and file integrity monitoring are in high demand. Career opportunities in this field include:
Tripwire Administrator : Responsible for managing Tripwire deployments, configuring policies, creating baselines, and analyzing alerts generated by the system.
Security Analyst : Utilizes Tripwire to analyze alerts, investigate potential security incidents, and develop strategies for enhancing the overall security posture of an organization.
Compliance Officer : Ensures that the organization adheres to relevant security standards, regulations, and policies by leveraging Tripwire's compliance-focused features.
Security Consultant : Provides expert advice and guidance on implementing Tripwire and other security solutions, conducts security assessments, and assists organizations in optimizing their security controls.
Tripwire continues to be a relevant and indispensable tool in the cybersecurity landscape. It helps organizations address various security challenges, including:
- Detecting unauthorized changes to files, configurations, and critical systems.
- Ensuring compliance with industry regulations and security standards.
- Identifying Vulnerabilities and misconfigurations that can be exploited by attackers.
- Enhancing Incident response capabilities through real-time alerts and detailed reports.
To maximize the effectiveness of Tripwire and ensure its successful implementation, organizations should follow these best practices:
- Regularly update Tripwire's baseline to reflect changes in the environment.
- Implement a robust change management process to differentiate authorized changes from unauthorized ones.
- Integrate Tripwire with other security solutions, such as SIEM and vulnerability scanners, for enhanced visibility and correlation.
- Periodically review and fine-tune Tripwire policies to minimize false positives and false negatives.
- Leverage Tripwire's compliance features to streamline Audits and maintain regulatory compliance.
In conclusion, Tripwire's file integrity monitoring capabilities provide organizations with a powerful tool to enhance their cybersecurity posture. By continuously monitoring and detecting unauthorized changes, Tripwire helps organizations identify potential security incidents, maintain compliance, and protect critical assets. As the cybersecurity landscape evolves, Tripwire remains a relevant and valuable solution for organizations across various industries.
References:
- Tripwire Official Website: https://www.tripwire.com/
- Tripwire Wikipedia Page: https://en.wikipedia.org/wiki/Tripwire_(software)
- Tripwire Enterprise User Guide: https://support.tripwire.com/s/article/Tripwire-Enterprise-User-Guide
- Tripwire and Cloud Security: https://www.tripwire.com/state-of-security/security-data-protection/cloud-tripwire/
SOC 2 Manager, Audit and Certification
@ Deloitte | US and CA Multiple Locations
Information Security Engineers
@ D. E. Shaw Research | New York City
Information Technology Specialist II: Network Architect
@ Los Angeles County Employees Retirement Association (LACERA) | Pasadena, CA
Product Security Analyst
@ Terumo Blood and Cell Technologies | Lakewood, CO, US
Product Security Test Engineer (Experienced or Senior)
@ Boeing | USA - Berkeley, MO
Cyber Security Graduate Trainee
@ Newcastle University | Newcastle, GB
Tripwire jobs
Looking for InfoSec / Cybersecurity jobs related to Tripwire? Check out all the latest job openings on our Tripwire job list page.
Tripwire talents
Looking for InfoSec / Cybersecurity talent with experience in Tripwire? Check out all the latest talent profiles on our Tripwire talent search page.
Related articles
Urban Survival Site
Want To Prep But Not Sure Where To Begin?
Sign Up for Our Newsletter and Get Your FREE One Year Urban Survival Plan!
We won't send you spam. Unsubscribe at any time.
6 DIY Trip Wire Alarms for Off-Grid Security
By Steve Nubie 2 Comments
Estimated reading time: 28 minutes

A lot of folks have never put together a trip wire alarm, and there’s a good reason. There are just not a lot of occasions where a trip wire is necessary. However, when those occasions do emerge, it’s at least worth understanding the concept of what works and what doesn’t.
What Exactly is a Trip Wire?
But who needs them now, do it yourself versus buy it yourself, trip wire 101, electrical wire, monofilament fishing line, bungee cord, lasers, infrared, and motion detectors, rocks in cans, firecracker poppers, .22-caliber blanks, air horns, sirens, and other noise makers, what about light, this is not about the use of lethal force, location, location, location, 1. bungee marbles, 2. monofilament on the rocks, 3. paracord pull-string fireworks, 4. thin wire .22-caliber blank, 5. winter white trip wire, 6. back gate avalanche, is this a good idea.
A trip wire is a long length of thin wire, monofilament fishing line, or any other type of cordage that is usually connected to something that makes noise. The idea is that when an intruder either human or animal steps into the wire, the alarm is sprung, alerting you to an intrusion.
The trip wire concept was developed in wartime as a way to alert troops of an enemy incursion. This was particularly needed at night and was often used in the dense island jungles during the war in the Pacific in World War II.
The usual configuration was a thin length of rope suspended low to the ground between trees with empty C-ration cans filled with stones to rattle the alarm whenever the wire was “tripped.” And while booby traps were sometimes used to maim or kill, there was always the concern that an innocent civilian or friendly soldier wandering off to go relieve himself would trip the wire.
Want to save this post for later? Click Here to Pin It On Pinterest!

The usual reason someone considers a trip wire is when they are in an area with the potential for any number of unknown threats. The idea is usually to make noise to signal an intruder .
- The threat could be from wild animals like bears or wolves approaching a camp in a remote area.
- In countries ravaged by civil wars and civil unrest, no night is safe and trip wires are sometimes used to at least alert the local population if a covert threat is approaching.
- Following a disaster , many people find themselves isolated and alone with the potential for looters or worse. That’s when a trip wire may at least scare them off, if not serve as a warning of an unwelcome approach.
- In times requiring a bug-out to a distant but safer location, there are occasions where a night must be spent on the road in unknown territory where the threat is equally mysterious. Trip wires would serve as a perimeter defense to at least alert anyone spending an unplanned night on the road of any approach.
- And yes, they’re still used in war zones, although the technology of trip wires in those areas is usually defined by lasers, electronic signals, or infrared beams connected to electronic alerts through cameras or video or in extreme cases: explosives.
- In fact, the concept of contemporary home security systems connected to motion-detector technology to turn on lights; sound an alarm, record video, or alert the local police are the 21 st century versions of the trip wire concept.
It may seem unnecessary to build your own trip wires when so many options appear on the Internet , but if a situation makes the Internet undependable or unavailable, or deliveries or the purchase of many things is difficult or impossible, that might be a good time to know how to improvise a trip wire.
There’s also the fact that in some instances, the electricity is out or unavailable, and most modern security solutions require at least some level of power. In a worst case scenario with a total grid failure, technology will quickly diminish and old-school, analog solutions will offer the most dependable options. Those are the types of trip wire concepts we’ll cover.
We might as well start with the wire. There are a variety of options . Usually, the wire or cord is low-profile and hard to see. It also needs to be relatively strong. If someone or something walks through the wire or cord and it easily breaks, little is accomplished except alerting the intruder to the fact that you’ve setup some trip wires.
Here are options to consider:

Electrical wire comes in a variety of gauges, but the smallest (and most inexpensive) gauges are referred to as 14 and 16 gauge. They’re more than strong enough to serve as a trip wire.
They’re all coated with a flexible plastic coating that comes in a range of colors. White, black, red, and green are the most common, and those colors present camouflaged, stealth characteristics, depending on the time of year, time of day, and natural surroundings. Floral wire is another option and also comes in a variety of colors.

Fishing line is thin, strong, and also hard to see. Buy one of the heavier weight tests of at least 50 pounds or more. Avoid any of the brightly colored lines. Go with a neutral, plain monofilament.

Paracord is another surprisingly strong option, but you have to think about the color of the cord. During winter, a white Paracord might makes sense if the ground is snow covered. A green or camo cord could work well in a forest or field. Black is an obvious choice for night.

You don’t see bungee cord mentioned in a lot of the write-ups about trip wires, but it has a characteristic that could make sense if you think about it. If the idea of your trip wire is to rattle a bell, cans, or other noise maker, a bungee cord will certainly make that happen.
In fact, a bungee cord may cause more noise to occur than any of the other options we’ve mentioned due to its flexibility and springiness. A black bungee makes sense. Green if you’re in the woods.
If your trip wire is designed to trigger a mechanism, bungee is not the best choice, but if you’re rattling cans the old-fashioned way, it’s a good option.

You can buy these things and improvise a trip wire yourself, but make sure they’re battery or solar powered or have a way to recharge the batteries . These are complicated solutions, so we’ll mention them but we’re not going to spend a lot of time covering ways to make technology work in a primitive environment.
Some websites offer tips and solutions to improvising trip wires with technology, but it’s a lot of work and you have to consider how and when you’ll need any trip wire, and for how long.
The idea of most trip wires is to make a lot of noise when someone trips over the wire. Noise makers vary depending on what you have available or may have bought in advance. We’re going to assume your situation caught you a bit by surprise and that you have to improvise from available materials.
It’s believable that a lot of us would have wire, cords, and fishing line lying, around but things that make noise require a bit of creativity or at least some pre-planning , especially if you require a very loud alarm.
How loud your alarm needs to be depends on your distance from the trip wire and whether you are inside or outside. Someone camping in a tent will be more likely to hear a rattle of rocks in a can than someone sleeping in their home or cabin.
If you are at a distance from your trip wire or indoors, you may need to plan and buy ahead to acquire louder alarms like blank cartridge firing mechanisms, firecracker poppers, air horns, or anything else that will be heard under most circumstances.
Want to prep but not sure where to begin? Click Here to Get Your FREE One Year Urban Survival Plan!
And if you can, paint your alarms to match the environment. If you don’t have paint, you can rub some mud or clay on the bell/can/noisemaker so it is somewhat camouflaged. Black is good at night, camo combos for any natural forest or field, and snow white for winter.
If you’re trying to keep animals at bay, the colors are less of an issue. Animals only see in black and white, but keep an eye on the contrast. They can still notice highly contrasting shades.

A lot of us have bells around for various reasons including cowbells, Christmas bells, antique bells, and collectible bells. And then some of us don’t. If you have any assortment of bells, you’re off to a good start with a trip wire.

Even if you’re not a bell collector, there’s a good chance you have access to tin cans and rocks. No rocks? Anything that makes noise in a can will do from bolts to nuts or better yet, marbles— although marbles may jostle around in your can in the wind, so maybe stick with the pebbles.

You only want a few in the can but enough to make noise when the can is jostled. Smooth, rounded stones and marbles are best. Look for rounded stones in river and creek beds.
Drop a few in and give the can a shake. Adjust until you think you have the most and best noise for a shake. And if you don’t think a rattling can is going to work, then you’ll need to think about stocking some very loud alarms like the next few items.

There’s a type of firework that has two stings emerging from either end of a firecracker. When you pull the stings, the firecracker pops. They’re loud, and you can tie them onto a number of trip wires around your area.
Some of them are made out of paper and will get wet due to rain, snow, or morning dew, so wrap them in plastic cut from a black or neutral garbage bag. They’ll most likely scare off a wild animal and might scare off an intruder. Either way you’ll certainly hear it.

This isn’t about setting up a full loaded .22 caliber round on a trip wire. That’s a really bad idea. Trip wires are indiscriminate and when tripped, the wire fires. Most .22-caliber blanks are used for nail hammers to drive nails and pins into concrete.
The firing mechanism for trip wires and .22 blanks can be bought online , although the blanks are available at most hardware stores next to the nail guns . There are also 12-gauge blank variations on this concept.
As a trip wire, they’re mostly designed to deter wild animals, but the people who sell them offer all sorts of reasons to use them . You’ll certainly hear it, and it will scare most anyone and anything away.
However, it may cause a response you don’t necessarily want. If someone is approaching and they are armed, they may perceive the detonation of a .22-caliber blank round as actual gunfire and return fire. Up to you.

If it makes noise, it’ll work on a trip wire. The only challenge is figuring out how to trigger the noise. Things like sirens need power, but if you’re handy with a little wiring, you can make a trip-switch to set off the siren.
There are also solar powered options available . There’s some advice out there about setting up a rock over an a ir horn that will fall on the air horn button when tripped. That requires some precise setup and once that rock is on the air horn, it’s going to make a lot of noise until you lift the rock.
You’ll also probably use up all the air in the horn by the time you get out of bed or your sleeping bag to lift the rock.

There are solar powered motion detectors that will illuminate an area. These are best hung high in a tree out of sight and out of reach. It’s a variation on the trip wire concept, and it’s usually used to dissuade animals. It could also deter an intruder, but if you’re using something to trip an alarm that will notify you of an intrusion, a light in the night will do little good if you don’t see it while you’re sleeping or otherwise occupied.
Most trip wire concepts are designed to make noise to let you know that someone or something is approaching, and improvising a light to a trip wire can get a little complicated unless you have some good skills with wiring and trip switches. We’re going to skip the lights and stick with noise.
Booby traps have often been used in times of war and they are designed to kill. That’s a really bad idea. The whole idea is to either scare something or someone away with sound or to at least be alerted to the presence of something approaching.
Even a blank .22-caliber cartridge should be pointed towards the ground. Otherwise, the blast could send shrapnel from a tree trunk or branch in someone’s direction, and you don’t want it to be one of your children or an innocent wanderer lost in the night. This is about making noise, not war .
Where you place any trip wire is as important as the design of the trip wire itself. You want it far enough away to give yourself some time to observe the direction of the alarm and see what’s coming plus prepare to respond. But you also want it close enough so you can hear it.
Another location factor is the height of the trip wire from the ground. If you’re concerned about human intruders or large animals like a bear , you’ll want your trip wire about a foot above the ground. 6-inches above the ground is about the minimum or someone or something could step on the wire without tripping it.

Also, if it’s any lower than 6 inches, every random squirrel, raccoon, possum or most any other rodent could trip your wire repeatedly. If that happens enough, you may take to ignoring the trip wire noise while assuming it’s just another passing rabbit when it’s the intruder you were so worried about in the first place.
Support for attaching a trip wire is something else to think about. A lot depends on what’s available at the location and what kind of trip wire you’re using. Two tree trunks could work, but they will create a very taut trip wire that may not ring any bells for long. They could also cause an intruder to literally trip which may be an effective deterrent–or not.
The branches of two trees or two saplings give some flexibility to any trip wire and could result in a sway in the wire, causing the noise to persist a little longer.
Two stakes in the ground are another solution, but if you’re trying to raise your trip wire to a foot of height, you’ll need long and large stakes deeply imbedded in the ground.
The number of trip wires you set up is another location consideration. Think in terms of avenues of approach. Around a home or dwelling, any open area like a gap in a fence, a gate, an open back or front yard, approaches to doors or windows, or approaches to outbuildings are worth thinking about.
A lot depends on what you’re worried about, the location, and the immediate threat level.

A remote survival camp or any campsite for that matter might require a number of trip wire setups, but even then –animals prefer open paths and clear terrain. A human intruder may do otherwise and stick to the cover of scrub, brush, and trees, so you just have to do your best to estimate what could be coming and from where.
Check your trip wires if you have them in place for any length of time. Improvising an alarm with some rocks in a can is a good idea, at least until it rains or freezes and the water or frozen rocks in the can fail to rattle.
It’s also possible one of your trips has worked loose; been tripped without you knowing it, and loose on the ground, or something as simple as a knot that has worked loose. It’s actually somewhat of a “set it and forget it” approach, but it’s worth checking them from time to time if you need them for any duration.
Remove your trip wires when you don’t need them anymore or when you move on. They will cause you or anyone else to trip, including family members, as long as they’re in place. You also may need them again.
The DIY Trip wires

The advantage of a bungee cord as a trip wire is its springiness. Think of it as a rubber band on steroids. In fact, the interior of a bungee cord is just that. Long strands of rubber encased in a flexible fabric braid.
You can attach anything that makes noise to a bungee cord. The advantage is that a bungee will rattle and shake longer while making more noise.
- Bungee cord of sufficient length for your trip wire area. You can buy coiled bungee cord in various colors and cut them to length. If you only have packaged bungee cords of varying lengths with hooks, you can connect them together, although the hooks will be somewhat visible during the day.
- Various soup cans painted to match the terrain or time of day. They should also have holes punched towards the top of the can on either side.

- (You can substitute bells for the cans.)
- Choose a bungee cord color that you think will blend in the best with the surrounding areas.
- Wrap the one end of the bungee around a tree trunk, branch, sapling or stake. Tie it off with two half-hitches and pull tight.
- Thread your can or cans onto the bungee.
- Stretch it tight to another tree trunk, branch, sapling or stake and wrap and knot with two half hitches until tightened.

- Add marbles to the can and test it with a few pulls on the bungee. Add or remove marbles depending on the sound.
- Test your bungee trip wire again with someone in camp or in the house and ask them if they can hear the cans? If not, move the trip wire closer or add some more cans.

Monofilament is an excellent trip wire source. It’s hard to see during the day and totally invisible at night. The key is to have a strong enough weight test to activate the noise without breaking. It can be used in most any trip wire setup in any location.
- Monofilament fishing line. 50 pound test or higher is best, but any weight test will do if it’s all you have on hand. You could even double or triple up the monofilament if you’re worried it will break or snap.
- Empty tin cans. Soup cans are a good size. Peel off any colorful labels and either paint them or coat them in a thin film of mud so they are less reflective. Paint the cans black or do a camo pattern depending on the surrounding area.
- Smooth, round rocks, nuts, bolts, marbles —anything hard that can easily move around and rattle in the can.
- Cordage or wire to attach the cans to the monofilament.
- Wrap the one end of the monofilament around a tree trunk, branch, sapling or stake. Tie it off with an improved clinch knot (a fishing knot perfectly suited to monofilament) and pull tight.
- Punch 4 holes in each can.

The holes should be punched in pairs towards the top of the can about a ½ inch apart and opposite each other at the rim of the can. This is so the can is bound tight to the monofilament as it is threaded through the holes to ensure a good shake.

- Thread the monofilament through the holes.

- Add the can or cans along the monofilament, but try to place them in spots that are obscured by brush, tall grass, or other natural camouflage. It makes no difference at night, but take a look when it’s dark to be sure.
- Stretch it tight to another tree trunk, branch, sapling, or stake and wrap and knot with another improved clinch knot and pull light.
- Try to locate the cans in a location that is hard to see during the day.
- Drop a few rocks in the can and shake the fishing line wire to see if the cans rattle. Add more or less rocks until the cans make a racket. Continue to add cans where you can. Tighten the cans to the monofilament if you need to.
- Test your monofilament trip wire and have someone in camp listen and ask them if they can hear the cans. If not, move the trip wire closer or add more cans.
- Thin paracord . A type I or type II is thin enough to be obscure but strong enough to function as a trip wire. Choose the color that best matches the terrain and time of day.
- Pull-string fireworks. They’re legal to buy in most states and can also be purchased online. You’ll need to have them on hand because they’re very difficult to improvise.
- Choose a paracord color that will blend in with the surrounding area.
- Wrap the one end of the paracord around a tree trunk, branch, sapling, or stake.
- Find a location that is hard to see along the paracord and tie one end of the pull-string firecracker to the cord.
- Tie the other end of the paracord to another tree trunk, branch, sapling, or stake and wrap and knot with two half hitches until tightened.
- Carefully tie the paracord to the other end of the pull-string using a square knot or any knot you can improvise. You have to do this delicately. You want the paracord tight, but you don’t want to accidentally detonate the firecracker. If you want to get the best tight line, you could tie the final end of the paracord to the tree or stake with a trucker’s hitch . This will give you a little more control over the slack, but be gentle.
- You don’t want to test your popper trip wire or you’ll have to retie another one. If you want to test the distance and whether or not you’ll hear it, have someone in camp or in the house listen while you pull a spare popper. If they don’t hear it, move the trip wire closer. Don’t be tempted to add multiple poppers to the same trip wire. What will most likely happen is that one popper will trip, leaving any others unexploded.
- Unlike bells and tin cans, you have to rearm your firecracker trip wire whenever it goes off. That’s not a bad idea to at least see if there are any footprints or paw prints to tell you if your intruder was human or a stray dog.

- Floral wire . Black is the default color, but if you have a green or white color that can match the terrain or time of year (snow), that’s a good idea.
- A .22-gauge firing capsule. You can buy these online. They’re hard to find in stores.
- Blank .22-gauge loads. Buy these online where you bought your firing capsule or at a hardware store in the nail bun aisle.
- Wrap the one end of the wire around a tree trunk, branch, sapling or stake. Choose a color that matches best with the surroundings.
- Attach an unloaded .22-gauge capsule in an obscure spot.
- Attach the other end of the wire to the .22-gauge firing capsule.
- Stretch it to another tree trunk, branch, sapling or stake and pull until you have tension on the .22-gauge firing mechanism.
- Test the unloaded .22-gauge capsule by pushing on the trip wire to see if the pin fires. If not, adjust the tension. If the pin fires, rearm the firing mechanism and carefully add a blank .22-gauge cartridge.
- If appropriate to the situation, do a test. It will be loud and attract a lot of attention. If the firing pin is firing when unloaded, you should be good to go if a test causes local problems or concerns. Anything that sounds like a gun shot in the neighborhood may attract some unwanted attention.

This setup uses a white length of electrical wire attached with overlapping loops through two holes in the top of a can painted white. Obviously, it’s a winter trip wire and it uses marbles or pebbles to create the alarm. The overlap of the wires causes the can to shake and rattle more than a conventional wire or line passing through the holes.
- White electrical wire
- A can or cans painted white
- Marbles or pebbles
Directions:
- Attach one end of the wire to a tree branch.
- Run the wire through the can in a discreet location, but overlap the wires so the can shakes when the wire is tripped.

- Attach the other end of the wire to a branch and test.
If trouble is close to home and you need to come up with a trip wire fast, this is one option. This is a trip wire connected to a gate, causing an avalanche of large rocks to fall onto a large piece of sheet metal or even a metal garbage can. It makes a lot of noise and can also be staged so the rocks fall onto the metal when the gate is pushed rather than pulled open.
You can improvise this kind of setup anywhere someone may enter uninvited, from a barn door to a back door to a door on a wood shed. This is not a stealthy trip wire. It assumes that a gate or other barrier is obstructing any view of the setup.
- Bucket to hold the ro cks.
- About two dozen large rocks from 1 to 2-inches in diameter.
- A large metal surface or object that will make a lot of noise when rocks land on it. Sheet metal, metal garbage cans, metal ductwork, any type of metal that’s relatively thin and will create noise.
- A wood platform 12” square to support the bucket
- Three wooden dowels about 3 feet long. (You can use old broom handles or even 1×2’s can work).
- Cordage . Any type and any color. The trip wire will also be obscured by the gate or barrier.
- Fill your bucket with your rocks and dump them on your metal sheet, can or whatever else your using to assess the noise. Ask someone inside your home or camp to determine if they can hear it.
- If you’re satisfied with the noise level, fill the bucket with your rocks.
- Pound the 3 support sticks into the ground in a triangle that will support the 12” square platform.
- Set the 12” platform on top of the support sticks. You don’t want to drive the support sticks too deep into the ground. You want this to be a precarious balancing act.
- You have two options. If your gate pulls open towards you, attach your trip wire to the gate and to the front support stick or your three sticks setup far enough away to allow the rocks to fall on the metal. Place the metal in the best location for the rocks to fall. You might want to put some rocks under the metal to lift it off the ground to increase the noise and hold it in place to some degree. When the gate is opened, the trip wire will pull out the support and the bucket will fall forward onto the metal.
- If your gate opens away from you, set up the support sticks and the platform right next to the gate. When someone pushes the gate open, it will topple the bucket with the rocks onto your metal plate or can.
- Test either option to see where the rocks fall and place your metal sheet or container in that location.
- Test again and ask someone inside the house to assess the noise level.
- If satisfied, set the trip or add more rocks or adjust the metal location or type of metal. It’s an easy set up and will create enough noise to cause most intruders to jump out of their boots.
Are There Other Approaches?
No doubt . Trip wires have been around a long time, and what you choose to improvise is only limited by your imagination and materials on hand . What we tried to do here was explore the concept so anyone could take the basic idea and adapt it to their needs, available supplies , and their location. It’s all a question of finding stuff that will make a lot of noise when someone trips over your wire.
In an emergency, it’s good to know how to do this stuff. In an ideal scenario, you would have sophisticated electronic devices that are solar powered and connected to motion detectors and all manner of alerts and alarms. Complicating things further is that any device with any level of electronics will also need to be weatherproof.
But this isn’t about an ideal scenario with a house surrounded by lasers . It’s about a sudden and surprising time when things rapidly become dangerous or threatening. Anyone in that situation would have plenty to think about and the ability to quickly improvise something as basic as perimeter alarms with trip wires not only makes sense but simply seems like a good idea. Just don’t throw way any old bells.
Like this post? Don't Forget to Pin It On Pinterest!
You May Also Like:
- 11 Home Security Tips for Life After SHTF
- How to Build a Bicycle Generator
- 20 Survival Uses for Wire Coat Hangers
- 5 Ways to Minimize Generator Noise
- 3 Things To Know BEFORE You Go Camping

© Copyright 2010-2022 Urban Survival Site · All Rights Reserved
Contact Us · Disclosure · Privacy · Terms of Use · Direct Ad Sales · Site Map
Facebook · Pinterest · Twitter
* Urban Survival Site is a participant in the Amazon Services LLC Associates Program, an affiliate advertising program designed to provide a means for us to earn fees by linking to Amazon.com and affiliated sites.
Enter your email address below to get your One Year Urban Survival Plan... it's 100% FREE!
Plus daily survival tips (unsubscribe anytime)
Buy Print Magazine
The Truth About Tripwires: Why Small Force Deployments Do Not Deter Aggression
Dan Reiter , Paul Poast PDF Download -->
A pillar of American grand strategy since 1945 has been the deployment of forces — sometimes smaller and sometimes larger — abroad. A key logic underpinning smaller deployments is that they serve as tripwires: Attacking them is assumed to inevitably trigger broader intervention, deterring aggression. We question this logic. Not only are small tripwire deployments unlikely to prevent an attacker from capturing its objective and establishing a strong defensive position, tripwire-force fatalities may be insufficient to provoke broader intervention. To deter, forward deployments must be sufficiently substantial to shift the local balance of power. Our claim is examined in three 20th-century deterrence attempts: the successful 1949 American attempt to deter a North Korean attack on South Korea; the unsuccessful 1950 American attempt to deter a North Korean attack on South Korea; and the unsuccessful 1914 British attempt to deter a German attack on Belgium.
Basing U.S. troops close to the front lines of an area where war is likely to break out has been a cornerstone of American grand strategy since World War II. 1 From the demilitarized zone between North and South Korea to the plains of West Germany during the Cold War, U.S. troops have been placed directly in the path of expected assaults. The goal of forward-deploying these troops is simple: to deter aggression. Mere verbal promises to protect an ally can be dismissed as “cheap talk.” 2 Making an effective threat to protect an ally requires non-verbal measures. After all, actions speak louder than words.
The United States has sometimes sought to achieve deterrence on the cheap through the deployment of smaller “tripwire” forces. While tripwire forces are too small to shift significantly the local balance of power, the idea is that such small deployments can still boost deterrence by increasing the likelihood of American intervention. According to this approach, the deaths of these troops in the early stages of fighting would compel a larger military response because, if America’s leaders were to do nothing in response to those deaths, they would be punished at home and the country would suffer damage to its international reputation. Thus, tripwire-force deployments boost deterrence by increasing credibility.
However, we argue that the deterrence benefits of tripwire-force deployments are exaggerated. These forces will not boost deterrence for two related reasons. First, tripwire deployments do not, in reality, significantly increase the credibility of the deterrent threat. The deaths of troops in combat will not necessarily create a strong public motive to intervene in order to seek revenge or protect a country’s reputation, even given the prospects of broader casualties. Second, even if the deaths of such troops could create these motives to intervene, potential attackers could strike anyway in order to achieve a fait accompli and create a strong defensive position.
In contrast to tripwire forces, the deployment of a larger contingent of troops can actually boost deterrence success. If forward-deployed forces are sufficient to shift the local balance of power, potential attackers will be less confident that they can succeed and less confident that they can achieve a fait accompli before reinforcements arrive. As a result, potential attackers will be less likely to actually launch an attack.
After presenting these general arguments below, we apply them to three empirical cases. We demonstrate that North Korea elected not to attack South Korea in 1949 because of the substantial deployment of U.S. troops to South Korean territory. On the other hand, the deployment of a small American tripwire force to South Korean territory in 1950 failed to deter a North Korean attack. Finally, we argue that, had Britain deployed a sufficient body of troops to Belgium before the July 1914 crisis, Germany would have been deterred from attacking Belgium and escalating the Austrian-Serbian crisis, permitting World War I to be avoided.
Understanding the logic and effectiveness of both tripwire and more substantial deployments is highly relevant to contemporary foreign policy debates. For example, during his presidency, Donald Trump consistently complained about the costs of deploying U.S. troops to allied territories and threatened to reduce American troop deployments abroad. 3 Or, consider NATO’s Baltics intervention plan, discussed below, which some consider to be essentially a tripwire plan. In 2018, the United States deployed a small number of marines to Taiwan ostensibly to protect diplomatic personnel there. But observers noted that these troops could serve only as a tripwire in the event of a Chinese invasion. 4 Strong faith that the deployment of a small tripwire force significantly bolsters deterrence could push President Joe Biden, who is eager to cut defense spending to both address domestic needs and decrease the deficit, to reduce U.S. troop deployments abroad, especially in South Korea, under the assumption that a smaller force would be sufficient to trigger America’s involvement in a conflict there and deter aggression. 5
The U.S. government should stop assuming that undersized tripwire-force deployments have outsized deterrence effects. If a state is going to commit troops to deter aggression, it should do so with the understanding that the troops being deployed ought to be able to shift the local balance of power on their own. When it comes to forward troop deployments, more is better.
Tripwires and the Hope of Deterrence
In order to prevent attacks on other states, some states make deterrent threats against potential attackers. A core tenet of deterrence theory is that such threats are more likely to succeed if the potential attacker believes the defender has credibility — the willingness to execute the threat — and the capability — the ability to carry it out. 6 Throughout the development of deterrence theory, scholars and policymakers have paid considerable attention to the credibility part of the deterrence formula, but less attention to the capability element.
Within the U.S. alliance network, tripwire forces have been seen as necessary for boosting deterrence, because alliance agreements alone are not viewed as sufficient to deter an attack. One reason is that alliance treaties frequently contain loopholes and conditions that enable states to find a legal justification not to intervene if an ally is at war, or to offer only very limited assistance. 7 Indeed, the United States deliberately included a number of loopholes in its post-1945 treaties, such as the North Atlantic Treaty, including restricting the geographic purview of some treaties, giving signatories the ability to decide what level of intervention would be appropriate, and requiring intervention only if Congress formally declared war, among others. Politicians might be able talk their way out of the obligations of an alliance treaty, as France did when it abandoned Czechoslovakia in 1938, but, it was argued, abandoning Americans who had been killed in battle by hostile forces would be much more difficult.
Within the U.S. alliance network, tripwire forces have been seen as necessary for boosting deterrence, because alliance agreements alone are not viewed as sufficient to deter an attack.
Credibility was the central question of Thomas Schelling’s famous 1966 book, Arms and Influence . How could defenders like the United States credibly signal their willingness to go to war on behalf of their allies? Schelling suggested deploying tripwire forces to the territory of the potential target. A tripwire force is defined as a body of troops that is not large enough to shift the local balance of forces in order to stop or significantly slow down an attack. Schelling’s main claim is that the presence of such a force makes a threat to intervene more credible, because the early and unavoidable deaths of friendly troops in combat would force defender intervention. As Schelling famously wrote of the American tripwire force sent to Berlin,
The garrison in Berlin is as fine a collection of soldiers as has ever been assembled, but excruciatingly small. What can 7,000 American troops do, or 12,000 Allied troops? Bluntly, they can die. They can die heroically, dramatically, and in a manner that guarantees that the action cannot stop there. They represent the pride, the honor, and the reputation of the United States government and its armed forces; and they can apparently hold the entire Red Army at bay. Precisely because there is no graceful way out if we wished our troops to yield ground, and because West Berlin is too small an area in which to ignore small encroachments, West Berlin and its military forces constitute one of the most impregnable military outposts of modern times. The Soviets have not dared to cross that frontier. 8
In making this claim, Schelling conflated pride, honor, and prestige to explain why setting off a tripwire would trigger an American response. 9 America’s reputation would be damaged if it did not intervene following the deaths of these forces, because it would signal a willingness to allow an enemy to overrun its allies — and even its own troops. Schelling also alludes to the possibility of a response driven by emotion — that the deaths of U.S. troops would trigger a public demand for revenge and an insistence on the deployment of American troops.
Subsequent scholarly work fleshed out, both theoretically and empirically, the credibility element posited by Schelling. Some scholars explored the possibility of making a credible nuclear deterrent threat, i.e., whether the promise of nuclear retaliation for an attack on an ally would be perceived as credible. 10 A critical component of this debate was whether long-range nuclear delivery was adequate for creating a credible deterrent threat, or if it was instead necessary for the United States to deploy tactical nuclear weapons in Europe. 11 The deployment of such weapons would both serve as a classic tripwire, in that their destruction would compel an escalatory response and create a “use-it-or-lose-it” logic — their quick destruction would mean that the weapons would be kept on a hair trigger. Some scholars maintained that a general nuclear deterrent still required conventional tripwire forces. As Glenn Snyder observed in 1961,
the point of having a trip-wire is not to show that an attack has taken place — which of course would be evident as soon as the Soviet forces crossed the border — but to implicate extra-Continental nuclear powers by means of something stronger than a treaty contract. 12
Others used game theoretic and experimental work to explore whether a threat’s credibility could be enhanced by building “audience costs,” whereby a leader is punished by an audience, typically domestic, that is displeased with the leader’s failure to fulfill a stated foreign policy promise or threat. 13 Relatedly, scholars developed the concepts of “tied hands” and “sunk costs.” 14 A government ties its own hands by raising the costs of failing to follow through on a threat. For example, it might create domestic “audience costs,” such as incurring domestic political consequences (i.e., being voted out of office) for failing to abide by a deterrent commitment. A government sinks costs by taking costly actions to demonstrate how seriously it takes the threat it is making — such as taking pricey mobilizing or arming measures. 15
Still other research has connected the desire for revenge with a willingness to support the use of force. Indeed, one survey found that, in a hypothetical scenario, a desire for revenge was a key reason that subjects were willing to support a nuclear attack against Iranian civilians following a deadly Iranian attack on U.S. forces. 16 Robert Harkavy points out that the desire for revenge goes beyond a need for “tit-for-tat” retaliation, as the latter is “devoid of much deep emotion.” 17 Instead, there is a need for retribution by righting a wrong. Harkavy was considering the perceptions of societies that had been defeated during major war, but the logic of revenge has been found to apply in other contexts, including when a country has not been directly attacked. 18
Flaws in Tripwire Logic
While the tripwire logic has been around for a long time and has compelling theoretical attributes, it has two interrelated flaws. First, potential attackers might not see the motives to avenge a tripwire force as increasing the motive to intervene. Second, the temptation of a fait accompli might encourage aggression even if reputation and revenge create motives for a defender to intervene.
Regarding the first critique, it is incorrect to assume that all individuals (in or out of government) place a high value on reputation, honor, and revenge, especially in relation to other priorities and values. 19 Indeed, a large segment of the population might have a distaste for the use of force and, hence, would punish a leader for even making a threat (but also reward that leader for backing away from the threat). 20 Critics of the audience-cost proposition have observed that publics and governments may be willing to accept the reputational costs of failing to execute a deterrence threat if failing to execute undermines other important values, such as a desire to avoid entering difficult to win, costly wars over dubious stakes. 21 Publics may put a higher value on consistency in policy, especially if consistency means staying out of conflict. 22 Emphasis on reputation and revenge is not strong across all populations. Studies have found that the willingness to demand revenge and defend the national reputation and honor varies interpersonally and across subnational cultures. 23
Further, leaders have the ability to shape the degree to which publics perceive harm to national honor for backing down from a threat. According to some surveys, presidential rhetoric can significantly reduce the audience costs that would otherwise be imposed for backing down. 24 This is also the case for revenge. In her careful study of the connection between revenge and support for war, Rachel Stein notes that
it is not the case that a highly vengeful public will seize upon the slightest provocation to demand war from a reluctant leader. Rather, broad public endorsement of revenge is a latent source of support for war that leaders can activate by deploying strategically crafted rhetoric. 25
Thus, motivated leaders can avoid war even after tripwire troops have been killed.
A leader’s rhetoric aside, the human and financial costs of intervention counterbalances the public desire to intervene for the sake of reputation or revenge. Desiring revenge, or to salvage one’s reputation, does not cause individuals to ignore the costs of war. There is an extensive body of scholarship on the sensitivity of democratic publics toward casualties, and specifically how this sensitivity affects the public willingness to support the use of force. Research on protracted wars has demonstrated persuasively that support for war declines as casualties mount. 26
There is less work on how casualties affect the willingness of the American public to support intervening with force. Anecdotally, there are episodes of casualties failing to inspire demands for broader intervention. Casualties suffered by American peacekeeping troops in Beirut in 1983 and Mogadishu in 1993, for example, did not spark a public demand for broader intervention, and indeed, in both cases, American forces were eventually withdrawn without triggering a public backlash. 27 Similarly, although several American vessels were attacked by German submarines in the Atlantic Ocean in 1941 before America’s entry into World War II, none of those attacks were sufficient to motivate the country’s entry into the war or retaliation against Germany. As late as October 1941, two American destroyers were attacked, killing 126 Americans, and still there was no public outrage and President Franklin Roosevelt did not order any retaliatory action. Meanwhile, naval recruitment dropped 15 percent, suggesting that concern over becoming a casualty at sea in clashes with German submarines exceeded demands for revenge. 28
A leader’s rhetoric aside, the human and financial costs of intervention counterbalances the public desire to intervene for the sake of reputation or revenge.
A few surveys have looked for tripwire effects by asking participants whether they would be more likely to support intervention if friendly forces suffered serious casualties. The results have been mixed. Some surveys have explored this question in the context of audience-cost theory, asking participants whether, if a leader were to make a threat and then back down, that leader would earn higher levels of disapproval if friendly forces had been killed. Michael Tomz’s research presented participants with scenarios in which a country attacked a neighbor and the U.S. president threatened to push out the invaders but then did not take that action. He found that subject disapproval of the president was higher when they were told that 20 Americans had been killed in the initial fighting. 29 Similarly, Graeme Davies and Robert Johns found that, when British subjects read about a scenario in which a terrorist group captured British soldiers and the prime minister threatened to take action but did not, their disapproval was higher when they were told of the deaths of four British combat pilots. 30 Only one survey experiment has more directly explored for tripwire effects in public opinion by asking respondents to consider scenarios where troops were forward deployed. In their series of surveys on an array of different conflict scenarios, Paul Musgrave and Steven Ward found tripwire effects to be contextually restricted, substantively limited, or non-existent. 31
What about international audience costs? Might the prospect of damaging their countries’ international reputation push governments to rescue embattled friendly troops? Some of the reasons why the prospect of domestic audience costs fails to deter are also reasons why the prospects of international audience costs fail to deter. If aggressors believe that a defender’s public is highly sensitive to casualties and wishes to avoid them, then the aggressor may come to believe that the defender will not approve broader intervention even at the risk of damaging its international reputation. 32 Aggressors may also see hesitant defender governments as motivated to use treaty loopholes and framing to reduce the international audience costs of deciding against broader intervention.
The Fait Accompli
Regarding the second critique, even if aggressors sometimes recognize that killing an ally’s troops will motivate that ally to intervene to protect its reputation or enact revenge, the prospect of a fait accompli may tempt them to attack anyway. 33 A fait accompli is the rapid conquest of territory and defeat of tripwire forces before reinforcements can arrive. Current scholarship proposes that attackers are tempted to launch a fait accompli out of a belief that a defender will accept the aggression, i.e., that the defender will accept a small loss of territory rather than invoke a broader war. 34 In some sense, a fait accompli becomes what Schelling called a “salami tactic” if it enables the attacker to gain some territory without inducing a response by the defender. 35 We propose an additional motivation: An aggressor might be tempted to launch a fait accompli if it believes that achieving the fait accompli will strengthen its defensive position, thereby further discouraging outside intervention by shifting the balance of power. A successful fait accompli might improve the attacker’s defensive position by providing geographic advantages were it to, say, capture an island or a mountain range. This would permit the attacker to construct stronger defensive positions or use the economic resources of the captured territory to boost its military power. 36 Strengthening the defensive position through any of these means raises the defender’s perceived cost of intervening, thereby dissuading it from taking action. Because democracies are very unwilling to intervene in wars with low chances of victory, 37 they might become discouraged and accept the conquest, albeit begrudgingly, if faced with the prospect of a long, difficult road to victory. Certainly, autocratic aggressors, such as Japan in 1941 and Argentina in 1982, hoped that their faits accomplis would discourage broader intervention from democratic defenders. Of course, the ability of a fait accompli to shift the military balance varies. The Soviet capture of West Berlin, for example, might not have provided communist forces either local geographical advantages or yielded economic resources that could have been converted to communist military power.
In short, there are good reasons to doubt that tripwire forces significantly boost deterrence. That said, believers in a tripwire effect inevitably point to the most well-known, apparently successful example of tripwire deterrence: the deployment of American and other NATO troops to West Berlin during the Cold War. During the Cold War, Western powers deployed as many as 12,000 troops in the city. This was not nearly enough to defend a city of 900,000, and yet peace obtained. Schelling and others inferred that, because the deaths of those troops in combat would have invoked immediate American intervention, the Soviets decided not to attack.
In the decades since Schelling wrote Arms and Influence , archives have been opened that cast doubt on his interpretation. They indicated that Stalin did not intend to invade West Berlin in 1948, nor did Khrushchev in the 1950s or early 1960s, meaning that tripwire forces did not deter an attack because there was no planned attack to deter. 38 Internal discussions within the East German and Soviet governments revolved around sustaining the East German economy and state, stemming the flow of migrants to the West, persuading the West to recognize East Germany, and the possibility of closing access to West Berlin. An actual invasion, including a fait accompli effort against West Berlin, was not discussed, even as a contingency. Further, his public threats and blusterous rhetoric notwithstanding, Khrushchev preferred to avoid actual confrontation with the West over Berlin. In June 1959, Khrushchev remarked privately, “[We] don’t think it’s worth it now to push the west to the wall, so that we will not give the impression that we are seeking the recognition of the GDR [German Democratic Republic]. The Americans don’t want to recognize the GDR.” 39
By 1961, as the refugee flow created an accelerating internal crisis for the East German government, there was not even passing mention of invading West Berlin as a solution. Rather, the more belligerent option — which was eventually chosen — was to close the border between East and West Germany. Internal Warsaw Pact discussions of military matters in the summer of 1961 surrounding this decision focused on what the Western reaction would be. The debate was over whether communist forces could deter NATO, not over whether they would invade West Berlin in light of American tripwire forces. 40
Flawed assumptions about tripwire deterrence underlie current NATO defense planning. Consider NATO’s strategy toward the Baltic states. 41 It presently deploys a battalion in each of the three Baltic states, each of which is “backstopped” by additional forces from Germany, the Czech Republic, and Norway, along with a brigade-sized U.S. force, which is stationed in Poland. 42 Some view these forces not as directed toward stopping a Russian invasion of a Baltic NATO member, but instead as a tripwire to provoke American involvement. 43 Michael O’Hanlon and Christopher Skaluba recently pointed out that these forces, dubbed NATO’s “enhanced forward deployment,” have not been “a truly integrated combat force; nor has [NATO] deployed many helicopters and air defense systems.” 44 An Atlantic Council report described NATO’s current strategy as relying on a “tripwire” and “rapid reinforcement,” warning that this approach does not adequately address Russia’s “time, space, and mass advantages,” affording Russia the ability to achieve a successful fait accompli . 45 In other words, NATO’s forward-deployed forces are simply not adequate in size, appropriately placed, or properly equipped to counter a Russian invasion. A 2016 RAND Corporation war game found that Russian forces could reach the outskirts of Riga and Tallinn in approximately 60 hours. 46 Given the rapidity of the NATO force’s defeat in the war game, the ability of Russian forces to achieve a fait accompli would leave NATO decision-makers with few feasible options. Would they be willing to initiate an all-out ground war, with the possibility of nuclear escalation? One must therefore seriously question the ability of these forces to “trip the alarm” for a sizeable counter-strike by NATO and the United States.
Deployments Beyond Tripwires
Tripwire-force deployments are insufficient to bolster deterrence because deterrence is about more than signaling. One must instead deploy a force that is sufficiently capable — one that can itself fulfill a deterrent threat. Troop deployments must be able to shift the local balance of power so as to alter the potential attacker’s likelihood of succeeding, or its likelihood of succeeding quickly and/or at a low cost. 47
There are three related ways in which forward-deployed troops can help fulfill a deterrent threat. First, they can give local forces a better chance of defeating the attacker’s forces through some combination of increasing troop quantity, improving military technology, and crafting an appropriate military strategy. 48 Even if the deployed forces were relatively small in number (but still larger than a simple tripwire force), they could be equipped with force-multiplying weaponry, such as advanced armor. 49 Foreign-deployed troops can also shift the local balance of power if equipped with the optimal military strategy. This was John Mearsheimer’s central policy conclusion in his classic 1983 book, Conventional Deterrence : that pre-deployed American troops armed with the right military strategy, and perhaps the right technology, could deter the Soviets from invading West Germany. 50 One element of military strategy is integrating with coalition partners. Alliance structures that plan for the effective, combined use of allied forces can serve as an especially powerful deterrent. 51 A sufficiently sized troop deployment could also defeat aggression from non-state actors. 52 Certainly, the number of deployed troops needed to shift the balance of power varies by context. Under some circumstances, a smaller contingent of troops could be adequate if troops in the region could be rapidly deployed before an aggressor could achieve a fait accompli . Offshore naval power could also play a role, permitting a smaller deployed force to accomplish its deterrence mission.
Tripwire-force deployments are insufficient to bolster deterrence because deterrence is about more than signaling. One must instead deploy a force that is sufficiently capable — one that can itself fulfill a deterrent threat.
Second, even if deployed troops cannot fully blunt an attack, they can slow the attacking forces down. The prospect of a slowed advance can boost deterrence because attackers often seek rapid victory. Slowing an advance can buy time for the defender to deploy larger numbers of troops to the allied territory before it is conquered. If an attacker can be convinced that quick victory is unlikely, deterrence is more likely to hold. 53 Deployed troops that are focused on buying time can play a key role in enhancing the fighting capacity of the allies if they are substantial enough to allow the allies to execute a war plan, including permitting the timely mobilization of reinforcements to aid embattled, pre-deployed forces. A small tripwire force is also unlikely to buy much time, something that is not commonly the purpose of such a deployment. Again, the purpose of a tripwire force is to, in the words of Schelling, “die heroically,” not hold the line until help arrives.
Third, deployed troops can preserve peace by making attempts at faits accomplis less attractive. As discussed, the lure of a fait accompli is that if an attacker can rapidly conquer a territorial objective without engaging in military combat, it may be able to establish a strong defensive position, which would dissuade a counterattack or broader intervention. A substantial forward troop deployment can undermine a fait accompli strategy by reducing the likelihood that the attacker will capture the desired territory and strengthen its defensive position before a response can occur.
In summary, substantial deployments that shift the local balance of power are significantly more likely to deter aggression than tripwire forces are. Some might propose that more substantial troop deployments could boost credibility as well as capability, because such deployments might constitute a sunk cost signal of the defender’s willingness to intervene. It is possible that larger troop deployments convey such a sunk cost signal, though we do not yet have historical, quantitative, or survey research to demonstrate such an effect. Regardless, a key, underappreciated cause of deterrence failure is not an aggressor’s assessment of credibility, but rather its assessment of capability. As we demonstrate in our case studies below, aggressors attempt faits accomplis because they believe they can overwhelm defending forces and capture their territorial objective rapidly, emphasizing the importance capability plays in helping deterrence work.
That said, there are three limits to our argument that large contingents of deployed troops bolster deterrence through improving the capability of the allied state. First, an attacker that is less focused on winning quickly might not be deterred by an increased likelihood of delay. Non-democracies, for example, might be less motivated to win quickly as compared with democracies, because non-democratic leaders are less fearful of the domestic political consequences of a lengthy war. 54 North Vietnam was not deterred by the presence of U.S. troops in South Vietnam, in part, because it was willing to wage a long and costly war. 55 It is also conceivable that the defender might not have the motivation or ability to make use of a delay to provide more support to the ally. In short, the importance of delay may vary by context.
Second, deployed troops only help if they shift the attacker’s calculus of victory. That is, the mere presence of such troops is not sufficient. The troops need to be the right size, have the appropriate armament, be deployed to the right location, and have the right strategy to change the attacker’s calculations. 56 Consider the German attack on the West in 1940, and Belgium in particular. British troops were not deployed to Belgium in peacetime. If they had been, they likely would not have been sent to the area where Germany actually attacked — the Ardennes — because Allied intelligence did not expect the main German attack to take place there, and hence British peacetime deployments might not have deterred a German attack. 57
Third, if the ally is sufficiently well armed, then the peacetime deployment of the defender’s troops would not be necessary to strengthen an already robust deterrent. For example, Taiwan currently has sufficient conventional forces to repel a Chinese amphibious invasion, meaning that American force deployments there would likely add little to an already strong capability. 58 Similarly, the Israeli Defense Forces are currently sufficiently strong to defeat any conventional ground attack from neighboring countries, making the peacetime deployment of American troops there unnecessary from a capabilities perspective. One policy implication of this is that a defender may be able to maintain a robust deterrent for an ally, not by deploying forces, but by offering substantial material aid to the ally, as the United States does for Taiwan and Israel.
History Rewritten? Three Critical Cases of Forward Troop Deployments
We test our theory that tripwire troop deployments will not significantly bolster deterrence, but that more substantial troop deployments will, by examining how troop deployments affected three attempts at deterrence in the 20th century: America’s attempt in 1949 to deter a North Korean attack on South Korea; America’s attempt in 1950 to deter a North Korean attack on South Korea; and Britain’s actions (and largely inactions) to deter a German attack on Belgium in 1914. First, North Korea did not attack South Korea in 1949, in part, because an adequately sized American troop deployment to South Korea shifted the local balance of power. Second, North Korea did attack South Korea in 1950, in part, because American troop deployments to South Korea had been reduced to a tripwire force that was insufficient to shift the local balance of power. Third, British troop deployments to Belgium in 1914 could have deterred a German attack if they had been sufficient to shift the local balance of power. However, a small tripwire force that did not shift the local balance of power would likely not have been sufficient to deter Germany. We chose these cases because they offer variation in the number of troops the defending power deployed (i.e., our independent variable), there are primary documents that provide insight into key decisions made in these cases, and the cases themselves are highly significant in world history and U.S. foreign policy.
Korea, 1949 & 1950
After World War II, the former Japanese colony of Korea was divided into two independent countries: communist North Korea and non-communist South Korea. The leaders of both countries, Kim Il Sung of North Korea and Syngman Rhee of South Korea, envisioned invading the other Korea and unifying the peninsula under a single government. Kim knew he required Soviet assistance and support to carry out a successful campaign. South Korea became a member of the United Nations in December 1948, placing it under the purview of the U.N. Charter’s Chapter 1 commitment to remove threats and suppress acts of aggression.
In March 1949, Kim first contacted Soviet leader Joseph Stalin about possible Soviet support for an invasion. Stalin “did not object in principle” to Kim’s plan to attack South Korea. 59 However, Stalin declined to approve and support such an attack. 60 He reached this decision after an extended discussion with Kim about the local balance of power on the Korean Peninsula. The presence of the American forces stationed in South Korea — first deployed there in September 1945 — was of great importance to Stalin. When Kim asked permission to invade the South, Stalin’s first question was to ask how many American troops were stationed there. Kim informed Stalin that as many as 20,000 American forces were there, a very sizable contingent given that the entire South Korean army at that point numbered only 60,000, in Kim’s estimation. 61 Stalin expressed concern with the local balance of forces and identified the American troop deployments in the South as one of the key reasons why he was declining to support a North Korean attack, recognizing that American troops would “interfere in case of hostilities.” 62 In 1949, then, deterrence held on the Korean Peninsula.
Although Stalin declined to support a North Korean attack on the South in March 1949, Moscow continued to monitor the American troop presence in South Korea. In a secret May 1949 report to Moscow, Soviet intelligence reported that the American and South Korean governments were in the process of negotiating reductions in the American troop presence. 63 In September 1949, Moscow asked Pyongyang directly if there were still American troops in South Korea, and how much assistance those troops could offer in the event of a North Korean invasion. North Korea estimated there were between 500 and 2,400 U.S. troops left in South Korea and that, in the event of war, “American instructors will take immediate part in organizing military actions.” 64 Internally, American leaders recognized that this reduction in troops would change the U.S. troop presence in South Korea to a “trip-wire.” 65
In early 1950, Kim again pressed Stalin to support an invasion. He understood that Stalin demanded rapid victory. In a visit to Moscow in early January, Kim stressed that his army could capture the South Korean capital of Seoul, located near the border, in a matter of days. 66 Stalin began to relax his opposition in late January, though he maintained that an invasion must be planned such that “there would not be too great a risk.” 67 Stalin saw political advantages to a Korean war: It would help Moscow maintain control of the communist world and prevent China from becoming a challenger for communist leadership.
Kim returned to Moscow in April, and, over the course of this visit, Stalin gave his approval for an invasion. Kim reiterated that the campaign would be over within days and Stalin was persuaded. 68 He understood that now a North Korean fait accompli was possible, offering victory before America could send substantial reinforcements. As Stalin declared to Kim that month, “The war should be quick and speedy. Southerners and Americans should not have time to come to their senses. They won’t have time to put up a strong resistance and to mobilize international support.” 69 Note Stalin’s mention of “strong” resistance, recognizing that North Korea would confront the weak American tripwire forces — a few hundred troops — that were then deployed to South Korea.
Stalin expressed concern with the local balance of forces and identified the American troop deployments in the South as one of the key reasons why he was declining to support a North Korean attack, recognizing that American troops would “interfere in case of hostilities.”
Kim sought to reassure Stalin that his plan for a fait accompli would avoid the risk of broader American intervention. Kim said that, once the attack had begun, there would be a mass uprising within South Korea against the Rhee government in support of the communist liberation: “Americans won’t have time to prepare and by the time they come to their senses, all the Korean people will be enthusiastically supporting the new government.” 70 That is, the fait accompli would help shift the local balance of power against the United States because, after a North Korean victory, the South Korean population would rally to accept and support communist rule.
After Stalin approved the attack in April 1950, he remained focused on the urgency of North Korea achieving a rapid fait accompli . The June 15, 1950 operational plan called for an initial attack on the Ongjin Peninsula on the west coast of South Korea, just over the 38th parallel border. 71 This would be followed by the capture of the capital of Seoul, also near the border, and the destruction of the South Korean military. Last, other major cities would be captured and the entirety of the country would be liberated. Stalin continued to stress the need for utmost secrecy, perhaps fearing that, if America sensed an impending invasion, it might send more troops to South Korea. Initial reports of U.S. casualties after the June 25 invasion, specifically of American bombers being shot down, did not disrupt Stalin’s plan of pressing for rapid victory to avoid broader American involvement. Upon hearing these reports, Stalin directed the Soviet ambassador to North Korea to convey to Kim that “the sooner South Korea is liberated the less chance there is for [American] intervention.” 72
In summary, it appears Stalin became willing to approve the North Korean invasion of South Korea when he was confident the North could achieve a fait accompli . The substantial reduction of U.S. forces in South Korea, from a consequential detachment to a tripwire force, helped provide this confidence. The evidence does not indicate that the reduction in U.S. forces in South Korea was necessary and sufficient to cause a North Korean invasion, but it does indicate that the communists desired a rapid fait accompli victory; that they realized that the size of the U.S. troop deployments to South Korea affected the likelihood of that victory; and that, as of fall 1949, those troops had been reduced.
One alternative perspective is that the key factor pushing Stalin to greenlight the invasion was not the shifting local balance of power caused by a reduction in U.S. troops, but rather Stalin’s conclusion by January 1950 that America was unwilling to intervene, i.e., that Stalin had doubts about America’s credibility, rather than America’s capability. This view posits that Stalin may have been especially encouraged by Secretary of State Dean Acheson’s January 1950 speech that appeared to place South Korea outside of the American defense perimeter, as Acheson declared that the perimeter “runs along the Aleutians to Japan and then goes to the Ryukyus.” 73
Two comments are in order. First, the effects of the 1950 Acheson speech on communist decision-making ought not be exaggerated. Other parts of the speech cast doubt on the idea that America would stand aside in the event of an invasion of South Korea, as Acheson specifically indicated that the United Nations would resist aggression anywhere in the Pacific region. Indeed, the media coverage of the speech implied that South Korea was inside the U.S. defense perimeter. 74 Importantly, as noted, in the first half of 1950, after Acheson’s speech, Stalin continued to express concern about the possibility of broader American intervention, emphasizing the need for secrecy and the importance of rapid victory in the South. This was not so much a dismissal of America as an irrelevant paper tiger but rather indicates the importance of accomplishing a rapid fait accompli before broader intervention could occur. As one team of historians summarized it, by May 1950,
Stalin would have concluded from press reports and intelligence that, though the Americans might want to aid … South Korea, it would take many months to mass and get that aid to the western Pacific. The timing was on Kim’s side if he moved quickly and decisively. 75
Second, new documentary evidence reveals that, in internal discussions, Soviet and Chinese officials did not take Acheson’s speech as a genuine statement of American disinterest in defending South Korea. Rather, they described Acheson’s speech as “slander,” an attempt to “deceive directly public opinion,” and a “smokescreen.” 76 Based on the recent revelation of this and other internal documents, historian Kim Donggil has concluded, “The argument that Acheson’s speech about South Korea resting outside the U.S. defensive perimeter was the deciding factor in Stalin’s decision does not accord with the facts.” 77 Another historian concurred, arguing that “recently released Soviet documents [demonstrate] that Acheson’s address had little if any impact on Communist deliberations.” 78
World War I
In 1914, the German war strategy depended on rapidly conquering Paris. Germany’s two major adversaries in 1914 were France and Russia, which were allied with each other. Germany recognized that war against one would mean war against both, and war against two major powers simultaneously would be a risky endeavor. Germany’s solution to this problem was the Schlieffen Plan, initially devised in 1905 by then-Chief of the German General Staff Marshal Alfred von Schlieffen. 79 Russia’s underdeveloped railroad network meant that the mobilization of its military would take weeks. If Germany could conquer France quickly, German forces could then rapidly redeploy to the east to confront the Russian colossus just as it was becoming ready for war. Moreover, the rapid German conquest of France and Belgium would dissuade Britain from entering a war against Germany. And control of the French coasts would facilitate the use of German submarines and air power against Britain. French and Belgian financial resources could be used to bolster German naval power, eventually permitting a successful German naval blockade of Britain, and thereby compelling Britain to accept German continental hegemony. 80 This is the military attraction of the fait accompli . Once achieved, it shifts the balance of power in the attacker’s favor, dissuading the defender from continuing the war.
Critically, the rapid conquest of France required the invasion of neutral Belgium, as the Franco-German frontier was relatively mountainous, making any attack there unattractive. 81 The importance of conquering Belgium and France rapidly cannot be overstated. Kaiser Wilhelm recognized this at least as early as 1905. 82 When Britain seemed, in early August 1914, to suggest it would remain neutral if Germany did not attack Belgium, Germany rejected the possibility because staying out of Belgium would fatally slow the pace of its offensive. Chief of the German General Staff Helmuth von Moltke commented on August 4,
An attack from German territory [directly to France] would have cost the German army 3 months and would have ensured Russia such a head start that we could no longer have reckoned on a success on both fronts. We had to go via Belgium with all our might on Paris for a quick reckoning with France. This was the only way to victory. 83
Britain did not pre-deploy any troops, not even tripwire forces, to Belgian territory in 1914. If it had pre-deployed troops in sufficient numbers to shift the local balance of power, a possibility made politically difficult by Belgium’s official neutrality, 84 Germany would have been deterred and World War I might well have been avoided. German forces would have had to face British forces from the outset of hostilities, as opposed to several days or weeks after the war’s outbreak. Schlieffen assumed that, absent the pre-deployment of troops, British forces would not be able to land soon after the outbreak of war:
If in a Franco-German war the English plan to land a force of 100,000 men or more in Antwerp, they can hardly do so in the first days of mobilization. No matter how well they prepare the assembly of their three army corps, their army organization and defence system present so many difficulties that their sudden appearance within the great Belgian fortress is almost inconceivable. 85
Moltke agreed. 86 Schlieffen was confident that British forces landing after the start of hostilities would not slow down the German push through Belgium into France. 87 Schlieffen also scoffed at the prospect of a blockade by the Royal Navy, confident that a short ground war would end the conflict. 88
Schlieffen recognized that the prewar deployment of British troops to Belgium would spoil the chances of a rapid conquest, imperiling the entire plan. He wrote in 1912,
A successful march through Belgium on both sides of the Meuse is therefore the prerequisite of a victory. It will succeed beyond doubt, if it is only the Belgian army which tries to obstruct it. But it will be very difficult if the English army, and perhaps even part of the French, is present. 89
Maj. Gen. Wilhelm von Hahnke commented in 1911, “Belgian neutrality must be broken by one side or the other. Whoever gets there first, occupies Brussels and imposes a war-levy of some thousand millions, has the upper hand.” 90 Moltke was of the same opinion: “The enterprise is only possible if the attack is made at once, before the areas between the forts are fortified.” 91 The German military and political leadership, including the Kaiser, Chancellor Theobald von Bethmann-Hollweg, Adm. Alfred von Tirpitz, and Moltke, all agreed with Schlieffen that the key questions were not only whether Britain would intervene, but also when British troops might arrive. 92
The focus on seizing Belgium quickly did not shift when Moltke succeeded Schlieffen in planning Germany’s military strategy. However, Moltke did alter another area of Germany’s strategy, which heightened the need for quick success. Moltke decided to respect Dutch neutrality, making it crucial to seize the Belgian fortress city of Liège at the very outset of the conflict, a task much more easily accomplished if a substantial peacetime garrison were not present. 93 In the words of one historian, “the quick seizure of Liège … was … regarded as an indispensable precondition for the successful execution of the great wheeling movement into northeastern France.” 94 The city of Liège was surrounded by a system of 12 forts, meaning the German advance would have to take these forts quickly to succeed.
The Belgian military was, by itself, unable to defend the Liège fortresses, both because of insufficient numbers (Belgian troops were dispersed throughout the country) and because Belgian troops themselves were inadequately trained and equipped. 95 The Belgian chief of staff in 1913 estimated that 60,000 troops would be needed to defend Liège, but, when German troops attacked in August 1914, there were only 25,000 Belgian defenders present. 96 The Germans contemptuously dismissed Belgian troops as “chocolate soldiers.” 97 Moltke declared, “We can count on the somewhat inefficient Belgian forces being quickly scattered.” 98 As war broke out and German forces advanced on Liège, the Belgian leadership hoped for the rapid arrival of Anglo-French forces to bolster its defenses there. 99 French forces were not sent, and British forces arrived too late to help. Defended only by Belgian troops, Liège fell to Germany on August 17, only two days later than the German war plan had envisioned. 100
British defense planners recognized that the Belgians by themselves might not be able to hold on to the Meuse forts, including at Liège, and that, if the forts fell to Germany, British troops could not arrive in time to help save Belgium.
Strikingly, British military planners agreed with Schlieffen. As early as 1906, they recognized that Germany would gain military advantage by going through Belgium to invade France and that the speed of substantial British troop deployments would be essential to thwarting German plans. The British regretted that the projected transport schedule of British troops would not allow for those troops to arrive in time. British officers understood that “Time is of the greatest importance.” 101 They understood that the Germans were focused on making “ every possible effort to press on and to try to beat us” in reaching Belgian territory. 102 Significantly reducing the time by which British troops could arrive in Belgium to confront the German invaders would provide “immense gain.” 103 British defense planners recognized that the Belgians by themselves might not be able to hold on to the Meuse forts, including at Liège, and that, if the forts fell to Germany, British troops could not arrive in time to help save Belgium. 104 A high-level 1911 British report reiterated that Germany might launch a surprise attack on Liège and that Belgian troops would be inadequate to defend it alone. 105 The British also recognized the low quality of the Belgian troops. 106 As late as May 1914, the British military noted that the critical Belgian fortresses, “if defended only by its peacetime [Belgian] garrison, would fall an easy prey to a German coup de main , executed at the outset of hostilities.” 107
One piece of evidence that substantial peacetime British troop deployments — meaning larger than a token tripwire force — could have shifted the local balance of power decisively enough to alter German plans in summer 1914 was discussion among German military planners of expected increases in Belgian forces. Belgium began to consider improving its military following the 1911 Agadir military standoff between French and German forces and, in 1913, passed a bill calling for the substantial expansion of the army, from 180,000 to 250,000 troops. While German military planners understood that an improvement in Belgian defenses would undermine the viability of the Schlieffen Plan, they reassured themselves that implementation would be slow. Indeed, though Russia’s growing power over time has traditionally been seen as an incentive for Germany to launch a preventive war, growth in Belgian power over time created similar incentives. This was not because Belgium threatened Germany, but because additional Belgian forces render impossible the quick advances the Schlieffen Plan required. 108 Germany’s focus on Belgian military power supports the claim that substantial British troop deployments would have eliminated Germany’s incentives to launch a preventive war in the West, because the local balance of power would have been immediately shifted against Germany, rather than more slowly through the process of Belgian military reforms.
In short, the weakness of Belgian forces, coupled with the absence of adequate British forces in the summer of 1914, fatally weakened prospects for deterring Germany from attacking Belgium. Even if British troop deployments had not been large enough to completely stop the German advance, as long as they were sufficient to slow down German troops this would have disrupted the tight schedule necessary for implementing the Schlieffen Plan. Germany’s decision to allow Austria to attack Serbia was predicated on the assumption that, if the conflict escalated, Britain would not disrupt the rapid conquest of Belgium. If Germany had not been confident in British military irrelevance, it would have restrained Austria, avoiding a broader war. 109
A counterargument to our claim is that a small British tripwire force, rather than a large contingent, could have deterred Germany, given that German war plans required Britain remaining neutral. If British troops deployed in Belgium were killed in the first days of the war, British intervention would have been inevitable, even if those troops had not been able to slow or stop the German march through Belgium. But we maintain, based on the views of the German military with regard to British neutrality, that deployment of a smaller tripwire British contingent insufficient to shift the local balance of power would not have deterred Germany.
To understand how German officials viewed British neutrality, one should focus on the views of German military leaders rather than German civilian leaders. 110 German military leaders were not concerned about Britain maintaining neutrality. The German military recognized that the operational necessity of invading Belgium made eventual British intervention inevitable. Moreover, the German military leaders would not have been deterred even if they fully believed that Britain was going to intervene, as long as that intervention was not immediate. 111 Indeed, in prewar planning discussions, German military leadership appeared unconcerned with Britain remaining neutral. They assumed that British ground forces would eventually arrive, but too late to prevent the German conquest of Belgium and France. 112 Historian Annika Mombauer put it starkly, “That Britain would not remain neutral was a mere hiccough for the [German] General Staff.” 113 Some German generals even welcomed British intervention, craving the opportunity to defeat British forces in battle, likely assuming that British intervention would be too little, too late to save Belgium or France. 114
Moltke’s invasion plan of Belgium actually presumed the eventual presence of British troops on Belgian soil. 115 More broadly, he assumed that British intervention in a European war would be inevitable “because England considers Germany stronger than France, is afraid of German hegemony and wants to preserve the balance in Europe.” 116 To this end, Moltke wanted to respect Dutch neutrality, in order to protect the German flank in anticipation of British intervention following a German invasion of Belgium. 117 On August 4, Moltke declared that seizing Belgium was sufficiently important that it must be done, even if this meant British intervention. 118 Moltke also argued that Germany ought to ignore any British commitment to stand aside if Germany respected Belgian neutrality, because such a commitment would not be credible given the threat to the European balance of power if Germany defeated France. 119
Thus, British troop deployments before July 1914 (or earlier) would have been unlikely to persuade the German military to avoid war if their only function was to increase the likelihood of British intervention. However, pre-deployed British forces might have persuaded the German military to avert war, by shifting the local balance of forces against Germany and slowing the German advance. In short, the peacetime dispatch to Belgium of a moderate British troop contingent might have prevented what became, at the time, the deadliest war in the history of humanity.
Implications for U.S. Foreign Policy
As a policy tool, forward troop deployments are misunderstood in two ways. First, small tripwire deployments do not necessarily have powerful credibility effects, as is often thought. That is because it is not certain that the prospect of a small number of American troop fatalities would automatically engender broader American military intervention. Second, the capability effects of larger troop deployments are underappreciated. If forward troop deployments can substantially shift the local balance of power, even if only by slowing down an attacker’s advance, they can complicate an attacker’s plans and reduce the likelihood of aggression.
The limited utility of tripwire troop deployments should push decision-makers to reject tripwire deployments and instead consider two other options. First, if decision-makers are unwilling to bear the costs of more substantial troop deployments in order to deter attacks on allies, then they should consider reducing foreign commitments to conserve resources. Indeed, advocates of strategic restraint have directly suggested that the United States should eschew tripwire deployments as costly and ineffective. 120
Second, if decision-makers are motivated to deter aggression abroad, they should recognize that successful deterrence requires more substantial foreign troop deployments.
This would have important implications for a variety of potential global hotspots. Consider the Russian threat to the Baltic states and Poland, all NATO members. The general concern among NATO commanders is that Russia could overrun tripwire forces and accomplish a quick fait accompli land grab. It could then consolidate its seizure through propaganda, a ceasefire agreement recognizing its territorial capture, and a veiled nuclear threat to deter a NATO counterattack. 121 More substantial troop deployments to shift the local balance of power would reduce this risk. At the 2016 Warsaw Summit, NATO agreed to expand its troop commitment to these states, building four multilateral battle groups, each of which contains about 1,200 troops. However, as noted above, some viewed these contingents as inadequate to shift the balance of power, arguing that their aim was to achieve “deterrence by trip wire.” 122 Even with these troop commitments, Russia might be tempted to launch a fait accompli , capturing territory before NATO could amass a more sizable force. 123 There is also concern about a possible Russian fait accompli attack against the Norwegian Arctic island of Svalbard. Deploying a substantial numbers of troops there, rather than a small tripwire force, could discourage such an attack. 124
[I]f decision-makers are unwilling to bear the costs of more substantial troop deployments in order to deter attacks on allies, then they should consider reducing foreign commitments to conserve resources.
Deploying a more significant number of troops could also help deter Chinese aggression. Andrew Krepinevich has proposed an integrated defense of the Japanese-Filipino-Taiwanese archipelago, a plan that includes the pre-deployment of U.S. troops to the region to alter Chinese military calculations of the local balance of power. 125 Specifically, pre-deployment and peacetime training exercises involving Japan and the United States on the Senkaku/Diaoyou Islands in the East China Sea could discourage China from launching a fait accompli attack there. 126
Our argument also sheds light on U.S. troop deployments to South Korea. A key question is whether current troop deployments to South Korea — about 28,000 troops — really change the local balance of power. Some have argued that the only significant contribution to deterrence the current American troop deployment can make is through tripwire effects, making a broader intervention more likely. 127 Our argument suggests that U.S. troops deployed to South Korea will boost deterrence but only if they appreciably change the local balance of power. If such a force is deemed by defense planners to be insufficiently sized or structured to change the balance of power, then increasing or altering U.S. forces deployed to South Korea would provide deterrence benefits. 128
Our argument also applies to U.S.-Japanese defense planning. Some propose that the deployment of American troops to Japanese territory, such as Okinawa, can deter an attack through a tripwire effect. 129 However, the mere presence of such troops does not necessarily deter an attacker. Deployments must be adequate to shift the local balance of power.
Last, our argument is germane to debates about peacekeeping. Some advocates of peacekeeping have made tripwire arguments that the presence of peacekeepers deters former insurgents from breaking the peace because the deaths of any peacekeeping troops in combat would ensure more substantial international intervention. 130 However, the early 1990s demonstrated that peacekeepers did not generate this credibility effect: Overpowered peacekeepers were captured in Bosnia and others were massacred in Rwanda, waiting in vain for rescue reinforcements that did not arrive. Peacekeepers act as a deterrent if they can shift the attacker’s calculus. This may require deployment in sufficient numbers or with the right equipment, such as armor.
We recognize that the pre-deployment of troops capable of shifting the local balance of power has clear limitations. Beyond the need to tailor any deployment to the local combat environment, increased troop deployments may raise financial costs that the public is unwilling to bear. Public opinion polls indicate Americans are hesitant about the prospect of raising defense spending. 131 In a fiscal environment in which the COVID-19 pandemic has placed pressure on, and prompted a reconsideration of, the U.S. defense budget, 132 increasing resources for foreign troop deployments may not be feasible. Moreover, increased troop deployments could create a moral hazard problem. Specifically, an ally that perceives greater protection from the United States could, in turn, feel more at liberty to engage in provocative or even aggressive action, knowing that it can rely on America for protection if the situation escalates. Some have proposed that moral hazard risks can be reduced by including language in alliance treaties that requires American intervention only if the ally was attacked first. However, others have observed that such “defensive wars” language can be vague, meaning that, even if an ally engages in provocative action, it can still argue that it was attacked first, triggering the alliance commitment. 133
The general policy implications of our paper are that policymakers should beware of assuming that small troop deployments can have outsized deterrence effects, and they should recognize that larger and more considered deployments may be necessary to provide real deterrence. Toward the end of the Obama administration, observers argued for just this: the need to move past Cold War faith in tripwire effects and instead devote more resources to the Army to boost troop deployments abroad: “Put simply, forward deployed soldiers and marines are more than just trip-wires and hostages. Allies do not have faith in American commitments because American troops might die; they have faith because American troops can kill and win.” 134
Dr. Dan Reiter is Samuel Candler Dobbs Professor of Political Science at Emory University. He is the award-winning author or co-author of dozens of articles and several books, including How Wars End (Princeton, 2009) and Democracies at War (Princeton, 2002, with Allan C. Stam).
Dr. Paul Poast is associate professor of political science at the University of Chicago and a non-resident fellow of the Chicago Council on Global Affairs. He is the author or co-author of three books, Economics of War (McGraw Hill-Irwin, 2006), Organizing Democracy (University of Chicago Press, 2018, with Johannes Urpelainen), and Arguing About Alliances (Cornell University Press, 2019).
Acknowledgements : An earlier version of this paper was presented at the 2019 annual meeting of the American Political Science Association meeting. We thank the participants of that panel for comments, especially those of Etel Solingen, Jack Levy, and Hein Goemans. For research assistance, thanks to Stefano Jud.
Image: U.S. Marine Corps photo by Lance Cpl. Kaleb Martin
1 Mark David Neiman, et al., "An International Game of Risk: Troop Placement and Major Power Competition," Journal of Politics (forthcoming), https://doi.org/10.1086/711716 .
2 Robert Jervis, The Logic of Images in International Relations (Princeton, NJ: Princeton University Press, 1970). Some recent scholarship is more confident that verbal statements in international relations are credible, or at least can be credible. See Anne E. Sartori, Deterrence by Diplomacy (Princeton, NJ: Princeton University Press, 2005); John J. Mearsheimer, Why Leaders Lie: The Truth About Lying in International Politics (Oxford: Oxford University Press, 2011); and Robert F. Trager, Diplomacy: Communication and the Origins of International Order (Cambridge: Cambridge University Press, 2017).
3 David Choi, “Trump Reportedly Asked the Pentagon to Explore Withdrawing U.S. Troops from Germany,” Task & Purpose , June 30, 2018, https://taskandpurpose.com/trump-pentagon-withdraw-troops-germany/ ; and Mark Landler, “Trump Orders Pentagon to Consider Reducing U.S. Forces in South Korea,” New York Times , May 3, 2018, https://www.nytimes.com/2018/05/03/world/asia/trump-troops-south-korea.html .
4 Brad Howard, “Marines May Be Headed for Taiwan for the First Time Since 1979,” Task & Purpose , June 29, 2018, https://taskandpurpose.com/marines-taiwan-china-mattis .
5 Karl Friedhoff, “US Troop Drawdown in South Korea Worth Considering,” The Hill , February 29, 2019, https://thehill.com/opinion/national-security/430428-us-troop-drawdown-in-south-korea-worth-considering .
6 Robert Jervis, Perception and Misperception in International Politics (Princeton, NJ: Princeton University Press, 1976), chap. 2.
7 Joshua C. Fjelstul and Dan Reiter, “Explaining Incompleteness and Conditionality in Alliance Agreements,” International Interactions 45, no. 6 (2019): 946–1002, http://doi.org/10.1080/03050629.2019.1647838 .
8 Thomas C. Schelling, Arms and Influence (New Haven, CT: Yale University Press, 1966), 22. See also Alexander L. George and Richard Smoke, Deterrence in American Foreign Policy: Theory and Practice (New York: Columbia University Press, 1974), 393.
9 Glenn Snyder similarly conflated these motives: “Some trip-wire effect could be realized with only token forces from the extra-Continental countries; an attack on such forces would implicate the honor, prestige, and other emotional values of these countries.” Glenn H. Snyder, Deterrence and Defense: Toward a Theory of National Security (Princeton, NJ: Princeton University Press, 1961), 130–31.
10 This work is indeed extensive. As a sample, see John J. Mearsheimer, "Nuclear Weapons and Deterrence in Europe," International Security 9, no. 3 (Winter 1984/1985): 19–46, https://www.jstor.org/stable/2538586?seq=1 ; Jacek Kugler, "Terror Without Deterrence: Reassessing the Role of Nuclear Weapons," Journal of Conflict Resolution 28, no. 3 (September 1984): 470–506, https://journals.sagepub.com/doi/10.1177/0022002784028003005 ; Daniel S. Geller, “Nuclear Weapons, Deterrence, and Crisis Escalation,” Journal of Conflict Resolution , 34, no. 2 (June 1990): 291–310, https://doi.org/10.1177/0022002790034002006 ; Kenneth N. Waltz, "Nuclear Myths and Political Realities," American Political Science Review 84, no. 3 (September 1990): 731–45, https://doi.org/10.2307/1962764 ; Robert Powell, Nuclear Deterrence Theory: The Search for Credibility (Cambridge: Cambridge University Press, 1990); Keir A. Lieber and Daryl G. Press, "The New Era of Nuclear Weapons, Deterrence, and Conflict," Strategic Studies Quarterly 7, no. 1 (Spring 2013): 3–14, https://www.jstor.org/stable/26270573?seq=1#metadata_info_tab_contents ; and Robert Jervis, Meaning of the Nuclear Revolution: Statecraft and the Prospect of Armageddon (Ithaca, NY: Cornell University Press, 1989).
11 For early work on the idea of tactical nuclear weapons, see Henry A. Kissinger, "Force and Diplomacy in the Nuclear Age," Foreign Affairs 34, no. 3 (April 1956): 349–66, https://www.jstor.org/stable/20031169?seq=1 ; and Morton H. Halperin, "Nuclear Weapons and Limited War," Journal of Conflict Resolution 5, no. 2 (June 1961): 146–66, https://journals.sagepub.com/doi/abs/10.1177/002200276100500203?journalCode=jcrb . For more recent discussion, see Matthew Fuhrmann and Todd S. Sechser, “Signaling Alliance Commitments: Hand-Tying and Sunk Costs in Extended Nuclear Deterrence,” American Journal of Political Science 58, no. 4 (October 2014): 919–35, https://doi.org/10.1111/ajps.12082 . For the use-it-or-lose-it logic applied to US nuclear forces on the Korean Peninsula, see Vipin Narang and Ankit Panda, “Command and Control in North Korea: What a Nuclear Launch Might Look Like,” War On the Rocks , Sept. 15, 2017, https://warontherocks.com/2017/09/command-and-control-in-north-korea-what-a-nuclear-launch-might-look-like .
12 Snyder, Deterrence and Defense , 133, note 13.
13 For an overview of the audience costs literature, see Bruce Bueno de Mesquita and Alastair Smith, "Domestic Explanations of International Relations," Annual Review of Political Science , no, 15 (2012): 161–81, https://doi.org/10.1146/annurev-polisci-070209-174835 ; and Allan Dafoe, Jonathan Renshon, and Paul Huth, "Reputation and Status as Motives for War," Annual Review of Political Science , no. 17 (2014): 371–93, https://doi.org/10.1146/annurev-polisci-071112-213421 . The audience costs literature fits in the broader literature on bargaining and war, as it is a proposed mechanism by which a threat of violence can eventually translate into the actual use of force. Moreover, it is a mechanism of “bargaining theory” that is susceptible to empirical evaluation. See Erik A. Gartzke and Paul Poast, "Empirically Assessing the Bargaining Theory of War: Potential and Challenges," in Oxford Research Encyclopedia of Politics (Oxford: Oxford University Press, 2017), https://doi.org/10.1093/acrefore/9780190228637.013.274 ; and Dan Reiter, “Exploring the Bargaining Model of War,” Perspectives on Politics 1, no. 1 (March 2003): 27–43, https://doi.org/10.1017/S1537592703000033 .
14 James D. Fearon, “Signaling Foreign Policy Interests: Tying Hands Versus Sinking Costs," Journal of Conflict Resolution 41, no. 1 (February 1997): 68–90, https://journals.sagepub.com/doi/10.1177/0022002797041001004 ; and Fuhrmann and Sechser, “Signaling Alliance Commitments.”
15 Fearon, “Signaling Foreign Policy Interests,” 69; and James D. Morrow, "Alliances, Credibility, and Peacetime Costs," Journal of Conflict Resolution 38, no. 2 (June 1994): 270–97, https://doi.org/10.1177/0022002794038002005 .
16 Scott D. Sagan and Benjamin A. Valentino, “Revisiting Hiroshima in Iran: What Americans Really Think About Using Nuclear Weapons and Killing Noncombatants,” International Security 42, no. 1 (Summer 2017): 41–79, muse.jhu.edu/article/667391 .
17 Robert E. Harkavy, "Defeat, National Humiliation, and the Revenge Motif in International Politics," International Politics 37, no. 3 (2000): 345–68, https://doi.org/10.1057/palgrave.ip.8890515 .
18 Peter Liberman, "An Eye for an Eye: Public Support for War Against Evildoers," International Organization 60, no. 3 (July 2006): 687–722, https://doi.org/10.1017/S002081830606022X ; and Rachel M. Stein, “War and Revenge: Explaining Conflict Initiation by Democracies,” American Political Science Review 109, no. 3 (August 2015): 556–73, https://doi.org/10.1017/S0003055415000301 .
19 The same can be said for leaders. Daryl Press holds that concerns about reputation do not matter to leaders in Calculating Credibility: How Leaders Assess Military Threats (Ithaca, NY: Cornell University Press, 2005). Others point to reputational concerns being conditional, not absolute. See Joshua D. Kertzer, Resolve in International Politics (Princeton, NJ: Princeton University Press, 2016); Danielle L. Lupton Reputation for Resolve: How Leaders Signal Determination in International Politics (Ithaca, NY: Cornell University Press, 2020); Keren Yarhi-Milo, Who Fights for Reputation: The Psychology of Leaders in International Conflict (Princeton, NJ: Princeton University Press, 2018); and Roseanne W. McManus Statements of Resolve: Achieving Coercive Credibility in International Conflict (Cambridge: Cambridge University Press, 2017).
20 Joshua D. Kertzer, and Ryan Brutger, "Decomposing Audience Costs: Bringing the Audience Back Into Audience Cost Theory," American Journal of Political Science 60, no. 1 (January 2016): 234–49, https://doi.org/10.1111/ajps.12201 . See also William G. Nomikos and Nicholas Sambanis, "What Is the Mechanism Underlying Audience Costs? Incompetence, Belligerence, and Inconsistency," Journal of Peace Research 56, no. 4 (July 2019): 575–88, https://doi.org/10.1177/0022343319839456 .
21 Jack Snyder and Erica D. Borghard, “The Costs of Empty Threats: A Penny, Not a Pound,” American Political Science Review 105, no. 3 (August 2011): 437–56, https://doi.org/10.1017/S000305541100027X ; and Marc Trachtenberg, “Audience Costs: An Historical Analysis,” Security Studies 21, no. 1 (2012): 3–42, https://doi.org/10.1080/09636412.2012.650590 .
22 Jack S. Levy, et al., “Backing Out or Backing In? Commitment and Consistency in Audience Cost Theory,” American Journal of Political Science 59, no. 4 (October 2015): 988–1001, https://doi.org/10.1111/ajps.12197 .
23 Stein, “War and Revenge”; Yarhi-Milo, Who Fights ; and Allan Dafoe and Devin Caughey, “Honor and War: Southern US Presidents and the Effects of Concern for Reputation,” World Politics 68, no. 2 (April 2016): 341–81, https://doi.org/10.1017/S0043887115000416 .
24 Matthew S. Levendusky and Michael C. Horowitz, "When Backing Down Is the Right Decision: Partisanship, New Information, and Audience Costs," Journal of Politics 74, no. 2 (April 2012): 323–38, https://doi.org/10.1017/S002238161100154X ; and Robert F. Trager and Lynn Vavreck, “The Political Costs of Crisis Bargaining: Presidential Rhetoric and the Role of Party,” American Journal of Political Science 55, no. 3 (July 2011): 526–45, https://doi.org/10.1111/j.1540-5907.2011.00521.x .
25 Stein, “War and Revenge,” 559.
26 Scott Sigmund Gartner and Gary M. Segura, Costly Calculations: A Theory of War, Casualties, and Politics (Cambridge: Cambridge University Press, 2021).
27 James Burk, “Public Support for Peacekeeping in Lebanon and Somalia: Assessing the Casualties Hypothesis,” Political Science Quarterly 114, no. 1 (Spring 1999): 53–78, https://doi.org/10.2307/2657991 .
28 Dan Reiter, “Democracy, Deception, and Entry Into War,” Security Studies 21, no. 4 (2012): 611–12, https://doi.org/10.1080/09636412.2012.734229 .
29 Michael Tomz, "Domestic Audience Costs in International Relations: An Experimental Approach," International Organization 61, no. 4 (2007): 829, https://doi.org/10.1017/S0020818307070282 .
30 Graeme A. M. Davies and Robert Johns, “Audience Costs Among the British Public: The Impact of Escalation, Crisis Type, and Prime Ministerial Rhetoric,” International Studies Quarterly 57, no. 4 (December 2013): 725–37, https://doi.org/10.1111/isqu.12045 .
31 Paul Musgrave and Steven Ward, “The Myth of the Tripwire Effect: Forward Military Deployments and U.S. Public Support for War,” unpublished manuscript, Department of Government, Cornell University, September 2018.
32 There is non-survey work on how decisions to abandon a formal treaty ally can harm a state’s ability to form subsequent alliances. See Mark J. C. Crescenzi, Of Friends and Foes: Reputation and Learning in International Politics (Oxford: Oxford University Press, 2018).
33 On faits accomplis , see Dan Altman, “By Fait Accompli, not Coercion: How States Wrest Territory from Their Adversaries,” International Studies Quarterly 61, no. 4 (December 2017): 881–91, https://doi.org/10.1093/isq/sqx049 ; and Dan Altman, “The Evolution of Territorial Conquest After 1945 and the Limits of the Territorial Integrity Norm,” International Organization 74, no. 3 (Summer 2020): 490–522, https://doi.org/10.1017/S0020818320000119 .
34 Altman, “Evolution,” 497.
35 Schelling, Arms and Influence , 66.
36 On how aggressors can redirect the economic resources of captured territory to boost their own military power, see Peter Liberman, Does Conquest Pay? The Exploitation of Occupied Industrial Societies (Princeton, NJ: Princeton University Press, 1998).
37 Dan Reiter and Allan C. Stam, Democracies at War (Princeton, NJ: Princeton University Press, 2002).
38 Marc Trachtenberg, History and Strategy (Princeton, NJ: Princeton University Press, 1991), esp. 193, 219; and Marc Trachtenberg, A Constructed Peace: The Making of the European Settlement, 1945–1963 (Princeton, NJ: Princeton University Press, 1999), 86–87.
39 Quoted in Hope M. Harrison, Driving the Soviets Up the Wall: Soviet-East German Relations 1953–1961 (Princeton, NJ: Princeton University Press, 2005), 124.
40 Harrison, Driving , 201. See also Trachtenberg, A Constructed Peace , 251–52, 323; Vladislav M. Zubok, “Khrushchev and the Berlin Crisis (1958–1962),” Woodrow Wilson International Center for Scholars, Cold War International History Project working paper #6, May 1993, https://www.wilsoncenter.org/sites/default/files/media/documents/publication/ACFB7D.pdf .
41 For a recent detailed analysis of NATO’s “Enhanced Forward Presence” in the eastern part of the alliance, see Alexander Lanoszka, Christian Leuprecht, and Alexander Moens, eds., Lessons from the Enhanced Forward Presence, 2017-2020 , NATO Defence College Research Paper No. 14, Nov. 30, 2020, https://www.ndc.nato.int/news/news.php?icode=1504 .
42 Michael O’Hanlon and Christopher Skaluba, “A Report from NATO’s Front Lines,” The National Interest , June 10, 2019, https://nationalinterest.org/feature/report-natos-front-lines-62067 .
43 Sebastian Roblin, “NATO vs Russia: A Massive Wargame Is Simulating What Would Happen if Putin Invaded Norway,” The National Interest , Oct. 27, 2018, https://nationalinterest.org/blog/buzz/nato-vs-russia-massive-wargame-simulating-what-would-happen-if-putin-invaded-norway-34497 .
44 O’Hanlon and Skaluba, “A Report from NATO’s Front Lines.”
45 Alexander R. Vershbow and Philip M. Breedlove, “Permanent Deterrence: Enhancements to the U.S. Military Presence in North Central Europe,” Atlantic Council, Feb. 7, 2019, 30–31, https://www.atlanticcouncil.org/in-depth-research-reports/report/permanent-deterrence/ .
46 David A. Shlabak, and Michael W. Johnson, Reinforcing Deterrence on NATO's Eastern Flank: Wargaming the Defense of the Baltics (Santa Monica, CA: RAND, 2016), https://www.rand.org/pubs/research_reports/RR1253.html . For a critique of this study, see Michael Kofman, “Fixing NATO Deterrence in the East Or: How I Learned to Stop Worrying and Love NATO’s Crushing Defeat by Russia,” War on the Rocks , May 12, 2016, https://warontherocks.com/2016/05/fixing-nato-deterrence-in-the-east-or-how-i-learned-to-stop-worrying-and-love-natos-crushing-defeat-by-russia/.
47 It is possible that more substantial deployments of troops could also bolster the credibility of a deterrent threat, if such deployments constitute a credible “sunk costs” signal.
48 On the contributions of quantity, technology, and strategy to military effectiveness and deterrence, see Stephen Biddle, Military Power: Explaining Victory and Defeat in Modern Battle (Princeton, NJ: Princeton University Press, 2004); and John J. Mearsheimer, Conventional Deterrence (Ithaca, NY: Cornell University Press, 1983).
49 Forward-deployed nuclear weapons could also serve this function, though one study found that nuclear forward deployments do not bolster deterrence success (Fuhrmann and Sechser, “Signaling”).
50 Mearsheimer, Conventional Deterrence , esp. chap. 7.
51 Paul Poast, Arguing About Alliances: The Art of Agreement in Military-Pact Negotiations (Ithaca, NY: Cornell University Press, 2019).
52 Kenneth N. Waltz, “A Strategy for the Rapid Deployment Force,” International Security 5, no. 4 (Spring 1981): 67, https://www.jstor.org/stable/2538713?seq=1 .
53 Mearsheimer, Conventional Deterrence , 64.
54 Reiter and Stam, Democracies at War , chap. 6.
55 Lien-Hang T. Nguyen, Hanoi’s War: An International History of the War for Peace in Vietnam (Chapel Hill, NC: University of North Carolina Press, 2012).
56 Mearsheimer, Conventional Deterrence .
57 Ernest R. May, Strange Victory: Hitler’s Conquest of France (New York: Gardner’s, 1999). See also the September 2019 remarks by Pascal Heyman, the Belgian Permanent Representative to NATO. Pascal Heyman, Twitter post, Sept. 3, 2019, 2:22am, https://twitter.com/PascalHeyman/status/1168786332572893184 .
58 Tanner Greer, “Taiwan Can Win a War with China,” Foreign Policy , Sept. 25, 2018, https://foreignpolicy.com/2018/09/25/taiwan-can-win-a-war-with-china/ .
59 Quoted in Kathryn Weathersby, “New Findings on the Korean War,” Cold War International History Project Bulletin , no. 3 (Fall 1993): 15, https://www.wilsoncenter.org/sites/default/files/media/documents/publication/CWIHPBulletin3.pdf .
60 Quoted in Kathryn Weathersby, “Korea, 1949-50: To Attack or Not to Attack? Stalin, Kim Il Sung, and the Prelude to War,” Cold War International History Project Bulletin no. 5 (Spring 1995): 8, https://www.wilsoncenter.org/sites/default/files/media/documents/publication/CWIHP_Bulletin_5.pdf .
61 Weathersby, “Korea, 1949-50,” 5. This estimate was not wholly inaccurate. There were some 16,000 U.S. forces in South Korea in December 1948, after which the U.S. government began to plan the drawdown of U.S. forces there. James F. Schnabel, The United States Army in the Korean War, Policy and Direction: The First Year (Washington, DC: Center of Military History, US Army, 1972), 30.
62 Quoted in Kathryn Weathersby, “Stalin and the Korean War,” in Origins of the Cold War: An International History , second ed., ed. Melvyn P. Leffler and David S. Painter (New York: Routledge, 2005), 270.
63 Kathryn Weathersby, “‘Should We Fear This?’ Stalin and the Danger of War with America,” Woodrow Wilson International Center for Scholars, Cold War International History Project, Working Paper No. 39 (2002), 21, https://www.wilsoncenter.org/sites/default/files/media/documents/publication/ACFAEF.pdf .
64 “Telegram from Gromyko to Tunkin at the Soviet Embassy in Pyongyang,” September 11, 1949; and “Telegram from Tunkin to the Soviet Foreign Ministry in Reply to 11 September Telegram,” Sept. 14, 1949, Wilson Center Digital Archive, accessed May 25, 2021, https://digitalarchive.wilsoncenter.org/search-results/1/%7B%22search-in%22%3A%22all%22%2C%22term%22%3A%22tunkin%22%7D?recordType=Record .
65 Charles Burton Marshall Oral History Interview with Niel M. Johnson, June 21, 1989 and June 23, 1989, Truman Library, accessed May 25, 2021, https://www.trumanlibrary.gov/library/oral-histories/marshall .
66 Shen Zhihua, “Sino-Soviet Relations and the Origins of the Korean War: Stalin’s Strategic Goals in the Far East,” Journal of Cold War Studies 2, no. 2 (Spring 2000): 52, https://muse.jhu.edu/article/9152 .
67 Quoted in Weathersby, “Korea, 1949–50,” 9.
68 Zhihua, “Sino-Soviet Relations,” 63.
69 Quoted in Weathersby, “‘Should We Fear This?’” 10. This is consistent with the recollection of Nikita Khrushchev, who was physically present at the Stalin-Kim meeting: “[I]f everything were done quickly … then U.S. intervention would be ruled out; the United States would not try to intervene with its armed forces.” Sergei Khrushchev, ed., Memoirs of Nikita Khrushchev , Volume 2: Reformer (1945–1964) , trans. George Shriver (University Park, PA: Pennsylvania State University Press, 2006), 92. See also William Stueck, Rethinking the Korean War: A New Diplomatic and Strategic History (Princeton, NJ: Princeton University Press, 2002), 74.
70 Quoted in Weathersby, “‘Should We Fear This?’” 10.
71 Weathersby, “‘Should We Fear This?’” 14.
72 “Ciphered Telegram No. 34691 from Feng Xi [Stalin] to Soviet Ambassador in Pyongyang Shtykov,” July 1, 1950, History and Public Policy Program Digital Archive, Wilson Center, https://digitalarchive.wilsoncenter.org/document/110687.pdf?v=b936d0b235200d206d07eca96e839700 . The report of American bombers and casualties can be found in “Telegram, Shtykov to CDE. Gromyko,” June 30, 1950, Digital Archive, Wilson Center, https://digitalarchive.wilsoncenter.org/document/114911 .
73 Weathersby, “‘Should We Fear This?’” 11; Sergei N. Goncharov, John W. Lewis, and Xue Litai, Uncertain Partners: Stalin, Mao, and the Korean War (Stanford, CA: Stanford University Press, 1993), 101; and Dean Acheson “Speech on the Far East,” Jan. 12, 1950, Teaching American History, accessed May 25, 2021, https://teachingamericanhistory.org/library/document/speech-on-the-far-east/ .
74 Walter R. Waggoner, “Acheson Says U. S. Counts on Chinese Anger at Soviet for Land Seizures in North,” New York Times , Jan. 13, 1950, 1, 2.
75 Goncharov, Lewis, and Litai, Uncertain Partners , 151.
76 Quoted in Odd Arne Westad, “Fighting for Friendship: Mao, Stalin, and the Sino-Soviet Treaty of 1950,” Cold War International History Project Bulletin , nos. 8-9 (Winter 1996/97): 232–33, https://www.wilsoncenter.org/sites/default/files/media/documents/publication/CWIHP_Bulletin_8-9.pdf .
77 Kim Donggil, “Stalin’s Korean U-Turn: The USSR’s Evolving Security Strategy and the Origins of the Korean War,” Seoul Journal of Corean Studies 24, no. 1 (June 2011): 96, https://www.researchgate.net/publication/298957606_Stalin's_Korean_U-Turn_The_USSR's_Evolving_Security_Strategy_and_the_Origins_of_the_Korean_War .
78 James I. Matray, “Dean Acheson’s Press Club Speech Reexamined,” Journal of Conflict Studies 22, no. 1 (Spring 2002), https://journals.lib.unb.ca/index.php/jcs/article/view/366/578 .
79 The plan was contained in his memorandum “War Against France.”
80 Fritz Fischer, Germany’s Aims in the First World War (New York, Norton, 1967), 100.
81 Terence Zuber questioned the existence of the Schlieffen Plan in Inventing the Schlieffen Plan: German War Planning, 1871–1914 (Oxford: Oxford University Press, 2002). The Zuber thesis has come under heavy criticism from historians. See Hans Ehlert, Michael Epkenhans, and Gerhard P. Gross, eds., The Schlieffen Plan: International Perspectives on the German Strategy for World War I , trans. David T. Zabecki (Lexington, KY: University Press of Kentucky, 2014). However, Zuber himself recognized that German strategy called for “the main body to advance through Belgium and Luxembourg into France.” See Inventing the Schlieffen Plan , 259.
82 John C. G. Röhl, Wilhelm II: Into the Abyss of War and Exile 1900-1941 , trans. Shelia de Bellaigue and Roy Bridge (Cambridge: Cambridge University Press, 2014), 325.
83 Quoted in Annika Mombauer, “German War Plans,” in War Planning 1914 , ed. Richard F. Hamilton and Holger H. Herwig (Cambridge: Cambridge University Press, 2010), 61.
84 Critics of our argument may propose that the political impossibility of such deployments makes such discussion moot. Our theory turns not on the political viability of a troop deployment, but rather on its military effects, and the process tracing evidence in this case clearly indicates that such deployments would have deterred Germany. Further, understanding the military advantages of pre-deployment and alliance more generally can overcome even traditional neutrality. Neutral countries that were invaded during the world wars joined alliances after wars’ ends. Dan Reiter, Crucible of Beliefs: Learning, Alliances, and World Wars (Ithaca, NY: Cornell University Press, 1996).
85 Quoted in Gerhard Ritter, The Schlieffen Plan: Critique of a Myth (London: Oswald Wolff, 1958), 161.
86 Fritz Fischer, War of Illusions: German Policies from 1911 to 1914 , trans. Marian Jackson (New York: Norton, 1975), 390.
87 Gerhard Ritter, Sword and the Scepter: The Problem of Militarism in Germany, Vol.2: The European Powers and the Wilhelminian Empire, 1890–1914 , trans. Heinz Norden (Coral Gables, FL: University of Miami Press, 1970), 207.
88 Fischer, War of Illusions , 390.
89 Quoted in Ritter, The Schlieffen Plan , 176.
90 Quoted in Ritter, The Schlieffen Plan , 186.
91 Quoted in Ritter, The Schlieffen Plan , 166.
92 Scott D. Sagan, “1914 Revisited: Allies, Offense, and Instability,” International Security 11, no. 2 (Fall 1986): 170–71, https://www.jstor.org/stable/2538961?seq=1 .
93 Annika Mombauer, Helmuth von Moltke and the Origins of the First World War (Cambridge: Cambridge University Press, 2001), 96–97; and L. C. F. Turner, “The Significance of the Schlieffen Plan,” in The War Plans of the Great Powers , ed. Paul M. Kennedy (London: George Allen & Unwin, 1979), 212
94 Ulrich Trumpener, “War Premeditated? German Intelligence Operations in July 1914,” Central European History 9, no. 1 (March 1976): 80, https://doi.org/10.1017/S0008938900018094 .
95 John Keegan, The First World War (New York: Knopf, 1999), 80–82.
96 Terence Zuber, Ten Days in August: The Siege of Liège 1914 (Stroud, UK: Spellmount, 2014), 31; and Barbara W. Tuchman, The Guns of August (New York: Bantam, 1962), 198.
97 Quoted in Fischer, Germany’s Aims , 37.
98 Quoted in Ritter, The Schlieffen Plan , 166.
99 Tuchman, Guns of August , 203.
100 Mombauer, “German War Plans,” 67.
101 “Lieutenant-Colonel N. W. Barnardiston to Major-General J. M. Grierson,” March 30, 1906, in British Documents on the Origins of the War, Vol. III (London: Her Majesty’s Stationery Office, 1928), 197.
102 “Lieutenant-Colonel N. W. Barnardiston to Major-General J. M. Grierson,” March 31, 1906, in British Documents on the Origins of the War, Vol. III , (London: Her Majesty’s Stationery Office, 1928), 199. Italics in original.
103 “Lieutenant-Colonel N. W. Barnardiston to Major-General J. M. Grierson,” 199.
104 Samuel R. Williamson, Jr., The Politics of Grand Strategy: Britain and France Prepare for War, 1904–1914 (Cambridge, MA: Harvard University Press, 1969), 66. There was a major battle between British and German troops at Mons, Belgium, in late August 1914. The British lacked the fortifications present at Liège and suffered defeat.
105 Daniel H. Thomas, The Guarantee of Belgian Independence and Neutrality in European Diplomacy, 1830’s–1930’s (Kingston, R.I.: D. H. Thomas Publishing, 1983), 461.
106 Williamson, Politics of Grand Strategy , 97.
107 Quoted in David Stevenson, “Battlefield or Barrier? Rearmament and Military Planning in Belgium, 1902–1914,” International History Review 29, no. 3 (September 2007): 503, https://doi.org/10.1080/07075332.2007.9641133
108 Stevenson, “Battlefield or Barrier?” esp. 501, 505–06; Mombauer, Moltke , 162–63.
109 Luigi Albertini, The Origins of the War of 1914, Vol. 2 , trans. Isabella M. Massey (London: Oxford University Press, 1952), 514. See also Sagan, “1914 Revisited,” 171.
110 For an argument that the German military held very strong control over decision-making, see Martin Kitchen, “Civil-Military Relations in Germany During the First World War,” in The Great War, 1914–18: Essays on the Military, Political and Social History of the First World War , ed. R. J. Q. Adams (London: MacMillan, 1990); and Jack Snyder, “Civil-Military Relations and the Cult of the Offensive, 1914 and 1984,” International Security 9, no. 1 (Summer 1984): 108–46, https://www.jstor.org/stable/2538637?seq=1 . For a different perspective on the role of the Kaiser, see Röhl, Wilhelm II . See also Holger Afflerbach, “Wilhelm II as Supreme Warlord in the First World War,” War in History 5, no. 4 (November 1998): 432, 432n, https://doi.org/10.1177%2F096834459800500403 .
111 Marc Trachtenberg argues that Germany did not care about British neutrality and that it would have invaded regardless. See Jack S. Levy, Thomas J. Christensen, and Marc Trachtenberg, “Correspondence: Mobilization and Inadvertence in the July Crisis," International Security, 16, no. 1 (Summer 1991): 189–203, https://www.jstor.org/stable/2539055?seq=1 . Dale Copeland makes a similar point in The Origins of Major War (Ithaca, NY: Cornell University Press, 2000), 84–85. These critiques are not problematic for our argument. These arguments are based on the assumption that British intervention would be too late to save Belgium. This would no longer be valid if Britain had pre-deployed troops.
112 Paul K. Huth, Extended Deterrence and the Prevention of War (New Haven, CT: Yale University Press, 1988), 198n; and Mombauer, “German War Plans,” 66.
113 Mombauer, Moltke , 209.
114 Mombauer, Moltke , 209; and Annika Mombauer, “A Reluctant Military Leader? Helmut von Moltke and the July Crisis of 1914,” War in History 6, no. 4 (October 1999): 439, https://doi.org/10.1177/096834459900600403 .
115 “Memo from Helmut von Moltke,” Dec. 21, 1912, in Der Weltkrieg 1914-1918. Kriegsrüstung und Kriegswirtschaft, Vol. 1 : Die militärische, wirtschaftliche und finanzielle Rüstung Deutschlands von vor der Reichsgründung bis zum Ausbruch des Weltkrieges + Anlagen (Berlin: Reichsarchiv (Abteilung 3), 1930), 156–74. Thanks to Stefano Jud for translation from the original German.
116 Quoted in Mombauer, Moltke , 221. See also pages 155 and 164.
117 Quoted in Ritter, Schlieffen Plan , 166.
118 Mombauer, Moltke , 221.
119 Mombauer, “Reluctant Military Leader,” 443.
120 Eugene Gholz, Daryl G. Press, and Harvey M Sapolsky, “Come Home America: The Strategy of Restraint in the Face of Temptation,” International Security 21, no. 4 (Spring 1997): esp. 33n, https://www.jstor.org/stable/2539282?seq=1 .
121 Hans Binnendijk, “The Folly of a NATO Troop Withdrawal Decision,” Defense News , June 9, 2020, https://www.defensenews.com/opinion/commentary/2020/06/09/the-folly-of-a-nato-troop-withdrawal-decision/ .
122 Quoted in Breedlove and Vershbow, “Permanent Deterrence,” 2.
123 Tobin Harshaw, “The Future of Nuclear Weapons and the Next Great War,” Bloomberg , Jan. 12, 2019, https://www.bnnbloomberg.ca/the-future-of-nuclear-weapons-and-the-next-great-war-1.1197360 .
124 James K. Wither, “Svalbard: NATO’s Arctic ‘Achilles’ Heel,” RUSI Journal 163, no. 5 (2018): 28–37, https://doi.org/10.1080/03071847.2018.1552453
125 Andrew F. Krepinevich, Jr., “How to Deter China: The Case for Archipelagic Defense,” Foreign Affairs 94, no. 2 (March/April 2015): 78–86, https://www.foreignaffairs.com/articles/china/2015-02-16/how-deter-china .
126 James E. Fanell and Kerry K. Gershaneck, “White Warships and Little Blue Men: The Looming ‘Short, Sharp War’ in the East China Sea Over the Senkakus,” Project 2049 Institute, March 30, 2018, https://project2049.net/2018/03/30/white-warships-and-little-blue-men-the-looming-short-sharp-war-in-the-east-china-sea-over-the-senkakus/ .
127 For example, see Michael J. Mazarr, et al., What Deters and Why: Exploring Requirements for Effective Deterrence of Interstate Aggression (Washington, DC: RAND, 2018), e.g., 37, https://www.rand.org/pubs/research_reports/RR2451.html .
128 On the ability of U.S. forces to contribute to conventional deterrence missions in South Korea, see Michael J. Mazarr et al., The Korean Peninsula: Three Dangerous Scenarios (Washington, DC: RAND, 2018), https://www.rand.org/pubs/perspectives/PE262.html .
129 Richard C. Bush, “Okinawa and Security in East Asia,” Brookings Institute, March 10, 2010, https://www.brookings.edu/on-the-record/okinawa-and-security-in-east-asia/ .
130 Virginia Page Fortna, “Interstate Peacekeeping: Causal Mechanisms and Empirical Effects,” World Politics 56, no. 4 (July 2004): 481–519, https://doi.org/10.1353/wp.2005.0004 .
131 “Most Americans Don’t Support Higher Defense Spending,” Yahoo! Finance , April 1, 2019, https://finance.yahoo.com/news/most-americans-don-t-support-221355051.html .
132 Missy Ryan, “Military Faces Another Potential Coronavirus Toll: Budget Cuts,” Washington Post , May 15, 2020, https://www.washingtonpost.com/national-security/military-faces-another-potential-coronavirus-toll-budget-cuts/2020/05/14/ae7abbf6-906b-11ea-8df0-ee33c3f5b0d6_story.html .
133 Brett V. Benson, Constructing International Security: Alliances, Deterrence, and Moral Hazard (Cambridge: Cambridge University Press, 2012); John Glaser, “Withdrawing from Overseas Bases: Why a Forward-Deployed Military Posture Is Unnecessary, Outdated, and Dangerous,” CATO Institute, July 18, 2017, https://www.cato.org/publications/policy-analysis/withdrawing-overseas-bases-why-forward-deployed-military-posture ; and Fjelstul and Reiter, “Explaining Incompleteness.”
134 Alexander Lanoszka and Michael Hunzeker, “The Efficacy of Landpower: Landpower and American Credibility,” Parameters 45, no. 4 (2016): 18, https://openaccess.city.ac.uk/id/eprint/15415/1/HunzekerLanoszkaParameters.pdf .
Related Articles
Stabilizing haiti: a guide for policymakers.
Ian Murray , Chris Bernotavicius
Proposals for a security-focused intervention in Haiti are logical given the rampant instability and endless escalation of gang violence. Many argue that Haiti’s foundational problems of economic underdevelopment, violence, and weak institutions cannot be…
From Panic to Policy: The Limits of Foreign Propaganda and the Foundations of an Effective Response
Gavin Wilde
American leaders and scholars have long feared the prospect that hostile foreign powers could subvert democracy by spreading false, misleading, and inflammatory information by using various media. Drawing on both historical experience and empirical literature,…
Climate Change and Military Power: Hunting for Submarines in the Warming Ocean
Andrea Gilli , Mauro Gilli , Antonio Ricchi , Aniello Russo , Sandro Carniel
Climate change will have significant effects on military power, capabilities, effectiveness, and employment. Yet, scholars have paid little attention to this topic. We address this gap by investigating the effects of changing ocean conditions on anti-submarine…
Sign up to the TNSR newsletter:

Get Personalized Tips on How To Grow Your Business
Join over 75,000 other entrepreneurs, business owners, and marketing pros who are receiving the cutting-edge tips, tricks, and examples that showing you how to grow your business.
Yes, Grow My Business!
What Is a Tripwire? Hint: Tripwires Can Transform Your Business Results
“You think that’s air you’re breathing?”
So said Morpheus in The Matrix when Neo comes to realize the “real world” wasn’t what he thought it was.
Have you ever had a similar realization that changed what you believed was possible?
Learning new marketing tactics – like what is a tripwire – can be an eye-opening experience.
I was chatting with a fellow entrepreneur on Skype recently. He was watching my updated webinar.
He mentioned my tips section about “smart” sales funnels and dynamic email segmentation / personalization . He said that for him, that was a “mind-blown” moment.
I felt the same way when I first learned about the concept of upsells and cross-sells.
My reaction was something like:
“You’re telling me that we can increase average revenue per sale by at least 50% … just by asking people at checkout?”
It turned around to be way more than 50% when we first started testing it way back in 2018. Plus… customers? They were actually happier because they got more value.
Today, I hope to blow your mind by teaching you the concept and conversion power of tripwires and how to apply it to your marketing/funnel to 10x sales on your core offering.
In a rush? Want to download this article as a PDF so you can easily take action on it later? Click here to download it now .
“ What Is a Tripwire?
According to Salesforce Inc.,
“A tripwire is something small but meaningful that gets a prospect to convert, at least to some degree, to a real customer.’’
A tripwire is very similar to the self-liquidating offer we’ve covered in the past.
In fact, a product splinter is another name for a tripwire. The latter is just the more popular term.
To give you a better perspective, here’s another tripwire definition :
A tripwire is a small offer (usually between $5 - $50) sold to new email subscribers after opt-in. It’s meant to accelerate the buyer/seller relationship.
People might sometimes join your email list but might not want your core offer. Yes, even after you nurture the relationship.
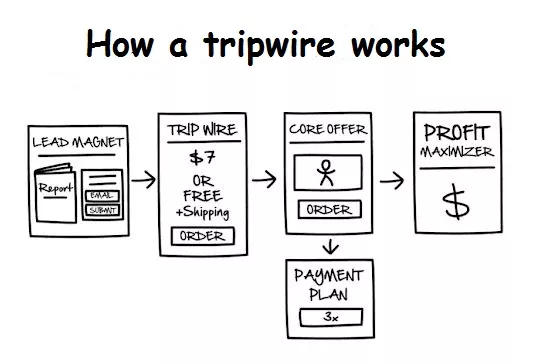
Your first step should be to make a simple and affordable offer. Doing so will help those potential customers overcome the fear of buying from you and gain trust.
If you think about a relationship with a customer as a slope, the value ladder is a straight line. The customer will visit the website, subscribe to a newsletter, and then boom ! That ladder goes way up at an almost 90-degree incline.
Then a customer may make a purchase for $100, $500, or even $1,000.
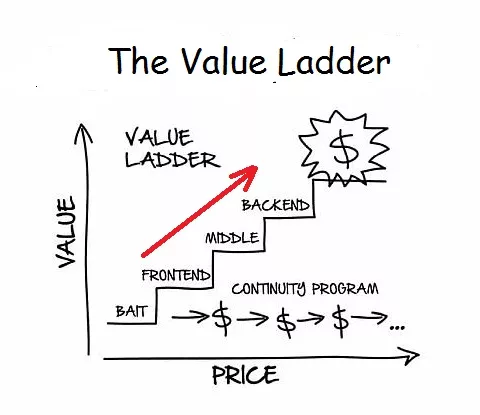
That’s all well and good; a lot of businesses successfully operate that way. But here’s the dilemma:
How do you service a larger market with automation services and still build trust? The answer? A tripwire.
A tripwire evens out that incline to convert more people and nurture a relationship. Now it’s sort of a 45-degree gradual incline in terms of the relationship.
You can then capture more of the market.
Basically, Tripwires help to gradually build buyer trust through an initial low-cost purchase. With trust established, you present higher-cost core offers.
According to Ryan Deiss, founder of DigitalMarketer.com, “People who purchased tripwires were 10 times more likely to purchase their core offer.”
If you’ve liked what you’ve read so far, you should subscribe to our newsletter!
Examples of Tripwires in Action
Disney Movie Club

The Disney Movie Club offers four movies for $1 with a membership.
The membership gets you access to their full library of movies. That offer is the tripwire leading to a subscription. It’s assumed that Disney Movie Club will charge your card after a month, and you’ll have to send the movies back.
That makes this offer a low barrier to entry in terms of starting a buyer/customer relationship.
DotComSecrets

Just to reiterate, a tripwire is supposed to be a standalone offer. It’s meant to be a stepping stone for building trust and adding value.
It’s like climbing up the value ladder, so to speak. I plan on covering the concept of the value ladder in a future blog post.
Russell Brunson from DotComSecrets talks about the value ladder in his book.
There are a lot of offers on the DotComSecrets homepage, but their tripwire is the free eBook, DotCom Secrets: The Underground Playbook For Growing Your Company Online .
The book presents a starting point to learn more about that. This is a front-end offer.
The idea is that people are going to read this book and learn strategies to grow their businesses. It’s an opportunity for Brunson to start a buyer/seller relationship. As I’ve said, it’s a substantial book.
For me, most of the content in the book is a refresher. Some of it is slightly different takes on various concepts. The idea is to upsell you on different products he offers, such as ClickFunnels or a coaching program.
This eBook is a great front-end offer. It’s a solid starting point for a very well-developed value that Brunson has in place.
Want your sales funnel to deliver much more sales? Our battle-tested, high-converting swipe file with marketing examples from million-dollar companies can help you achieve that. Click here to access it now!
BTB Boxing & Fitness

Australian gym, BTB Boxing & Fitness , does a decent job with their tripwire offer. They offer a 7-day trial for $7, which they call an ''introductory offer.''
For seven days, you can use the full gym like a member, take any class, and use the equipment without any restrictions.
It is a great way to try out their gym and see if you like the mood, instructors, gear, and environment.
The $7 tripwire offer gives you what members get for a short time. After that, you pay $39 per week as a full membership fee.
This low-risk way to test the gym first is designed to get prospects hooked into signing up for full membership. And the full membership money could keep rolling in for months or years.
BTB Boxing & Fitness also has $65 and $90 add-on offers. Those offers would eventually bring in more revenue in the long run.
Check out these additional tripwire examples to inspire you to create your own.
Need all your marketing projects and tasks done-for-you by a team of proven human professionals? Sign up to try our done-for-you services for 7 days for only $7 .
How to Make Your Own Tripwire Right Now
The easiest way to make your own tripwire is to look at your current core offer. Think of how you can splinter off a piece of that. This can be in the form of an eBook, for example, just like Russell Brunson did.
If you’re selling a service, what we used to do was to sell a “Project Roadmap.” We called this a “service slice” (same idea as a product splinter).
This would cost $300 and ensured we got paid for the time we put into planning the proposal. It also created an association between us delivering our expertise and our time. It made it easier for us to make our core sale.
So look at what you’re doing now. See if you can splinter it, package it, and sell it off to new email subscribers. If you are selling services, you’d want to sell the roadmap after the customer opts in and makes a consultation.
For digital marketers, online entrepreneurs, or info-product marketers:
Place the tripwire right after someone opts into your email list. Make sure to include a risk reversal, like a 30-day money-back guarantee.
Common Tripwire Mistakes to Avoid
Be careful not to make these common mistakes with your tripwire offer:
- Pricing too high - Keep it under $50. Going higher could hurt conversions.
- Offering too much for free - Give some value but not too much. You should save that for the core offer.
- Forgetting follow-up - Check in after purchase to start a relationship.
- Not linking to core offer - Clearly show how tripwire leads to the main products.
Some other tripwire mistakes to avoid are:
- Making it too complicated
- Bad sales page design
- Weak value proposition
- No clear next steps
Tripwires fail when people don't buy them or when buyers don't convert later. Avoid these pitfalls to maximize success!
The key is giving some value at a low cost while leaving them wanting more from your core offerings. Do this right, and the tripwire smoothly ushers buyers along your sales funnel.
Sick of guessing which words will sell? Create high-converting ads, pages, and funnels with done-for-you templates and scripts from million-dollar companies. Click here to access your Ultimate Swipe File!
Let’s wrap it all up.
A tripwire “ignites” the buyer/seller relationship and increases core offer purchases. In other words, invest a little money and get some value.
That builds trust and makes them more open to a future purchase, assuming it delivers value.
- The price of a tripwire is typically between $5 and $50. Keeping the price low (but the value relative to the price high) entices customers to make bigger purchases once they gain trust in you.
- A tripwire is a useful way to persuade shy or reluctant customers to finally buy your core offer. Even if they would have refused before, likely because of a “trust gap.” The tripwire is a low-perceived-risk way to bridge this gap.
- An eBook is a decent starting point if you want to make your own tripwire.
- Don’t forget to offer a risk reversal after opt-in. This further builds the trust between the customer and your brand.
Have you ever used a tripwire before?
What were the results?
Are you thinking of ways to create tripwires for your own business?
Let me know in the comments below.
Keep AutoGrowin’, Stay Focused,

1. https://www.salesforce.com/ca/blog/2016/04/art-of-tripwire-sales.html
2. https://www.paldesk.com/how-to-create-a-value-ladder-to-maintain-clients
3. https://www.nichepursuits.com/tripwire-funnels
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Delegate All Your Marketing Projects (Minus The Hiring Headaches) — See 29 Examples of Tasks and Projects You Can Delegate Now 💪
About growbo.
Growbo is a platform to help brands, businesses, and agencies accelerate their marketing success by providing an all-in-one marketing team (16 skillsets) via an easy-to-use app. Founded in 2010, we've helped 1,000's of companies, from small to enterprise, to scale their businesses by delegating their marketing without dealing with hiring, managing, payroll... Try it today with a $7 for 7-day trial

Yes, Grow My Business
Download Your FREE Guide to See How We Can Help You
Do You Want to Delegate Your Digital Marketing Projects—Without The Headaches of Hiring?

Yes, Gimme the Guide!
Tripwire Marketing: Lure in More Customers With 12 Slam-Dunk Ideas
You’re unhappy with your conversion rate . People just aren’t buying what you’re selling. The solution might lie in tripwire marketing.
The term tripwire marketing might sound a little shady, like you’re trying to get one over on your customer. That’s not the case at all.
Marketing and advertising experts have been using tripwire marketing for decades in one form or another, and it works just as well online as it does in brick-and-mortar stores. In fact, it’s even more effective because you can more easily stay in touch with the customer.
What is tripwire marketing? And how does it work? Those are two of the many questions I’ll answer for you today.
If you’re interested in a particular topic, feel free to skip around. I’m going to cover the following:
- What Is Tripwire Marketing?
- How Tripwire Marketing Can Help Boost Your Conversions
Tripwire Funnel Examples
- Building Your Tripwire Strategy
How to Create a Tripwire
- What Is a Good Conversion Rate for Tripwire Marketing?
- Optimize Your Tripwire’s Conversions With With Website Optimization Tools
- Start Now: 12 Tripwire Ideas
What is Tripwire Marketing?
Tripwire marketing is a conversion-acceleration hack that convinces target consumers to buy something small from you rather than a more expensive product or service.
There are actually two versions of tripwire marketing you can use to produce more conversions.
The first one involves luring in customers with low-cost offers.
Imagine for a moment that you sell online courses . You offer a monster e-course with dozens of videos, articles, and other assets, and it’s priced at $1,000.
That’s a lot of money for a consumer to spend on a company with which he has no experience. If you haven’t been in business long, you might not have strong social proof or other ways to speed up conversions and overcome objections.
To incentivize conversions, you might create a mini-course that supplements your primary course. It could include one or two short videos, a couple checklists, and a few articles.
Pricing this much smaller course at $20 or even $100 makes the product far more attractive to new customers. Most people are more willing to spend small amounts of money than a huge chunk.
You then set up a tripwire marketing campaign . The tripwire — your mini-course — serves as proof of concept. It shows your customers that you deliver what you promise. They become enmeshed in your sales funnel, so you can market to them via email and other means to convert them on the larger product.
The second tripwire marketing strategy focuses on consumer behavior.
Let’s say you run a subscription service for which you charge $30 per month. Customer A has been a loyal subscriber for six months, then suddenly cancels his membership.
That’s a tripwire.
You can then use email marketing to reel in Customer A. Reach out via email to ask what went wrong or if you can improve your subscription service in any way. Then you offer a can’t-miss deal, such as one month for $5 instead of the standard $30 — with the option to cancel at any time, of course.
Both tripwire marketing campaigns can produce incredible ROI , but let’s explore the reasons behind their often-impressive results.
How Tripwire Marketing Can Help you Get More Conversions

Your conversion rate is the percentage of people who, when presented with an offer, take you up on the deal. It’s that simple.
When you make your offer more appealing — such as creating a low-cost alternative to an expensive product — your conversions will increase. You just have to make sure you’re providing sufficient value to warrant further purchases.
I’ve talked about lead magnets on the Crazy Egg blog as well as on NeilPatel.com , and they still work. However, sometimes it’s better to offer a product or service at a low price point than to offer it for free.
Why? People don’t always value free.
Business Insider published an excerpt of famed marketer Ramit Sethi’s bestselling book, “ Your Move: The Underdog’s Guide to Building Your Business .” In it, Sethi says:
“People value what they pay for…You’re not doing [prospects] a disservice by charging them, you’re actually doing a profound service for the people who want to take action.”
Sethi says he used to give away free copies of his $2,000 course. He just wanted to help people. However, most never even logged in.
He makes a good point that, if you don’t put a value on a product, your prospects probably won’t, either. But when you charge even a nominal amount, you send the message that you assign value to your own product — and so should everyone else.

Tripwire marketing should become part of your overall conversion funnel strategy . It deserves its own place.
The tripwire itself can belong in a few different places in your funnel depending on how you use it.
For instance, many marketers use tripwires as a top-of-funnel strategy. They use SEO and content marketing to increase web traffic, then offer an insane amount of value for a low price. That’s a great way to convert people quickly.
You can also use it in the middle of the funnel, though. Let’s say you have an email list full of people who converted on your free lead magnet. Set up a drip campaign — a series of emails — that promotes your tripwire offer.
Finally, consider tripwire marketing for the retention part of your funnel. Bring customers back by offering a great deal on something of immense value, then slip them into another drip campaign — one designed to promote your more expensive product or service.
Building your Tripwire Strategy
There’s a reason I call tripwire marketing a strategy. It isn’t something you just throw together and toss into the air, hoping consumers grab it. Make your tripwire an integral part of your business.
Go back to the questions you ask yourself when designing any marketing strategy:
- Who is your target customer?
- What do they want?
- What’s preventing them from getting what they want?
- How can you provide a solution?
Once you answer those questions accurately, you can apply them to creating a tripwire product and marketing it effectively.
If you want to lure back customers who have stopped buying from you, use the tripwire as an excuse for them to come back. You might send an email that says, “Hey, I just launched this super affordable product I think you might be interested in.”
When the prospect converts on your offer, remind him or her that you still have the original product available.
Now that you’re familiar with tripwire marketing, let’s dig into some specifics. How do you create a tripwire that will boost conversions for your business ?
The best tripwire ideas come from specific needs or desires. Analyze data you already have based on consumer buying habits and other user behaviors so you know where to start.
Step 1: Examine your product or service line
What products do you already offer? How much do they cost? These two questions become integral to creating a tripwire because you need to know what motivates your audience.
Think about common objections to your products or services. Maybe your target market finds them too expensive, for instance, or perhaps you’re new to the space, so you haven’t built sufficient trust.
Step 2: Find the product or service that gets the most sales
If you sell multiple products or services, figure out which one gets the most sales. That should become the basis for your tripwire because your most popular item already creates demand.
Maybe you create and sell hidden object games that customers can download and play. Most games cost around $12, but your conversions are lower than you’d like.
Look for the games that get the most downloads. You can decide how many you want to focus on. These will become the basis for your tripwire in the next step.
Step 3: Create a new version that costs much less, but still contains value
I’m not suggesting that you should take a huge financial hit for your business. If you sell online games, don’t give them away for free just because nobody’s buying.
Instead, either create a new version of an existing product or service — think “product lite” — or bundle several low-cost items at a great discount.
The goal here is similar to that of a lead magnet . You want people to buy your product because it’s a great deal.
Step 4: Start an email drip campaign for customers who buy the tripwire item
When you sell a tripwire item, don’t stop there. Nurture your leads by communicating via email.
You want those customers to come back and spend more on your business. To do that, you must remind them of the value they received from your tripwire products.
Direct them to your blog, invite them to follow you on social, and end each email with a CTA for your more expensive product. Make sure it’s directly related to the tripwire.
For instance, if your audience bought a hidden-object game bundle for $1, don’t ask them to convert on an offer for first-person shooter games. You’re targeting the wrong audience.
Step 5: Feature your tripwire product throughout your website
Exposure is critical to the success of your tripwire marketing campaign. If prospects can’t find it, they won’t buy.
Consider adding the tripwire product to your navigation bar or header. You could also use a Hello Bar to capture your website visitors’ attention.
Don’t forget to emphasize the value proposition. It isn’t just what the customer will get, but the low price involved. Your CTA might look like this: “Get 4 of our best-selling games for just $1! Offer ends soon.”
Creating a limited-time tripwire can boost conversions even further. Consider rotating your offers if you have more than one so you can take advantage of urgency.
Step 6: Add a lead magnet to your conversion forms to capture more emails
Lead magnets, tripwire marketing, and email marketing can work together in harmony. In most cases, you want to focus on one CTA at a time. Giving your prospects a choice, however, can sometimes pay off.
Let’s say you have three products:
- Huge online course (main product)
- Mini course (tripwire product)
- Short e-book (lead magnet)
The tripwire creates a happy medium between free and expensive.
The same strategy can work for other industries, including SaaS. Your three options might include the following:
- Primary SaaS product
The free demo restricts features, so if your audience wants to try out the full package, they might convert on the $10 trial versus the free demo.
You’re not necessarily leaving money on the table, either. Those who try the free demo might still buy your product, and you can enter them into your email database.
Step 7: Follow up with tripwire customers to ask for their feedback
Don’t miss out on an opportunity to get direct feedback from your customers. I do this all the time.
I recently sent out an email to my subscriber list that asked for direct feedback. It looked like this:
Notice that I didn’t ask people to fill out a survey or answer a poll. I asked them to actually reply to my email and give me detailed feedback.
You can do the same. Sure, you might have to wade through hundreds (or even thousands) of emails, but you’ll get insightful feedback that you can apply to tripwire marketing moving forward.
What Is a Good Conversion Rate for a Tripwire?
There’s no set “good conversion rate” for tripwire marketing, but you can learn from case studies. For instance, one company generated a conversion rate of nearly 10 percent using a tripwire priced at $9.95.

More importantly, their upsell rate — the percentage of people who converted on the larger product — was 26 percent. That’s pretty impressive.
You might not have the same results, but you can keep fine-tuning your tripwire marketing efforts until you find the strategy that results in the most conversions.
Optimize your Tripwire’s Conversion s with Website Optimization Tools
Conversion rate optimization (CRO) can play a hefty role in your tripwire marketing campaign’s success. You already have a powerful strategy to lure in more customers, but you need the tools necessary to understand your audience and better serve their needs.
Consider, for instance, how your website visitors behave when they land on your site. What pages do they visit first? How long do they spend? How far do they scroll?
You can get those results from user behavior reports , such as heatmaps and scroll maps. These tools allow you to visualize user behavior and capitalize on what you learn.
A heatmap, for instance, might show intense activity on your lead magnet form. Perhaps you could test replacing that area with your tripwire offer.

Don’t rely on guesswork, though. Continually A/B test the placement of your tripwire offers on your website to pinpoint the best locations.
Start Now: 12 Tripwire Marketing Ideas
There’s no reason to wait when it comes to tripwire marketing. Get out there with your offer and start earning more conversions.
If you’re struggling to come up with tripwire ideas, here are 12 that might resonate with your audience.
- Content upgrade
- 15-minute consultation
- Cheat sheet or checklist
- Instructional video
- Trial period
- Email consultations
- Partial product
- X downloads
- X products for $X
Any of these tripwires can work, but the right one depends on your business model.
You can see tripwire marketing in action at DesignCuts.com . It’s an extreme example that proves the methodology works.
DesignCuts offers bundles of creative assets at steep discounts — usually 97 percent or more.

This might just seem like a regular marketing strategy, but it’s not. DesignCuts wants you to buy these steeply discounted bundles, but it also wants you to buy individual products from its marketplace.
As you can see from DesignCuts and similar businesses, tripwire marketing can work as a foundational strategy as well as a supplement to your other marketing efforts.
What is tripwire marketing?
It’s a way to convince your target audience to buy a product from your business at a low cost. The action triggers a marketing campaign designed to convert those buyers on more expensive offers.
You can also use tripwire marketing to bring back customers who have disappeared into the ether. Remind them you still exist and why they bought from you in the first place.
I’ve provided 12 tripwire marketing ideas, but you can get creative and come up with your own, too. Focus on your target audience’s pain points .Then hit them with a product at a price point they can’t refuse.
Make your website better. Instantly.
Keep reading about content marketing.

Want a Better Way to Engage Your Audience? Try Data-Driven Micro-Content
Content marketing is in a state of surplus: there is too much supply of branded content and diminishing returns of audience engagement.


10 Effective FOMO Marketing Techniques to Increase Online Results
In case you’re allergic to social media and haven’t ever before heard the term, FOMO means “the fear of missing out.” But what is FOMO…

You’re unhappy with your conversion rate. People just aren’t buying what you’re selling. The solution might lie in tripwire marketing. The term tripwire marketing might…

Where to Place Customer Testimonials On a Website (+Examples)
Consumers have become increasingly blind to marketing and advertising strategies. The buyer’s journey gets longer and longer, and people are slower to trust companies. What’s…

A Step-by-Step Guide to Develop a Content Marketing Strategy That Converts
Your content marketing strategy influences how you reach your audience. If you don’t have a content strategy, now’s the time to create one. Many businesses…

Why Your Website Needs Infographics
The internet is suffused with data that is ever-flowing and ever-changing. Keeping your audience engaged with your content, whether it is on your website, social…

How To Increase Top of Funnel Traffic Through Link Retargeting
As a basic concept in marketing, the sales funnel is all about making prospects aware of your brand at first touch, right through to the…

What Is a Case Study in Marketing and How to Build One (Examples)
A marketing case study allows you to illustrate and explain how you achieved enormous success in a specific situation. For instance, last year, Jacob McMillen…

How to Identify Your Target Audience for Better Marketing
What is a target audience? And why does your specific target audience matter? That’s what we’re going to cover today. When you’re in business, you…

How to Find Your Target Market So Content Sticks (Guaranteed Success)
You hear it all the time: “learn how to find your target market and create interesting content.” But there’s a severe lack of useful material…

What Makes a Great Press Webpage?
PRs and SEOs love press releases. You get an SEO boost, earning links from journalists in your space across a bunch of different sites. And…

How To Be A Subject Matter Expert When You Don’t Know The Topic
Copywriters and content marketers are often required to write about industries or topics they know little about. This can make it a challenge to position…

How to Sell Without Selling In Every Blog Post
We all know blogging is an important part of online marketing. To succeed online today requires as many landing pages as possible, each ranking for…

7 Ways to Make Your Content More Actionable
One of the most disillusioning things about being a content marketer is putting the time and energy into creating A+ content only to have it…

10 Ways to Squeeze More Value out of Your Long-Form Blog Post
You put so much time and effort (and money, possibly) into your epic blog post. And boy did it get you results. That sucker got…
Over 300,000 websites use Crazy Egg to improve what's working, fix what isn't and test new ideas.
Cyber Insight
What is Tripwire Strategy: A Practical Guide to Cybersecurity
Updated on: June 17, 2023

I’ve seen the devastating effects of cyber attacks on countless individuals and businesses. The costs of a breach go beyond just financial losses, and can include damage to reputation, loss of trust with customers, and even legal action. That’s why it’s crucial for organizations to have a comprehensive cybersecurity strategy in place. One key tactic that’s often overlooked is implementing a tripwire strategy.
But what exactly is a tripwire strategy? Simply put, it’s a defense technique that enables organizations to detect unauthorized access to their systems. By establishing a set of tripwires, organizations can monitor their networks and quickly identify any suspicious activity. This is critical to minimizing the damage caused by cyber attacks and protecting important information.
In this practical guide, we’ll dive deeper into the concept of a tripwire strategy and provide actionable tips for implementing it in your organization. From identifying critical assets to setting up automated monitoring tools, we’ll cover everything you need to know to stay ahead of potential cyber threats. So buckle up, because your organization’s cybersecurity is about to get a whole lot tighter.
What is tripwire strategy?
- Tripwire strategy involves deploying a small number of armed forces to an area of geopolitical conflict.
- The primary aim of these forces is not to be an offensive threat, but to serve as a deterrent against any potential aggressors.
- if an aggressor crosses the line, they trigger a response.
- Tripwire strategy was prominently used during the Cold War, as it allowed countries to mark their presence in areas of conflict without being overtly aggressive.
- In recent years, the tripwire strategy has fallen out of favor, as modern militaries tend to favor more agile, mobile forces instead of static deployments.
While tripwire strategy may no longer be in vogue, it remains an interesting chapter in military history. The idea of using a small, lightly-armed force as a deterrent can be seen as a practical application of game theory: by making an aggressive move against the tripwire, an enemy risks triggering a larger response. Though the tactics and technologies of war have changed drastically since the Cold War, the basic principles of deterrence and strategic positioning remain key elements of military strategy.
???? Pro Tips:
1. Clearly define your cyber security objectives and identify the critical assets you need to protect. 2. Monitor and review your network traffic, logs, and system activities to detect any unauthorized changes or suspicious behavior. 3. Implement automated alerts and notifications to identify any deviations from your established security protocols or policy. 4. Establish contingency plans and responses in the event of a security breach or incident. 5. Regularly review and update your tripwire strategy to ensure that it aligns with your organization’s goals and objectives and adapts to emerging threats.
Understanding the Tripwire Strategy
The tripwire strategy is a military tactic that involves the deployment of a small number of armed forces into a geopolitical conflict zone. The primary purpose of these forces is not to attack the enemy or initiate conflict but to serve as a deterrent force. The presence of these troops makes it clear to the enemy that any attack on them would result in an immediate and forceful response from the larger military force.
The Origins of the Tripwire Strategy
The tripwire strategy came into prominence during the Cold War. At the time, NATO forces realized that it was not practical to maintain large standing armies in areas of geopolitical conflict. Instead, they decided to use smaller forces that could be quickly deployed in case of any trouble. These forces served as a tripwire that would trigger a much larger military response, should the enemy engage them.
The Role of Small Armed Forces in the Tripwire Strategy
The role of small armed forces in the tripwire strategy is critical. These forces serve as the first line of defense against the enemy and are often deployed in remote areas that have strategic significance, such as border regions or areas of strategic importance. While these forces may not be enough to engage the enemy, they are enough to trigger a larger response from the military, which serves as a deterrent force.
- Small forces have a lower deployment cost as they require fewer resources and logistics.
- Small forces have a lower operational cost as they have fewer logistical requirements.
- Small forces can be quickly deployed in case of any trouble, providing faster response.
The Importance of Deterrence in the Tripwire Strategy
The tripwire strategy is all about deterrence. The presence of small forces in a conflict zone serves as a warning to the enemy that any aggressive move will result in an immediate and forceful response. This perception of strength from the enemy effectively deters them from taking any aggressive action, which helps prevent the escalation of the conflict.
The presence of small forces can prevent the escalation of a conflict and minimize the loss of life and resources.
Examples of the Tripwire Strategy in Action
The tripwire strategy has been used in several geopolitical conflicts. One of the most well-known examples is the Korean Demilitarized Zone, where the United States and South Korea have deployed a small number of troops to deter any potential aggression by the North Korean army. Similarly, the United States has deployed a small force of around 1,000 troops to Poland to serve as a deterrent force against Russian aggression in the region.
The Effectiveness of the Tripwire Strategy in Geopolitical Conflicts
The effectiveness of the tripwire strategy in geopolitical conflicts is a subject of debate. While some experts believe that this strategy is effective in preventing the escalation of conflicts and minimizing the loss of life and resources, others argue that it can be counterproductive if the enemy decides to attack these small forces.
However, the fact remains that the tripwire strategy has been used successfully in several conflicts, such as the Korean Demilitarized Zone and the deployment of NATO forces in Eastern European countries in the aftermath of the Ukraine crisis.
Criticisms and Controversies Surrounding the Tripwire Strategy
The tripwire strategy is not without its critics and controversies. Some critics argue that the strategy has the potential to provoke the enemy into attacking the small forces, which can lead to the escalation of the conflict and result in higher loss of life and resources.
Another criticism of the strategy is that it can be seen as an aggressive move by the enemy, which can further strain relations between the opposing forces.
Despite these criticisms, the tripwire strategy remains a popular military tactic that is used by several countries to deter aggression and prevent the escalation of conflicts.
most recent

Cybersecurity Basics
What are the three approaches to security in cyber security: explained.

Services & Solutions
What is security solution and why it matters: ultimate guide.

Training & Certification
Is a masters in cybersecurity worth the investment.

What is the Cyber Security Strategy Objective? Protecting Against Breaches.

What is Dart in Cyber Security? A Powerful Tool for Threat Detection.

Decoding SLED: Is Public Sector Cybersecurity the Same?
PH +1 000 000 0000
24 M Drive East Hampton, NY 11937
© 2024 INFO
- Generative AI
- Office Suites
- Collaboration Software
- Productivity Software
- Augmented Reality
- Emerging Technology
- Remote Work
- Artificial Intelligence
- Operating Systems
- IT Leadership
- IT Management
- IT Operations
- Cloud Computing
- Computers and Peripherals
- Data Center
- Enterprise Applications
- Vendors and Providers
- Enterprise Buyer’s Guides
- United States
- Netherlands
- United Kingdom
- New Zealand
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Copyright Notice
- Member Preferences
- About AdChoices
- E-commerce Affiliate Relationships
- Your California Privacy Rights
Our Network
- Network World
Tripwire: The next generation of security tools
Unix Insider –
If you have ever discovered a system attack, you know that reloading the system and all its applications would be the first thing to do because you can’t identify the files an intruder may have tampered with. Reloading from scratch is tedious and time consuming, and putting a firewall in front of each host on the network still wouldn’t guarantee an uncompromised system.
Network intrusion detection systems (IDSs) can monitor and notify you of attacks, but how many IDSs do you really want to manage? An IDS relies on knowing a method of attack, and it can be bypassed if that method were to change with the help of an anti-IDS scanner, such as Whisker by Rain Forest Puppy.
A layered, or “onion,” approach to security is preferred because no single security mechanism is without its flaws. Previous Unix Insider articles have discussed hardening the host to minimize security exposures; this one covers Tripwire, a method for intrusion detection on a host level.
What is Tripwire?
Tripwire is an integrity assessment software package that maintains a database of file attributes and sends alerts when any of those attributes change. Essentially, it tells you if your servers’ files have changed since the previous day. Because it works on the host level, it should be integrated with other security mechanisms such as firewalls and network intrusion detection. While Tripwire’s primary purpose is to provide security, it provides the administrator with some source control as well.
Two versions of Tripwire are available: Tripwire 1.3.1 Academic Source Release (ASR) and the commercial version, Tripwire 2.2.1. Tripwire’s ASR was developed at Purdue University in 1992 by Gene Kim and Gene Spafford. The release (it’s still freely available) is the most widely used piece of integrity assessment software in the world. However, the relatively static ASR isn’t often upgraded. Tripwire does provide bug fixes and minor feature updates, but if you want support and the major new features, you’ll have to pay for them ($495 per host).
Tripwire 2.2.1 for Solaris
I haven’t used Tripwire 1.3 very much, mostly because it’s a hassle to configure and it requires meticulous care to keep the database on a write-protected floppy. Although maintenance on a large installation would be a nightmare, I see good reason to use it on static systems such as firewalls.
Recently I took a critical look at the improvements made to Tripwire 2.2.1 for Sun Solaris. They include:
- Support for Windows NT
- Much more flexibility in policy definitions, which provide more granular checking and readability
- Improved reporting mechanisms, including a GUI report viewer that runs on Windows NT (it can view a Unix-generated report as well)
- Stronger protection of policy, configuration, and database files using cryptographic signatures
- Performance optimization
- Enterprise management features for large installations
Tripwire 2.2.1’s installation guide is succinct, with useful examples and no gratuitous sales pitches. I strongly recommend that Tripwire be installed on a clean system that hasn’t been on the network. The default policy file will get you started. You should prepare a phrase for a “site key” and a “local key” and store them in a safe place (not online!).
You may want to customize the
(Note: You won’t need to store clear text copies of the policy and configuration files, because they can be regenerated at any time. You may, however, want to have them available for comparison purposes. The initial database should be backed up and stored offline in a safe location, providing a baseline for later comparison.)
The most significant changes in Tripwire 2.2.1 are enhancements to the policy file and the addition of cryptography to protect key files.
Cryptographic protection
One of the ASR’s biggest weaknesses is its dependency on write protection for database file hardware. If a file is software-mounted read-only, it can be compromised. While it’s still a good idea to have the database mounted read-only on a hardware level, the commercial version provides additional protection if that isn’t done.
Tripwire 2.2.1 cryptographically signs key files, using a 1,024-bit El Gamal encryption algorithm. The cryptographic signature routines (hashes) used in Tripwire’s commercial releases are stronger than those in the ASR.
The Tripwire policy file
The Tripwire policy file specifies the files, file characteristics, and directories that need to be checked. Both versions of Tripwire check all inode attributes, which include file permissions and signatures. Tripwire 2.2.1 has an expanded policy language that allows you to name and group rules, set severity levels, and provide email notification on a per-rule basis.
Aspects of the policy file include:
- Traversing mount points: Tripwire checks only the files and subdirectories on the device. For example, if you have a filesystem /usr/local and you tell Tripwire to check /usr , it won’t check anything under /usr/local unless you explicitly tell it to do so.
– (minus) — Ignore the following property + (plus) — Check the following property p — File permissions i — Inode number n — Number of links u — Userid of owner g — Groupid of owner t — File type s — File size l — Growing files (indicates that you expect the file to get bigger, not smaller; used for log files) d — Device number of the disk where the inode is stored r — Device number of devices b — Number of blocks allocated a — Access time stamp (indicates that the file has been read) m — Modification time stamp c — Inode creation/modification time stamp (indicates the last time the inode itself was modified) C — CRC-32 cryptographic signature M — MD5 cryptographic signature S — SHA cryptographic signature H — HAVAL cryptographic signature
- Stop points: The ability to ignore specific files in a directory tree. For example, you may want to check if any files in /etc were modified but may choose to disregard /etc/mnttab .
- Rulename: You can categorize file types by attaching labels to files. The Tripwire documentation suggests using rcfiles to group files run by root at system startup. As another example, the label localfiles could be associated with all locally developed files.
- Severity: You can associate a severity level with a rule and optionally run Tripwire with a specified severity level. Tripwire will check only the rules that meet or exceed the specified severity level. You can also attach a severity level to a block of rules.
- Emailto: You can send email notification on a rule-by-rule basis, directly from the policy file. This is useful if you’re checking an application supported by another administrator.
- Recursion: Tripwire can be directed to scan only the contents of the inode directory, not all the subdirectories. This is useful if you want to make sure /export/home1 is not 777 (or owned by a user) but you don’t care what users do to their own directories. You can also specify how many subdirectories you want to check.
- Directives: For large installations, it’s more efficient to have one policy file that can be run on all systems. However, you may want different actions taken, depending on the system. If so, you can use directives to make conditional statements about the rules to run, depending on the specified host or hosts.
- Variable definitions: Tripwire 2.2.1 lets you put your own hooks into the rules by supporting variable definitions in any place a string would normally appear. This helps make the policy file more readable and efficient.
Tripwire trip-ups
Every software package has its weaknesses, and Tripwire is no exception. For example, its cryptographic signatures improve security, but they’re not a panacea. If the keys aren’t protected, says Rain Forest Puppy, the database can be decrypted, tampered with, and re-signed. If the application can do it, so can a person. However, a person would have to know how the database was encrypted in the first place.
While the keys live on disk, the portions of the keys that must be used to sign files (the private portion of the site and local key files) are themselves encrypted symmetrically with Triple-DES and aren’t on disk. Someone would have to either brute-force the private portion of the 1,024-bit El Gamal key or force the triple-DES key to decrypt the same. It’s not impossible, but it is difficult. Tripwire relies on some obfuscation in this regard, which isn’t necessarily a bad thing. Simson Garfinkel pointed this out in his paper “Open Source: How Secure?”:
…security through obscurity only breaks down if keeping the secret is difficult. It’s pretty easy for a crook to look under your doormat and find the key. On the other hand, the orientation of the pins in your front door lock is simply another secret that provides security. That secret is better because you would have to try every possible key or [sic] to find the correct one.
Tripwire also experiences problems when it encounters applications that reset the access time stamp. For example, backup programs access files for reading, which modify the
fsdb exploit
Although you can use fsdb (the file system debugger) to reset file system attributes such as
An attacker could use this to mask the file access before Tripwire runs. However, the fsdb manual page even warns that “fsdb is intended for experienced users only.” Unless you know what you’re doing, don’t experiment with fsdb because it’s very powerful and doesn’t have an undo feature.
Everything can be exploited. The goal in security is to make the exploitation difficult; the longer an intruder sticks around, the greater the likelihood that he’ll be detected. In a paper proposing a cyber-UL, Tan of the L0pht recommended establishing standards for information security products, similar to those used by Underwriters Laboratories to determine a safe’s effectiveness. Tan notes, however, that computer crackers aren’t nearly as rushed as safe crackers are. He also points out that information is often copied or read, making the intrusion difficult to detect.
Defeating Tripwire takes time and a lot of skill, which should slow an attacker down long enough to get caught (assuming a good IDS is in use). Are the improvements in the commercial Tripwire worth the cost? If a systems administrator’s time is a limited resource, the improvements to the policy file alone are worth it.
Acknowledgments
Quite a few people assisted me with this article. I would particularly like to thank Rain Forest Puppy, Brian Martin and my partner, Jon Klein (who pointed out the fsdb exploit). In addition, the engineers at Tripwire went out of their way to answer each question I sent them. Joseph Wheeler, in particular, made himself available over a weekend and patiently answered my questions.
I’m still compiling the results of the reader survey from my December column, and I very much appreciate everyone who took the time to send feedback. Look for the results in next month’s column.
Related content
Meta opens its mixed-reality horizon os to other headset makers, a crafty new android notification power-up, microsoft uses its genai leverage against china — prelude to a tech cold war, how to fix icloud sync in seconds, from our editors straight to your inbox, show me more, gen z workers pick genai over managers for career advice.

Adobe’s new Firefly Image 3 adds genAI features to Photoshop

Enterprises want AI PCs, just not yet

Why the world will be wearing more technology in the future

Is AR/VR set for another growth spurt? | Ep. 143

Voice cloning, song creation via AI gets even scarier

More tech layoffs as AI takes hold

Is AR/VR set for another growth spurt?

Tripwire Funnels: Complete Guide With 9 Powerful Examples
Are you spending a lot of money, time, and effort driving traffic to your website – but it isn’t converting enough?
Are you using SEO, social media, content marketing, and paid ads, but your conversion rates are below par?
What if I told you that you can change this and start getting massive conversions and profits simply by introducing a tripwire in your sales funnel?
What is a tripwire you ask?
Well, a tripwire is a low-cost introductory offer specifically designed to convert cold traffic into paying customers.
In other words, you use a tripwire to warm people up to purchasing your core product/service.
But will it work for me?
It definitely can and there are many companies that use tripwires to rake in huge profits.
McDonald’s, for instance, has been using tripwire marketing to build a billion dollar empire.
McDonald’s does not make any profits on their burgers (which is supposed to be their core product) as they sell it at a lower price (tripwire) to attract customers.
They make the profits on upsells and order bumps which include everything that is bought along with the burgers – like fries and drinks.
In this guide, you will learn everything there is to know about tripwires and most importantly, how you can use them in your sales funnel to maximize conversions and profits.
Here’s what we will be covering.
So let’s explore this further.
What Exactly Is a Tripwire?
To put it simply, a tripwire is a high-value product/service offered at a far lower cost, making it an irresistible deal.
It lowers the barrier to entry as it involves low risk and a lower level of commitment.
The goal of a tripwire is twofold.
The first goal is to quickly increase your customer base by converting cold traffic into buying customers. And the second goal is to identify qualifying leads who are more likely to spend money on your products/services (and hence easier to sell to).
Once a customer takes up your tripwire offer, you can upsell them complementary offers leading to your core (or high ticket) offer.
This works because of the fact that it’s much easier to sell to existing customers who have purchased and used your product/service than to a new customer who has no idea who you are.
Let’s look at a simple example.
Let’s say your goal is to sell a box of 50 premium chocolates priced at $350.
If that’s your initial offer, people will be hesitant to buy because for one, the product cost is very high, and they also don’t know who you are or how those chocolates actually taste.
So instead, you make your initial offer a tripwire.
You give them a smaller pack of 5 chocolates at a highly discounted rate of say $5 (instead of the actual rate which would be $35) making this a no-brainer deal.
Anyone who is genuinely interested will find it silly to pass on such a deal.
Once a customer takes you up on the tripwire offer, you can then upsell them a slightly bigger box of chocolates, say a box of 25 at the standard rate of $175.
And if they take you up on that, you can sell them your core offer which is the box of 50 at $350.
Not every person who takes up your tripwire offer is going to end up buying your core product, but a lot of them will (which will also lead to repeat transactions), making you a ton of profits.
So even though you might incur a small loss initially (as part of your low-cost tripwire offer), you will end up making a whole lot more going forward.
Now the obvious question that arises is, why not give away the 5 chocolates for free?
Well, by giving away the product for free, you will get a lot more leads, but there is no way to figure out if these leads will be interested in shelling out money to buy your products.
Instead, when you put a price tag on it and someone buys your product, they become your customer and it’s much easier to sell to your existing customers.
So a tripwire offer helps you identify buyers. It helps you separate the wheat from the chaff.
Now let’s look at a real life example of a tripwire offer.
The following image shows a tripwire offer from Rebus university that sells real estate related training courses.
As you would notice, the product, which in this case is a membership to a real estate training course is of an extremely high value consisting of 12 power-packed courses.
In comparison, the offer rate of $7 (for 7 days of access) appears miniscule making it an irresistible deal.
Once the customer takes up the offer and gets to experience the courses first hand, they are highly likely to continue the membership at its original price which in this case is $127 after the trial period.
So instead of presenting the customer with an initial offer of $127 which will put them in a state of freeze, the company offers them a no-brainer tripwire offer of $7 with an option to cancel anytime.
This brings down the customer’s guard as it’s a low cost, low risk, and low commitment offer. And once they find real value in the training course, they are more than likely to sign up for the monthly membership.
We will look at many such examples of tripwires in action in the later part of this article. Ideas that will help you formulate your own successful tripwire.
How Is a Tripwire Different From a Lead Magnet?
A tripwire might seem very similar to a lead magnet but it is not.
A lead magnet is used to generate leads by offering a free incentive whereas a tripwire is used to convert leads into customers by offering a low cost (not free) incentive.
Let’s look at the differences in further details.
A lead magnet offers an incentive in the form of a free product (eg. a free ebook) in exchange for the prospect’s email address or other contact information.
The following image is a good example of a lead magnet.
As you can see, the prospect just needs to enter their email address to get a free copy of the gardening book.
A tripwire, on the other hand, offers a heavily discounted product/service as an incentive to convert prospects into customers. For example, an ebook that is sold for less than one-fourth of its original cost.
You can use a lead magnet and a tripwire together in your sales funnel as shown in the image below.
You first generate leads by offering a related product as a free lead magnet and then pitch your tripwire offer to those leads.
Finally, you pitch your high ticket offer to customers who took up the tripwire offer.
This is a really popular sales funnel model used by a lot of marketers.
How Is a Tripwire Different From a Discount Coupon?
A lot of people tend to confuse tripwire offers with discounted offers (like discount coupons). Although they might look the same, they differ in terms of their objectives.
The objective of a discounted deal is to increase conversions while also increasing profits. Therefore, you can only offer a nominal discount that does not cut too deeply into your profit margins.
Whereas the sole objective of a tripwire is to quickly convert as much traffic as possible into customers. Therefore, while offering a tripwire, you are not usually focused on making a profit.
In-fact, there is a possibility that you may incur a loss because you are offering a high-quality product at a very low cost. This loss can be recovered by upselling to your customers once they have taken up your tripwire offer.
For example, let’s say the cost of an ebook is $25 and you offer it for $20 as part of a discounted deal for a limited period. This will increase your conversions while increasing your profits.
Whereas in a tripwire offer, you will be offering the $25 ebook for some insanely low price like $2 or $5. The moment someone sees this, they will want to take up the offer as the value they are getting from the product is far higher than the price they need to pay.
So you get far higher conversions but in doing so, your profit margins become extremely low or non-existent in-case in some cases.
Where Should You Use a Tripwire in Your Sales Funnel?
A tripwire is generally used in the beginning (top) or middle of a sales funnel.
Top of Funnel
In this strategy, you drive traffic to your website using SEO, social media, paid ads, etc. and then sell them your tripwire offer.
For customers who take up the tripwire, you can show a discounted order bump and then an upsell or two before selling them on the core offer.
Upsells can be sent via a series of emails.
This is a great way to convert people quickly.
Middle of Funnel
You can also use a tripwire in the middle of your sales funnel.
In this strategy, you drive traffic to your website and use a lead magnet (free offer) to get people to sign up for your email newsletter.
You can then send your tripwire offer(s) through a series of emails.
You can also use this strategy if you already have an email list.
You can also use this funnel strategy to bring back existing customers who are no longer actively engaged with your business.
The 5 Factors That Make a Tripwire Successful
Simply implementing a tripwire does not necessarily guarantee its success.
If you want your tripwire to be successful, your tripwire offer needs to have a combination of 5 important factors.
These factors are as follows.
1. Low Cost but High Perceived Value
To be successful, your tripwire offer should be a combination of low risk, low commitment, low cost, and high value.
Always make sure that the perceived value of your tripwire product/service is much higher than the price being charged.
A question that pops up in the minds of most customers upon seeing such offers is, ‘ Okay, where’s the catch? ’
Give a clear message to your customers that there is absolutely no catch and no risk involved when they take up your offer.
Also, offer a money back guarantee.
For example, if your tripwire is a product/service trial, assure your customers that they are free to cancel the trial anytime and that they will not incur additional charges (as shown in the image below).
2. High Product Quality
The product that you offer as a tripwire needs to be of high quality so it builds trust and encourages your customers to continue doing business with you.
Think of this product as a small sample to your core offer. If the sample is not good, people will not be interested in purchasing your core offer or your upsells.
Therefore, it is important that the product you offer is of the best quality and offers high value to your customers.
3. Useful but Incomplete
Your tripwire product should offer high value but also leave your customers wanting more.
It should evoke a desire in them to go back to your website and buy more products/services.
For example, if you are selling an online course , you can give away the first few chapters of the course as the tripwire product. This way, your customers gain value out of the chapters and their most natural step would be to buy the remaining chapters.
So always make sure that your tripwire naturally leads to your core product.
4. Creates a Sense of Urgency
In order to be successful, your tripwire should create a sense of urgency.
Let your customers know that your offer is not going to last forever.
If it’s a physical product you can tell your customers that you have limited inventory and that the products will be sold out quickly if they don’t act fast.
In the case of a digital product, you can put a time limit for which the tripwire offer will be available.
Urgency creates the fear of missing out which will motivate your prospect to take up your tripwire offer.
5. Specific and Relevant
If you offer a tripwire product that is completely unrelated to your core offer, then people will not be interested in buying your core offer.
So make sure that there is a connection between the products your offer as your lead magnet, tripwire, order bumps, upsells and your core offer. All of these should naturally lead to the other.
For example, if you offer a free ebook on indoor gardening as a lead magnet, your tripwire should be something related to an indoor gardening webinar, and your core product could be a complete indoor gardening DVD course.
As you can see, all of these products naturally lead to the other.
As a rule of thumb, try to come up with your tripwire offer based on your core offer and not the other way round.
8 Types of Products You Can Offer as a Tripwire
Depending on your industry, there are a ton of products/services that you can offer as a tripwire.
The following are just some examples to give you a head start.
1. Product/Service Trials:
Trials can work great as tripwires.
You can offer your customers a limited time trial (ideally 7 to 10 days) at a low cost (say $7 for 7-day access) that allows them to test out and use all the features of your product or service.
This can work great for digital products, training courses, and membership sites.
2. Physical Products as Free-Plus-Shipping Offers:
In this type of tripwire, you offer a physical product completely free of cost as long as the customer covers the shipping fee.
For example, you can sell a physical book for free and charge only for shipping.
3. A Smaller Version of a Core Product Offering:
You can take a small portion of your core product and offer it as a tripwire.
For example, if you sell a training program that consists of 15 modules, you can give the first two modules at a low cost as a tripwire.
4. Complementary Products
A complimentary product that ties into your main product can make for a great tripwire too.
For example, if you sell sneakers, you can give a sneaker cleaner as a tripwire.
5. Small Workbooks or Journals
You can offer workbooks or journals that go along with your main product as a tripwire.
6. E-books or Info Products
An ebook related to your core product can make for the perfect tripwire.
Just make sure that the ebook offers high value and is not merely a product plug.
7. Webinars
Webinars are usually used as a free lead magnet, but they can work well as tripwires too.
A good way to go about this is to use a free lead magnet to get people on your email list and then send them a link to the paid webinar.
People will sign-up for a paid webinar as long as they are sure it is going to give them great value.
8. Consultations
You can offer a 15-minute one-on-one consultation on phone, chat or email as a tripwire.
Again the best way to approach this is to first start off with a lead magnet and then pitch your tripwire to people on your email list.
Your free product should give them a great value which will encourage them to take up the tripwire offer.
How to Price Your Tripwire Offer
Tripwires are typically priced between $1 and $20. But the price can be higher depending on the average cost of your products.
For example, if your core product sells at $2000, you can even consider selling a $100 tripwire offer.
As a rule of thumb, just make sure that the product that you are offering is of a far higher value than the price you are charging for it.
For example, an ebook that sells at $45 can be offered at one tenth its price at $5. Now that’s an offer that is super hard to resist. Also, because this is a digital product, you will not incur a loss.
So you have the freedom to price it as low as possible. This is not the case with a physical product though.
If your tripwire is a physical product, make sure that you price it in such a way that it does not burn a huge hole in your pocket.
Ideally, you need to price it so that you break even or incur as little loss as possible. You can always increase the shipping fee a little to offset the low price.
You can keep making corrective changes to your tripwire strategy based on the conversion rate and the average cart value (ACV) of your tripwire funnel.
9 Powerful Examples of Successful Tripwires in Action
Let’s look at 8 powerful examples of tripwire offers from successful marketers and e-commerce stores that will help you formulate your own tripwire strategy.
1. Ryan Levesque – Free Plus Shipping Tripwire Offer
One of the most popular tripwire strategies is ‘Free plus shipping’.
You basically offer a physical product completely free of cost as long as the customer pays for shipping.
The following image is a good example of this strategy in action.
As you can see, Ryan Levesque , the founder of, ‘The Ask Method ’, is selling his bestselling book ‘Ask’ for free as long as the customer is ready to pay $7.95 for shipping.
The book retails at $12.99.
Given the popularity of the book and the high value it promises, this is a no-brainer deal.
A tripwire like this can be used for any physical product (as we will see in the next example), but books definitely work great for this as you can keep the cost of production low and still up the overall value of the product.
Just make sure that the product you give for free is complementary or is in someway related to your core offer.
2. DotcomSecrets – Free + Shipping + Order Bump
Another popular tripwire strategy is to combine your free plus shipping offer with an order bump and upsell.
This way you can start making profits from your tripwire even before showing your customer the core offer.
As an example let’s look at how Russel Brunson the founder of ClickFunnels users this strategy.
As you can see from the following image, Russel sells his popular book DotComSecrets (cost $19.95) free of cost as long as you are ready to pay the shipping of $7.95.
But that’s not all. Once you enter your shipping details and go to the payment step, you are presented with an order bump as you can see from the image below.
The order bump includes a package deal of 5 of Russel’s best selling books available at a discounted rate of $37.
Because you are already paying for shipping and the shipping cost will remain the same for 1 book or this deal of 5 books, this deal is sure to tempt you to take up the order bump.
It’s a given that not everyone will take up the order bump, but many will, resulting in a considerable increase in earnings.
Let’s look at another example.
TheAwesomeParents.com offers a free pair of premium socks (original cost – $22) as a tripwire. You only need to pay for shipping
Once you take up the tripwire offer, they upsell related products as you can see from the image below.
In this way discounted order bumps and upsells can help you easily make a profit using a tripwire.
Of-course once the customer has taken up your tripwire and order bump/upsell, you can start selling them your core offer through a series of emails.
3. Name.com – First Year Discount and Then Regular Pricing
Name.com (domain name reseller) offers an extremely low price for registrations of newer domain name extensions.
For instance, you can buy a ‘.club’ extension for as low as 99 cents for the first year making this an irresistible deal. From the second year onward, the regular rate of $15.98 is charged.
Name.com knows that once a customer buys a domain name there is a high likelihood that they will continue for many years to come. So they make more than the low-cost tripwire over repeat transactions.
This strategy can work great for membership sites like forums.
Instead of the entire year, you can give the first month at a lower cost and then charge regular rates from the 2nd month onward.
Once a customer starts participating in the forum and starts finding value, there is a high likelihood that will continue their membership.
4. DesignCuts.com – Bundled Products as a Tripwire
Bundled products can work great as a tripwire offer.
Let’s look at an example.
DesignCuts.com offers design related resources like fonts, graphics, textures, templates and more for designers.
They release tripwire deals on a regular basis that generally includes a bundled collection of various design elements at extremely low prices.
All of their deals are offered for a limited time making it that much more attractive.
The following is one such example.
As you can see (from the above image), they offer an absolutely amazing deal for their vintage design library that includes vintage fonts, lettering library, textures, decorative elements, vintage brushes, illustrations and a lot more at an insanely low price.
Any designer will find this offer too good to pass up on. And once they take up the offer, they are more than likely to checkout the multitude of other resources offered by the site.
5. Ahrefs – $7 Trial for 7 Days
Product trials can make for great tripwire offers.
Ahrefs (online competitor research tool) offers a $7 trial (for 7 days) as a tripwire.
The 7 days trial gives you full access to all the features and you have the option to cancel anytime.
Once the trial is over, you will be charged the regular amount which is $99 per month for the Lite plan or $179 per month for the standard plan.
Many Ahrefs competitors offer a free trial with limited features but this is a better option as you get to use all the features for a low cost.
There is a high likelihood that anyone who signs up for the tripwire will continue with the monthly plan as they get to experience all the amazing features firsthand and know that these features are worth the money.
6. ExceedNutrition – $1 Trial for 14 Days
A really popular tripwire option is the $1 trial.
This tripwire is absolutely irresistible because of its super low rate and the fact that you get access to all the features of a product for a set period of time.
A good example is Exceednutrition.com that sells recipe packs.
This site offers a $1 trial that gives you access to all membership features for a period of 14 days.
As you can see from the image below, the customer is free to cancel anytime and there is also a money back guarantee that makes this deal completely risk free with low commitment.
Here’s another example (refer to the image below) of a $1 trial from JumpManual.com that offers training courses for basketball players to improve their vertical jump.
JumpManual.com offers a $1 trial for 7 days access to their complete training library.
Once the trial is over, you get to keep the product at a 73% discount or cancel anytime.
The discount makes this offer even more enticing. There is a high likelihood that the discount and the value that the product offers will motivate the buyers to make the $66 payment and keep the course.
Here’s one more example of a $1 trial from SaleHOO.com which is a directory of wholesale suppliers and dropshippers.
This is again a 7-day trial where you get full access to the directory.
Once the trial is over, you are charged an annual fee of $67 to continue access.
And while we are at it, let’s look at one more example, this time for a physical product.
YogaBody.com offers a $1 trial (for 1 month) for their Yoga Trapeze product (original cost $199).
So you only need to pay $1 plus the shipping fee to get this product.
This trial allows you to use this product for 30 days and if you are not satisfied, you can send it back at no additional cost. If you are satisfied and want to keep it, you can make the remaining payment.
So as you can see, trials can work for physical products too.
7. Snackcrate – A Smaller Sample as a Tripwire
Product samples can work great as tripwire offers too. Let’s see this in action.
Snackcrate is a subscription service that sends its customers snacks from various countries on a monthly basis.
In order to get more customers, Snackcrate offers a starter subscription box as a tripwire.
As you can see from the image below, this box costs only $5 and comes with over half a pound of snacks. So customers get to enjoy amazing snacks at an insanely low cost making this a super attractive offer.
To encourage customers to continue, Snackcrate also offers a discount for the 2nd month.
From the 3rd month onward the regular price of $26 is charged.
Customers are free to cancel their subscriptions at any time.
8. Shawn Thomas – Low-Cost Flash Sale as a Tripwire
Flash sales where you offer a product/service for an extremely low rate for a short period of time can make for a great tripwire offer.
The following image is an example of a popular course by Shawn Thomas (author and entrepreneur) that you can get access to for as low as $8 for a limited period of time. The actual cost of the course is $48.
As you can see, this course gives you access to a multitude of ebooks, videos, and articles making this an irresistible deal to pass up on.
Also, the deal is available only for a limited time that creates a sense of urgency that will motivate people to buy this as soon as possible.
9. Disney Movie Club – 4 Movies for $1 Tripwire Offer
In order to encourage you to join, the Disney Movie Club offers 4 movies of your choice for as low as $1 along with free shipping!
Anyone who is considering joining the Club will find this offer silly to pass up on.
Disney more than makes up for this low-cost offer because as per their membership terms, once you join (using this offer) you need to buy five more movie titles in the course of 2 years at a regular rate.
This again sounds very nominal as anyone who is into Disney movies, will certainly buy more than 5 titles in over 2 years.
Use CartFlows to Create Successful Tripwire Funnels
As we saw in this article, there are various strategies that go into making a tripwire successful and one of them is using order bumps and upsells to promote related products/services to customers who take up your tripwire offer.
If you are wondering how you can add these to your tripwire offer without hiring an expensive programmer or buying expensive software, then worry not.
You have an extremely easy to use and affordable solution available in CartFlows.
What Is CartFlows
CartFlows is a complete checkout optimization plugin for WordPress that integrates seamlessly with WooCommerce.
With CartFlows, you can easily build complex sales funnels including landing pages, checkout pages, order bumps, upsell/downsell pages and thank you pages with the click of a button.
The following image is an example of a checkout page created using CartFlows for a Free plus Shipping tripwire offer.
As you can see, this page also features an order bump right above the ‘ Call to Action ’ button.
You can create such pages easily using CartFlows as this plugin gives you access to prebuilt templates (for landing, checkout, upsell and thank you pages) that can easily be edited using your favorite page builder be it Elementor, Divi or Beaver Builder.
Once the page is designed, you can add additional functionalities like order bumps right from within your WordPress dashboard as shown in the image below.
You can also add Upsell/Downsell pages with ease and decide where you want them to appear in your checkout flow (sales funnel).
The following is an example of an upsell page created using CartFlows.
We encourage you to take CartFlows for a spin today and see how it changes the way you do business online.
You can download the free version of CartFlows from the WordPress repository here .
Wrapping Up
You are probably good at driving traffic to your website and even at generating leads using a lead magnet.
But if you are not able to get those leads to convert into customers, then all your effort is going to vain.
As we saw in this article, a tripwire could act as a bridge helping you convert leads into customers, whom you can then upsell to maximizing your profits.
So if you have never used tripwire marketing before, then it’s high time you give it a try even if it is only for a short period of time.
Use the strategies and tools mentioned in this article to create your own tripwire offer and see how it increases your conversion rates and your profit margins.
We are certain you will fall in love with this marketing tactic.
Get exclusive access to new tips, articles, guides, updates, and more.
Disclosure: This blog may contain affiliate links. If you make a purchase through one of these links, we may receive a small commission. Read disclosure . Rest assured that we only recommend products that we have personally used and believe will add value to our readers. Thanks for your support!
Hello Problem Solving Skills,
Thank you so much. Glad you liked it. 🙂
Your email address will not be published. Required fields are marked *
We believe creating beautiful websites should not be expensive. That's why Astra is free for everyone. Get started for free and extend with affordable packages.
YEAR IN REVIEW
Download is Just A Click Away!
Enter your email address and be the first to learn about updates and new features.
site categories
Former national enquirer publisher david pecker details “catch and kill” strategy to save donald trump from potentially damaging stories — update, ‘the lord of the rings’ owner embracer to split business into three listed groups.
By Jesse Whittock
Jesse Whittock
International TV Co-Editor
More Stories By Jesse
- Indian Actress Sayani Gupta Signs With Crimson Media & The SB Initiative
- 3Point0 Labs Signs Hisham Fageeh & Sultan Tamer’s Saudi-American Firm DH’BAB Productions
- Anthony Scaramucci Hosting U.S. Edition Of ‘The Rest Is Politics’; BBC Makes ‘Chess Masters’ Play; Erin Richards To Star In Welsh Drama ‘Mudtown’; Sarajevo To Honor Elia Suleiman — Global Briefs

The company that owns IP rights to the Lord of the Rings franchise is dividing its business.
Embracer Group has unveiled plans to split into three operations: games publisher Asmodee Group, indie gaming label Coffee Stain & Friends and Middle-earth Enterprises & Friends, which will house the Lord of the Rings and Tomb Raider rights.
Related Stories

Take-Two Buys Gearbox, Company Behind The Borderlands Franchise, From Embracer For $460 Million
'tomb raider: the legend of lara croft': netflix drops first trailer for new anime series.
Embracer’s largest shareholder, CEO Lars Wingefors, is planning on a “new long-term ownership structure” and will remain “a long-term, active, committed and supportive owner of all three entities.” Shareholders representing more than 50% of the capital and votes are supporting the plan.
Embracer has been working on a r estructuring program since June last year, focusing on cost savings, capital allocation, efficiencies and consolidation, while also selling businesses such as Borderlands franchise owner Gearbox Entertainment to Take-Two Interactive . The company owns or controls 9,003 franchises in areas such as comics and gaming.
Middle-earth Enterprises & Friends will focus on gaming development and publishing for PC and console, as well as managing the Lord of the Rings and Tomb Raider franchises. Embracer claimed the new structure will allow it to have “a better structure to maximize the potential of its highly strategic franchises.”
It will house several gaming levels such as Crystal Dynamics, Dambuster Studios, Eidos-Montréal, Flying Wild Hog Studios, Tripwire, Vertigo Games, Warhorse Studios and 4A Games, and own the IP to the likes of Dead Island , Killing Floor and Metro .
Phil Rogers will take the leading role at Middle-Earth Enterprises & Friend in the process leading up to the split. He is currently interim Group Chief Strategy Officer, with responsibility for the concluded restructuring program, and CEO of the operative group Crystal Dynamics – Eidos. Operating group CEOs at several labels will report to him, starting today.
Sweden-based Embracer acquired Middle-earth Enterprises, which owns the IP behind The Lord of the Rings and The Hobbit in August 2022, paying almost $400M for them. Amazon has acquired the TV rights to The Lord of the Rings in 2017, committing a $1B for a five-season series. Lord of the Rings: The Rings of Power launched on the streamer in September 2022. Season 2 is due to launch this year.
Read an open letter from Embracer Group CEO Wingefors here.
My journey started more than 30 years ago trading comic books to collectors and I have always dreamt to build something meaningful and significant. For me, building a business is not about reaching a certain size or position, it is about the journey to turn many small and sometimes a few large steps into something greater. Today is clearly a day when we take a bigger step. I am so excited to imagine what the coming decades will bring. At the IPO in 2016 I made a promise to stakeholders that I would be around for at least 25 years – and I still have 17 years left to fulfill that.
It has not always been a straight road, but I am very proud of the achievements made possible by thousands of talented individuals who create exceptional content entertaining millions of people worldwide. We have some of the most extraordinary companies and IPs in the games and entertainment industry within Embracer today, and it is my duty to ensure the best possible conditions for continued success.
I am convinced that the best is still ahead of us.
History has shown that diversified groups like ours can significantly enhance their chances of success by adopting a more agile, fast-moving approach and focusing on well-defined core market segments.
Numerous inspiring examples from Sweden illustrate how large enterprises have achieved greater success by dividing into multiple separate specialized companies. I am deeply motivated and inspired by these success stories and believe they offer valuable insights for our own strategic direction. The time is right for Embracer to become three public companies, each boasting sufficient scale, coherent strategies, specialized business models and empowered by visionary leadership teams. Rather than imposing conformity on thriving businesses, we should foster an environment that amplifies existing success. I am confident that this will be easier with three distinct winning formulas in specific market segments.
Asmodee is the leading developer, publisher, and distributor of tabletop games on the planet. “Coffee Stain & Friends” will become the leading and most innovative developer of community-driven games for PC/Console and Mobile. “Middle-earth Enterprises & Friends” will be developing immersive world-class entertainment IPs, including the iconic Lord of the Rings, leveraging in-house AAA capabilities and formidable partnerships.
I have always viewed my role as a Group CEO and main owner to be a promotor for successful entrepreneurs, gamemakers and business leaders in achieving more success.
This will not change.
There is not one way to do business, but some business models are more similar than others. The same goes for businesspeople. The ambitions may be similar, but the approach differs. The similarities between the businesses that will make up Asmodee, “Coffee Stain & Friends” and “Middle-earth Enterprises & Friends” are striking, but so are also the differences when it comes to go-to-market strategies and business profiles. All the companies have bright futures ahead, by perfecting what is working for each of them, and by continuing to cooperate when it makes sense.
There is significant untapped potential within the group, which I am confident the new structure will unleash. This will empower each individual and each team to grow and excel further in their careers as well as provide them with their own leadership and strategic direction.
This is the start of a new chapter, a chapter that I intend to remain part of as an active, committed, and supportive shareholder of all three new entities, with an evergreen horizon. Moving towards three independent companies reinforces Embracer’s vision of backing entrepreneurs and creators with a long-term mindset, allowing them to continue to deliver unforgettable experiences and entertainment across the globe.
I would especially like to thank all employees standing with us in the past challenges. Today marks the first day of the new journey, lets join it together and create the future.
This is the start of a new chapter.
Yours sincerely,
Lars Wingefors
Must Read Stories
Tiktok faces potential u.s. ban as joe biden signs bill; ceo vows court fight.

Sony Global Scripted Boss Nina Lederman Exiting After Six Years
Zendaya-palooza: ‘challengers’ opens as ‘dune: part two’ returns to imax, saturday’s contenders lineup: gypsy rose blanchard, ‘quiet on set’ team, more.
Subscribe to Deadline Breaking News Alerts and keep your inbox happy.
Read More About:
Deadline is a part of Penske Media Corporation. © 2024 Deadline Hollywood, LLC. All Rights Reserved.

IMAGES
VIDEO
COMMENTS
trip wire: [noun] a low-placed concealed wire used especially in warfare to trip an enemy or trespasser and usually to trigger an alarm or explosive device when moved.
Learn what a trip wire is, how to use it for alarms, traps and security, and where to get a trip wire kit. A trip wire is a thin line that triggers an alarm when an intruder trips over it.
Tripwire Enterprise. Tripwire Enterprise pairs the industry's most respected FIM with security configuration management (SCM) to provide real-time change intelligence and threat detection. For the compliance officer, it delivers proactive system hardening and automated compliance enforcement—resulting in a reduction of audit cycles and cost.
What is Tripwire? Tripwire is a comprehensive security solution that provides file integrity monitoring, vulnerability management, and configuration assessment capabilities. Its primary objective is to detect and alert on unauthorized changes made to files, directories, and system configurations.
The DIY Trip wires. 1. Bungee Marbles. The advantage of a bungee cord as a trip wire is its springiness. Think of it as a rubber band on steroids. In fact, the interior of a bungee cord is just that. Long strands of rubber encased in a flexible fabric braid. You can attach anything that makes noise to a bungee cord.
A small tripwire force is also unlikely to buy much time, something that is not commonly the purpose of such a deployment. Again, the purpose of a tripwire force is to, in the words of Schelling, "die heroically," not hold the line until help arrives. Third, deployed troops can preserve peace by making attempts at faits accomplis less ...
A tripwire is a passive triggering mechanism. Typically, a wire or cord is attached to a device for detecting or reacting to physical movement. Military applications. Such tripwires may be attached to one or more mines - especially fragmentation or bounding mines - in order to increase the area where triggering may occur.
Tripwire is a widely used security technology that helps organizations detect and respond to security incidents in real-time. It provides a comprehensive defense against cyber threats by monitoring changes made to files and directories on a regular basis. The technology is designed to provide continuous security and data integrity monitoring ...
Tripwire, Inc. is a software company based in Portland, Oregon, that focuses on security and compliance automation. It is a subsidiary of technology company Fortra. History. Tripwire's intrusion detection software was created in the 1990s by Purdue University graduate student Gene Kim and his professor Gene Spafford.
A tripwire is a useful way to persuade shy or reluctant customers to finally buy your core offer. Even if they would have refused before, likely because of a "trust gap." The tripwire is a low-perceived-risk way to bridge this gap. An eBook is a decent starting point if you want to make your own tripwire.
The tripwire is unrelated to the main product; In order to prompt the customer to buy the main product, the tripwire must relate to it and prove the main product's value. The tripwire completely duplicates the main product; In this case, the customers will not need to buy the main product at full price. Too big a discount / other benefit
Tripwire implementation has also raised some concerns. Tripwires vary by DoD component as do threshold values and approval authorities for each tripwire category. In some instances, it is unclear whether threshold values have an empirical basis (e.g., the post-award limitation on subcontracting or the constraint on selecting best value); in
Tripwire helps reduce your attack surface and risk exposure with proper system hardening and continuous configuration monitoring. See how Tripwire enables you to maintain a secure baseline configuration, monitor assets for deviations, while automating and guiding security teams for rapid repair of non-compliant systems and misconfigurations. ...
Tripwire marketing is the practice of offering leads a low-cost product with the intention of selling them more expensive products later. Tripwire marketing is a common practice intended to increase first customer acquisition. The theory behind marketing tripwires is that higher-cost purchases result in higher friction and reduced willingness ...
Tripwire IP360 is available as a managed service, Tripwire ExpertOps. It provides both personalized consulting and cloud-based infrastructure and is easy to deploy and use, with simple subscription pricing and a low total cost of ownership.
Tripwire marketing is a conversion-acceleration hack that convinces target consumers to buy something small from you rather than a more expensive product or service. There are actually two versions of tripwire marketing you can use to produce more conversions. The first one involves luring in customers with low-cost offers.
The tripwire strategy is a military tactic that involves the deployment of a small number of armed forces into a geopolitical conflict zone. The primary purpose of these forces is not to attack the enemy or initiate conflict but to serve as a deterrent force. The presence of these troops makes it clear to the enemy that any attack on them would ...
Tripwire is an integrity assessment software package that maintains a database of file attributes and sends alerts when any of those attributes change. Essentially, it tells you if your servers ...
Tripwire marketing is a conversion acceleration hack that persuades target customers to buy something small instead of a more expensive product or service. Tripwire is an attractive, low-cost ...
What Is A Tripwire? Although the word conjures up images of someone getting caught in a trap, the definition is far from sinister! A tripwire is a compelling, low-priced offer that's designed solely to turn a prospect into a customer.They're usually priced between $5.00 - $30.00, but the majority are less than $20.00.. The price point you choose depends on how your tripwire offer fits in ...
ExceedNutrition - $1 Trial for 14 Days. A really popular tripwire option is the $1 trial. This tripwire is absolutely irresistible because of its super low rate and the fact that you get access to all the features of a product for a set period of time. A good example is Exceednutrition.com that sells recipe packs.
Tripwire is the third book in the Jack Reacher series written by Lee Child. It was published in 1999 by Putnam in America and Bantam in the United Kingdom. It is written in the third person. In the novel, retired military police officer Jack Reacher becomes embroiled in a mystery involving a Vietnam War veteran who was reported missing in ...
What is Tripwire Enterprise? Fortra's TE is a cybersecurity solution that monitors integrity to bolster security and ensure continuous compliance. The most basic use cases for the solution that most customers are already aware of are monitoring file integrity and managing security configurations .
It will house several gaming levels such as Crystal Dynamics, Dambuster Studios, Eidos-Montréal, Flying Wild Hog Studios, Tripwire, Vertigo Games, Warhorse Studios and 4A Games, and own the IP to ...
Tripwire Advisory Services are available in annual subscriptions in increments of four hours per month (four, eight, twelve, or any unit of hours that fits your needs). For example, your consultant can provide expert input on questions that arise during operation for your Tripwire solution, review procedures and documentation, and offer best ...