How to trust self-signed certificates on macOS
HTTPS and SSL are important for security and it’s great that most browsers require or strongly encourage them to be used. This can be a little tricky, though, when you’re doing local development and you keep getting console errors about localhost not having SSL enabled. If you create a self-signed certificate with something like mkcert then you’re halfway there.
The rest of the battle is getting your web server to use the certificate (which will depend on what kind of server you’re using) and getting your system to trust your certificate.
To make sure your system and browsers (including Chrome, Firefox, Safari, Edge, etc.) will accept your certificate as valid, you can follow these steps:
- Open Keychain Access and the All Items category (lower left)
- Locate your self-signed certificate file ( .pem , .p12 , or something else) in Finder
- Drag your certificate file from Finder to Keychain Access, in the list on the right
- Open Certificates on the very bottom left
- Find the certificate you just dragged in and double click it (if there’s a dropdown arrow on the left then just ignore that, we want the top level one)
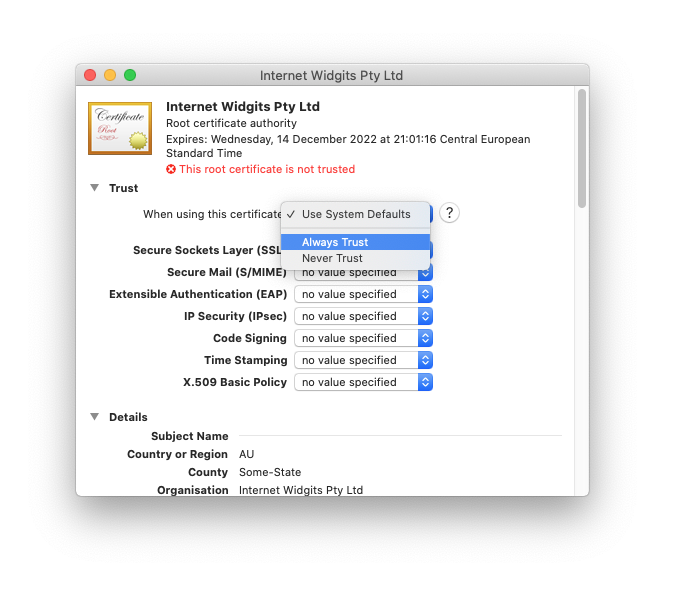
- Click the Trust dropdown arrow then change When using this certificate from System Defaults to Always Trust
Here’s a video that might also be helpful:
Now if you’re running anything on localhost that’s using your self-signed certificate, you can open that in any browser and you should see in the address bar that this is now a trusted site!
Published Sep 4, 2020
Learnings, tutorials, and advice about career, technology, and software development Brady Dowling on Twitter

Installing Self-Signed certificate to iOS 13 / macOS 10.15
by Lukas Kukacka
This is a followup of previous post about Generating Self-Signed certificate compatible with iOS 13 / macOS 10.15.
However, just using such a certificate on your server and connecting to the server is not enough.
Installing and trusting certificate on iOS 13
Install certificate.
- AirDrop works well. It will tell you directly “Someone would like to share a profile”
- Opening the certificate from iCloud Drive works fine
- Email should work as well
- Once received or opened, the certificate will become available in Settings
- Go to Settings → General → Profile & Device Management
- Select the new certificate in “Downloaded profile” section and check if all certificate information is correct (i.e. it is really your certificate)
- Tap “Install” , you end up on information screen, read the information 😀, tap “Install” again and confirm once again.
Trust certificate
Certificate is installed, now it has to be trusted.
Please follow steps at Apple support page: Trust manually installed certificate profiles in iOS and iPadOS .
Installing and trusting certificate on macOS 10.15
- Import the certificate to Keychain (Double click it or drag&drop it to Keychain)
- Select the certificate in Keychain
- Cmd+I or Right click → Get Info
- Expand the Trust section
- Change “When using this certificate: to “Always trust”
- Close the window. When closing the window, you will be asked for Touch ID or password to confirm the change
- Done. The certificate will now have little plus symbol on its icon in Keychain
Subscribe via RSS
SharePoint Framework (SPFx) courses for full-stack developers
Voitanos started in 2017 when founder Andrew Connell launched our flagship course, Mastering the SharePoint Framework that consists of 239 lessons spanning 41+ hours of instruction.
But maybe you just need to learn how to create web parts , extensions , Adaptive Card Extensions , or another SPFx related topic? We also offer smaller & more affordable self-paced on-demand video courses on specific topics, & free email courses!
SharePoint Framework courses →
Microsoft Teams App Dev courses for for full-stack developers
Microsoft Teams has taken over communication and collaboration and is turning into the cornerstone of custom apps built on the Microsoft 365 platform.
Learn with Andrew Connell in his multi-week accelerator program or start with his free email course, the Microsoft Teams AppDev OnRamp and learn what's involved in Teams app development.
Microsoft Teams App Dev courses →
Low/No-Code for Power Apps & Power Automate courses
While we're exclusively focused on creating educational articles, videos, as well as courses for web & cloud developers, we recognize the importance of low-code & no-code solutions.
That's why we've partnered with Laura Rogers & IWMentor to bring you the best Power Platform courses on Power Apps & Power Automate & courses for end users on SharePoint , Microsoft Teams , & Microsoft 365 .
Power Platform low/no-code courses →
Microsoft 365 Search for IT Pros & stakeholders courses
Organizations who've adopted Microsoft 365 know that Microsoft 365 Search is a huge topic to tackle. While you can click a few buttons & call it a day, modern collaborative experiences need a focused approach to build search-based solutions.
We hear the requests for guidance on search for their Microsoft 365 deployments . That's why we've partnered with Agnes Molnar & Search Explained to bring you the best content in this area!
Microsoft 365 search courses →
Here you'll find articles & other useful resources.
Videos (YouTube channel)
Learn about the SharePoint Framework, Microsoft 365, Microsoft Teams, Microsoft Azure, & other web development topics on our YouTube channel.
Newsletter: Full Stack Dev's Microsoft 365 Playbook
Subscribe to the The Full Stack Dev's Microsoft 365 Playbook by Andrew Connell, a bi-weekly newsletter for full stack developers who focus on Microsoft 365, Microsoft Azure, the SharePoint Framework, Microsoft Teams, and related topics.
Here you'll find future & past webinars from Voitanos. All previously recorded webinars are available for viewing on demand.
Podcast: Full Stack Dev's Microsoft 365 Playbook
The Full Stack Dev's Microsoft 365 Playbook with Andrew Connell helps you be the best Microsoft 365 & Azure full stack developer. This podcast includes exclusive podcast episodes as well as the audio from videos published in our YouTube channel and articles published on our site, delivered straight to your favorite podcasting app!
Show: CloudDev Clarity
This show is where Andrew Connell & Julie Turner discuss, debate, and even disagree on topics specific to developers who are primarily working in the Microsoft cloud space. That includes Microsoft Azure and Microsoft 365, but it's not limited to those areas! They'll also cover topics related to these areas, like testing tools, development tools, practices, and anything else.
Learn about a feature that’s been in Microsoft Graph for a very long time. But it’s always surprising to me how many people aren’t aware of it.
Tuesday, April 16, 2024
It’s been a few years since I published my last SPFx wish list - this time I want to expand it to all Microsoft 365 development topics!
Tuesday, April 2, 2024
The SharePoint Server SE feature update 23H4 is out, but this time it doesn’t include any changes to SPFx.
Friday, March 29, 2024
Creating and Trusting Self-Signed Certs on MacOS and Chrome
In this post, I'll explain how to create a self-signed certificate configure Chrome on your macOS to trust it for local development.
A few years ago I write a post Set up Self-Signed Certificates & Trusting them on OS X . I use Chrome as my primary browser which had a few changes both to the way it handles SSL certs. Since I know I’ll have to do this again in the future, I’m updating the post to reflect those changes if for no other reason, so I have something to go back to in the future.
There are two parts to this process:
- creating the self-signed cert
- adding the self-signed cert to the machine’s Trusted Root Authority
Workarounds
There are two workarounds you can leverage to avoid these issues… but use them at your own risk. I would skip this section and just do it the right way. They are listed here for information only.
Temporary Workaround
There is a temporary workaround. Until Chrome 65, you can configure Chrome to respect the old commonName behavior with the EnableCommonNameFallbackForLocalAnchors setting.
On Windows, add the following registry key
On MacOS, run the following:
Dangerous Workaround
Another option is to simply launch Chrome and instruct it to ignore all certificate warnings. Launch Chrome with the --ignore-certificate-errors argument.
This works when you work with your self-signed certs, but you should never browse the web in this mode.
Creating the Self-Signed Cert
Last time I did this, I used the openssl utility. It wasn’t too hard, but one thing that changed is how Chrome respects certificates.
As of Chrome 58, you can’t just identify the host using the commonName property. You must now also include the host in the subjectAltName property as well. The trick is you can’t specify the subjectAltName property using just the command line openssl tool.
Instead you must use a configuration file. What I did was take the default openssl configuration file on my machine, copy it and make a few edits. Here’s what the final one looks like:
The things to note are:
- lines 69-73: I specify the alternate URLs I want the cert to be registered for… in this case localhost
- line 61: the alternate URLs are used in the subjectAltName property for the cert.
With the config file set up, now you can create the certificate. Run the following command ( do it on one line… I’ve broken it up for readability ):
What are all these properties?
- req : PKCS#10 certificate request and certificate generating utility
- config : The configuration file to use.
- new x590 sha256 : Create a new key and output a self signed certificate instead of a certificate request; this is typically used to generate a test certificate or a self signed root CA.
- newkey : This option creates a new certificate request and a new private key. The argument takes one of several forms. rsa:nbits, where nbits is the number of bits, generates an RSA key nbits in size.
- nodes : If this option is specified then if a private key is created it will not be encrypted.
- days : When the -x509 option is being used this specifies the number of days to certify the certificate for. The default is 30 days.
- keyout : This gives the filename to write the newly created private key to.
- out : This specifies the output filename to write to or standard output by default.
At this point you’ve got the key and associated certificate created with the desired subjectAltName property.
Add Certificate to Trusted Root Authority
When browsing a site with a self-signed cert, you will likely see something like this in the Chrome address bar:
Chrome & Insecure Certificate
This indicates there’s an issue with the certificate. Typically this is because the cert is not trusted by the computer. What you need to do is add it to the machine’s Trusted Root Authority.
Within Chrome, do the following:
Developer Tools » Security tab
Click the View Certificate button to see the certificate:
Chrome > Developer Tools > Security Tab > View Certificate
Click and drag the image to your desktop. It looks like a little certificate.
Exporting the certificate
Open the Keychain Access utility in OS X.
Select the System option on the left.
Click the lock icon in the upper-left corner to enable changes.
Keychain > System
In the lower left, select the Certificates option.
Keychain Certificates
Drag the certificate you copied to the desktop into the list of certificates.
After localhost gets added to the System keychain, double-click it to open it again.
Expand the Trust section and for the first option, pick Always Trust .
Trusting Certificates
At this point everything has been configured. Quick Chrome and all other browsers and try again to navigate to the local HTTPS site. The browser should report it as a valid certificate:
Chrome & Trusted Certificate View
At this point you now have a self-signed certificate installed on your machine.
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Adding Self Signed Certificate to trusted root certificate store using Command Line
Is there any way to add certificate to Local Computer's Trusted Root Certification Authority using command line? I tried using certmgr.exe, it shows success but when i check root CA, i don't see my certificate there.
I followed the guide here:
Basically trying this command:
The command works and shows success on command line, but i can not see the certificate in actual trusted root store through mmc, Is it the procedure for self signed certificate is different? I have setup an IIS server with SSL Binding to this certificate which is originally placed in "MY" store. But im doing everything through autoamted scripts so i want to know how can i add this certificate to trusted root CA using cmd line option??
- trusted-root-certificates
- What were the actual command line options you used with CertMgr.exe? What (user) context is are the scripts running in? How did you create the certificate? How are you checking the root CA? – Ƭᴇcʜιᴇ007 Aug 18, 2012 at 0:56
- i used only this command: certmgr.exe -add -c mycertificate.cer -s -r localMachine root – Johnydep Aug 19, 2012 at 19:55
- and off course the script is a invoked java process running under admin privileges. – Johnydep Oct 6, 2012 at 13:26
3 Answers 3
Did you try it manually (by double-clicking on the CER file)? If even manually it's not working, you might be encountering a Vista bug .

Install a Root CA certificate from the command line (cmd.exe)
(This requires the Windows SDK. Visual Studio will install it for you and add it to the %PATH% .)
certmgr /add /c mycertificate.cer /s /r localMachine root
Note that no errors will be reported; the command will always return success (even when using a non-existing file for the certificate!). If the certificate doesn't show up in the Certificate Manager ( certmgr.msc ) after running this command, repeat the process using the manual steps below to check if there is any error in your certificate file.
Manual steps to install a Root CA certificate
- Double-click on the .cer file.
- On the Certificate dialog box, click Install Certificate to start the Certificate Import Wizard .
- On the Welcome page, click Next .
- On the Certificate Store page, select Place all certificates in the following store and click Browse .
- In the Select Certificate Store dialog box, select Show Physical Stores .
- Double-click Trusted Root Certification Authorities , select Local Computer , and then click OK .
- On the Certificate Store page, click Next .
- On the summary page, review the details and click Finish .
Install a Root CA certificate from PowerShell
See @harrymc's great answer below.
- Thank you, actually yes the problem was with certificate itself as i tried with other certificates and it worked. – Johnydep Sep 3, 2012 at 2:13
- the OP mentions using command line – João Pimentel Ferreira Aug 25, 2020 at 9:14
- 1 @JoãoPimentelFerreira: The OP's command line is fine, the certificate was buggy (see OP's comment above yours). But his use case is narrower than your bounty's. – tricasse Aug 25, 2020 at 17:55
The PowerShell command Import-Certificate can be used to import a certificate:
To run it through the Command Prompt (or batch) you may run it as:
Note above the use of the ^ escape character.
To list all available certificate stores, start a PowerShell session and enter:
- does this solution avoid warnings on the browsers? – João Pimentel Ferreira Aug 25, 2020 at 15:58
- 1 What kind of warnings? There shouldn't be any if the certificate is there. – harrymc Aug 28, 2020 at 9:02
- 1 @JoãoPimentelFerreira: If you mean the invalid SSL certificate warning, why is it invalid? Problems like elapsed date can be worked around in some browsers but not all. Missing Root Certification Authority is much more serious. So which is it? – harrymc Aug 28, 2020 at 14:20
- 1 @JoãoPimentelFerreira: Too late - your bounty has elapsed; it only lasts 7+1 days. Don't worry about it. – harrymc Sep 3, 2020 at 12:59
- 1 It sometimes happens. No problem on my side. – harrymc Sep 4, 2020 at 16:10
Powershell "Import-Certificate -FilePath 'C:\path\Cert.Cer' -CertStoreLocation Cert:\LocalMachine\Root"
The path location needs to have the ' rather than the " for cmd
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged ssl iis trusted-root-certificates ..
- The Overflow Blog
- Net neutrality is in; TikTok and noncompetes are out
- Upcoming research at Stack Overflow
- Featured on Meta
- Testing a new version of Stack Overflow Jobs
Hot Network Questions
- First measure with shorter than others in MuseScore
- You are given 8 fair coins and flip all of them at once. Afterwards, you are allowed to reflip as many coins as you want. What is the expected # heads
- is_number Function Implementation in C++
- Why is intensity additive?
- What would be the color of this ammonia ocean?
- Graphical artifacts appearing on translucent lines in plots
- Quantum circuit not showing when using qiskit with pycharm
- What does this concatenation operator do?
- Are there non-antisymmetric solutions to the electronic Hamiltonian?
- Fastest way to do damage/kill with wind
- One Up 8x8 puzzle
- Why does changing one's name to 'Vladimir' indicate allegiance to Moscow?
- Why don't room temperature superconductors exist?
- Is an explanation for consciousness even possible? If not, what are we searching for?
- A cipher proposed by Littlewood
- Is It Appropriate to Use Class Time for Students to Fill Out Course Evaluations?
- Changed file and folder names within a compressed .zip email attachment received from Outlook
- How can I expose Geometry Nodes properties in my addon panel?
- Can Lost Isle Calling's activated ability be copied effectively?
- What animal would make the best centaur
- Why do I get 9V while the figure in the datasheet says I should get ~4V?
- Pipe union fitting leaks slowly. How to seal?
- Is it idiomatic to say "I have to race with time" to mean I have to do a thing very fast and finish it before something bad might happen?
- room light controller
Five Tips for Using Self Signed SSL Certificates with iOS
SSL certificates are relatively cheap to purchase , but sometimes it would be easier if you could create your own. You might need to setup SSL on development and test servers that have different host names or on systems that will only ever be accessed on your local network.
Self-signed SSL certificates allow you to quickly create certificates for free, without having to pay a Certificate Authority (CA) or comply with any auditing requirements.
The downside of using self-signed certificates is that browsers will not automatically trust sites that use them. In Mobile Safari you would see an error like this:
The HttpWatch iOS app provides some more detail:
The rest of this post provides tips on how to setup iOS to avoid these errors and how to simplify the creation and management of self signed certificates.
Tip #1 – Don’t Accept your Self-Signed Certificate in Mobile Safari
It’s tempting to just select Continue or Details->Accept when you first try using your self-signed certificate in Safari:
This would allow you to open the site in Safari, but there are two significant downsides:
- Accepting the certificate in Safari just adds an SSL exception that prevents Safari warning you about the site. It doesn’t install the certificate as a trusted certificate on iOS. Any other apps (e.g. Chrome, HttpWatch, etc…) on the device will still fail to connect to the site.
- Once the SSL exception is added there doesn’t seem to be a way to remove it in iOS 7. In previous versions going to Settings->Safari and selecting ‘Clear Cookies and Data’ would delete it. This no longer seems to work in iOS 7 (please leave a comment if you know how to do this).
Tip #2 – Install Self-Signed Certificates as an iOS Configuration Profile
You can add an SSL certificate to the trusted list in iOS by simply emailing the file to yourself as an attachment:
Then select Install to add the certificate. Once you’ve done this you use the certificate without warnings in Safari or other iOS apps that use the device’s keychain..
Also unlike Safari SSL exceptions, you can access the certificate at any time in Settings->General->Profiles and remove it if required:
Apple provides an iPhone configuration utility for Mac and PC that can also install certificates. This would be a better option where email is not available or you have a larger number of iOS devices to manage.
Tip #3 – Don’t create Self-Signed Certificates within IIS
Creating self-signed certificates in IIS appears to be easy. You just select the ‘Create Self-Signed Certificate’ menu item:
Unfortunately, IIS uses the computer name as the host name in the certificate:
It most cases the computer name will not match the intended host name and you end up with a self-signed certificate that is never trusted – even when it is added to iOS:
It’s possible to fix this problem by installing and running the SelfSSL tool from the IIS 6 Toolkit. However, it’s probably easier just to use OpenSSL as described in the next tip.
Tip #4 – Creating Self-Signed Certificates with OpenSSL is Easy
One of the easiest ways of creating a self-signed certificate is to use the OpenSSL command line tool that is available on most platforms and installed by default on Mac OSX.
First create a private key file:
Then create the self signed certificate:
You can use any filenames you like for the key and certificate (.cer) files. The /CN parameter needs to be set to the required hostname (e.g. for https://www.mysite.com in the example above). The days parameter specifies the expiration date as days from today’s date.
There’s even a site to do this if you don’t feel like downloading OpenSSL, but of course it’s more secure to do it yourself.
On Apache servers the key and certificate file can be used directly in your SSL configuration. With IIS you need a PFX file so that you can import the certificate into the Server Certificates section of IIS. OpenSSL can create the PFX file for you as well:
Tip # 5: Consider Creating Your Own Certificate Authority (CA)
One problem with self-signed certificates is that you’ll need to set up trust relationships for each certificate on each device. An alternative is to create your own Certificate Authority (CA) root certificate and then create certificates based on it.
Instead of paying a commercial CA to create SSL certificates on your behalf, you are acting as your own CA. The advantage is that your custom CA certificate only has to be installed once on each device. The devices will then automatically trust any certificates you issue based on your root CA certificate.
Creating the CA certificate is a simple two step process. First create a private key file as before:
Then create the certificate:
The certificate file (myCA.cer) created above can be publicly shared and installed on iOS or other OS’s to act like a built in trusted root CA. Custom CA certificates on iOS are also stored in General->Settings->Profile:
The private key file (myCA.key) is only used when creating new SSL certificates.
You can create as many certificates as you like based on this CA certificate. There’s an extra step involved because you have to create a CSR (Client Signing Request) as if you were purchasing a commercial SSL certificate.
First you would create a private key:
and then create the CSR:
Then use the CSR to create the certificate:
The certificate created (mycert.cer) can be installed on a web server and accessed from any iOS device that already has the CA certificate installed.
UPDATED September 24th, 2015 – The OpenSSL certificate creation commands now include the -sha256 flag to avoid browser warnings about the use of SHA1. This tip was provided in a comment by Giancarlo Gomez – Thanks
Tags: IIS , iOS , OpenSSL , SSL
- 13 Comments
- Post a Comment
Got Something to Say?
Your email address will not be published. Required fields are marked *
Ready to get started? TRY FOR FREE Buy Now
Der Flounder
Enabling safari to successfully connect after changing a self-signed certificate.
Every so often, I need to use Safari to access something which is using a self-signed certificate. When I do so, Safari now walks you through the following procedure:
- Warns you something’s not right and give you the option of either going back or seeing the details.
- If you choose to see the details, Safari will let you view the certificate.
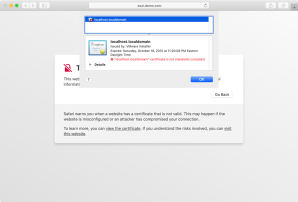
Safari will also give you the option of proceeding anyway.

If you choose to proceed anyway, Safari will store the self-signed certificate in your login keychain and mark it as trusted.
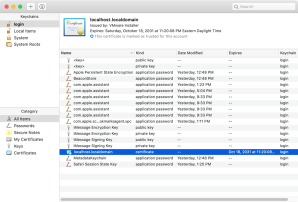
With this certificate now marked as trusted, Safari will allow you to visit the website.
However, what happens when the SSL certificate changes but keeps the same subject name? At this point, connections from Safari to the site will fail with an error message similar to the one described below:
Safari Can’t Open the Page Safari can’t open the page because Safari can’t establish a secure connection to the server “server.name.here”.

The reason that this message appears is because Safari is using HTTP Strict Transport Security , otherwise known as HSTS. One of the requirements of HSTS as implemented by Safari is that if the security of the connection cannot be ensured, Safari must terminate the connection and should not allow the user to access the web application.
Since the self-signed certificate stored in your login keychain and the SSL certificate being received don’t match each other, that tells Safari that the certificate being received can’t be trusted. The result is Safari immediately terminates the connection and displays an error message like the one shown above.
However, what if the certificate changing is known behavior and you know that proceeding is safe? It’s possible to re-set Safari’s behavior, but it’s not intuitive. For more details, please see below the jump.
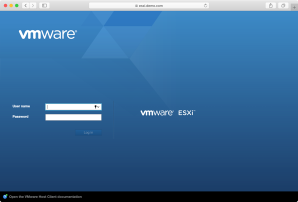
In my case, the certificate change is because I was switching between test instances of VMware’s ESXi hypervisor, which includes a web admin console which by default is protected by a self-signed certificate which is generated when you install ESXi. Because I had multiple ESXi test instances and wanted to use the same domain name for each, I had multiple unique self-signed SSL certificates which all happened to share the same DNS name: esxi.demo.com
What that meant is that for the first instance, I was given the option of storing the SSL certificate in my login keychain and I could thereafter connect to the first instance. But after doing that for first instance, I couldn’t then connect to the others because of HSTS.
To fix this, I used the following procedure:
1. Quit Safari
2. Open /Applications/Utilities and launch Keychain Access.app
3. Select the login keychain.
4. Identify the self-signed certificate which Safari stored in the keychain.

5. Delete the self-signed certificate.

Note: If you are running macOS Mojave or macOS Catalina, you will also need to run steps 6 through 13 to enable Terminal to have Full Disk Access. Otherwise, skip to step 14.
6. Open System Preferences.
7. Choose the Security & Privacy preference pane.

8. Select the Privacy tab.
9. Click the lock icon in the lower left corner of the preference panel and authenticate with an admin account’s credentials.

10. Select Full Disk Access .
11. Click the [+] plus button.
12. Select /Applications/Utilities/Terminal.app .
13. If needed, quit and relaunch Terminal.
Note: All of the commands referenced below should be run as the logged-in user. Do not run them as root.
14. Open Terminal
15. Run the following command to stop Safari’s HTTP Storage Manager.

16. Run a command similar to the one shown below to remove the server address from the Safari’s list of accepted self-signed sites:
For example, if the server name is esxi.demo.com , the command would look like this:
17. Run the following command to start Safari’s HTTP Storage Manager again:
To test this, open Safari and try connecting again to your site. It should now walk you through the procedure of storing the self-signed certificate and allowing you to connect again.

Share this:
So you have to do all that every time you switch esxi demo instances? Hopefully you don’t do that too often…
Thx for this!
Man, thank you for this post!
Thank you so much for providing this guide, it worked perfectly for me on Mac OS X Catalina! I was pulling my hair out and going absolutely mad before I discovered your writeup, you’re a lifesaver!
I’m with Ventura and from the start is not working as Safari is never trusting the certificate ;/
- No trackbacks yet.
Leave a comment Cancel reply
Recent comments.
- February 2024
- January 2024
- December 2023
- November 2023
- October 2023
- September 2023
- August 2023
- February 2023
- January 2023
- December 2022
- November 2022
- October 2022
- September 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- September 2021
- August 2021
- February 2021
- January 2021
- December 2020
- November 2020
- October 2020
- September 2020
- August 2020
- February 2020
- January 2020
- December 2019
- November 2019
- October 2019
- September 2019
- August 2019
- February 2019
- January 2019
- December 2018
- November 2018
- October 2018
- September 2018
- August 2018
- February 2018
- January 2018
- December 2017
- November 2017
- October 2017
- September 2017
- August 2017
- February 2017
- January 2017
- December 2016
- November 2016
- October 2016
- September 2016
- August 2016
- February 2016
- January 2016
- December 2015
- November 2015
- October 2015
- September 2015
- August 2015
- February 2015
- January 2015
- December 2014
- November 2014
- October 2014
- September 2014
- August 2014
- February 2014
- January 2014
- December 2013
- November 2013
- October 2013
- September 2013
- August 2013
- February 2013
- January 2013
- December 2012
- November 2012
- October 2012
- September 2012
- August 2012
- February 2012
- January 2012
- December 2011
- November 2011
- October 2011
- September 2011
- August 2011
- February 2011
- January 2011
- December 2010
- November 2010
- October 2010
- September 2010
- August 2010
- February 2010
- December 2009
- November 2009
- October 2009
- September 2009
- February 2009
- December 2008
- November 2008
- October 2008
- September 2008
- February 2008
- December 2007
- November 2007
- October 2007
- September 2007
- February 2007
- January 2007
- December 2006
- November 2006
- October 2006
- September 2006
- August 2006
- February 2006
- January 2006
- December 2005
- November 2005
- October 2005
- September 2005
- February 2005
- January 2005
- December 2004
- November 2004
- October 2004
- September 2004
- August 2004
- February 2004
- January 2004
- December 2003
- November 2003
- October 2003
- September 2003
- August 2003
- 10,416,525 hits

- Already have a WordPress.com account? Log in now.
- Subscribe Subscribed
- Copy shortlink
- Report this content
- View post in Reader
- Manage subscriptions
- Collapse this bar
Adding self-signed as trusted root certificate
If the server uses self-signed certificates, Can we import the root certificate of self-signed certificate, as trusted into the iOS device ?
and if we import root certificate as trusted into the device, Does connection work with ATS enabled ?
One can, but this solution is really only practical for enterprise apps where one can distribute the CA certificate via MDM. Prompting users to add root certificates isn't a very good UX for most users.
Thanks for your time on this query. My query was specific to self-signed certificate and not related custom CA certificates. Can you please reconfirm, if we can import the root certificate of self-signed certificate, as trusted into the iOS device ?
Yes, self-signed certificates can be imported into the device as trusted certificates.
Thanks for your time again.
I was able to import the self-signed certificate as trusted certificates, but even then i was getting the security-risk pop-up asking user to cancel or proceed with the server connection and the lock was in white color instead of green color (in safari browser). I have following two queries
1. Can you please confirm whether importing self-signed certificates into device as trusted certificates, should result in secured connection with server (green lock visible to user) ?
2. if we import self-signed root certificate as trusted into the device, Does connection work with ATS enabled as well ?
Yes, adding a self-signed certificate will always prompt the user about the certificate being untrused when attempting to add the certificate to the trusted store.
A self-signed certificate is not verified or audited by any external entities, so no, it will never have a green lock.
These two reasons are why most non-enterprise apps don't use self-signed certificates.
ATS will work with a trusted self-signed certificate.
There are edge cases that can prevent self-signed certificates from working as server certificates. What I typically do is create a root certificate (which is self-signed, obvious) and have that issue my server certificate. You can then install the root certificate like you would any other root certificate, and that puts you on the well-trodden path.
You can create a certificate authority and issue certificates from it using your Mac; Technote 2326 Creating Certificates for TLS Testing has the details.
Share and Enjoy — Quinn “The Eskimo!” Apple Developer Relations, Developer Technical Support, Core OS/Hardware
Looks like Quinn's URL has changed. Try https://developer.apple.com/library/content/technotes/tn2326/_index.html
You’re right that the correct link has changed. Fortunately the good folks at DevPubs catch this and redirect you. The reason why my link was broken is because I fluffed up the post (there was an incorrect character in my source Markdown)-:. I’ve fixed that now.
Thanks for pointing this out.
As a bonus extra, you might want to check out my Q&A about installing test CA root certificates: QA1948 HTTPS and Test Servers .
The certificate for this server is invalid. You might be connecting to a server that is pretending to be “localhost” which could put your confidential information at risk.
is that Q\&A still applicable?
My app makes HTTPS requests to localhost
Trust manually installed certificate profiles in iOS, iPadOS, and visionOS
If you manually install a profile that contains a certificate payload in iOS, iPadOS, and visionOS, that certificate isn't automatically trusted for SSL. Learn how to manually trust an installed certificate profile.
This article is intended for system administrators for a school, business, or other organization.
You must manually turn on trust for SSL/TLS when you install a profile that is sent to you via email or downloaded from a website.
If you want to turn on SSL/TLS trust for that certificate, go to Settings > General > About > Certificate Trust Settings. Under "Enable full trust for root certificates," turn on trust for the certificate.*
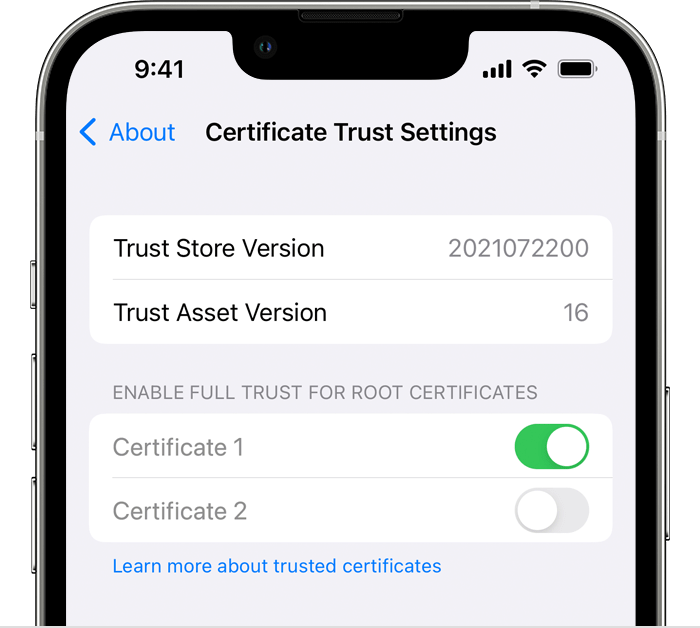
Apple recommends deploying certificates via Apple Configurator or Mobile Device Management (MDM). Certificate payloads are automatically trusted for SSL when installed with Configurator, MDM, or as part of an MDM enrollment profile.
*If “Enable full trust for root certificates” doesn’t appear, you haven't installed any additional certificates.
Explore Apple Support Community
Find what’s been asked and answered by Apple customers.
Contact Apple Support
Need more help? Save time by starting your support request online and we'll connect you to an expert.
- Configuring and Managing B2B Messaging
Import Signed Certificate
The key import process replaces the self-signed private key certificate.
Take these steps:
On the Manage B2B Certificates page, locate the self-signed private key for which you want to import the new key. You can narrow the list of certificates by using the Search field to enter whole or partial words or click Refine to choose from predefined values.
Select Import from the drop-down list in the Action column.
Enter the password of the self-signed private key certificate.
Browse for the file you want to upload, select it, and click Import . The file that contains the signed key is uploaded. Notice that the Type field changed from Self-Signed to Trusted.

IMAGES
VIDEO
COMMENTS
Import and export keychain items; Delete a keychain; Use certificates. Get information about a certificate; Determine if a certificate is valid; Change the trust settings of a certificate; Request a certificate from a certificate authority; Add certificates to a keychain; Create your own certificate authority; Create self-signed certificates ...
From Safari Help. Change the trust settings of a certificate. You can view or change a certificate's trust policies in Keychain Access. Open Keychain Access for me. In the Category list, select a category. Select a certificate, then choose File > Get Info. Click the Trust disclosure triangle to display the trust policies for the certificate.
To allow the self signed certificates to be FULLY trusted in Chrome and Safari, you need to import a new certificate authority into your Mac. To do so follow these instructions, ... Importing self-signed local certificates, tuning chrome://flags & HSTS domain did not help. Chrome should definitely keep that old good button "Add security ...
Open Keychain Access and the All Items category (lower left) Locate your self-signed certificate file ( .pem, .p12, or something else) in Finder. Drag your certificate file from Finder to Keychain Access, in the list on the right. Open Certificates on the very bottom left. Find the certificate you just dragged in and double click it (if there ...
A certificate, also known as a "digital certificate" or a "public key certificate," is a file that helps keep web communications secure. Certificates are issued by trusted organizations, such as VeriSign, Inc. or RSA Security, Inc. When you visit an encrypted website—for example, to do online banking—Safari checks if the site's ...
In the Keychain Access app on your Mac, choose Keychain Access > Certificate Assistant > Create a Certificate. Enter a name for the certificate. Choose an identity type, then choose the type of certificate. For an explanation of certificate types, click Learn More. To manually specify the information in the certificate, such as key pairs ...
I want to import a client certificate into MacOS 13.4 for use with Safari. I have imported the certificate both with Keychain access and the security command into MacOS. Command used: security import ... Importing a self-signed SSL certificate on MacOS. 30. Can't import public key into OSX Keychain. 5.
Import the certificate to Keychain (Double click it or drag&drop it to Keychain) Select the certificate in Keychain. Cmd+I or Right click → Get Info. Expand the Trust section. Change "When using this certificate: to "Always trust". Close the window. When closing the window, you will be asked for Touch ID or password to confirm the change.
Adding the certificate. 1. On safari navigate using https to the desired sample page. 2. When you get the Certificate not trusted popup click on show Certificate. 3. Click on the checkbox to always trust the site, click on the Trust drop arrow, verify that the three selections are all set to always trust and click continue. 4.
new x590 sha256: Create a new key and output a self signed certificate instead of a certificate request; this is typically used to generate a test certificate or a self signed root CA. newkey: This option creates a new certificate request and a new private key. The argument takes one of several forms. rsa:nbits, where nbits is the number of ...
On the Certificate dialog box, click Install Certificate to start the Certificate Import Wizard. On the Welcome page, click Next. On the Certificate Store page, select Place all certificates in the following store and click Browse. In the Select Certificate Store dialog box, select Show Physical Stores.
Open settings and use the search at the top to look for profiles. Open profiles and "install" the profile for your self-signed cert. Then go to settings->general->about->certificate trust settings (all the way at the bottom) and flip the toggle to trust all roots for that profile. This is a real pain because apple has intentionally made it a pain.
Tip #1 - Don't Accept your Self-Signed Certificate in Mobile Safari. It's tempting to just select Continue or Details->Accept when you first try using your self-signed certificate in Safari: ... With IIS you need a PFX file so that you can import the certificate into the Server Certificates section of IIS. OpenSSL can create the PFX file ...
Root certificates installed manually on an unsupervised iPhone and iPad through a profile display the following warning, "Installing the certificate "name of certificate" adds it to the list of trusted certificates on your iPhone or iPad. This certificate won't be trusted for websites until you enable it in Certificate Trust Settings.".
1. Since you're using Dropbox, you don't need a web server of your own to solve this. Find the cert in the Dropbox iOS app. Tap the ellipsis in the upper right and select Copy Link. Open Safari, paste in the link, and go. If Dropbox offers to open it in the Dropbox app, say no. Click the link to Download the file.
Add self-signed certificate. Ask Question Asked 2 years ago. Modified 2 years ago. ... I did import that certificate into my Synology NAS and set it as default, and when I trust the CA certificate in my MacBooks it all worked. ... safari; security; certificate. The Overflow Blog Net neutrality is in; TikTok and noncompetes are out. Upcoming ...
We would like to show you a description here but the site won't allow us.
I've been using self-signed certificates in the intranet of my small office and after upgrading to iOS 11, the certificates does not work for me. (Chrome and other browsers are happy with them.) I've got my self-signed root ca file and converted it to .der file, and installed it onto my iPad via web.
Hi, Thanks for your time again. I was able to import the self-signed certificate as trusted certificates, but even then i was getting the security-risk pop-up asking user to cancel or proceed with the server connection and the lock was in white color instead of green color (in safari browser).
First, email your root certificate (e.g. fake-root-cert.pem) to yourself. Next, open the email on your phone, and click the attachment. This will open the iOS Setting up and offer you to install ...
Under "Enable full trust for root certificates," turn on trust for the certificate.* Apple recommends deploying certificates via Apple Configurator or Mobile Device Management (MDM). Certificate payloads are automatically trusted for SSL when installed with Configurator, MDM, or as part of an MDM enrollment profile.
Select Import from the drop-down list in the Action column. Enter the password of the self-signed private key certificate. Browse for the file you want to upload, select it, and click Import. The file that contains the signed key is uploaded. Notice that the